当前位置:网站首页>Introduction to security encryption
Introduction to security encryption
2022-06-21 21:35:00 【JH_ Cao】
Catalog
Symmetric encryption


AES The key length of is 128、192、256 There are three kinds of . In symmetric encryption algorithm , For the moment AES Is safe . But there is a problem , How to distribute the key ? Transmission in the Internet environment , Keys are easy to steal . Generally speaking, there is 3 Key distribution methods :
1、 Private shared key
2、 Key distribution center send
3、 Asymmetric encryption To encrypt Symmetric encryption key
Asymmetric encryption
The general asymmetric encryption algorithm uses RSA Algorithm Generate key pair ( Public key pub_key、 Private key pri_key) Public keys are generally public , The private key is saved by yourself , No one else knows Characteristic is :
1、 Public key encrypted plaintext information , Only the corresponding private key can be decrypted ( For typical asymmetric encryption )
2、 The plaintext information encrypted by the private key , Only the corresponding public key can be decrypted ( For digital signature , I'll tell you more about it later )

certificate
1、 for instance : I have a driver's license in my life , Id card , Diploma, etc , These are issued by the authority , It can be used as proof of legitimacy .
2、 The public key may be counterfeited , In the process of using asymmetric encryption , Transfer the public key , There is still a threat to the security of asymmetric encryption .
3、 To address this threat , An authority is required to issue a certificate on whether the public key is legal
4、 Generally, these institutions are internationally recognized , Or some companies need to pay for certificates

Mixed encryption
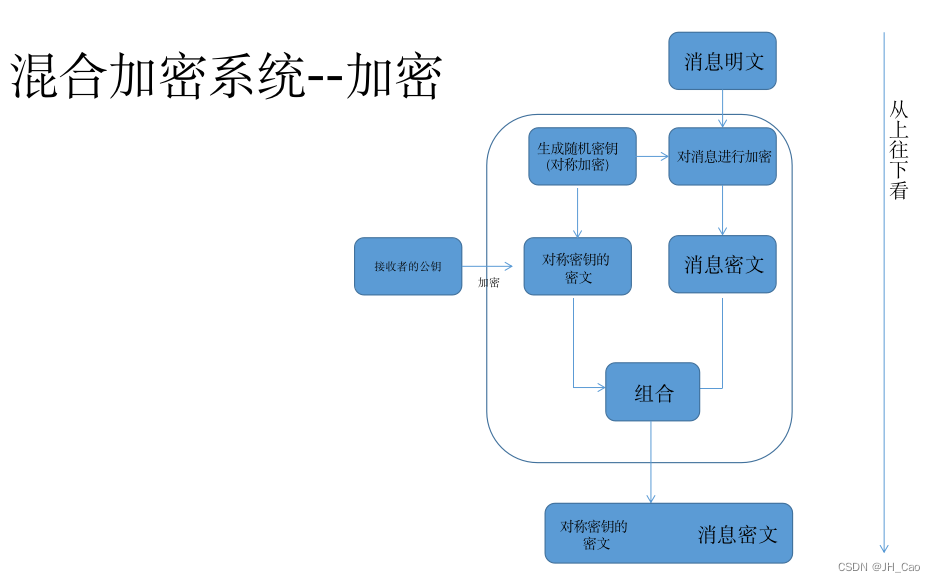

digital signature
1、 Signatures in life , Such as signing a labor contract 、 Leave slip signed by the leader , The function is to show that it is operated by myself
2、 Empathy , Digital signatures on the Internet , It is the proof that the message was sent personally , Not forged or tampered with

边栏推荐
- Cylinder function block (FB) of PLC function block series
- 天齐锂业通过聆讯:单季净利33亿 蒋卫平夫妇身价超500亿
- 30 groups of outdoor travel vlog record LUTS color matching preset moody travel LUTS
- matplotlib plt.subplots()详解
- ARP协议及ARP攻击
- MySQL数据库---存储引擎
- Mysql database - storage engine
- 晶合集成通过注册:拟募资95亿 合肥建投与美的是股东
- OpenJudge NOI 1.13 45:十进制到八进制
- 拖延患者自救指南|“我有不拖延的100种借口,却不愿意跨出一步”
猜你喜欢

Citus 11 for Postgres 完全开源,可从任何节点查询(Citus 官方博客)

ASP. Net core creates razor page and uploads multiple files (buffer mode)
用keil 5编译C51时出现定义未使用的处理方法

集群一---LVS负载均衡集群NAT模式及LVS负载均衡实战部署
![[applet] realize applet and background ASP through request Net data JSON transmission (post protocol text + code)](/img/e7/1a270d2aa03f38426bc57bd0ee00b6.png)
[applet] realize applet and background ASP through request Net data JSON transmission (post protocol text + code)

Implementation principle of global load balancing

科研漫畫 | 看圖可以學腦電,來試試?
![[Internet of things development] punctual atom STM32 warship v3+ smart cloud aiot+app control](/img/78/90f7eca3ca9504a7f8b232e577ae03.png)
[Internet of things development] punctual atom STM32 warship v3+ smart cloud aiot+app control

【物联网开发】正点原子STM32战舰v3+机智云AIoT+APP控制

js的对象操作(与c的对象比较简单的多)
随机推荐
如何有序协同和管理多个研发项目?
Lvs+keepalived high availability cluster deployment
Delaying patient self-help guide | "I have 100 excuses for not delaying, but I am not willing to take a step"
杰理之开启四声道打开 EQ 后播歌卡顿问题【篇】
Installing component and package libraries in Ad
Number of free radical electrons and valence electrons of rdkit | molecule
科研漫畫 | 看圖可以學腦電,來試試?
J - Count the string HDU - 3336 (KMP)
Definition of unused processing methods when compiling C51 with keil 5
Go language self-study series | golang standard library encoding/xml
ARP协议及ARP攻击
Dedecms dream weaving background system adds its own column menu
Xmind8 最新破解教程(亲测有用)
[applet] realize applet and background ASP through request Net data JSON transmission (post protocol text + code)
基于接口划分VLAN:静态VLAN【未完善】
混合云演习常见案例
ASP. Net core creates razor page and uploads multiple files (buffer mode)
matplotlib plt.subplots()详解
js的对象操作(与c的对象比较简单的多)
Maximum weight matching of bipartite graph (build a board and stick to two questions)