当前位置:网站首页>Shelling of ESP law of reverse crackme
Shelling of ESP law of reverse crackme
2022-06-22 03:32:00 【A traveler】
1 Preface
This question comes from a reverse question in the advanced area of attack and defense world experts crackme, By shelling the executable program , This shell is the shell of Beidou , involves ESP The laws of , The general process is to find call Situated ESp, Follow in the data window , Next hardware access breakpoint , That's it OEP It's about , use ODdump Just shell it out . Use after shelling IDA Open view main The pseudo code in the function writes a script , Finally get flag, This involves the use of three common reverse tools ,exeinfope,onllydbg ida;
2 Tool is introduced
OllyDug
OLLYDBG Is a new dynamic tracking tool , take IDA And SoftICE A combination of ideas ,Ring 3 Level debugger , Very easy to get started , Have replaced SoftICE It has become the most popular debugging and decryption tool . It also supports plug-in extension functions , Is the most powerful debugging tool at present .
Ollydbg Basic function shortcut keys :
F2: To set breakpoints explain : Set a breakpoint on an instruction , Press again to cancel the breakpoint .
F4: Execute the command to the current cursor explain : When encountering a loop, you can use F4 Execute the instruction until the end of the loop .
F7: Step in explain : When a function call is encountered, it will follow .
F8: step over explain : Encountered a function call that does not follow .
F9: Carry on explain : Run the program until the next breakpoint .
IDA
Interactive anti assembler professional (Interactive Disassembler Professional), People often call it IDA Pro, Or for short IDA, It is headquartered in Liege, Belgium (Liège) Of Hex-Rayd A product of the company .
IDA Basic function shortcut keys :
Enter Follow up function implementation , Check the address corresponding to the label
Esc Return to the follow-up office
A Explain that the address at the cursor is the first address of a string
B Conversion between hexadecimal number and binary number
C Explain that the address at the cursor is an instruction
D Explain that the address at the cursor is data
G Quickly find the corresponding address
H Conversion between hexadecimal number and decimal number
PEID
PEID It's a famous shell checking tool , It's powerful , Almost all the shells can be detected , Its quantity has exceeded 470 Kind of PE Shell type and signature of the document .
3 Experimental process
3.1 experimental analysis
After downloading the executable program from the website , First, follow the process to use PEID Open to see if the program is shelled , As shown in the figure below :

From the results shown in the figure, we can see , The program exists nsPack shell , Procedure is 32 Bit , The name of this shell is Beidou compression shell (nsPack), It is also suggested to use Quick unpack Tool shelling , But this question uses ESP Law of manual shelling , Of course , It can also be realized by directly using the universal shelling tool , But this is not the end ;
3.2 Experimental principle
ESP The principle of the law is “ Stack balance ” principle .
about RETN We can think of it this way :
1. Change the current ESP The address pointed to in is out of the stack ;
2.JMP To this address .
This completes the process of calling a subroutine . The key here is : If we want to return to the parent program , When we perform stack operations in the stack , Make sure you are in RETN Before this order ,ESP It points to the address we pushed into the stack . This is also known as “ Stack balance ” principle !
So we can assume that the shell is a subroutine , When the shell decompresses the code before and after , What he has to do is follow the principle of stack balancing .ESP The law can be generally understood as :
1、 Break at the command line hr esp-4( At this time ESP Namely OD The value currently displayed after loading )
2、hr ESP( The key flag is indicated by the next line of code ESP value ( Step through ))
ESP The scope of application of the law : Almost all compressed shells , Partially encrypted shell . As long as it's in the JMP To OEP after ,ESP=0012FFC4 Shell of , In theory, we can all use . But when to set a breakpoint to avoid verification , When to break OD To break it , This still needs a lot of summary and accumulation .
Memory breakpoint search OEP Principle : First , stay OD Memory breakpoints and normal breakpoints in (F2 Break down ) There are essential differences . Memory breakpoints are equivalent to commands bpm, His interruptions require DR0-DR7 Debug register , in other words OD Through these DR0-DR7 To determine whether to break the normal breakpoint (F2 Next break ) Equivalent to bpx, It changes a byte of the current address of the executed code to CC(int3). When the program runs to int3 An exception will be generated when , And this exception will be handed over to OD Handle , Give this exception to EIP-1 in the future , It just stops where it needs to be interrupted ( This will vary according to the system ), meanwhile OD On the top int3 Change back to the original code . Memory breakpoints are divided into : Memory access breakpoints , Memory write breakpoint .
3.3 Operation process
Drag the program to ollydbg Open in , As shown in the figure below :
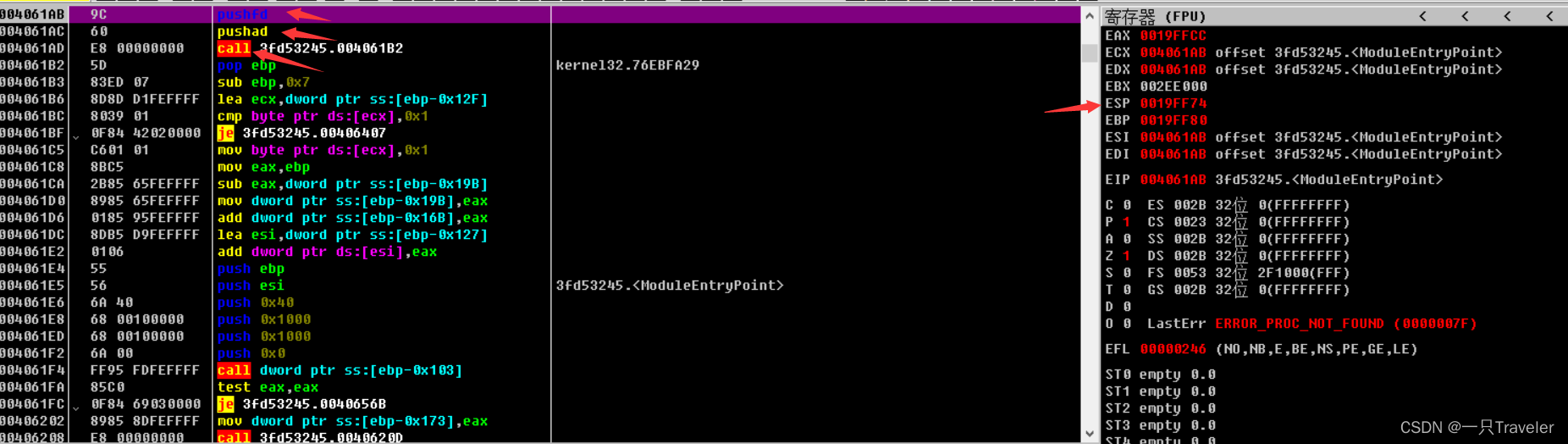
You can see pushfd and pushad It is the characteristic of Beidou shell , The first two pushfd and pushad Press in all EFlags Registers and general purpose registers .call After execution, press the next instruction address and jump .
After these three instructions are executed ESP It's worth the difference 0019FF74,0019FF70、0019FF50,0019FF4C,call Instructions are in shell code , For decompression , Short jump to the next 004061B2
two F8 Execute to call After the statement , And then it's in ESP Data window trace at , Right click in the data window to set word Grade or Dword Level hardware access breakpoints , As shown in the figure :
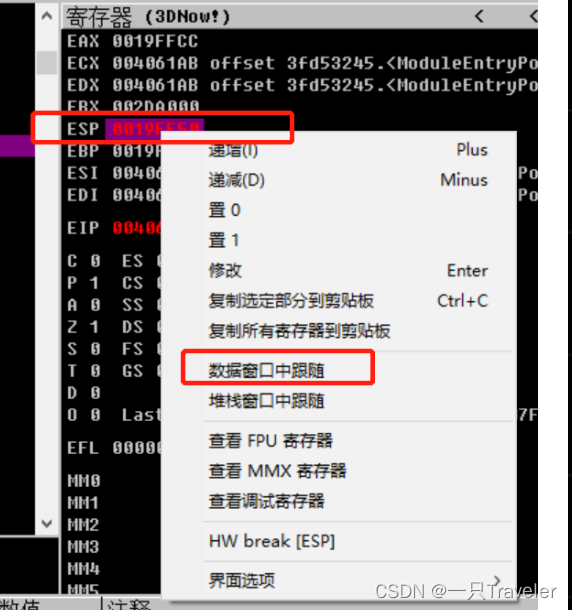
Then click AB Set the hardware access breakpoint at the location :

Why setting breakpoints is word Level :
In addition to specifying a mode for hardware breakpoints , You must also specify a size . The size of the execution class breakpoint must be 1 byte , Write class or read / The size of the write class breakpoint can be set to 1、2 or 4 byte . If the size is set to 2 byte , The address of the breakpoint must be word aligned (2 Integer multiples of bytes ). Again ,4 The address of the byte breakpoint must be doubleword aligned (4 Integer multiples of bytes ). The size of a hardware breakpoint and its address together constitute the address range that triggers such a breakpoint . Here's an example . At the address 0804C834h One set at 4 Take byte write breakpoints as an example , This breakpoint will be determined by 1 Byte write 0804C837h、2 Byte write 0804C836h、4 Byte write 0804C832h Wait for the operation to trigger .
After the breakpoint is set ,shift+F9 Run the program ,

In the picture we can see , The program is suspended at popfd It's about , The code in the box replaces retn sentence , Here, the shell function call is completed , It's time to return , Why does the program stop at popfd Well ; Because our hardware access breakpoints are broken 0019ff50, The decompressing code in the shell involves at most call Press in 0019ff4c So you can access 0019ff50 Only popad, When he executes it, he accesses the truncation , So stop at popfd here
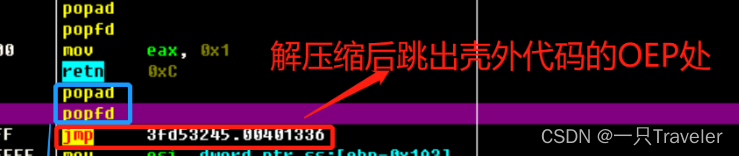
Popfd Below jmp Is to unzip and jump out of the shell code OEP It's about ;
continue F8 function
jmp After jumping out of the shell, you will find the decompressed code , Right click to analyze the current code .text. The data in the segment is reassembled into assembly code

After analysis, the results are as follows :

Then it is at this position that the shell is peeled , use OD plug-in unit OllyDump Come on, shelling , Generate a new executable :

After preservation , So far, the manual shelling is completed
Then drag the shelled program to IDA in ;F5 see main The pseudo code in the main function can be found :
int __cdecl main(int argc, const char **argv, const char **envp)
{
int v3; // [email protected]
char *v4; // [email protected]
char v5; // [email protected]
int result; // [email protected]
signed int v7; // [email protected]
int v8; // [email protected]
*(_BYTE *)(v3 - 56) = 0;
memset((void *)(v3 - 55), 0, 0x31u);
printf("Please Input Flag:");
gets_s((char *)(v3 - 56), 0x2Cu);
v4 = (char *)(v3 - 56);
do
v5 = *v4++;
while ( v5 );
if ( &v4[-v3 + 55] == (char *)42 )
{
v7 = 0;
while ( (*(_BYTE *)(v3 + v7 - 56) ^ byte_402130[v7 % 16]) == dword_402150[v7] )
{
if ( ++v7 >= 42 )
{
printf("right!\n");
goto LABEL_10;
}
}
printf("error!\n");
LABEL_10:
v8 = v3 ^ *(_DWORD *)(v3 - 4);
result = 0;
}
else
{
printf("error!\n");
result = -1;
}
return result;
}
Pass the first 15 Line code , We know that the input is correct flag And byte_402130[v4 % 16] XOR equals dword_402150[v4], This v4 Is an array subscript , The maximum is 41

It's actually "this_is_not_flag"
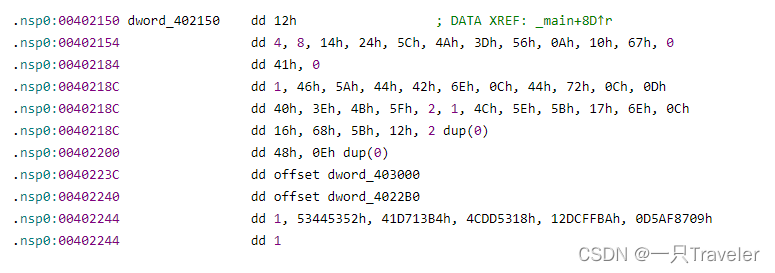
This number takes 42 Just one , Then write the code :
byte_402130 = "this_is_not_flag"
dword_402150 = [ 0x12, 4, 8, 0x14, 0x24, 0x5C, 0x4A, 0x3D, 0x56, 0x0A, 0x10, 0x67,
0, 0x41, 0, 1, 0x46, 0x5A, 0x44, 0x42, 0x6E, 0x0C, 0x44, 0x72, 0x0C, 0x0D,
0x40, 0x3E, 0x4B, 0x5F, 2, 1, 0x4C, 0x5E, 0x5B, 0x17, 0x6E, 0x0C, 0x16, 0x68,
0x5B, 0x12, 0, 0, 0x48 ]
x = ''
for i in range(0,42):
x += chr(dword_402150[i]^ord(byte_402130[i%16]))
print(x)
After running the code, you get flag:

3 Conclusion
Software reverse is a process in which practice makes perfect , In addition to learning the experience and skills of others , More is the need for continuous practice . The reverse process of software is boring , You must have enough patience and care . For my understanding : The most basic tool for cracking software is the software written by others for cracking analysis , There are many such software , The most basic are three . Boss call PEID, The second name is DIE64, Third name OD. Encounter the software to be cracked , Brothers go to battle in turn . Boss, go first , The function is to check whether the software is shelled , What shell is it ? Shell is the bulletproof jacket of software , This bulletproof vest is written with a special program , This bulletproof vest is another layer of protection added after the software has been verified . Its purpose is to deal with the cracking tools we use , Let us have a hard time . After our boss checked , Knowing the model of this bulletproof vest, you can use the corresponding tool to take off the bulletproof vest to deal with it . next , The second one goes on , The function is to identify what language the software is written in , Usually there are C、VC、VB、DELPHI、 Easy language, etc , Because different languages have special ways to crack . Know if there is a shell ? What language is it written in ? Then the third brother came on stage .OD The function of is to analyze software . What to analyze ? Is to find out the key position of verification , Analysis and verification mechanism .
边栏推荐
猜你喜欢
![[网鼎杯 2018]Fakebook1 参考](/img/c8/a9d77308b6cc542c8c47a570b9234c.png)
[网鼎杯 2018]Fakebook1 参考

CMD view the console output of hearts, diamonds, spades and clubs to solve the garbled code

【NVMe2.0b 12】NVM 容量模型

rabbmitMQ 简单模式<一>

你是一名技术管理者还是项目管理者?

华硕重装系统键盘灯失效 =>重装ATK驱动

【NVMe2.0b 5】NVM Subsystem
![[nvme2.0b 9] controller initialization process](/img/70/536b2c850c611d5d0c013586d4c2d5.png)
[nvme2.0b 9] controller initialization process

AtCoder Regular Contest 142
![[microservices | Nacos] quickly realize the configuration center function of Nacos, and complete configuration update and version iteration](/img/20/4c4a062ac7a4d265cde236ee677ac1.png)
[microservices | Nacos] quickly realize the configuration center function of Nacos, and complete configuration update and version iteration
随机推荐
Magic method "six"__ enter__ And__ exit__
AtCoder Regular Contest 142
A component required a bean of type 'com.example.demo3.service.UserServiceImp' that could not be fou
How to do activities in beauty salons
[pwn basics]pwntools learning
调度功能:splunk-operator-controller-manager
Why is setinterval so easy to get stuck in the high and low level
作为接口的模板
rabbmitMQ 发布关键字模式<三>
Splunk: Auto load Balanced TCP Output issue
Runtime package for golang concurrent programming
Wechat applet onpagescroll is invalid
【NVMe2.0b 11】NVMe Reset
基于Pytorch的图像分类总结:Swin Transformer
3de 机器人吸盘抓box
3de从设计中恢复
fastdfs-5.0.5安装
Splunk: Auto load Balanced TCP Output issue
CMD view the console output of hearts, diamonds, spades and clubs to solve the garbled code
Project management software development project management