当前位置:网站首页>Upload lab level 1-4
Upload lab level 1-4
2022-07-23 11:31:00 【qianpd】
upload-lab Range practice
The first level
There is basically nothing to say about this level , Because it's through javascript To verify the user's input is the so-called front-end verification, so you can directly capture packets or modify the front-end code .
As shown in the figure above, change the suffix from jpg It is amended as follows php Upload from New 
The second level
This level is about documents MIME Head for detection ,MIME The header is in the packet Content-Type: image/png This can show the type of uploaded files, but it can be modified by capturing packets or uploaded directly png or jpg The format of file capture is manually changed to script language type .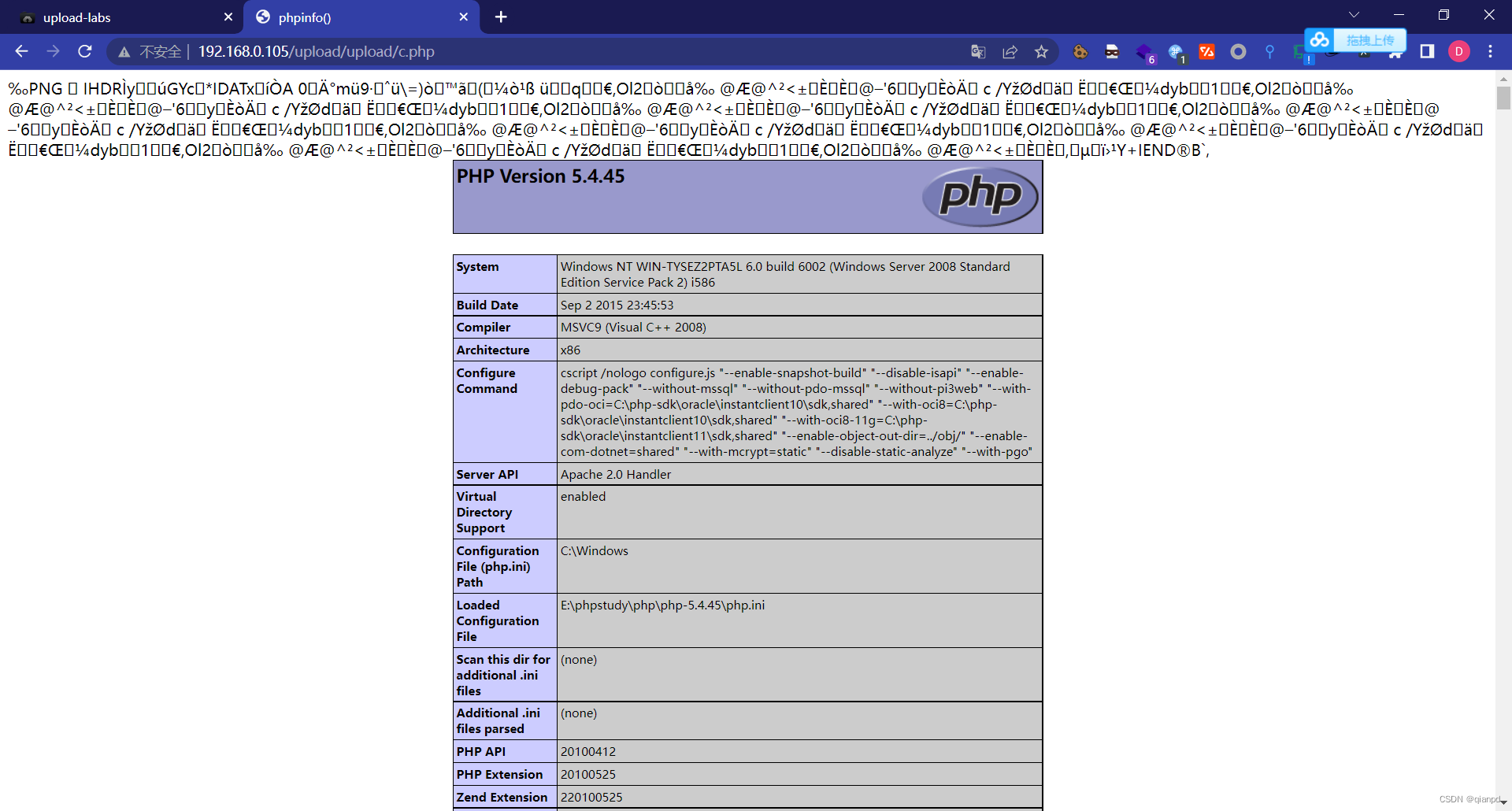
The third level
This level is the blacklist to control the files uploaded by users 
You can see that it prohibits the suffix upload of common scripting languages, and it is controlled by the back-end language, so it is impossible to modify the suffix upload through packet capturing , But we can upload things like .phtml .php3 Such suffixes go around , The prerequisite for this is Apach The configuration file httpd.conf Lieutenant general 
Open it , I don't know why I can't resolve it after I open it , Just leave a small hole first .
The fourth level
Like the third level, this level is blacklist detection , And there are more suffixes than the last one 
Almost all suffixes that can be used are filtered, but they are not right .htaccess File file filtering, we can upload one first .htaccess The file can then bypass the filter .
.htaccess It's a plain text file , It contains Apache Server configuration related instructions .
.htaccess The main functions are :URL rewrite 、 Custom error page 、MIME Type configuration and access control . Mainly reflected in the application of pseudo static 、 Photo anti theft chain 、 Customize 404 Error page 、 prevent / Allow specific IP/IP paragraph 、 Directory browsing and home page 、 Access to the specified file type is prohibited 、 File password protection, etc .
Simply put, it can specify a file as a script file for execution, regardless of whether the file type is the suffix of the script file
There is no right in the third and fourth levels .htaccess Why only the fourth level can be used to filter files? You can see how they handle uploaded files
The third level 
The fourth level 
You can see that in the third level, we will rename the uploaded files, but in the fourth level, there is no ,.htaccess Files must be uploaded with .htaccess After uploading and renaming, other things will be added in front of it, which will lead to .htaccess File cannot execute
<FilesMatch "te">
SetHandler application/x-httpd-php
</FilesMatch>
// It means that the file name is marked with te All as php File parsing
There's another point here htaccess The attack requires PHP Version in 5.6 Version below and must be ts The version cannot be nts edition nts No resolution 
See there are 403 If you report an error, you will be successful , And then there's the upload webshell file 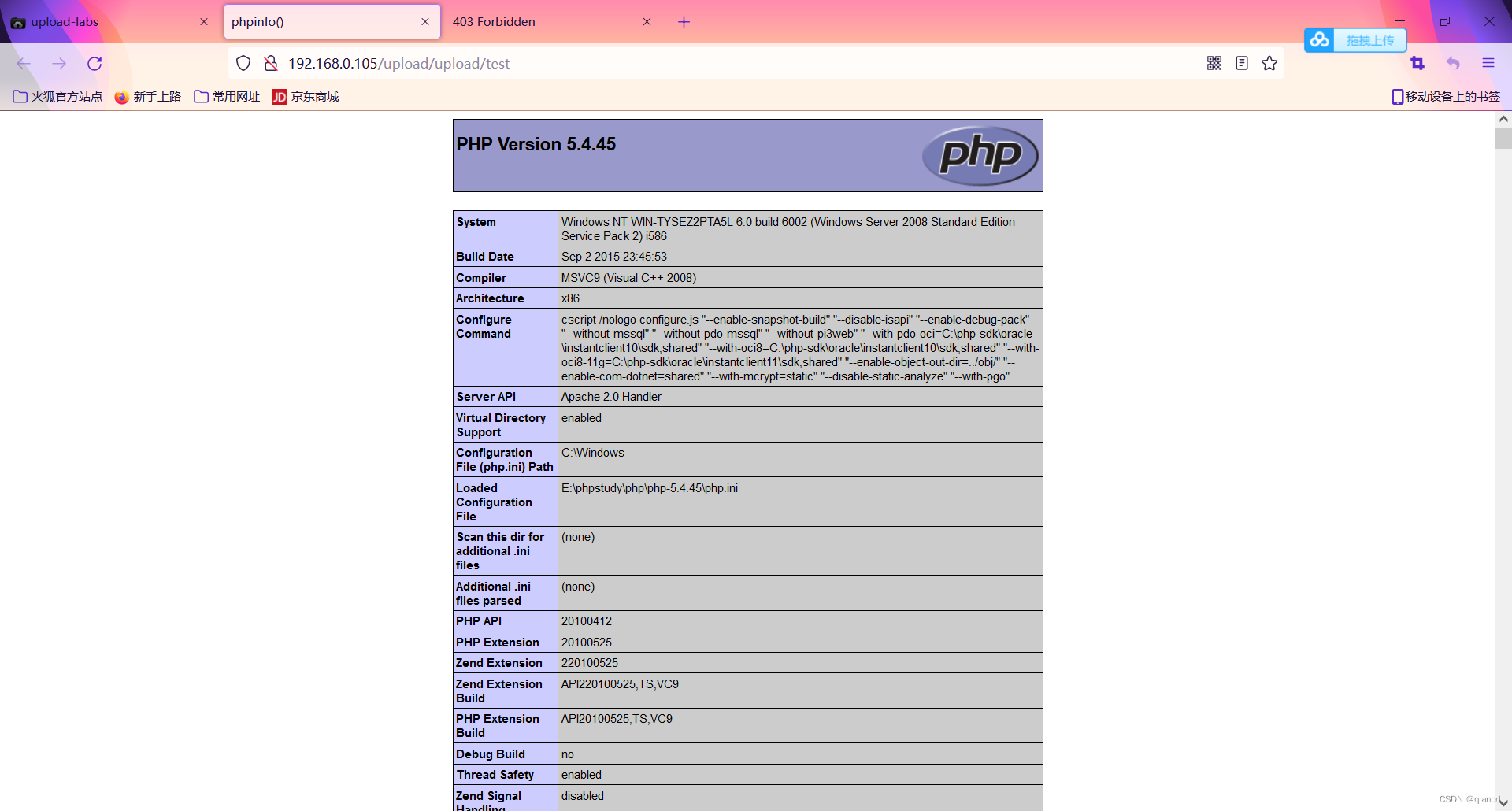
In a nutshell htaccess The condition for successful upload attack is
- php Version in 5.6 once
- php by ts edition
- Filter the blacklist
- The uploaded file will not be renamed ( The name is under your control )
边栏推荐
猜你喜欢

自定义MVC(下)

Fed Brad: last week's employment report showed that the U.S. economy is robust and can withstand higher interest rates

数字藏品系统开发:NFT的主要特点有哪些?
Genesis provided a loan of US $2.36 billion to Sanya capital
Burpsuite learning notes

py程序可以运行,但打包出的exe运行提示错误:加载“cv2”二进制扩展时检测到递归。请检查OpenCV安装。

Flex+js realizes that the height of the internal box follows the maximum height

数字藏品开发/数字藏品系统开发解决方案

Genesis曾向三箭资本提供23.6亿美元的贷款

CTF-web 常用软件安装及环境搭建
随机推荐
【C语言】什么是函数?函数的分类和侧重(帮你快速分类和记忆函数)
MySQL增删改查&&高级查询语句
NFT数字藏品开发:数字藏品在未来究竟有哪些可能的应用场景?
C语言之二分查找法或折半查找法剖析(经典例题,经典解析)
自定义公式输入框
Composants web - cycle de vie des éléments personnalisés
js的call、apply、bind
文件上传漏洞常见绕过方式
MySQL之账号管理&&四大引擎&&建库建表
Common errors in C language debugging -- brief answer
NepCTF2022 Writeup
Bank of Indonesia governor said the country is actively exploring encrypted assets
First blog
Inheritance mode of JS
JS call, apply, bind
中间人攻击arp欺骗及与beef-xss联动
Basis of penetration test
数字藏品开发/数字藏品系统开发解决方案
高阶函数的应用:手写Promise源码(一)
数字藏品系统开发/数字藏品方案介绍