当前位置:网站首页>CSRF (Cross Site Request Forgery) &ssrf (server request forgery) (IV)
CSRF (Cross Site Request Forgery) &ssrf (server request forgery) (IV)
2022-06-25 04:54:00 【Key_ Words】
The first part :CSRF( Cross-site request forgery )
1.CSRF Attack principle diagram

2.CSRF Basic concepts
CSRF Cross-site request forgery (Cross—Site Request Forgery), Follow XSS The attack is the same , There is great harm , You can understand :
The attacker stole your identity , Send malicious requests in your name , This request is completely legal for the server , However, it has completed an operation expected by the attacker , For example, send email in your name 、 Send a message , Stealing your account , Add system administrator , Even buying goods 、 Virtual money transfer, etc . as follows : among Web A For existence CSRF Loopholes in the website ,Web B Malicious websites built for attackers ,User C by Web A Legitimate users of the site .
3.CSRF Explanation of attack principle and process
(1) user C Open the browser , Visit trusted sites A, Enter the user name and password to log in to the website A;
(2) After the user information has been verified , Website A produce Cookie Information and return it to the browser , At this time, the user logs into the website A success , Can send request to website normally A;
(3) The user did not exit the website A Before , In the same browser , Open one TAB Page visit website B;
(4) Website B After receiving the user's request , Return some offensive code , And send a request to visit a third-party site A;
(5) After the browser receives the attack code , According to the website B Request , Carry... Without the user's knowledge Cookie Information , To the website A Request . Website A I don't know that the request was actually made by B Sponsored , So according to the user C Of Cookie Information to C Permission to process the request , Lead from website B The malicious code was executed .
4.CSRF Attack conditions
(1) The target sites are CSRF Loophole
(2) The victim logs in
(3) The victim clicks on the attack link
The second part :SSRF( Server request forgery )
1.SSRF Basic concepts
(Server-Side Request Forgery, Server side Request Forgery ): Generally speaking, we can forge requests initiated by the server , In order to get the data that the client can't get .SSRF The main reason for the vulnerability is that the interface provided by the server contains the content of the request URL Parameters , And not transmitted to the client URL Parameters are filtered . The harm caused by this vulnerability is :
(1)、 It can be used for external network 、 The intranet where the server is located 、 Local port scan , Get some services banner Information ;
(2)、 Attack an application running on an intranet or local network ( Like spillover );
(3)、 On the Intranet Web Application for fingerprint identification , By accessing the default file ;
(4)、 Attacking the Internet Web application , Mainly used Get Parameters can be used to implement the attack ( such as Struts2 Exploit ,SQL Injection, etc. );
(5)、 utilize File Protocol read local file .
2. Bypass SSRF Several methods of filtering
1、 change IP Address
Because it is possible to filter out the intranet IP The way .
You can bypass by hexadecimal :
192.168.0.1 Various base numbers of
(1)、8 Base format :0300.0250.0.1
(2)、16 Base format :0xC0.0xA8.0.1
(3)、10 Decimal integer format :3232235521
(4)、16 Decimal integer format :0xC0A80001
2、 Use parsing URL What happened
In some cases , Back end programs may have access to URL To analyze , For the parsed host Address filtering . At this time, there may be right URL Improper parameter parsing , This results in bypassing the filter .
When a back-end program passes an incorrect regular expression ( For example, will http Later on com Until the character content , That is to say www.baidu.com, Think it's an access request host Address time ) For the above URL When parsing the content of , It is likely that the visit URL Of host by www.baidu.com, And actually this URL The requested content is 192.168.0.1 Content on .
3. utilize DNS analysis
There is a magical service on the Internet ,http://xip.io When we visit the subdomain of this website , for example 192.168.0.1.xip.io, Will automatically redirect to 192.168.0.1.

4、 Through all kinds of non HTTP agreement
(1)、GOPHER agreement : adopt GOPHER We're in a URL Construct... In parameter Post perhaps Get request , So as to attack the intranet application . For example, we can use GOPHER Agreement with the intranet Redis Service attack .
(2)、File agreement :File The protocol is mainly used to access files in the local computer , We can go through similar file:/// File path this format to access local files on your computer . Use file The protocol can avoid the server program from accessing IP Filtering by . For example, we can go through file:///d:/1.txt To visit D Plate 1.txt The content of
Request:file:///C:/Windows/win.ini
5.DNS Rebinding

5
For user requests URL Parameters , First, the server will do DNS analysis , And then to DNS Server returned IP Address to determine , If it's on the blacklist , Just pass fall .
But in the whole process , The first time to ask DNS The service resolves the domain name to the second server to request URL There is a time between to check , Take advantage of the time difference , We can do it DNS Rebind attack .
To complete the DNS Rebind attack , We need a domain name , And specify the resolution of this domain name to our own DNS Server, In our controllable DNS Server Write resolution service on , Set up TTL Time is 0. So that we can attack , The whole attack process is :
(1)、 The server side gets URL Parameters , For the first time DNS analysis , Got a non intranet IP
(2)、 For what is obtained IP Judge , Found as non blacklist IP, Then through verification
(3)、 Server side for URL Visit , because DNS Server settings TTL by 0, So again DNS analysis , This time, DNS The server returns the intranet address .
(4)、 Since the verification has been bypassed , So the server returns the result of accessing the intranet resources .
Reference resources http://www.freebuf.com/articles/web/135342.html
边栏推荐
- 【Flink】RocksDB增量模式checkpoint大小持续增长的问题及解决
- dotnet-exec 0.4.0 released
- Records of ros2/dds/qos/ topics
- buuctf web
- cannot import name ‘escape’ from ‘jinja2’【成功解决】
- Precise delay based on Cortex-M3 and M4 (systick delay of system timer can be used for STM32, aducm4050, etc.)
- Region of Halcon: generation of multiple regions (3)
- ThinkPHP 5 log management
- ASEMI三相整流桥的工作原理
- OLAP analysis engine kylin4.0
猜你喜欢
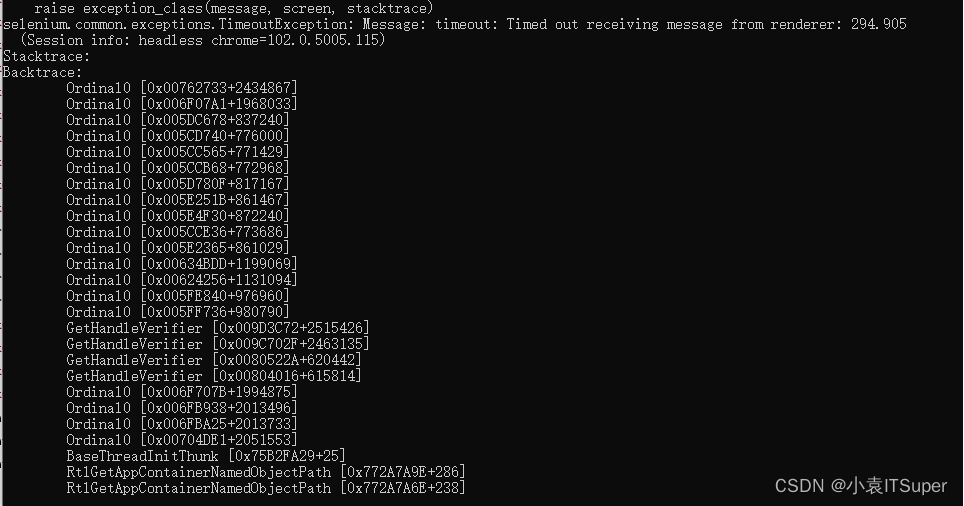
成功解决:selenium.common.exceptions.TimeoutException: Message: timeout: Timed out receiving message from
三角形类(构造与析构)

以太网是什么要怎么连接电脑

为什么TCP握手刚刚好是3次呢?
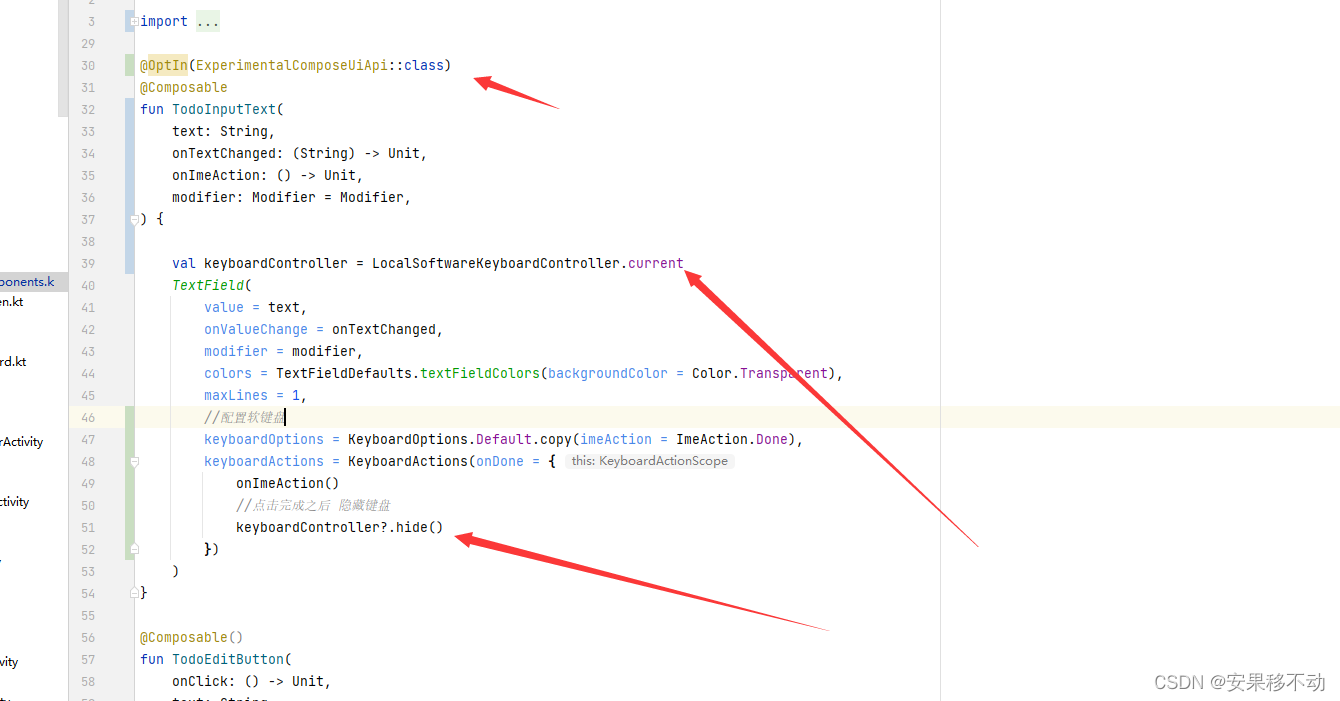
Kotlin Compose 监听软键盘 点击enter提交事件

WPF 使用 MAUI 的自绘制逻辑

Record the problem of C # print size once

Why does the SQL statement hit the index faster than it does not?
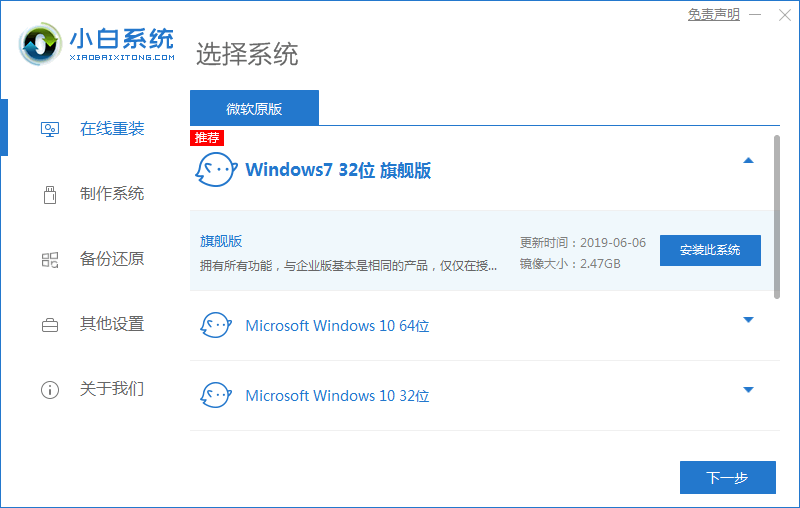
小白一键重装官网下载使用方法

大话云原生数据库中的存算分离
随机推荐
How to download and use Xiaobai one click reload on the official website
Kotlin compose listens to the soft keyboard and clicks enter to submit the event
Apache+php uploading large files
epplus复制模板后打印区域变小的问题
Integrate CDN to create the ultimate service experience for customers!
Introduction to the hardest core PWN in the whole network_ Graphic analysis
Coordinate system left multiply right multiply
DMA double buffer mode of stm32
《QDebug 2022年6月》
olap分析引擎——Kylin4.0
大话云原生数据库中的存算分离
[Flink] problems and solutions of the continuous growth of checkpoint size in rocksdb incremental mode
Successfully solved: selenium common. exceptions. TimeoutException: Message: timeout: Timed out receiving message from
Laravel Aurora push
leetcode1221. Split balance string
Efficient NoSQL database service Amazon dynamodb experience sharing
Swift rapid development
Méthode de récupération des données d'ouverture du disque dur à l'état solide
[image fusion] image fusion based on MATLAB directional discrete cosine transform and principal component analysis [including Matlab source code 1907]
Mysql interactive_ Timeout and wait_ Timeout differences
