当前位置:网站首页>Locating memory leaks with poolmon
Locating memory leaks with poolmon
2022-06-24 04:52:00 【shawyang】
poolmon Integrated into the wdk in , Need to run wdksetup.exe Installation , and windbg Also need to run wdksetup.exe Installation , But notice wdksetup.exe Not included Windows Performance Toolkit, Don't confuse .
First, how to install poolmon, Then introduce how to use
open https://docs.microsoft.com/zh-cn/windows-hardware/drivers/download-the-wdk
1、 Download and install wdk
Pay attention to the direct steps 3 Link download in wdksetup.exe
https://go.microsoft.com/fwlink/?linkid=2166289
function wdksetup.exe Download the installation files to a directory
Close the interface after downloading
Then download the completed directory ( The installation files are retained for deployment on multiple machines , After compression, it can be copied to other machines , Instead of downloading it again ), Find... In this directory wdksetup.exe Run the setup
2、cd /d "poolmon Absolute path directory of "
poolmon.exe The location of C:\Program Files (x86)\Windows Kits\10\Tools\x64\poolmon.exe
cd /d "C:\Program Files (x86)\Windows Kits\10\Tools\x64"
3、 perform poolmon -u -n c:\1.txt
use notepad++ open c:\1.txt( Software writers are anti Chinese , The software itself works very well , Alignment )
4、 Pay attention to page above 1 The article Bytes One column is in reverse order , Look at the first column of the previous articles Tag name
5、 perform cd /d c:\
findstr /m /l /s $tagname *.sys
Corresponding to the above figure, i.e
findstr /m /l /s MmSt *.sys
findstr /m /l /s Se *.sys
findstr /m /l /s FMfn *.sys
According to the keywords found, you can determine which software occupies the most memory , I have this case in , Mainly occupied by the operating system
6、 If Bytes A column of maximum values corresponds to Tag The name is DRPI, Then execute findstr /mls DRPI *.sys
explain DRPI This height is mainly 360 Occupy
Parameters /m /l /s It can be combined into /mls
Other Microsoft official information about the installation package :https://docs.microsoft.com/zh-cn/windows-hardware/drivers/other-wdk-downloads
边栏推荐
- ribbon
- Loss and optimization of linear regression, machine learning to predict house prices
- 集成阿里云短信服务以及报签名不合法的原因
- Web penetration test - 5. Brute force cracking vulnerability - (9) MS-SQL password cracking
- Facebook internal announcement: instant messaging will be re integrated
- Here's all you want to know about takin data (1) startup command
- 解析后人类时代类人机器人的优越性
- Library management backstage
- ribbon
- Naming of tables in MySQL
猜你喜欢
阿里云新一代云计算体系架构 CIPU 到底是啥?
Advanced authentication of uni app [Day12]
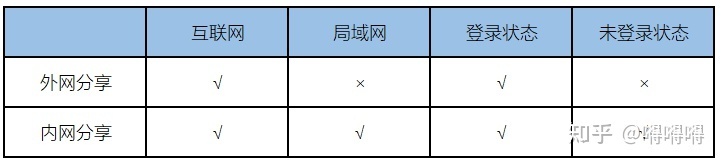
An interface testing software that supports offline document sharing in the Intranet
重新认识WorkPlus,不止IM即时通讯,是企业移动应用管理专家

Detailed explanation of tcpip protocol

大一下学期期末总结(补充知识漏洞)

让孩子们学习Steam 教育的应用精髓

什么是数据中台

TCPIP协议详解

SAP mts/ato/mto/eto topic 7: ATO mode 1 m+m mode strategy 82 (6892)
随机推荐
Customer disaster recovery case - a MySQL database migration scheme
SAP MTS/ATO/MTO/ETO专题之七:ATO模式1 M+M模式策略用82(6892)
Introduction to vulnerability priority technology (VPT)
Physicochemical properties and specificity of Worthington trypsin
External network access SVN server (external network access SVN server deployed on the cloud)
How does ECS publish websites? What software tools are needed?
一文简述:供应链攻击知多少
How to restart the ECS? What are the differences between ECS restart and normal computers?
What is the new generation cloud computing architecture cipu of Alibaba cloud?
How to operate ECs and what types of system configuration schemes can be supported
RedHat 8 time synchronization and time zone modification
Verifying data models in golang
Bi-sql - Select
ribbon
Summary of Android interview questions in 2020 (elementary)
大一下学期期末总结(补充知识漏洞)
Introduction to gradient descent method - black horse programmer machine learning handout
Data acquisition gateway intelligent industrial Internet of things
集成阿里云短信服务以及报签名不合法的原因
一款支持内网脱机分享文档的接口测试软件
![Advanced authentication of uni app [Day12]](/img/2e/59ad76ce8911d6d1f644322b34aaa5)