当前位置:网站首页>SSH private key realizes login to remote target server
SSH private key realizes login to remote target server
2022-07-25 21:08:00 【Cloud computing security】

Catalog
In our test or production environment , For server security , Sometimes it may be necessary to SSH Log in to the server by using the key , Next , Will show how to pass SSH Private key way to remote server .
One 、 The remote server generates a key pair
1、 First, generate SSH Key pair
All the way back
[[email protected] ~]# ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/build/.ssh/id_rsa):
Created directory '/home/build/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/build/.ssh/id_rsa.
Your public key has been saved in /home/build/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:PlPyHlOiZEHn3cAyctH5019FwGNCSdR9dhyR5pj2rAA [email protected]
The key's randomart image is:
+---[RSA 2048]----+
| . oB==.B=|
| ..o+.*o=oB|
| .o.o.+*++|
| E +o.o|
| S + o o.o|
| + = + o.|
| = + . . |
| + o . |
| . |
+----[SHA256]-----+
2、 A pair of key pairs will be generated ( Public and private keys )
Private key :id_rsa
Public key :id_rsa.pub
[[email protected] ~]# cd ~/.ssh/
[[email protected] .ssh]# ll
total 8
-rw------- 1 build build 1679 Jul 18 15:14 id_rsa
-rw-r--r-- 1 build build 396 Jul 18 15:14 id_rsa.pub
Two 、 Download private key to local ( Connect to the client )
1、 Download the private key to the connection client
When the key pair is generated , Put the private key (id_rsa) Download to connect client local , such as , I will download it to my Windows Local , And then through Xshell Client tools ssh Connect to the target server remotely .

2、Xshell configure connections
Connect
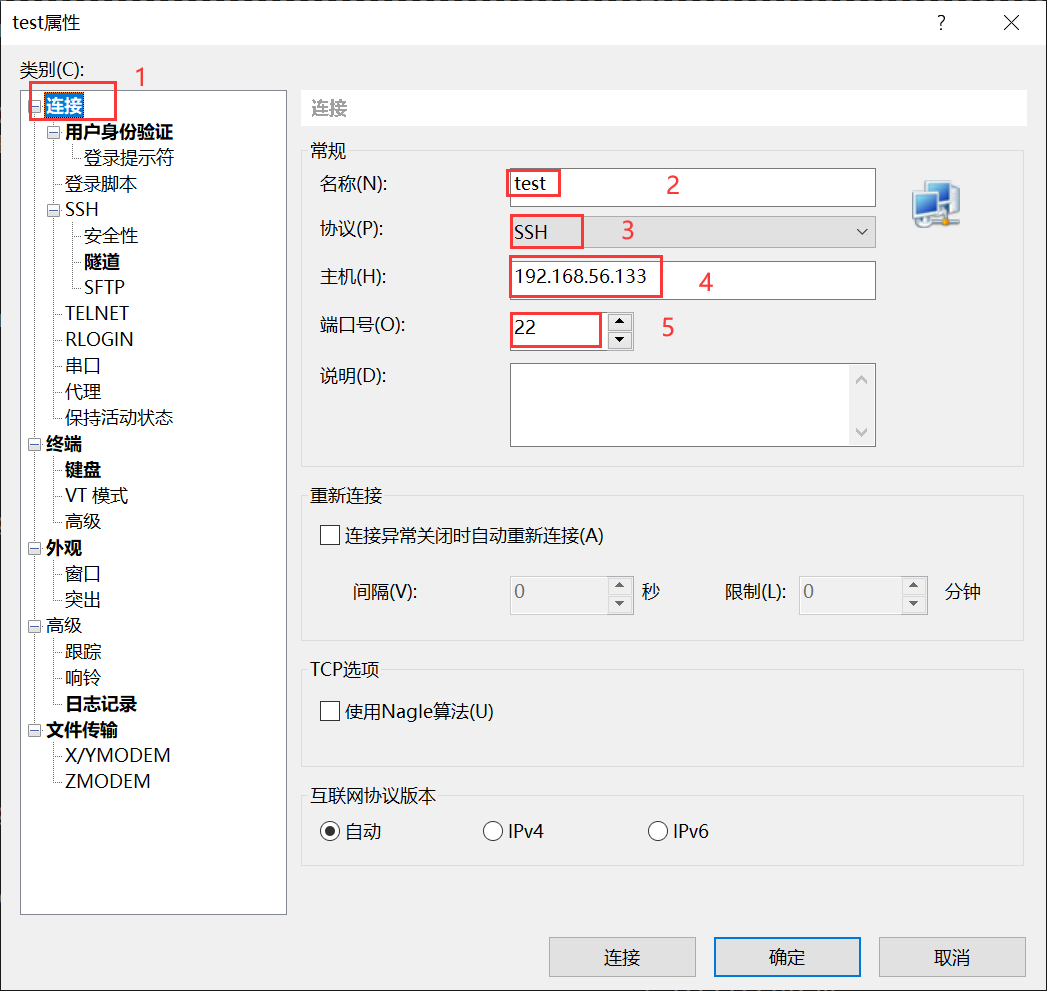
User authentication , Finally, click “ Connect ”

choice “ Browse ” Under Options “ file ”, And select the private key file we just downloaded from the target server

Finally, click “ determine ”
But at this time, you will find that you still need to enter root User password . This is not what we need , What we need is direct password free login , Otherwise it doesn't make any sense .

3、 ... and 、 The remote server copies the public key ( Realize the secret free )
According to the error in the above figure , So we also need to configure password free login , It's simple , The two methods .
- If it is a key pair generated by itself on the target server , It's just
~/.ssh/Create a new directory namedauthorized_keysThe file of ( If it doesn't exist ), And copy and paste your public key into the file . - If ssh The key pair is not generated directly on the target server , You need to copy the key pair to the target server , And generate the corresponding
authorized_keysfile .
say something authorized_keys file , This file is the file to realize secret free login , What we use ssh-copy-id <192.168.56.133> In fact, it is to distribute your public key to 133 Realize secret free login on the target server .
That is to say, my remote target server needs to contain at least the following three files , In order to realize secret free login in the way of private key .
[[email protected] .ssh]# ll
total 12
-rw------- 1 root root 395 Jul 18 15:50 authorized_keys
-rw------- 1 root root 1675 Jul 15 17:03 id_rsa
-rw-r--r-- 1 root root 395 Jul 15 17:03 id_rsa.pub
Here's the picture , You can log in normally .

边栏推荐
- DDD的Go实战
- cts测试步骤(卡西欧cts200测试)
- "Shallow in and shallow out" MySQL and InnoDB [it is recommended to collect and share]
- ROS_ Rqt toolbox
- The role of the resize function is "suggestions collection"
- Solution to oom exceptions caused by improper use of multithreading in production environment (supreme Collection Edition)
- Leetcode-6131: the shortest dice sequence impossible to get
- Rent two or three things
- NPM module removal_ [solved] after NPM uninstalls the module, the module is not removed from package.json [easy to understand]
- MPI learning notes (II): two implementation methods of matrix multiplication
猜你喜欢
Solution to oom exceptions caused by improper use of multithreading in production environment (supreme Collection Edition)

476-82(322、64、2、46、62、114)

Matlab---eeglab check EEG signal

Jmeter分布式压测

Vivo official website app full model UI adaptation scheme

leetcode-6129:全 0 子数组的数目
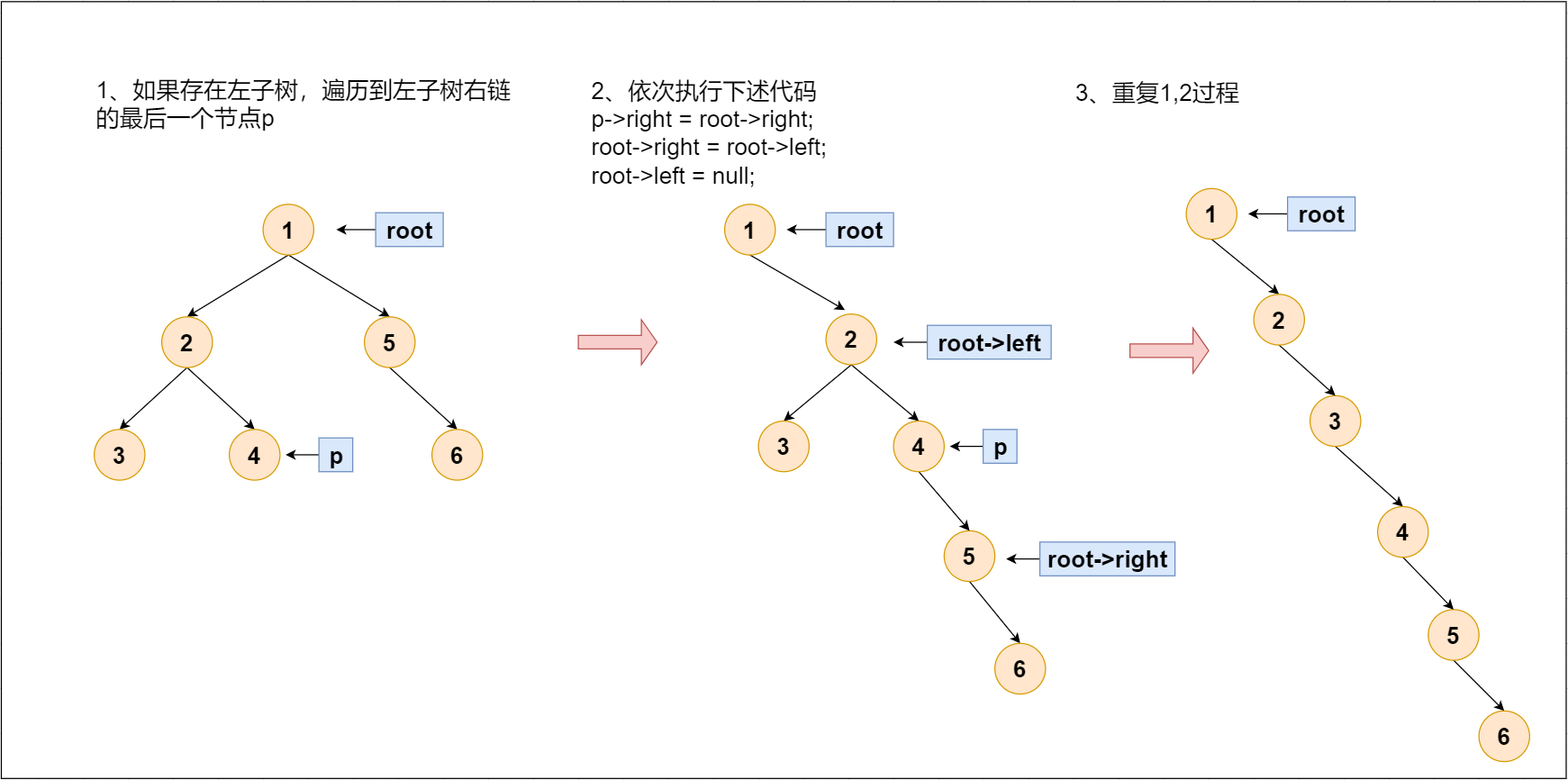
leetcode-114:二叉树展开为链表

Leetcode-155: minimum stack

Today's sleep quality record 75 points

Character function and string function (2)
随机推荐
图片怎么存储到数据库里「建议收藏」
Use Navicat to connect to MySQL database through SSH channel (pro test is feasible)
KEGG通路的从属/注释信息如何获取
leetcode-6130:设计数字容器系统
Unity VS—— VS中默认调试为启动而不是附加到Unity调试
IEC61131 address representation
PayPal PHP product trial period "recommended collection"
两数,三数之和
Please give an example of how to optimize MySQL index (sqlserver index optimization)
Detailed explanation of document operation
matlab----EEGLab查看脑电信号
Step num problem
Leetcode-6127: number of high-quality pairs
有哪些优化mysql索引的方式请举例(sqlserver索引优化)
数据库sql语句练习题「建议收藏」
A detailed explanation of SCP command
一道golang中关于map的并发读写的面试题
Debugged PEB (beingdebugged, ntglobalflag)
Leetcode-114: expand binary tree into linked list
预处理指令