当前位置:网站首页>Set up SSO based on SAML 2.0 in salesforce and enable JIT user provisioning (between SF orgs / between SF org and experience cloud / other IDPs)
Set up SSO based on SAML 2.0 in salesforce and enable JIT user provisioning (between SF orgs / between SF org and experience cloud / other IDPs)
2022-07-27 18:11:00 【sf_ wilson】
【 Preface 】: It was successfully built earlier SSO Demo All are SF Org As SP,Azure AD / LinkedIn And other third-party services as IdP, Until now, I happen to meet new customers who want to implement SSO, Thinking of accumulating practical experience is happy , After a round of negotiation, I realized that it actually existed Two challenges :
#1. The client's Azure yes On-Premise Of ADFS, The previous successful experience is Azure AD Cloud service ;
#2. Combined with the project background , We Need to put Experience Cloud As SP, Before, it was SF Org As SP;
At that time, we need to have a round first POC, The initialized workflow needs to run first , For example, what input elements do we need from customers , What we need to output later . Based on this background , So I collected two official documents to hold Buddha's feet temporarily :

After reading the document, I didn't find SF Experience Community How to communicate with local Azure Conduct SSO Direct answer to configuration , But because they are all based on SAML 2.0 Agreed , Considering that the configuration of the other side is still a black box for me , The top priority now is to SF As SP and IdP To build SF Org between , Further more SF And Experience Cloud Between the SSO technological process . therefore This article will be based on the final effect shown in the figure below , Summarize the construction process and try to further extend the topic .

【 Basic knowledge of 】:
SSO What is it? ?
Single sign-on (SSO) is an authentication method that enables users to access multiple applications with one login and one set of credentials.
IdP And SP What is it? ?
The system that authenticates users is called an identity provider. The system that trusts the identity provider for authentication is called the service provider.
about SSO SF Two protocols supported :Salesforce supports SSO with SAML and OpenID Connect. For exams , Support self-registration The use of JIT Yes. SAML SSO,OpenID Connect Auth, Provider The corresponding is Registration Handler.
What is? SAML?
SAML is an open-standard authentication protocol that Salesforce uses for single sign-on (SSO) into a Salesforce org from a third-party identity provider. You can also use SAML to automatically create user accounts with Just-in-Time (JIT) user provisioning.
SAML How about the authentication mechanism ?
When a user tries to log in, your identity provider sends SAML assertions containing facts about the user to Salesforce. Salesforce receives the assertion, validates it against your Salesforce configuration, and allows the user to access your org.
【 Construction process 】: With SF Org Room construction SSO For example
#1. Both: stay SP And IdP Enable My Domain;
#2. IdP: stay IdP Enable Identity Provider;
#3. IdP: stay IdP Download the certificate and Metadata Or copy Salesforce Identity Of URL As an input to the next step ;
#4. SP: find Single Sign-On Settings term , After entering, there are 3 Ways of planting ( Manual New, Import the downloaded in the previous step from the local xml file , Copied from URL Import configuration items from ) To configure SSO Settings;
#5. SP: Upload IdP certificate , Suggest SAML Identity Type choice Federation ID ( If it needs to be enabled later JIT User Provisioning This type must ), And save ;
#6. SP: from SSO Copy the details page of 3 Sample information :Entity ID, Issuer And Endpoints On display Login URL For subsequent use ;
#7. SP: It opens at My Domain, stay Authentication Configuration At panel Check the match just now Authentication Service;
#8. IdP: by SP Create the corresponding Connected App, among Entity ID, Issuer yes #6 A copy of ,Start URL And ACR Fill in the #6 In the corresponding position of Login URL;
#9. test - Exit for two SF Orgs, visit SP Of login page , Then it will be in the account secret Form I can see SSO The icon ;
#10. misarrangement - Use SAML tracer Google plug-in monitoring SSO Time redirection process and XML Assert Parameter , If there is a problem, you can copy SAML Of Response XML And go to SP Of SSO Configuration details page use SAML Assertion Validator Validation error / Of course, you can also use Login History and Identity Provider Event Log Positioning error ;

matters needing attention :
1. One Org Please make sure Issuer And Entity ID The strings put together are unique ;
2. stay SF Intersexual SSO(SF Org between / Experience Cloud between ), among Identity Provider Information is public ,SSO Settings And Connected App It needs to be created accordingly ; Explain with foreword legend ,SPs In the same Org, deng Salesforce With Deng Experience Cloud It's two different domain, So in SP Created in SSO Settings when , You need to use... Separately IdP Two sets of xml Information :

After creation SP Medium SSO Settings And IdP Medium Connected App The corresponding are as follows :

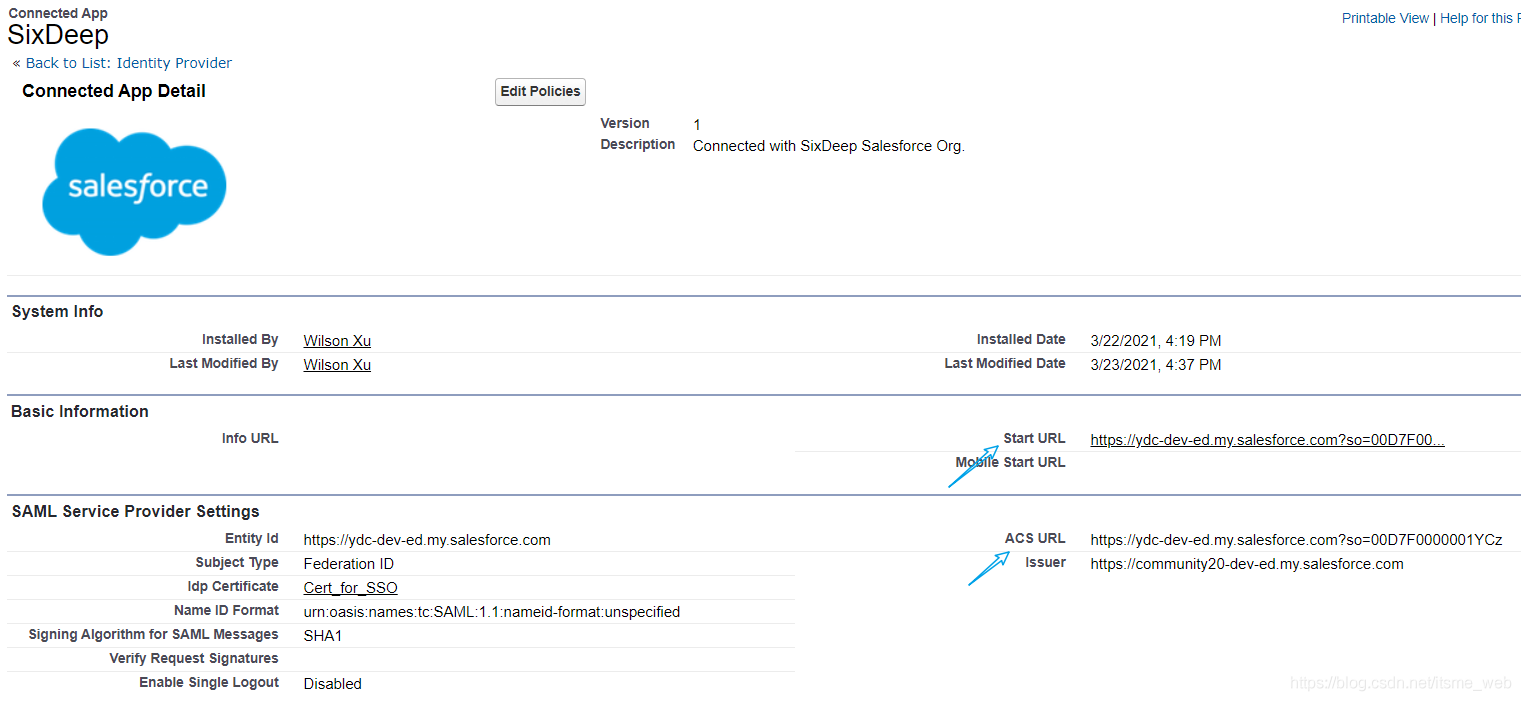
chart 1. SF Org between


chart 2. Experience Cloud between
It is not difficult for you to see in the figure above 2 The marks correspond to My Domain And Experience Cloud Of siteURL
3. by Experience Cloud After construction SSO, Don't forget to go Workspaces -> Administration -> Login & Registration Tick it , Same as 【 Construction process 】#7
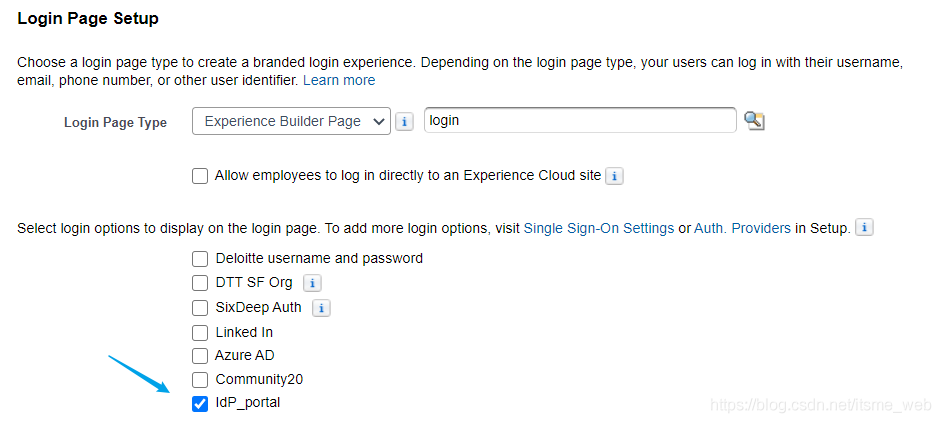
4. stay IdP Stay logged in , In order to achieve Click on the link skip fall Login Form Jump to the SP in , Please make sure SSO Only one authorization service of is enabled , Here's the picture :
【 Other topics 】:
Certificate management best practices :
Build in practice SSO when ,IdP Often managed by the client , Because the certificate has an expiration date , If there are different certificates in the certificate configuration phase , When the certificate expires, the prompt message will not tell us which certificate has expired , Therefore, unified certificate will be a good choice .
stay SF Room construction SSO when ,IdP Medium Identity Provider And Connected App Need public 1 A certificate ,SSO Settings need >=2 A certificate ( One from IdP, One is generally self signed , And assertion decryption may need ).
Span Org Exchange certificates at SF Of Certificate and Key Management There is a call. keystore The concept of , Unified password is required for export and import , The following is an example of import :

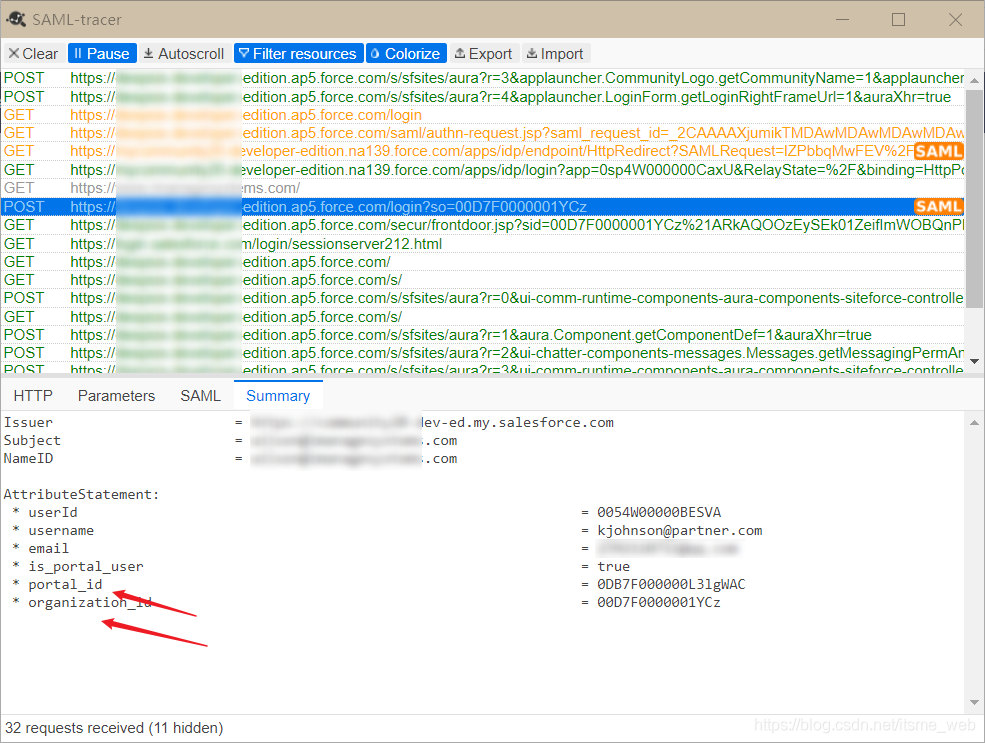
Connected App Custom attribute Application :

Used to pass parameters , Use after designation SAML tracer You can see , Here's the picture :
【 Problems and solutions 】:
The problem belongs to :A. Azure AD As IdP,Experience Cloud As SP Single sign on
Q1、 Use the following chart Community Login Page When performing single sign on

An error is as follows :AADSTS50105: The signed in user {email address} is not assigned to a role for the application '{tanent id}'(SixDeep-Salesforce).
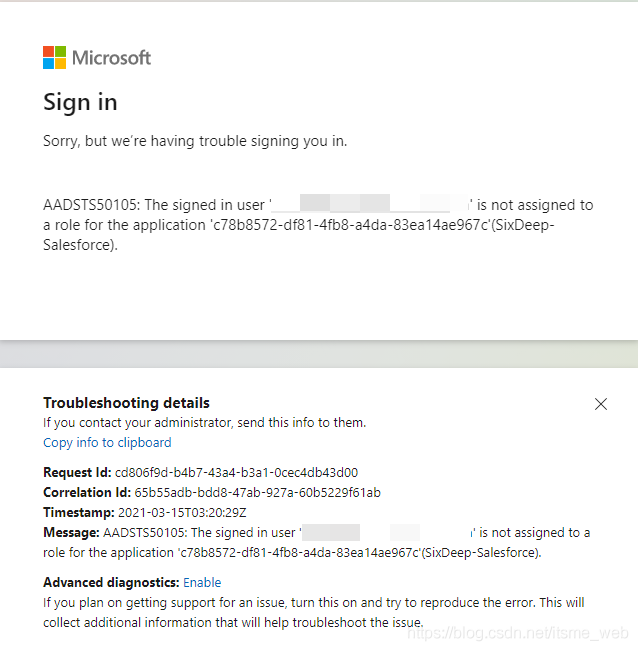
A1、 Sign in Azure Portal, stay Azure Services Click Azure Active Directory, Get into tenant Then click left navigation Enterprise applications, Click on Salesforce Click on the left navigation after application Properties Reach the target page , take User assignment required? Check and save the configuration .

Be careful : Even for newly invited user Allocated Azure AD Of role, Nor can it solve the above problems .
Q2、 At single sign on , An error is as follows :AADSTS50011: The reply URL specified in the request does not match the reply URLs configured for the application: 'https://ydc-dev-ed.my.salesforce.com'.

A2、 If you want this Azure AD At the same time as SF and Community Of IdP, Please classify the two login url Configure in Azure End .
Q3、 If there are more than one SSO Settings, How to get specific ssoUrl for web?
A3、 Method 1 :AuthConfiguration Class
String startUrl = '/';
String communityUrl = 'https://uat-my-community.cs75.force.com';
String samlId = '0LE0w0000008P6P'; //This is the configId
String ssoUrl = Auth.AuthConfiguration.getSamlSsoUrl(communityUrl, startUrl, samlId);
System.debug(LoggingLevel.INFO, '*** ssoUrl: ' + ssoUrl);
https://uat-my-community.cs75.force.com/saml/authn-request.jsp?saml_request_id=_2CAAAAXpm0jApMDAwMDAwMDAwMDAwMDAwAAAA6NgdrdxH9-XZDeMhVf5NA0dt7ZIhLaCuGR--mVXpbfRc0WOaXY2XATixsA1cGKSEEc-VqbSuJhvHObhO6vyCCu76s1g5-ZSOqqBF7rBrq6nMqVkywECPr25uskPz7wgEBOCD3rNkCcRhc2ZFt_aLfnT8Oj0pPT0n_CGRynJ5qyBW7B4BXDli2UrYsvTPAL7qk-Tnfm7nPV0YtlOAGAM7mkSaC8UA6qvgYvXV5mgSChT1Hk7HlRX_wZFpVbI_BHVe-A&saml_acs=https://uat-my-community.cs75.force.com/login&saml_binding_type=HttpRedirect&Issuer=https://mydomain--uat.my.salesforce.com&samlSsoConfig=0LE0w0000008P6P&RelayState=/Method 2 : from Auth Endpoint (https://hostname/.well-known/auth-configuration) analysis
{
"OrgId": "00D0T0000008lYN",
"Url": "https://uat-my-community.cs112.force.com",
"MobileSDK": {
"UseiOSNativeBrowserForAuthentication": false,
"UseAndroidNativeBrowserForAuthentication": false
},
"LoginPage": {
"LoginPageUrl": "https://uat-my-community.cs112.force.com/login",
"LogoUrl": "https://uat-my-community.cs112.force.com/img/logo214.svg",
"BackgroundColor": "#B1BAC1",
"SelfRegistrationEnabled": false,
"SelfRegistrationUrl": null,
"ForgotPasswordUrl": "https://uat-my-community.cs112.force.com/secur/forgotpassword.jsp",
"DefaultProfileForRegistration": null,
"FooterText": "salesforce.com",
"UsernamePasswordEnabled": false,
"PrimaryColor": "#1797C0",
"RightFrameUrl": null
},
"SamlProviders": [
{
"Name": "Azure AD",
"SsoUrl": "https://uat-my-community.cs112.force.com/saml/authn-request.jsp?saml_request_id=_2CAAAAXpqUKasOdMdDAwMDAwMDAwMDAwMDAwAAAA6HH-eNyh6ZifsARp9k1tURQBUhBpFeP0thiiFVz_NDOy8LdUYlsoyu7PBoco8nLt8sPcJYE19JruPxftEuSuM9tmWZ-oqNvqeh0IGDUvHT9UtzJ1TturBcvHu6t6kP_c2_jcwl1LY0ih0LXkkttbZ3RivA973j0q-bgXb0ZpqAgPoCj53yem9Ptfc6ptZmmTWtS2UAg-CbWYPyW1fzP0fNDba7439yGorwtimcCFqRrMqifVgmc0yENfaHAp59VBA&saml_acs=https%3A%2F%2Fuat-my-community.cs112.force.com%2Flogin&saml_binding_type=HttpRedirect&Issuer=https%3A%2F%2Fuat-my-community.cs112.force.com%2Flogin&samlSsoConfig=0LE0T0000007OUa&RelayState=%2F"
},
{
"Name": "Test by Wilson",
"SsoUrl": "https://uat-my-community.cs112.force.com/saml/authn-request.jsp?saml_request_id=_2CAAAAXpqUKsPMDAwMDAwMDAwbMDAwMDAawAAAA6C707EK6JFsISvUbqwk6uuUG75YKiPpwfCfDdAZfPVkvTyTsDU6m7SS6VsojTRiG5trrrvO9mwqw-m9JOxa4qNnK84TQWOmxzYJni3kX7Y1OBpE23quHmJoVtbre5n2gEvTOM1x652_VGzOXo6iyHnJvOWe8M-cgHi5xBAziKS-vdmuL-eHxxN6BqS7d81XzNAUrPVmajx0awI3yx0OFSy8qM1EcoKSTeuIgo27nGKUDhhrBu46WyuDkfjLvsaph6Q&saml_acs=https%3A%2F%2Fuat-my-community.cs112.force.com%2Flogin&saml_binding_type=HttpRedirect&Issuer=https%3A%2F%2Fsavsg--uat.my.salesforce.com&samlSsoConfig=0LE0T0000007OV9&RelayState=%2F"
},
{
"Name": "Test by IMS",
"SsoUrl": "https://uat-my-community.cs112.force.com/saml/authn-request.jsp?saml_request_id=_2CAAAAXpqUKsQMDAwMDAwMDAwMDAwMDAawAAAA6IbdhAQK4MROyK16eJ1T3SD1gq6EfZy7Sv3kJ133cuI_yEKHOa371y31WXPwkMAxwazI_6T71LBTQm3KUQOs2kTBKCWVNXOm_d-cNrNArED3Z0kzsNWUnTyUcmzw_qeywnyqO-qnrotDRcADtXy7QWBfue2Xkz4DkBLlg5S1yfzlXOUSMzQjPXkVOLZwZlrIJ1Pb24f1pWcDUXPXuxppfOgpmrmPXOCQYhJmLPUeoleew5sjlGJqnNLUUVGhPKeNV6A&saml_acs=https%3A%2F%2Fuat-my-community.cs112.force.com%2Flogin&saml_binding_type=HttpRedirect&Issuer=https%3A%2F%2Fwww.imanagesystems.com&samlSsoConfig=0LE0T0000007OVT&RelayState=%2F"
}
],
"AuthProviders": [],
"CertificateLogin": null,
"LoginPageType": "standard",
"LoginPageTypeConfigs": {}
}Q4、 If there are more than one SSO Settings How to get ssoUrl for mobile application? | OAuth 2.0 User-Agent Flow for Desktop or Mobile App Integration
A4、 To configure a connected app, When mobile (ios / android) Visit the final endpoint Jump to the first Microsoft Landing page , After authorization, click connected app approval page Of accept, Posterior band access_token Jump back to community home page.
HttpRequest request = new HttpRequest();
request.setEndpoint('https://my-community.cs112.force.com/services/oauth2/authorize?response_type=token&client_id={consumer key}&redirect_uri={redirect url configured in the connected app}&state=mystate&display=touch');
request.setTimeout(60000);
request.setMethod('GET');
request.setHeader('Content-Type', 'application/json');
HttpResponse response = new Http().send(request);
String rdUrl = response.getHeader('Location');
System.debug(LoggingLevel.INFO, '*** rdUrl: ' + rdUrl);
Pagereference pgr = New Pagereference(rdUrl);
String sourceStr = pgr.getParameters().get('source');
String startUrl = '/';
String communityUrl = 'https://my-community.cs112.force.com';
String samlId = '0LE0T0000008OUa'; //This is the configId
String ssoUrl = Auth.AuthConfiguration.getSamlSsoUrl(communityUrl, startUrl, samlId);
String finalEndpoint = ssoUrl+'setup/secur/RemoteAccessAuthorizationPage.apexp?source='+sourceStr;
System.debug(LoggingLevel.INFO, '*** finalEndpoint: ' + finalEndpoint);Q5、Azure AD The same SFDC Connector Of Enterprise application Can you connect multiple SFDC Orgs?
A5、 Sure . For example, global enterprises A, There are differences all over the world office, Each country uses a separate SFDC Org, here A Companies can be in Azure AD Open one SFDC Connector Enterprise application, Will others SFDC Of Entity ID,Reply URL Just configure them , At this time, we can pass on Claims It's equipped with Group To distinguish the difference SFDC Orgs Users in , And then help JIT Apex Handler Confirm the login user's country . Here's the thing to watch out for , Please make sure the same Application Of User Only belong to one Group. because Azure AD Multiple attributes with the same value will be passed , but Apex Handler from attributes Chinese analysis key ( Such as GroupID) when ,Map Medium key The same name will be covered , You can only get one . It is different for the same person to visit SFDC Orgs The needs of , It is suggested that SFDC After creating the user , take Federation ID Post in or create a Common Group Special maintenance for special needs .



边栏推荐
- vue使用keep-alive实现页面缓存
- 卷积神经网络——YOLOV2(YOLO9000)论文翻译
- 知物由学 | 再造巴别塔,我们如何进行NLP跨语言知识迁移?
- Wechat applet realizes location map display and introduces map map without navigation
- XStream reports an error abstractreflectionconverter$unknownfield exception when parsing XML
- Configuration and basic use of vim
- hutool- 数字计算
- The global cloud market is growing rapidly, and data security has entered a strong regulatory era of rule of law
- Hutool digital computing
- Does PostgreSQL 14 support winserver2022?
猜你喜欢

JDBC connection database reading foreground cannot display data

工信部再治数据安全,网易易盾“隐私合规”守住企业经营底线

Numpy array matrix operation

登录页面tableLayout(表格布局)
2022 safety officer-a certificate examination questions and online simulation examination

Convolutional neural network -- Translation of yolov2 (yolo9000) papers

Evaluation index of machine learning (II) -- classification evaluation index

How to restrict root remote login so that ordinary users have root privileges

Machine learning: IOU of concept understanding

Fast parsing combined with Huatu document encryption software
随机推荐
[MCU] 2.3 CPU of AT89S52
X-sheet development tutorial: initialization configuration custom layout
用slmgr命令激活正版Win7旗舰版系统
Class not found: “com.parkManagement.dao.DaoTest 测试找不到测试类
fragmentTransaction.replace第二个参数报错
ts学习笔记-interface
知物由学 | SO加固如何提升Android应用的安全性?
golang 等待一组goroutine完成,并带返回值(2)
机器学习之评价指标(一)——回归评价指标
Learn from things | Yidun mobile terminal isomorphism practice, improve the official website interaction experience in a few steps
卷积神经网络——YOLOV1论文翻译
JSP custom tag (bottom)
Wechat applet cloud function batch delete multiple data error: errcode: -502005 database collection not exists
Kubernetes 1.24 high availability cluster binary deployment
JDBC connection database reading foreground cannot display data
How difficult the interview is! I was forced to survive the six rounds of interview of ant financial! Almost out (interview resumption)
Wechat applet to make calls
js工具-cookie简单封装
卷积神经网络之卷积计算过程个人理解
MySQL creates a student table and queries grades