当前位置:网站首页>Remote access and control - SSH Remote Management and TCP wrappers access control
Remote access and control - SSH Remote Management and TCP wrappers access control
2022-06-22 22:40:00 【Be the best Messi】
One 、SSH Remote management
1、 Definition
SSH(Secure Shell ) It's a secure channel protocol , It is mainly used to realize the remote login of character interface 、 Remote replication and other functions .
SSH The protocol encrypts the data transmission between the two sides , It includes the user password entered when the user logs in . therefore SSH The protocol has good security .
2、 advantage

3、 Client and server
client :Putty、Xshell、CRT
Server side :OpenSSH
- OpenSSH It's the realization of SSH Open source software agreement for the project , Applicable to all kinds of UNIX、Linux operating system .
- CentOS 7 The system is installed by default openssh Related packages , And sshd Service added as bootstrap .
4、SSH Service opening 、 Port number and configuration file
SSH Service opening
- perform “systemctl start sshd” Command to start sshd service
SSH The port number of the service - sshd The default port number used by the service is 22
SSH The configuration file for the service - sshd_config The configuration file is for the server
- ssh_config It's a profile for the client
Two 、 To configure OpenSSH Server side
1、 Configuration file common settings options




2、AllowUsers and DenyUsers
AllowUsers and DenyUsers Can't be used at the same time . There will be conflict



3、 ... and 、 Use SSH Client program
1、SSH Remote login
ssh [ Options ] [email protected]
When a user logs in for the first time SSH Server time , Must accept the server from ECDSA Secret key ( Enter... At the prompt "yes") Before you can continue to verify . The received secret key information will be saved to ~/.ssh/known_hosts In file , After successful password verification , You can log in to the command environment of the target server .
Options explain
-1 Compulsory use ssh Protocol version 1
-2 Compulsory use ssh Protocol version 2
-4 Compulsory use IPv4 Address
-6 Compulsory use IPv6 Address
-A Turn on the authentication agent connection forwarding function
-a Turn off the authentication agent connection forwarding function
-b Use the address specified by this machine as the source of the peer-to-peer connection IP Address
-C Request to compress all data
-F Appoint ssh The configuration file for the command , The default configuration file is “/etc/ssh/ssh_config”
-f The background to perform ssh Instructions
-g Allow the remote host to connect to the forwarding port of this machine
-i Specify the identity file ( Private key file )
-l Specify the login user name to connect to the remote server
-N Do not execute remote instructions
-o Specify configuration options
-p Specify the port on the remote server
-q silent mode , All warning and diagnostic messages are disabled
-X Turn on X11 Forward capability
-x close X11 Forward capability
-y Turn on trust X11 Forward capability
2、SCP Remote Replication
①、 Downlink replication
scp -r [email protected]:/etc/ /root/
Copy 192.168.0.5 The host /etc All contents in the directory are transferred to this computer /root Directory
②、 Uplink replication
scp -r /etc/ [email protected]:/root
Copy the of this machine /etc Contents in directory to 192.168.0.6 The host /root Under the table of contents
3、sftp Security FTP
Because of the use of encryption / Decryption technology , So the transmission efficiency is higher than the ordinary FTP Be low , But it's more secure .
sftp [email protected]
[email protected]'s password:
Connected to 192.168.226.20.
sftp> ls
sftp> get file name # Download the file
sftp> put file name # Upload files
sftp> exit # sign out


Four 、sshd The service supports two authentication methods
1、 Password authentication
Login name of the local system user in the server 、 Password verification . Simple and convenient , But it could be brutally cracked
2、 Key pair verification
Matching key information is required to pass the verification . Usually create a pair of key files in the client first ( Public key 、 Private key ), Then put the public key file in the specified location in the server . When logging in remotely , The system will use the public key 、 The private key is encrypted / Decryption Association verification . Can enhance security , No login and interaction .
When password verification 、 When key pair verification is enabled , The server will take precedence over key pair Authentication . The verification mode can be set according to the actual situation .
vim /etc/ssh/sshd_config
PasswordAuthentication yes # Enable password authentication
PubkeyAuthentication yes # Enable key pair validation
AuthorizedKeysFile .ssh/authorized_keys # Specify the public key library file

①、 Create a secret key pair on the client
adopt ssh-keygen Tool to create a key pair file for the current user . The available encryption algorithms are RSA、ECDSA or DSA etc. (ssh-keygen Ordered “-t” Option to specify the type of algorithm ).
useradd admin
echo "123456" | passwd --stdin admin
su - admin
ssh-keygen -t rsa
Generating public/private ecdsa key pair.
Enter file in which to save the key (/home/ljm/.ssh/id_rsa): # Specify the private key location , Press enter to use the default location
Created directory '/home/admin/.ssh'. # Generated private key 、 The public key file is stored in the hidden directory in the host directory by default .ssh/ Next
Enter passphrase (empty for no passphrase): # Set the password for the private key
Enter same passphrase again: # Confirm input
ls -l .ssh/id_admin* #id_ecdsa It's a private key file , Permissions default to 600;id_ecdsa.pub It's a public key file , To provide to SSH The server

②、 Upload the public key file to the server
scp ~/.ssh/id_r
sa.pub [email protected]:/opt
or
This method can be used directly on the server /home/admin/.ssh/ The public key text is imported into the directory
cd ~/.ssh/
ssh-copy-id -i id_rsa.pub [email protected]

③、 Import the public key text into the server ( The second one )
mkdir .ssh
ls -A
cat /id_rsa.pub >> .ssh/authorized_keys
cat authorized_keys

④、 Use secret key pair authentication on the client
ssh [email protected]
@192.168.226.20's password: # Enter the password for the private key
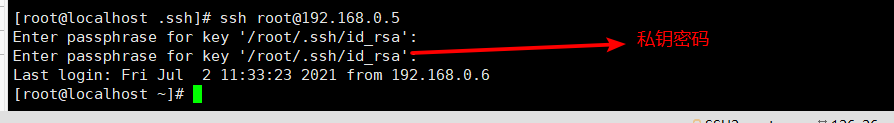
⑤、 Set up on the client ssh Agent function , Realize interactive login free
ssh-agent bash
ssh-add
Enter passphrass for /root/.ssh/id_rsa: # Enter the password for the private key
[email protected]

5、 ... and 、TCP Wrappers Access control

TCP Wrappers take TCP Service program “ The parcel ” get up , Monitor for TCP The port of the server , Added a security detection process , External connection requests must first pass this layer of security detection , Access to the real service program is only possible with permission .
majority Linux Distribution version ,TCP Wrappers It's a default feature .
rpm -q tcp_wrappers
Query whether to install
1、 There are two ways to implement the protection mechanism
Use it directly tcpd Programs protect other services , Need to run tcpd Program .
Called by other network service programs libwrap.so.* Link library , No need to run tcpd Program . This method is more widely used , And more efficient .
①、 Viewing program libwrap.so.* Link library ——ldd command
ldd [ Parameters ] [ file ]
Description of common parameters -v Detail mode , Print all relevant information
-u Print unused direct dependencies
-d Perform relocation and report any missing objects
-r Perform relocation of data objects and functions , And report any missing objects and functions
– -help Display help information
The file needs to be written with an absolute path
When we don't know the absolute path of the file , have access to which Command query
You can also use two commands together :ldd $(which sshd)
2、TCP Wrappers Access policy for
TCP Wrappers The protection objects of the mechanism are various network service programs , Access control for the client address of the access service .
The corresponding two policy files are /etc/hosts.allow and /etc/hosts.deny, It is used to set the allow and reject policies respectively .

3、TCP Wrappers The basic principles of the mechanism
First check /etc/hosts.allow file , If you find a matching strategy , Access to ;
Otherwise continue to check /etc/hosts.deny file , If you find a matching strategy , Access denied ;
If you check the two files above and find no matching policy , Access to .
Allow all , Refuse individual
Just in /etc/hosts.deny Add the corresponding rejection policy to the file
Allow individual , Reject all
In addition to the /etc/hosts.allow In addition to the allowed policy , Still need to be in /etc/hosts.deny Set in file “ALL:ALL” The rejection strategy of .
4、 Example
Just hope from IP The address is 12.0.0.1 The host of or located in 192.168.80.0/24 Host access of network segment sshd service , Other addresses are rejected .
vi /etc/hosts.allow
sshd:12.0.0.1,192.168.80.*
vi /etc/hosts.deny
sshd:ALL
Catalog
4、SSH Service opening 、 Port number and configuration file
Two 、 To configure OpenSSH Server side
1、 Configuration file common settings options
3、 ... and 、 Use SSH Client program
Four 、sshd The service supports two authentication methods
1、 There are two ways to implement the protection mechanism
2、TCP Wrappers Access policy for
3、TCP Wrappers The basic principles of the mechanism
边栏推荐
- Eureka service registration and discovery
- Solve the problem that MySQL in phpstudy cannot be started and conflicts with locally installed MySQL
- June25,2022 PMP Exam clearance manual-6
- 【持续更新中...】2021年全国大学生电子设计大赛 (三)匿名四轴拓空者飞控系统设计解读
- Developing salary management system based on C language course paper + source code and executable EXE file
- Mysql database DML operation exercise
- SPA项目开发之首页导航+左侧菜单
- 组合总数[标准回溯 + 回溯技巧--降低栈深度]
- [path planning] week 1: hodgepodge
- KDD'22 | 阿里: 基于EE探索的精排CTR预估
猜你喜欢

Note: by the end of 2022, the printing entrance of Guangdong second-class cost engineer's admission card has been opened
【知乎知识主推荐】 无人机中的城堡- 专注于无人机在不同技术领域的应用

KDD'22 | 阿里: 基于EE探索的精排CTR预估

CyCa children's physique etiquette Shenzhen training results assessment successfully concluded
【ROS 入门学习 】CmakeList.txt 和Packages.xml释义

【几何法视觉】4.2 分段线性变换

Self service library system Tkinter interface and openpyxl form comprehensive design case

SPA项目开发之登录注册
![Next permutation [give play to subjective initiative to discover laws]](/img/bb/262e1a21e4babb8d221d737ced3bcc.png)
Next permutation [give play to subjective initiative to discover laws]

注意|24日截止 2022年广东二级造价工程师准考证打印入口开通
随机推荐
322. change exchange
Shell (34): time
CyCa children's physique etiquette Shenzhen training results assessment successfully concluded
322.零钱兑换
CYCA少儿形体礼仪 深圳市培训成果考核圆满落幕
SPA项目开发之动态树+数据表格+分页
Several soapdatamodules on Delphi soap WebService server side
Which is the higher priority of V-IF or V-for?
Las point cloud create mesh
redis 报错解决与常用配置
R language data preprocessing, converting type variables into factor variables, converting data sets into H2O format, and dividing data sets (training set, test set, verification set)
Why do you think it is common for Chinese people to earn more than 10000 yuan a month?
Cvpr2022 𞓜 feature decoupling learning and dynamic fusion for re captured images
R language builds a binary classification model based on H2O package: using H2O GLM constructs regularized logistic regression model and uses H2O AUC value of AUC calculation model
腾讯云上传文件出现的问题:in a frame because it set ‘X-Frame-Options‘ to ‘deny‘.
British teddy bear joins the pubg mobile game
pycharm 配置远程连接服务器开发环境
June25,2022 PMP Exam clearance manual-6
Mysql8 installation and environment configuration
CSV add a new column