当前位置:网站首页>Arm GIC (V) how arm TrustZone supports security interrupt analysis notes.
Arm GIC (V) how arm TrustZone supports security interrupt analysis notes.
2022-07-01 12:14:00 【Galloping tortoise】
Catalog
The previous blog posts mainly combed GIC V3 Infrastructure , Interrupt the whole life cycle , And interruptions IRQ、FIQ Basic concepts . That's in ARM TrustZone How to support security interruption ?
ARM TrustZone A great advantage is that it is easy to manage peripherals , Management peripherals include : Peripheral access , Peripherals as Master How to issue secure access or non secure access , And how peripherals generate security interrupts , as well as CPU How to respond to this interrupt . Today we mainly introduce how to generate security interruption , There are three parts involved : Security peripherals ,GIC, as well as CPU.
CPU How to support secure interrupts ?
about CPU In itself, there is no perception of whether an interrupt is safe or unsafe ,CPU Only distinguish between IRQ, still FIQ. When CPU When receiving an interrupt, it will check whether the interrupt is masked according to the status register , for example PSTATE.DAIF, among I bit identification IRQ Whether it is Mask,F bit identification FIQ Whether it is Mask. If not Mask Words ,CPU This interrupt may be handled .
 Where to deal with this interrupt ? for example Armv8-A CPU It is divided into EL0,EL1,EL2,EL3,EL0 It does not handle interrupts ,EL1,EL2,EL3 Can handle interrupts , What are the details EL Handling interrupts , It is determined by the system register , for example SCR_EL3.FIQ and SCR_EL3.IRQ To mark the corresponding interrupt ,CPU Whether to directly enter EL3 The corresponding exception handler. however exception handler How to deal with this interrupt , That's about software , For example, processing interrupts directly , Or as a event To do other things , It's all controlled by software .
Where to deal with this interrupt ? for example Armv8-A CPU It is divided into EL0,EL1,EL2,EL3,EL0 It does not handle interrupts ,EL1,EL2,EL3 Can handle interrupts , What are the details EL Handling interrupts , It is determined by the system register , for example SCR_EL3.FIQ and SCR_EL3.IRQ To mark the corresponding interrupt ,CPU Whether to directly enter EL3 The corresponding exception handler. however exception handler How to deal with this interrupt , That's about software , For example, processing interrupts directly , Or as a event To do other things , It's all controlled by software .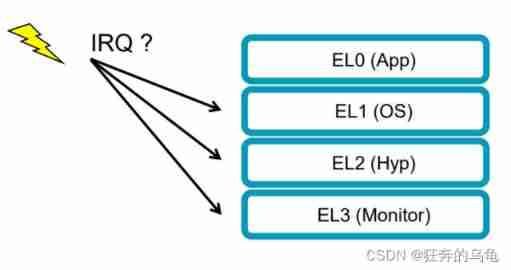 Visible for CPU For example, I don't know whether the interruption is safe or unsafe , Just do two things according to the type of interrupt received : Is it shielded ? If not shielded , Where to deal with it ? Currently in Armv7-A In the framework of ,FIQ When safety is interrupted , stay Armv8-A and GICv3 Architecture FIQ It does not mean security interruption , Indicates an interruption , At present EL May not handle , It needs to be handled in another place .
Visible for CPU For example, I don't know whether the interruption is safe or unsafe , Just do two things according to the type of interrupt received : Is it shielded ? If not shielded , Where to deal with it ? Currently in Armv7-A In the framework of ,FIQ When safety is interrupted , stay Armv8-A and GICv3 Architecture FIQ It does not mean security interruption , Indicates an interruption , At present EL May not handle , It needs to be handled in another place .
GIC How to support secure interrupts ?
GIC It is also evolving , Now the latest one should GICv4, from GICv1 Start supporting TrustZone,GICv2 relative GICv1 It mainly supports virtualization ,GICv3 relative GICv2 Big changes , Support Message base interrupt, Supported by CPU more , Some enhancements have also been made in terms of security ,GICv4 Enhanced virtualization .
GICv1 and GICv2 The main thing is to cooperate with Armv7-A Of CPU, How to support TrustZone What about ? combination Armv7-A The architecture of , Because I want to FIQ Reserved for security interruption , that GIC It is mainly realized by two points , The first is to divide safety Group,Group 0 Security interrupts can be generated IRQ perhaps FIQ,Group 1 Giving unsafe interrupts can only produce IRQ. The second one follows FIQ dependent registers All need security to configure , for example Group 0 Related configuration , Only CPU Configure in a safe state , Do this to achieve the purpose of safety .
 GICv3 The main thing is to cooperate with Armv8-A Of CPU, however Armv8-A relative Armv7-A Of TrustZone optimized ,Secure World It is divided into S-EL1(Trusted OS) and EL3(Secure Monitor) Are different privilege levels , If it looks like GICv2 That is divided into Group 0 and Group 1,Group 0 If you give S-EL1 and EL3 Use , In fact, it is not enough . So in GICv3 There are three hours Group,Group0,Secure Group 1 and non-secure Group 1, This makes it easy to distinguish , for example Group 0 to EL3 Use ,Secure Group 1 to S-EL1 use ,Non-secure Group 1 to EL1 To use , This division is very reasonable , But there is another problem , If there are three Group, and CPU There are only two signal lines on the side IRQ and FIQ, How to distinguish these three Group Well ? This is also where many developers tend to misunderstand , stay GICv3 Of GIC CPU interface with CPU Together , Also said GIC Distributor Send the interrupt to GIC CPU interface after ,CPU interface I know CPU In which EL, And whether it is safe or not ,CPU According to where the interrupt is Group, as well as CPU To decide whether to send IRQ, still FIQ, In this way, it is easy to distinguish three with two interrupt signals Group The problem of .
GICv3 The main thing is to cooperate with Armv8-A Of CPU, however Armv8-A relative Armv7-A Of TrustZone optimized ,Secure World It is divided into S-EL1(Trusted OS) and EL3(Secure Monitor) Are different privilege levels , If it looks like GICv2 That is divided into Group 0 and Group 1,Group 0 If you give S-EL1 and EL3 Use , In fact, it is not enough . So in GICv3 There are three hours Group,Group0,Secure Group 1 and non-secure Group 1, This makes it easy to distinguish , for example Group 0 to EL3 Use ,Secure Group 1 to S-EL1 use ,Non-secure Group 1 to EL1 To use , This division is very reasonable , But there is another problem , If there are three Group, and CPU There are only two signal lines on the side IRQ and FIQ, How to distinguish these three Group Well ? This is also where many developers tend to misunderstand , stay GICv3 Of GIC CPU interface with CPU Together , Also said GIC Distributor Send the interrupt to GIC CPU interface after ,CPU interface I know CPU In which EL, And whether it is safe or not ,CPU According to where the interrupt is Group, as well as CPU To decide whether to send IRQ, still FIQ, In this way, it is easy to distinguish three with two interrupt signals Group The problem of .
 But here's something to note FIQ No longer means security interruption , For example, for Non-secure Group 1 The interrupt , If CPU stay Secure world,CPU interface Just give it to CPU Send a FIQ, If CPU stay Non-secure world Just one IRQ.CPU Receiving this IRQ perhaps IFQ, Is it shielded , And where to deal with , Is mentioned above CPU System register , Follow GIC No problem .
But here's something to note FIQ No longer means security interruption , For example, for Non-secure Group 1 The interrupt , If CPU stay Secure world,CPU interface Just give it to CPU Send a FIQ, If CPU stay Non-secure world Just one IRQ.CPU Receiving this IRQ perhaps IFQ, Is it shielded , And where to deal with , Is mentioned above CPU System register , Follow GIC No problem .

How can peripherals support secure interrupts
stay GICv3 in , Interrupts are divided into SGI,PPI,SPI,LPI. among LPI Only Non-secure Group 1, In other words, only unsafe interrupts can be generated , The other three can be configured as Group 0,Non-secure Group 1 or Secure Group 1.SGI yes software generated interrupts, It is generally used for inter nuclear communication ,PPI yes private peripheral interrupt Mainly for CPU For private peripherals , Generally, security peripherals are made SPI,shared peripheral interrupt.
TF-A2.6.0 Source code analysis
void __init gicv3_distif_init(void)
{
unsigned int bitmap;
assert(gicv3_driver_data != NULL);
assert(gicv3_driver_data->gicd_base != 0U);
assert(IS_IN_EL3());
/* * Clear the "enable" bits for G0/G1S/G1NS interrupts before configuring * the ARE_S bit. The Distributor might generate a system error * otherwise. */
gicd_clr_ctlr(gicv3_driver_data->gicd_base,
CTLR_ENABLE_G0_BIT |
CTLR_ENABLE_G1S_BIT |
CTLR_ENABLE_G1NS_BIT,
RWP_TRUE); // The current interrupt is disabled, Clear grouping information , Reconfigure the current function
/* Set the ARE_S and ARE_NS bit now that interrupts have been disabled */
gicd_set_ctlr(gicv3_driver_data->gicd_base,
CTLR_ARE_S_BIT | CTLR_ARE_NS_BIT, RWP_TRUE); // Affinity routing can
/* Set the default attribute of all (E)SPIs */
/* Set up SPIs The default configuration ( Such as setting SPIs The default grouping is G1NS, * Interrupt priority 、 Interrupt trigger mode, level or edge trigger ) */
gicv3_spis_config_defaults(gicv3_driver_data->gicd_base);
/* To configure TF-A in gicv3_driver_data The list needs to be configured as a security interrupt Group SPI interrupt . *( For example, configure security interrupt grouping 0 perhaps 1、 Configure interrupt priority 、 Configure to route to CPU The way , As well as enabling disconnection ) */
bitmap = gicv3_secure_spis_config_props(
gicv3_driver_data->gicd_base,
gicv3_driver_data->interrupt_props,
gicv3_driver_data->interrupt_props_num);
/* Enable the secure (E)SPIs now that they have been configured */
gicd_set_ctlr(gicv3_driver_data->gicd_base, bitmap, RWP_TRUE); // Enable the above configured SPIs
}
unsigned int gicv3_secure_spis_config_props(uintptr_t gicd_base,
const interrupt_prop_t *interrupt_props,
unsigned int interrupt_props_num)
{
unsigned int i;
const interrupt_prop_t *current_prop;
unsigned long long gic_affinity_val;
unsigned int ctlr_enable = 0U;
/* Make sure there's a valid property array */
if (interrupt_props_num > 0U) {
assert(interrupt_props != NULL);
}
for (i = 0U; i < interrupt_props_num; i++) {
current_prop = &interrupt_props[i];
unsigned int intr_num = current_prop->intr_num;
/* Skip SGI, (E)PPI and LPI interrupts */
if (!IS_SPI(intr_num)) {
continue;
}
/* Configure this interrupt as a secure interrupt */
gicd_clr_igroupr(gicd_base, intr_num);
/* Configure this interrupt as G0 or a G1S interrupt */
assert((current_prop->intr_grp == INTR_GROUP0) ||
(current_prop->intr_grp == INTR_GROUP1S));
if (current_prop->intr_grp == INTR_GROUP1S) {
gicd_set_igrpmodr(gicd_base, intr_num);
ctlr_enable |= CTLR_ENABLE_G1S_BIT;
} else {
gicd_clr_igrpmodr(gicd_base, intr_num);
ctlr_enable |= CTLR_ENABLE_G0_BIT;
}
/* Set interrupt configuration */
gicd_set_icfgr(gicd_base, intr_num, current_prop->intr_cfg);
/* Set the priority of this interrupt */
gicd_set_ipriorityr(gicd_base, intr_num,
current_prop->intr_pri);
/* Target (E)SPIs to the primary CPU */
gic_affinity_val =
gicd_irouter_val_from_mpidr(read_mpidr(), 0U);
gicd_write_irouter(gicd_base, intr_num,
gic_affinity_val);
/* Enable this interrupt */
gicd_set_isenabler(gicd_base, intr_num);
}
return ctlr_enable;
}
边栏推荐
- 栈的应用——括号匹配问题
- Theoretical basis of graph
- Mysql database knowledge collation
- Summary of JFrame knowledge points 1
- Onenet Internet of things platform - mqtt product devices send messages to message queues MQ
- Want to ask, is there a discount for opening a securities account? Is it safe to open a mobile account?
- How to use opcache, an optimization acceleration component of PHP
- The Missing Semester
- [speech signal processing] 3 speech signal visualization -- prosody
- Golang根据参数引入相应配置文件的实现方式
猜你喜欢

Acly and metabolic diseases
![Wechat applet reports an error: [rendering layer network layer error] pages/main/main Local resource pictures in wxss cannot be obtained through wxss. You can use network pictures, Base64, or < image/](/img/6a/fe448ca635690bc5260436546b588e.jpg)
Wechat applet reports an error: [rendering layer network layer error] pages/main/main Local resource pictures in wxss cannot be obtained through wxss. You can use network pictures, Base64, or < image/

Summary of JFrame knowledge points 1

Istio, ebpf and rsocket Broker: in depth study of service grid

比特熊直播间一周年,英雄集结令!邀你来合影!

Machine learning - Data Science Library - day two

C serialization simple experiment
![[Yunju entrepreneurial foundation notes] Chapter 7 Entrepreneurial Resource test 2](/img/2b/f42ac6745eb126254af62ad5217f70.jpg)
[Yunju entrepreneurial foundation notes] Chapter 7 Entrepreneurial Resource test 2

谈思生物直播—GENOVIS张洪妍抗体特异性酶切技术助力抗体药物结构表征

Switch basic experiment
随机推荐
[datawhale202206] pytorch recommendation system: recall model DSSM & youtubednn
Golang根据参数引入相应配置文件的实现方式
GID:旷视提出全方位的检测模型知识蒸馏 | CVPR 2021
CPU 上下文切换的机制和类型 (CPU Context Switch)
241. Design priority for operational expressions: DFS application questions
谈思生物直播—GENOVIS张洪妍抗体特异性酶切技术助力抗体药物结构表征
How does Nike dominate the list all the year round? Here comes the answer to the latest financial report
Interpretation of R & D effectiveness measurement framework
Leetcode force buckle (Sword finger offer 31-35) 31 Stack push pop-up sequence 32i II. 3. Print binary tree from top to bottom 33 Post order traversal sequence 34 of binary search tree The path with a
91. (cesium chapter) cesium rocket launch simulation
Onenet Internet of things platform - mqtts product equipment connected to the platform
Computer graduation project asp Net attendance management system vs developing SQLSERVER database web structure c programming computer web page source code project
The Missing Semester
Summary of JFrame knowledge points 2
Self organization is the two-way rush of managers and members
How to understand the developed query statements
【datawhale202206】pyTorch推荐系统:精排模型 DeepFM&DIN
C # dependency injection (straight to the point) will be explained as soon as you see the series
【datawhale202206】pyTorch推荐系统:召回模型 DSSM&YoutubeDNN
[Yu Yue education] financial management reference materials of Ningbo University of Finance and Economics