当前位置:网站首页>「开源摘星计划」Containerd拉取Harbor中的私有镜像,云原生进阶必备技能
「开源摘星计划」Containerd拉取Harbor中的私有镜像,云原生进阶必备技能
2022-06-23 18:50:00 【51CTO】

【摘要】 配置 Containerd 拉取 harbor 私有仓库中的镜像,打工人必备技能!
本文已参与「开源摘星计划」,欢迎正在阅读的你加入。
活动链接: https://github.com/weopenprojects/WeOpen-Star
前言
在k8s的1.20版本发布之后,对外宣称在1.23.x不再使用doker shim作为默认的底层容器运行时,而是通过Container Runtime Interface(CRI)使用containerd来作为容器运行时, 因此原来在docker中配置的个人仓库环境不再起作用,导致k8s配置pods时拉取镜像失败, 本文将进行演示如何在 containerd 配置从Harbor私有仓库拉取镜像。
环境说明
- 操作系统:CentOS
- Harbor Version:2.3.5
- Containerd Version:1.6.5
- Harbor地址: https://192.168.2.22:443
Containerd使用二进制安装的方式,安装步骤见: https://blog.51cto.com/lidabai/5408290
Harbor使用https证书认证的方式部署的,部署文档见: https://blog.51cto.com/lidabai/5173694
修改containerd配置
配置Harbor私有镜像仓库地址
[[email protected] ~]
# vim /etc/containerd/config.toml
...
version
=
2
...
[plugins]
[plugins.
"io.containerd.grpc.v1.cri"]
[plugins.
"io.containerd.grpc.v1.cri".cni]
...
########################################################配置以下部分:
[plugins.
"io.containerd.grpc.v1.cri".registry]
config_path
=
""
[plugins.
"io.containerd.grpc.v1.cri".registry.auths]
[plugins.
"io.containerd.grpc.v1.cri".registry.headers]
[plugins.
"io.containerd.grpc.v1.cri".registry.mirrors]
[plugins.
"io.containerd.grpc.v1.cri".registry.mirrors.
"docker.io"]
endpoint
= [
"https://kvuwuws2.mirror.aliyuncs.com",
"http://hub-mirror.c.163.com"]
[plugins.
"io.containerd.grpc.v1.cri".registry.mirrors.
"harbor.lidabai"]
#名称
endpoint
= [
"https://192.168.2.22:443"]
#Harbor的Url地址
[plugins.
"io.containerd.grpc.v1.cri".registry.configs]
[plugin.
"io.containerd.grpc.v1.cri".registry.configs.
"harbor.lidabai".tls]
#tle,harbor 证书认证配置
insecure_skip_verify
=
true
#是否跳过证书认证
ca_file
=
"/etc/containerd/harbor/ca.crt"
# CA 证书
cert_file
=
"/etc/containerd/harbor/harbor.crt"
# harbor 证书
key_file
=
"/etc/containerd/harbor/harbor.key"
# harbor 私钥
[plugin.
"io.containerd.grpc.v1.cri".registry.configs.
"harbor.lidabai".auth]
#auth,配置注册表凭据
username
=
"admin"
#Harbor用户名
password
=
"Harbor12345"
#Harbor密码
auth
=
""
identitytoken
=
""
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.
- 23.
- 24.
- 25.
- 26.
- 27.
- 28.
- 29.
- 30.
- 31.
- 32.
- 33.
- 34.
- 35.

重启containerd.service服务
重新加载载 systemd 的 daemon守护进程并重启containerd.service服务,然后k8s集群节点便可正常从Harbor拉取镜像了。
拉取镜像
虽然上面的方式可以使k8s直接拉取镜像,但是在利用 ctl命令 进行手动拉取镜像此时会报如下错误(巨坑-经过无数次失败测试,原本以为是CA证书签发的harbor证书问题),即使你在config.toml中配置insecure_skip_verify为true也是不行的,可以添加-k参数跳过证书校验。
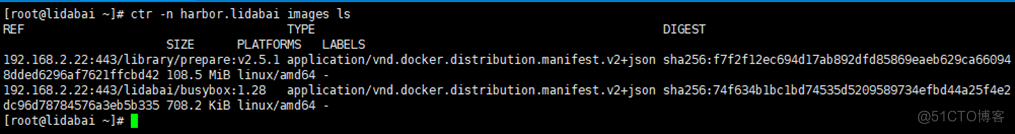
查看下载的镜像
刚才我们下载镜像时通过-n参数指定了namespace。在查看时也要通过-n指定namespace,否则看不到。
踩坑记录
unexpected status code [manifests 1.28]: 401 Unauthorized
【问题描述】
下载Harbor中的私有镜像时报错:
[[email protected] app]
# ctr -n harbor.lidabai images pull 192.168.2.22:443/lidabai/busybox:1.28 -k
ctr: failed to resolve reference
"192.168.2.22:443/lidabai/busybox:1.28": unexpected status code [manifests
1.28]:
401 Unauthorized
- 1.
- 2.

【原因】401未经授权
【解决】通过-u参数指定Harbor用户名和密码。

x509: certificate signed by unknown authority
【报错描述】在拉取镜像时报出错误:
[[email protected] ~]
# ctr images pull 192.168.2.22:443/library/prepare:v2.5.1
error
=
"failed to do request: Head \"https://192.168.2.22:443/v2/library/prepare/manifests/v2.5.1\": x509: certificate signed by unknown authority"
host
=
"192.168.2.22:443"
ctr: failed to resolve reference
"192.168.2.22:443/library/prepare:v2.5.1": failed to
do request: Head
"https://192.168.2.22:443/v2/library/prepare/manifests/v2.5.1": x509: certificate signed by unknown authority
- 1.
- 2.
- 3.

【解决办法】:
1)通过-k参数跳过证书校验。

2)指定CA证书、Harbor相关证书文件路径。
$ mkdir /etc/containerd/harbor/
#创建证书存放目录
$ scp /app/harbor-cert/{ca.pem,harbor.pem,harbor-key.pem}
192.168.2.41:/etc/containerd/harbor/
$ ctr
-n harbor.lidabai images pull
192.168.2.22:443/library/prepare:v2.5.1 \
--tlscacert /etc/containerd/harbor/ca.pem \
#或ca.crt
--tlscert /etc/containerd/harbor/harbor.pem \
#或harbor.crt
--tlskey /etc/containerd/harbor/harbor-key.pem
#或harbor.key
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
精品文章阅读
Harbor高可用集群设计及部署(实操+视频),基于离线安装方式
Harbor进阶:使用Harbor存储Helm chart
Python实现Harbor私有镜像仓库的垃圾自动化
Harbor jobservice组件异常问题处理
Harbor高可用设计: 使用外部Redis缓存部分
如何将dockerhub上的镜像迁移到Harbor私有镜像仓库中?
边栏推荐
- Goldfish rhca memoirs: do447 managing user and team access -- effectively managing users with teams
- GL Studio 5 installation and experience
- Matrix analysis notes (III-1)
- Function definition and function parameters
- 1、 Summary and introduction
- [one by one series] identityserver4 (II) using client credentials to protect API resources
- 打新债有何要求 打新债安全吗
- How to write a great online user manual in 7 steps
- Hardware development notes (6): basic process of hardware development, making a USB to RS232 module (5): creating USB package library and associating principle graphic devices
- 科班出身,结果外包都不要
猜你喜欢
随机推荐
基于 ShardingSphere 的得物数据库中间件平台“彩虹桥”演进之路
19 classic cases of generator functions
活动报名 | MongoDB 5.0 时序存储特性介绍
Real topic of the 13th National Competition of single chip microcomputer in the Blue Bridge Cup
打新债有条件吗 打新债安全吗
Ready to migrate to the cloud? Please accept this list of migration steps
FlagAI飞智:AI基础模型开源项目,支持一键调用OPT等模型
Live sharing | Tencent cloud mongodb intelligent diagnosis and Performance Optimization Practice
What are the useful personnel management software? Personnel management system software ranking!
Application of JDBC in performance test
Netcf summary
硬件开发笔记(六): 硬件开发基本流程,制作一个USB转RS232的模块(五):创建USB封装库并关联原理图元器件
深入理解和把握数字经济的基本特征
Activity registration | introduction to mongodb 5.0 sequential storage features
如何通过7个步骤编写出色的在线用户手册
Development notes of wedding studio applet based on wechat applet
八大误区,逐个击破(终篇):云难以扩展、定制性差,还会让管理员失去控制权?
Save: software analysis, verification and test platform
不止雷军 iQOO产品经理也称赞高通骁龙8+:焕然一新
NAACL 2022 Findings | 字节提出MTG:多语言文本生成数据集









