当前位置:网站首页>Simple text analysis of malicious samples - Introduction
Simple text analysis of malicious samples - Introduction
2022-06-25 04:33:00 【vlan911】
Introduction , This article is an introductory article , The content in it paves the way for subsequent software security analysis , There's something , But not much , So if you find it useful, just take a look , Don't look if you think it's useless , Don't spray ; Such application scenarios , In fact, it is malicious sample behavior analysis 、 At the back door 、 After the emergency response, copy away the malicious samples and conduct a preliminary investigation , Can find out what the sample did , What functions does it have
Preface :
This article simply uses three tools
RegShot( Registry comparison tool )
Process monitoring tools Procmon.exe
Flaming sword
Download the sample , This sample is not a Trojan back door , But it is also recommended that you analyze it in the virtual machine , The download address is as follows :
https://github.com/Shyujikou/binarybook/tree/master/chap01/sample_mal/Release

The first tool we use is the registry comparison tool , Its function is to snapshot the registry , After running the program, the registry will be snapshot again , If something happens in the registry “ Additions and deletions ” after , Will be detected , Make a quick comparison and express it to us , It is convenient for us to check the changes in the registry .

We chose to save the report to Location , What I choose here is the desktop , Then create a snapshot A; Take a full snapshot
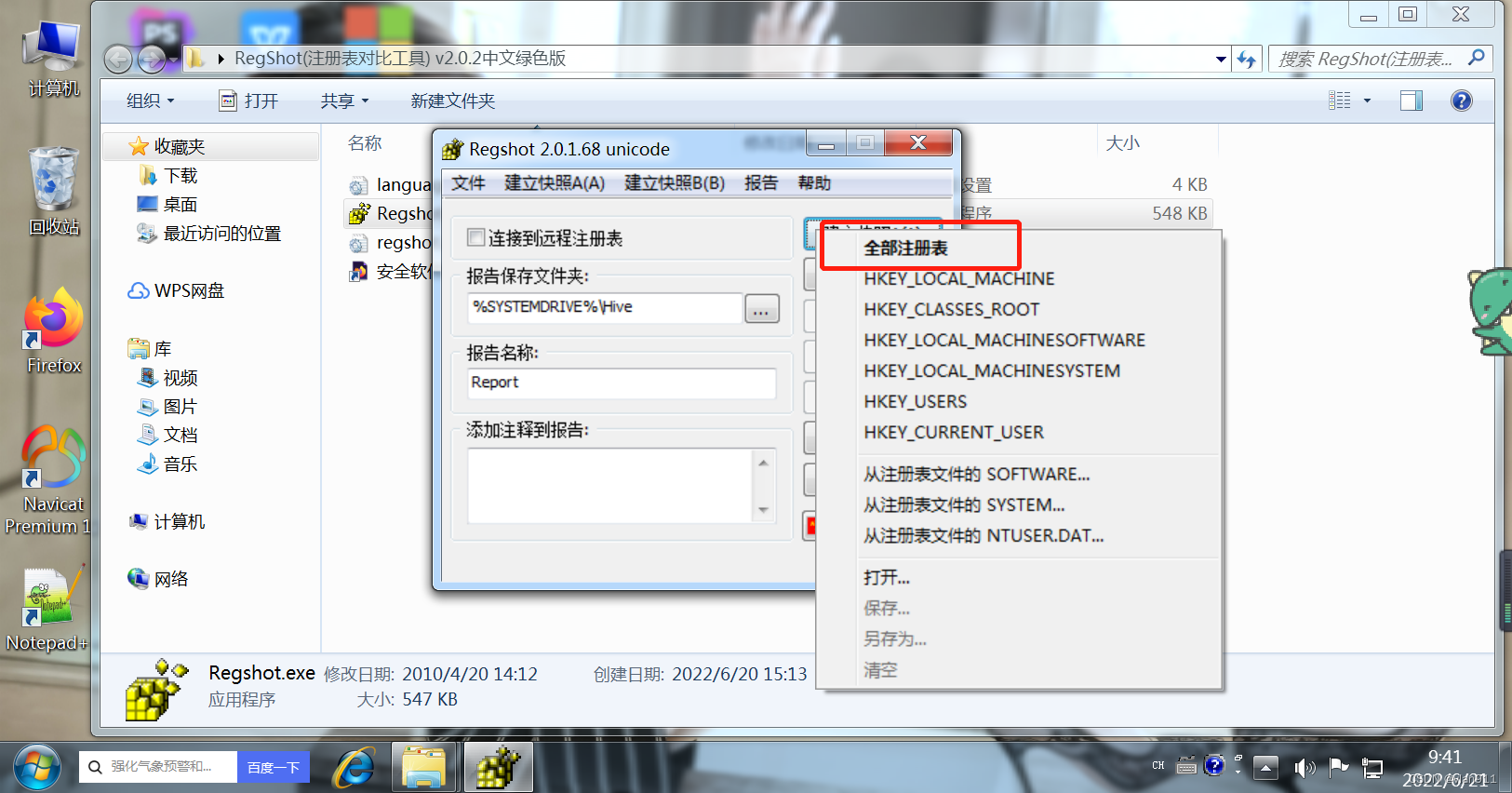
At this point, we double-click sample_mal.exe , But don't quit the program 
Now we turn on Process monitoring tools Procmon.exe
We filter the processes we specify for analysis 

At this point, after filtering , In fact, we can already find ,sample_mal.exe Did an operation to open the registry

At this point, we exit sample_mal.exe, To see what he is going to do , We found that he did a lot of things 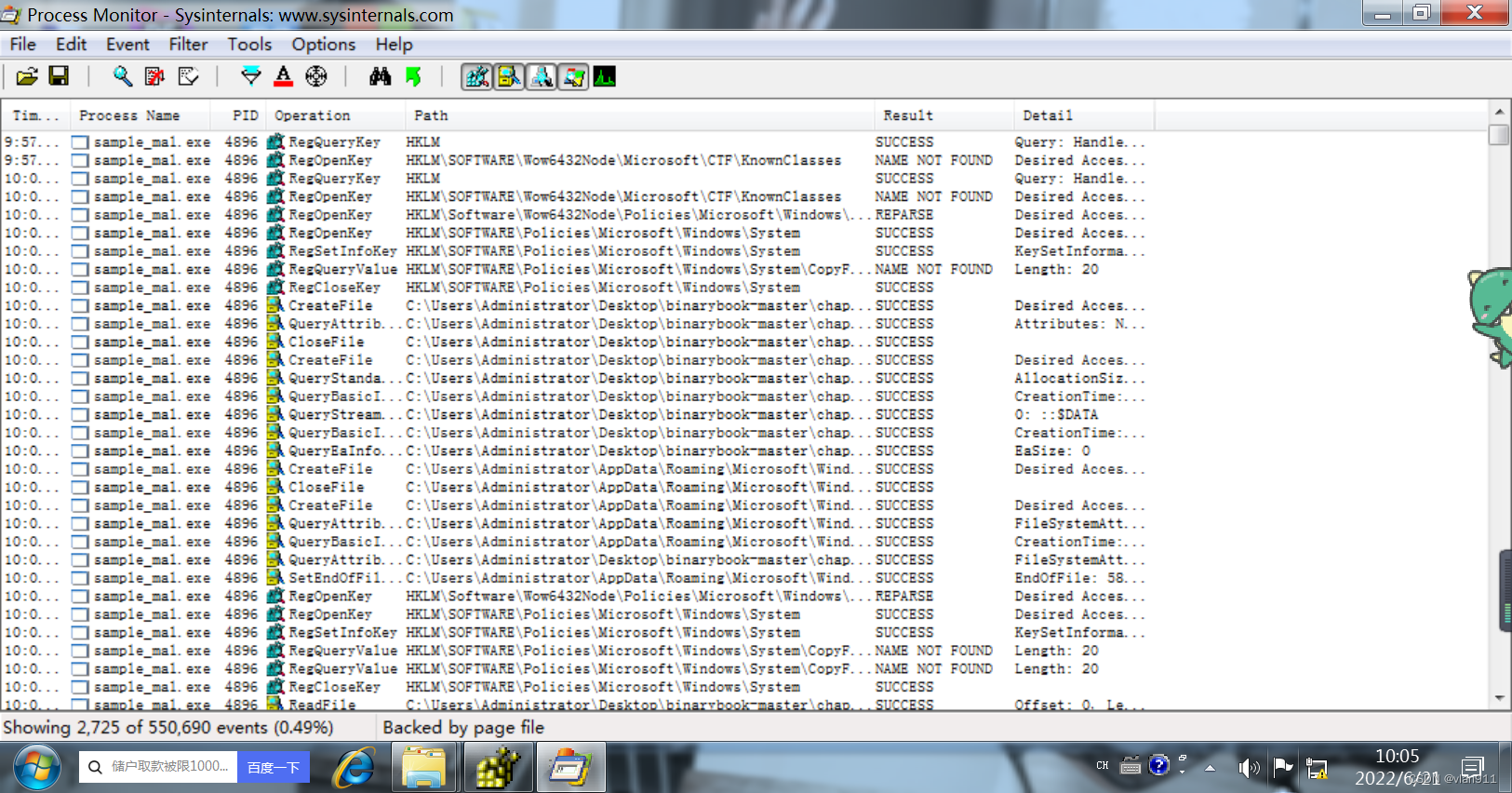
It's a mess , There are no readable lines , But there's no way , I still have to look through the garbage , Here is an introduction Procmon The meaning of each item of
CloseFile file - close
CreateFile file - establish
CreateMailSlot Create mail bits
CreatePipe Create pipes
DeviceChange Equipment changes
DeviceIoControl Device input / Output control
FileStreamInformation File stream information
FileSystemControl File system control
FlushBuffersFile Empty buffer file
InternalDeviceIoControl Internal equipment IO control
Load Image Mount image
LockFile file - lock
NotifyChangeDirectory Prompt to change directory
PlugAndPlay Plug and play
Power Power Supply
Process Create process - establish
Process Defined process - Definition
Process Exit process - close
Profiling interrupt Configuration interrupt ?
ReadFile file - Read
RegCloseKey The registry - Off key
RegCreateKey The registry - Create key
RegDeleteKey The registry - Delete key
RegDeleteValue The registry - Delete value
RegEnumKey The registry - Phyllic key
RegEnumValue The registry - Enumerated values
RegFlushKey The registry - Empty key
RegLoadKey The registry - Read key
RegOpenKey The registry - Open key
RegQueryKey The registry - Query key
RegQueryKeySecurity The registry - Query key security
RegQueryMultipleValueKey Query multivalued keys
RegQueryValue The registry - The query value
RegRenameKey The registry - Rename key
RegSetInfoKey Set the information key
RegSetKeySecurity The registry - Set key security
RegSetValue The registry - Set the value
RegUnloadKey Unload key
Thread Create Threads - establish
Thread Exit Threads - close
UnlockFileAll File unlock all | |
|-QueryAllInformationFile Query all information files
QueryAttribbuteTagFile Query attribute tag file
QueryAttributeInformationVolume Query attribute information volume
QueryBasicInformationFile Query the basic information file
QueryCompressionInformationFile Query compressed information file
QueryControlInformationVolume Query control information volume
QueryDeviceInformationVolume Querying device information volumes
QueryDirectory Inquire about - Catalog
QueryFileInternalInformationFile Query file internal information file
QueryFileQuota Query file quota
QueryFullSizeInformationVolume Query the full size information volume
QueryInformationVolume Query information volume
QueryLabelInformationVolume Query label information volume
QueryMinorCode49> Query sub code
QueryMoveClusterInformationFile Query the mobile cluster information file
QueryNameInformationFile Query name information file
QueryNetworkOpenInformationFile Query the network opening information file
QueryObjectIdInformationVolume Query object Id Information volume
QueryOpen Inquire about - open
QueryPositionInformationFile Query location information file
QuerySecurityFile Query security file
QuerySizeInformationVolume Query the size information volume
QueryStandardInformationFile Query the standard information file
QueryStreamInformationFile Query stream information file
SetAllInformationFile Set the full information file
SetBasicInformationFile Set the basic information file
SetDispositionInformationFile Set the deployment information file
SetEndOfFileInformationFile Set the end of file information file
SetFileQuota Set file quota
SetLinkInformationFile Set the connection information file
SetPipeInformation Set pipeline information
SetPositionInformationFile Set the location information file
SetRenameInformationFile Set rename information file
SetSecurityFile Set the security file
SetShortNameInformation Set short name information
SetValidDataLengthInformationFile Set legal data length information file
SetVolumeInformation Set volume information
Shutdown close
SystemControl System control
Thread Pro Threads
WriteFile file - write in
Then we'll look at him , Extract important information
create a file C:\Users\Administrator\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\0.exe
We did see this in the directory he prompted 0.exe file , In fact, the contents of this file are similar to sample_mal.exe It's exactly the same , It's just a copy of the past

This folder has a feature , He will start with the calculator ; in other words ,0.exe It will automatically after the calculator restarts , It won't be because you restart the computer process .
Then he created a folder named 1.exe The file of , After comparison , He and 0.exe The content of is the same 
And pay attention to , Their dates are 2015 year , Not when the file was actually changed 
And he shut down sample_mal.exe process , So the process cannot be found , The file was also removed , I just can't find the operation to remove it 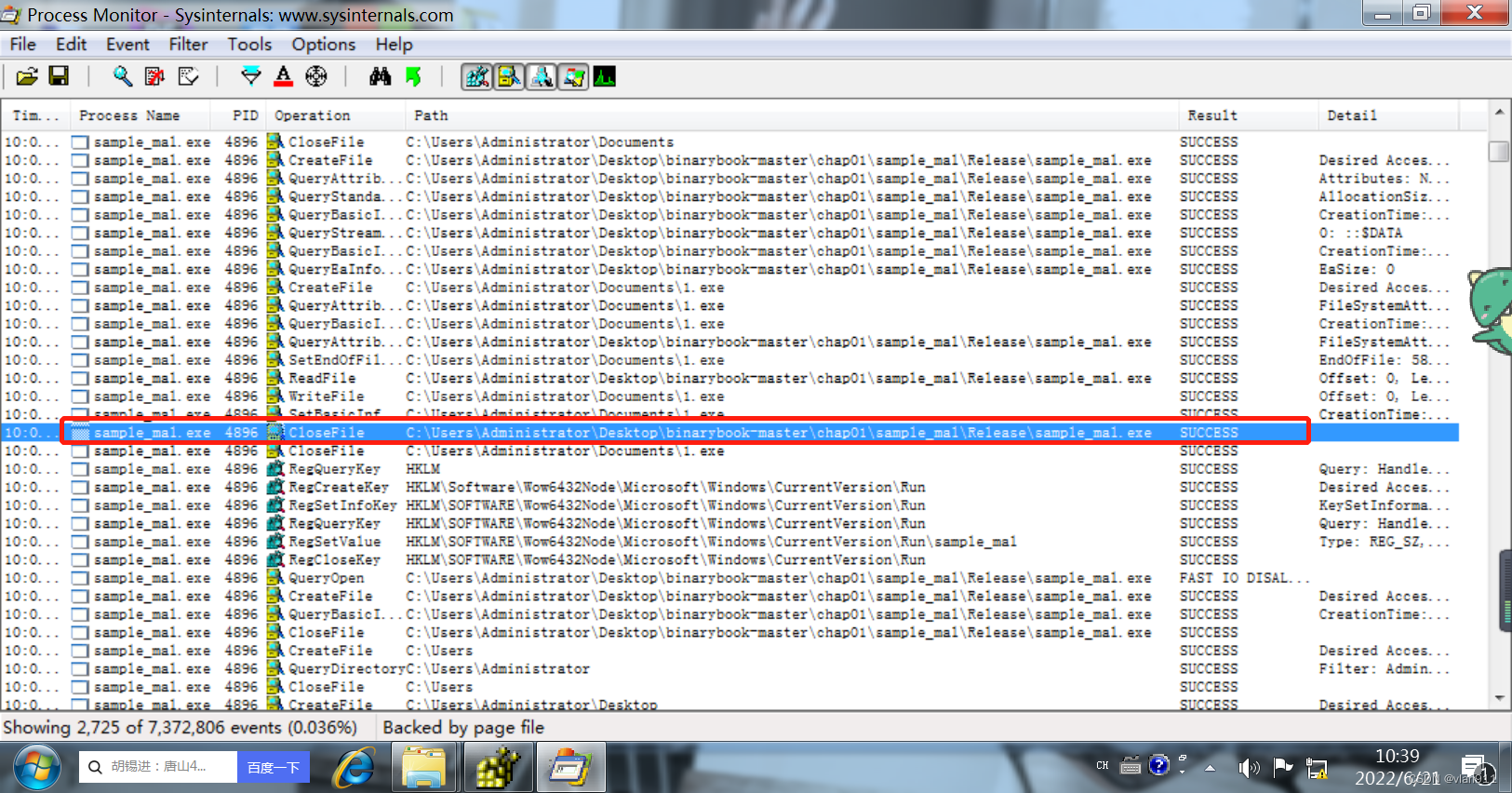

What a heaven reward for hard work ! What else did you find out ? That is, the registry has also been added with new content , The purpose is to restart the sample file after the calculator restarts , But this time it was rebooted 1.exe, That is, generated in the document 1.exe In fact, it is used in conjunction with the registry


Let's check the registry
win+r regedit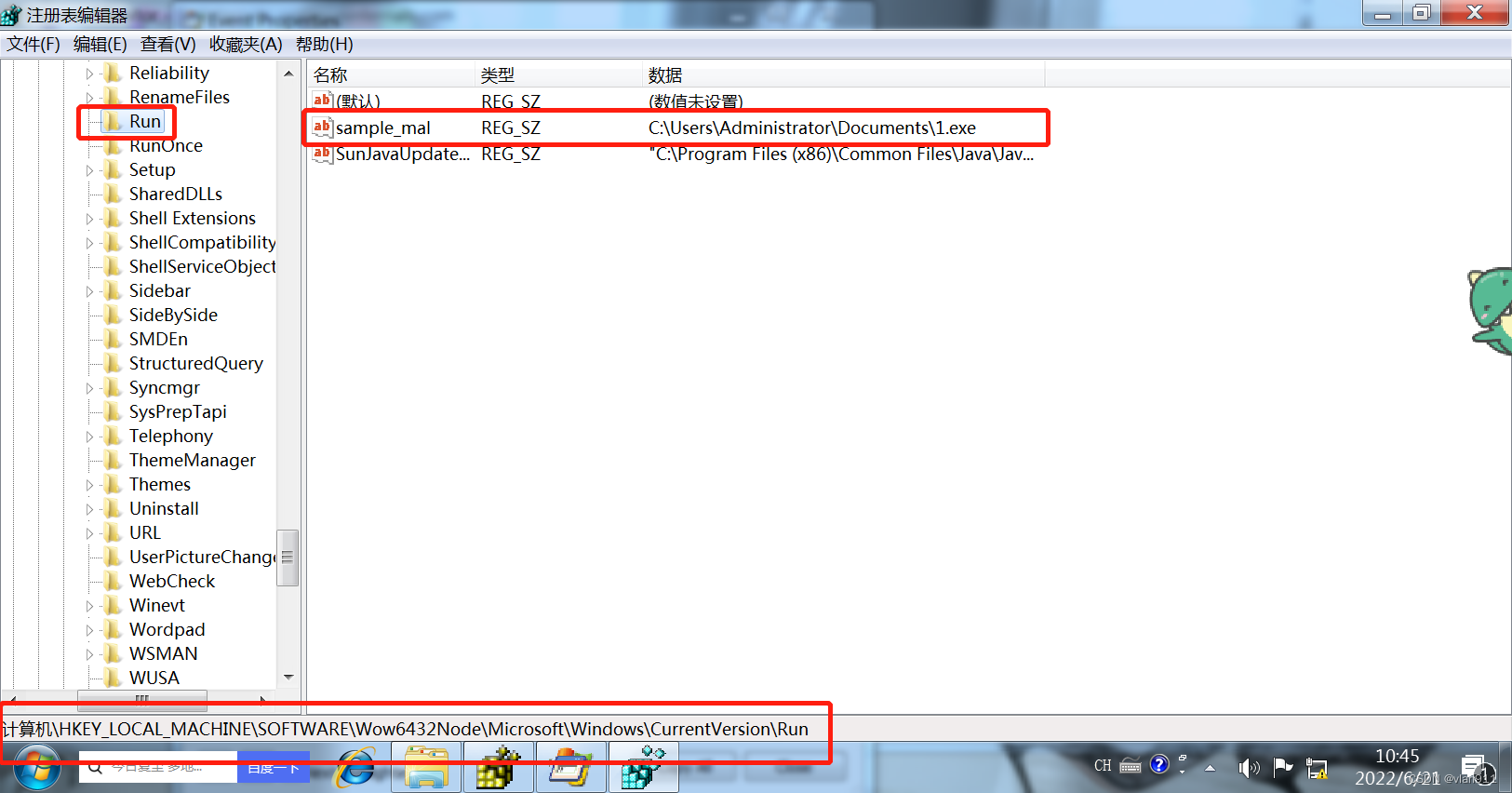
That's true , It should prove our conjecture ; But if we don't have this process Tools , So how do you know about the registry changes ? So we went back to the beginning –
RegShot( Registry comparison tool )
At this time, all the work that the sample should do is done , Let's go ahead and take a registry snapshot of the registry tool B
It's a cliche , Let's wait a moment , It will automatically pop up the results , Let's turn on html Documents will do 
It's just that , The registry change key displayed here is actually different from the actual one 
The author looked for it for a long time and couldn't find it , Still wondering why 
In fact, I made a slip of the tongue ,sample_mal.exe Samples and generated 0.exe、1.exe There's a difference , Their content is the same , But the function is a little different , That's it 0.exe and 1.exe There is an execution sequence ,0.exe Has a high priority ,0.exe After operation ,1.exe It doesn't work ; The second is that they will be removed after running , But it will not be copied again
We can look at nothing first , What happens if you restart the calculator 

At this time, the file in the folder is actually started 0.exe And removed , We restart the computer directly 
Ow , Miscalculation ,0.exe Be missing , however 1.exe After execution ,1.exe Deleted at the same time as the registry , But actually 0.exe Will be generated again , This is a doll , So we want to eliminate the impact , It needs to be removed at the same time 0.exe as well as 1.exe And clear the corresponding registry contents

Yes, of course , This is a later story , If we have a velvet sword , You can view the startup items directly 
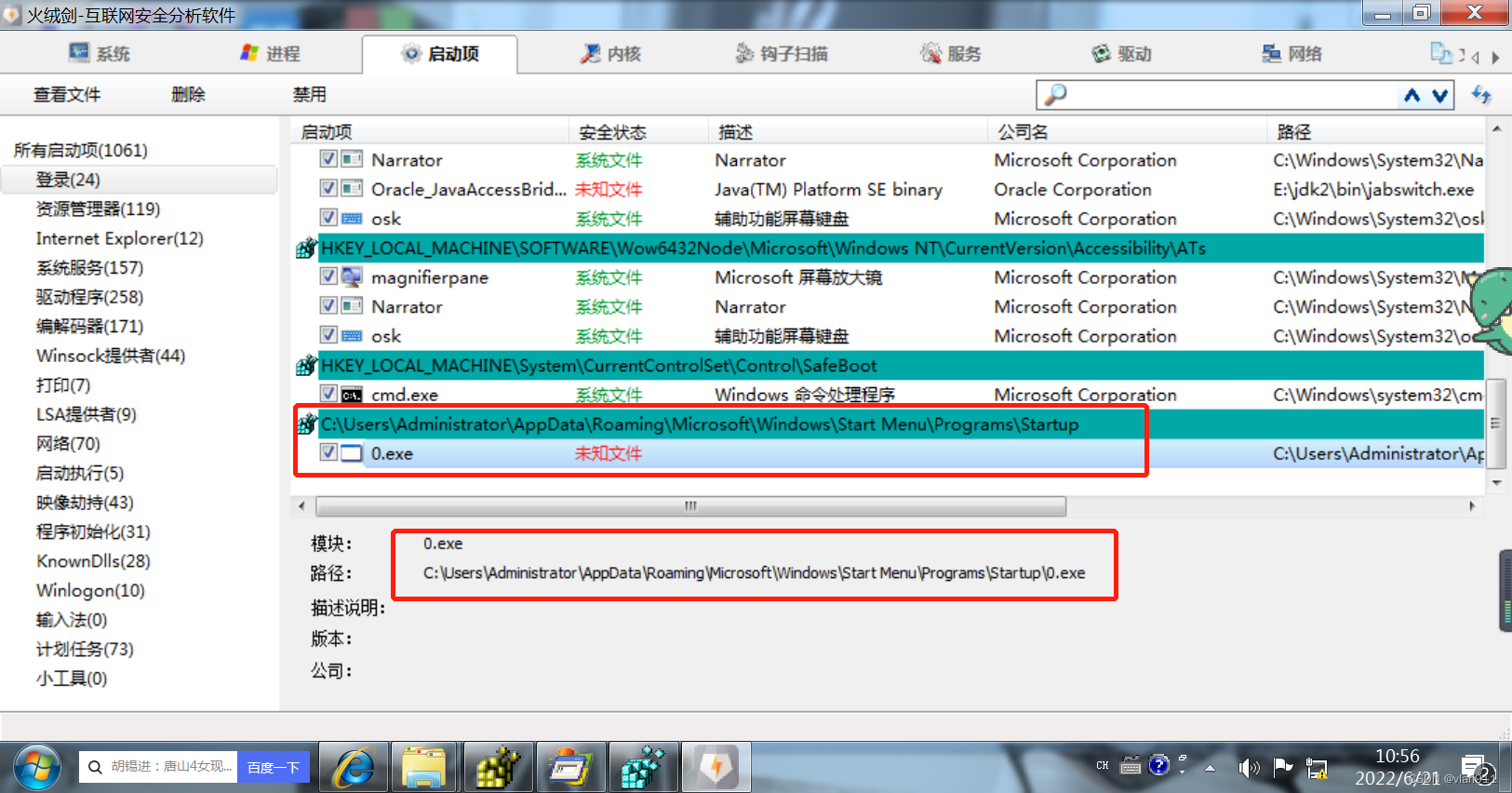
Conclusion :
No dice , Let's have fun
边栏推荐
- Record small knowledge points
- LabVIEW开发气体调节器
- Musk released humanoid robot. Why is AI significant to musk?
- Finereport (sail soft) handling the problem that the histogram data label is blocked
- How much do you know about the use value of WMS warehouse management system
- js的call()和apply()
- php封装curl发送get、post请求方法,并使用
- GBASE 8s存储过程流程控制
- GBASE 8s活锁、死锁问题的解决
- Package for gbase 8s
猜你喜欢

CTF_ Web: basic 12 questions WP of attack and defense world novice zone

95% of programmers fish here

Basic use of OBS browser+ browser

Gbase 8s overall architecture

深度学习——几种学习类型
CTF_ Web: Advanced questions of attack and defense world expert zone WP (15-18)
![[openwrt] we recommend a domestically developed version of openwrt, an introduction to istoreos. It is very easy to use. It is mainly optimized. It solves the problem of Sinicization.](/img/62/6152d5a30c92a340cb286c7b1cbc54.png)
[openwrt] we recommend a domestically developed version of openwrt, an introduction to istoreos. It is very easy to use. It is mainly optimized. It solves the problem of Sinicization.
![L'épée leetcode fait référence au chemin leetcode de l'offre II 091 pour peindre la maison [planification dynamique] heroding](/img/ad/69fce7cf064479a0ddd477fb935de2.png)
L'épée leetcode fait référence au chemin leetcode de l'offre II 091 pour peindre la maison [planification dynamique] heroding
CTF_ Web: Advanced questions of attack and defense world expert zone WP (1-4)
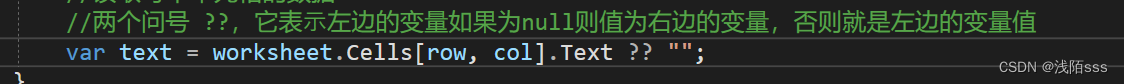
记录小知识点
随机推荐
小白学习MySQL - 统计的'投机取巧'
2021.6.14 notes
Vigilance against over range collection of privacy - ten mobile app violations
Easyrecovery15 very easy to use computer data recovery software
Cascading deletion of gbase 8s
php封装curl发送get、post请求方法,并使用
5 key indicators of SEO: ranking + traffic + session + length of stay + bounce rate
GBASE 8s 索引R树
kenlm
Failed to install redis interface
kenlm
Sourcetree pulls the code and prompts to fill in authentic, but the configuration cannot change the user
【LeetCode】22. bracket-generating
Record small knowledge points
CTF_ Web: deserialization learning notes (I) classes and objects in PHP
BSC smart contract dividend mainstream currency | including marketing wallet | deflation | reflow | dividend free token | available for direct deployment
关于TCP连接四次握手(或者叫四次挥手)的详细总结
GBASE 8s的隔离级别介绍
Doubts about judging the tinyint field type of MySQL
GBASE 8s活锁、死锁问题的解决