当前位置:网站首页>Database learning - Database Security
Database learning - Database Security
2022-07-05 15:08:00 【Hulake_】
Catalog
One . Database security issues
1.1 The background of security issues
1.3 What is data confidentiality
Two . Introduction to computer security
2.1 Three kinds of security problems of computer system
2.1.1 What is computer system security
2.1.2 Computer security involves problems
2.2 Trusted computer system evaluation standard
2.2.1 TCSEC/TDI Security classification
3、 ... and . Database security control
3.1 Overview of database security control
3.1.2 Security model in computer system
3.1.3 Common methods of database security control
3.2 User identification and authentication (Identification & Authentication)
3.2.2 The user identifies his name or identity
3.3.1 Functions of access control mechanism
3.3.2 Common access control methods
Four . Autonomous access control method
4.2 Access rights in relational systems
4.3.3 WITH GRANT OPTION Clause
4.4.1 The function of withdrawing permission
4.4.2 Cascade recycling of permissions
4.4.3 SQL Flexible authorization mechanism
5、 ... and . Forced access control method
5.1 Definition of mandatory access control
5.4 Enforce access control rules
8.2 The basic idea of encryption
Nine . Summary of database security
One . Database security issues
1.1 The background of security issues
- One of the characteristics of database is that data can be shared ;
- But data sharing will inevitably bring about database security problems ;
- Data sharing in a database system cannot be unconditional ;
example : Military secrets 、 State secrets 、 New product experimental data 、 Market demand analysis 、 Marketing strategy 、 Sales plan 、 Customer profile 、 Medical records 、 Bank savings data
1.2 What is database security
The security of database means to protect database , Prevent data leakage caused by users' illegal use of the database 、 To alter or destroy .
1.3 What is data confidentiality
- Data confidentiality refers to whether users can keep confidential the confidential data after legally accessing them .
- Through the formulation of legal and ethical norms and policies and regulations to ensure .
Two . Introduction to computer security
2.1 Three kinds of security problems of computer system
2.1.1 What is computer system security
All kinds of security measures established and taken for computer system , To protect the hardware in the computer system 、 Software and data , Prevent the system from being damaged due to accidental or malicious reasons , Data is changed or leaked, etc .
2.1.2 Computer security involves problems
- Technical problems of the computer system itself :
- Computer security theory and strategy ;
- Computer security technology ;
- Management issues :
- security management ;
- Safety assessment ;
- Safety products ;
- Policies and regulations ;
2.2 Trusted computer system evaluation standard
In order to reduce and eliminate security attacks on the system , Countries have quoted or formulated a series of safety standards :
- TCSEC ( Orange Book );
- TDI ( Purple Book );
2.2.1 TCSEC/TDI Security classification
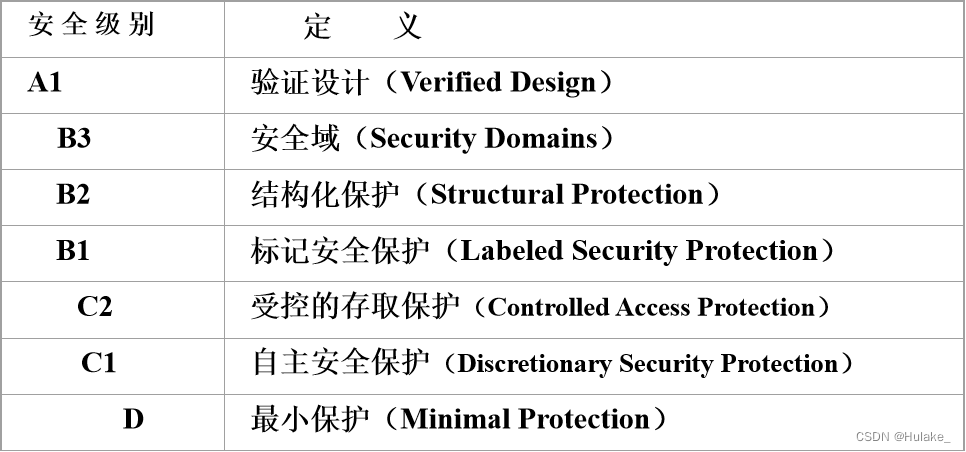
- Four groups (division) Seven levels :
- D ;
- C(C1,C2);
- B(B1,B2,B3);
- A(A1);
- Gradually increase the reliability or reliability of the system ;
- There is a partial downward compatible relationship between security levels , That is, the security provided by the higher security level should include all the protection requirements of the lower level , At the same time, it provides more or more perfect protection capabilities .

3、 ... and . Database security control
3.1 Overview of database security control
3.1.1 Illegal use of database
- The user writes a legal program to bypass DBMS And its authorization mechanism , Direct access through the operating system 、 Modify or back up the data in the database ;
- Direct or write applications to perform unauthorized operations ;
- We can deduce some confidential data from the database through several legitimate queries ;
- Acts that undermine safety may be unintentional , intended , Malicious .
3.1.2 Security model in computer system
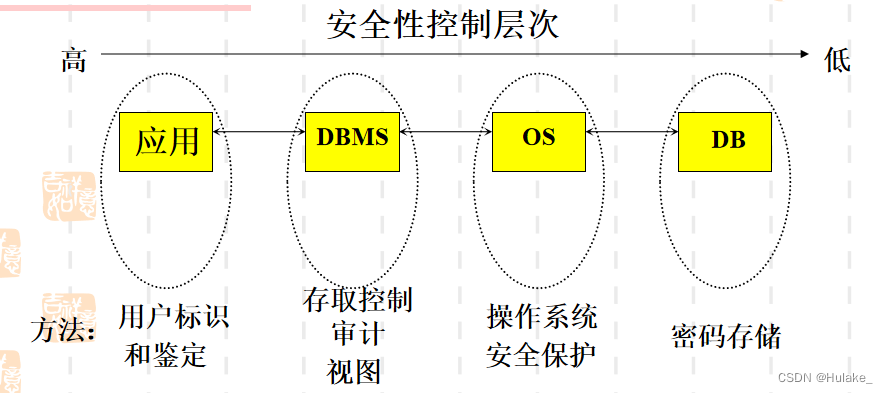
3.1.3 Common methods of database security control
- User identification and authentication ;
- Access control ;
- View ;
- Audit ;
- Password storage ;
3.2 User identification and authentication (Identification & Authentication)
The outermost security protection provided by the system ;
3.2.1 The basic method
- The system provides a certain way for users to identify their name or identity ;
- The system records the identification of all legal users ;
- Every time the user requests to enter the system , The system checks the identity provided by the user ;
- The right to use the machine will be provided only after passing the appraisal ;
- User identification and authentication can be repeated many times ;
3.2.2 The user identifies his name or identity
- user name / password : It's easy , Easy to be stolen ;
- Each user has a predetermined calculation process or function :
- The system provides a random number ;
- Users calculate according to their pre agreed calculation process or function ;
- The system identifies the user's identity according to the user's calculation results ;
3.3 Access control
3.3.1 Functions of access control mechanism
Composition of access control mechanism :
- Define access rights ;
- Check access rights ;
The definition of user rights and the check mechanism of legal rights together constitute DBMS Security subsystem of ;
1) Define access rights
In the database system , In order to ensure that users can only access the data they have the right to access , Access rights must be defined for each user in advance .
2) Check access rights
For users who have obtained the right to use the computer through authentication ( That is, legal users ), The system controls his various operation requests according to his access permission definitions , Make sure he only performs legal operations .
3.3.2 Common access control methods
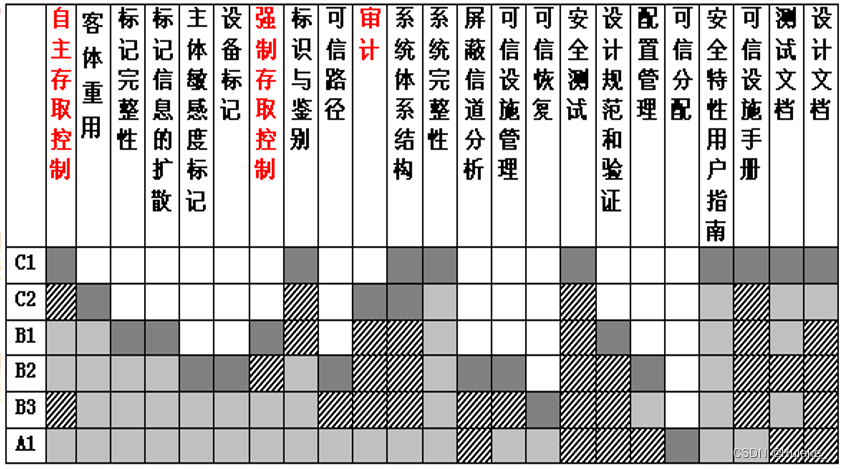
- Autonomous access control (Discretionary Access Control , abbreviation DAC):C2 level —— flexible ;
- Forced access control (Mandatory Access Control, abbreviation MAC):B1 level —— Strictly ;
Four . Autonomous access control method
4.1 Access rights
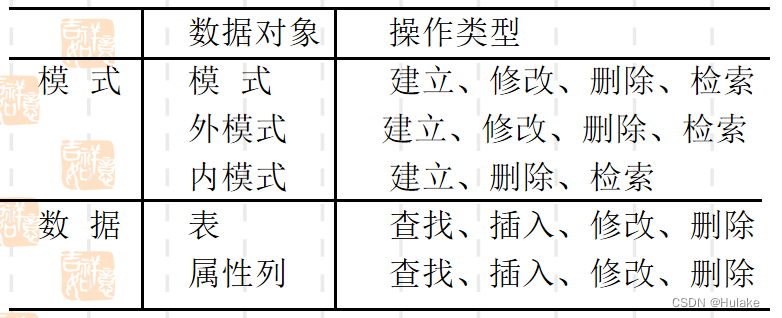
Access rights consist of two elements :
- Data objects ;
- Operation type ;
4.2 Access rights in relational systems
4.3 to grant authorization
- GRANT The general format of the statement :
GRANT < jurisdiction >[,< jurisdiction >]...
[ON < object type > < Object name >]
TO < user >[,< user >]...
[WITH GRANT OPTION];
- Who defines ?DBA And the creator of the table ( That is, the owner of the table );
- REVOKE function : Grant the specified operation permission to the specified user... For the specified operation object .
4.3.1 Operating authority
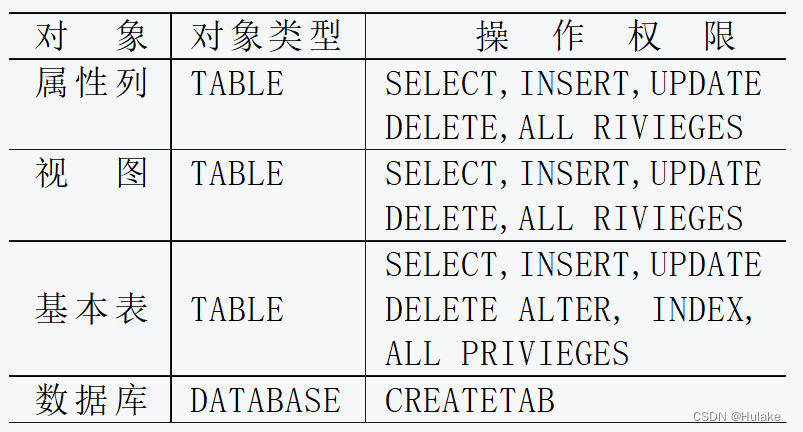
4.3.2 User's rights
- Build table (CREATETAB) Authority : Belong to DBA;
- DBA grant --> Ordinary users ;
- The owner of the basic table or view has all operation permissions on the table or view ;
- Users who accept permissions :
- One or more specific users ;
- PUBLIC( All users );
4.3.3 WITH GRANT OPTION Clause
- It specifies WITH GRANT OPTION Clause : Users who have obtained certain permissions can also grant such permissions to other users .
- Is not specified WITH GRANT OPTION Clause : Users with certain permissions can only use this permission , The permission cannot be propagated
4.4 Take back authority
4.4.1 The function of withdrawing permission
- REVOKE The general format of the statement is :
REVOKE < jurisdiction >[,< jurisdiction >]...
[ON < object type > < Object name >]
FROM < user >[,< user >]...;
- function : Withdraw the specified permission on the specified object from the specified user
4.4.2 Cascade recycling of permissions
- The system will recover directly or indirectly from U5 Get the right SC Tabular INSERT jurisdiction : -->U5--> U6--> U7
- Take back U5、U6、U7 Get right SC Tabular INSERT jurisdiction : <--U5<-- U6<-- U7
4.4.3 SQL Flexible authorization mechanism
- DBA Have all permissions on all objects in the database , Different permissions can be granted to different users according to the needs of the application .
- Users have all the operation permissions for the basic tables and views they have created , And you can use GRANT Statement grants some of these permissions to other users .
- Authorized users, if any “ Continue to authorize ” Permission of , You can also grant the obtained permission to other users .
- All delegated powers can be used when necessary REVOKE Statement retraction .
5、 ... and . Forced access control method
5.1 Definition of mandatory access control
- Forced access control (MAC) It refers to the system to ensure a higher degree of security , according to TDI/TCSEC Security policy requirements in the standard , The mandatory access inspection means adopted .
- MAC Not directly perceived or controlled by users .
- MAC It is applicable to departments with strict and fixed classification of data : The military 、 Government sector ;
5.2 Subject and object
- stay MAC in ,DBMS All entities managed are divided into subject and object Subject is the activity entity in the system ;
- DBMS The actual users managed
- Processes that represent users An object is a passive entity in a system , Is manipulated by the subject file 、 Base watch 、 Indexes 、 View ;
5.3 Sensitivity markers
- For subject and object ,DBMS For each of them ( value ) Assign a sensitivity marker (Label);
- Sensitivity markers are divided into several levels :
- Top secret (Top Secret);
- confidential (Secret);
- trusted (Confidential);
- Open (Public);
- The sensitivity marker of the subject is called the license level (Clearance Level)
- The sensitivity marker of an object is called the secret level (Classification Level)
- MAC The mechanism is through the comparison of the subject Label And objective Label, Finally determine whether the subject can access the object
5.4 Enforce access control rules
When a user ( Or a subject ) To mark label When registering with the system , The system requires that his access to any object must follow the following two rules :
- Only if the subject's license level is greater than or equal to the object's secret level , The subject can read the corresponding object ;
- Only if the license level of the subject is equal to the secret level of the object , The subject can write the corresponding object .
6、 ... and . View mechanism
- The view mechanism hides the data to be kept secret from users who have no right to access the data ;
- The main function of view mechanism is to provide data independence , Its security protection function is too subtle , It is often far from meeting the requirements of the application system .
The view mechanism is used in conjunction with the authorization mechanism :
- First, use the view mechanism to shield some confidential data ;
- The access rights are further defined above the view ;
- It indirectly implements the definition of user rights supporting access predicates ;
7、 ... and . Audit
7.1 Concept of audit
- Enable a dedicated audit log (Audit Log): Record all the user's operations on the database ;
- DBA You can use the trace information in the audit log : Find out who has access to data illegally ;
- C2 Above security level DBMS Must have audit function ;
7.2 Optional audit function
- Auditing takes time and space ;
- DBA According to the security requirements of the application , Flexibly turn on or off the audit function .
7.3 Audit function related
- Mandatory mechanisms : User identification and authentication 、 Access control 、 View ;
- Preventive monitoring means : Audit Technology
8、 ... and . Data encryption
8.1 Data encryption
An effective means to prevent the data in the database from being classified in storage and transmission ;
8.2 The basic idea of encryption
- According to a certain algorithm, the original data ( The term is clear text ,Plain text) Transform to unrecognizable format ( The term is ciphertext ,Cipher text);
- People who don't know the decryption algorithm can't know the content of the data ;
8.3 Encryption method
- Alternative method : Use key (Encryption Key) Convert every character in plaintext into a character in ciphertext ;
- Replacement method : Rearrange the characters of plaintext in different order ;
- Hybrid method : The United States 1977 The official encryption standard formulated in : Data encryption standard (Data Encryption Standard, abbreviation DES)
Nine . Summary of database security
- With the development of computer network , Data sharing is increasingly strengthened , The security of data is becoming more and more important .
- DBMS Is the core of managing data , Therefore, it must have a complete and effective security mechanism .
- Trusted computer system evaluation standard 》TCSEC/TDI It is the most important of a series of safety standards quoted or formulated by various countries .
- CSEC/TDI From security policy 、 responsibility 、 The four aspects of assurance and documentation describe the indicators of security level .
- There are many technologies and methods to realize the security of database system , The most important are access control technology and audit technology .
- At present, many large DBMS Reached C2 level , Its security version has reached B1;
- C2 Class DBMS It must have independent access control function and preliminary audit function ;
- B1 Class DBMS It must have mandatory access control and enhanced audit functions ;
- The autonomous access control function is generally through SQL Of GRANT Statement and REVOKE Statement to achieve ;
Ten . Database column
边栏推荐
- webRTC SDP mslabel lable
- "Sequelae" of the withdrawal of community group purchase from the city
- qt creater断点调试程序详解
- Select sort and bubble sort
- 美团优选管理层变动:老将刘薇调岗,前阿里高管加盟
- Live broadcast preview | how to implement Devops with automatic tools (welfare at the end of the article)
- [detailed explanation of Huawei machine test] character statistics and rearrangement
- Detailed explanation of QT creator breakpoint debugger
- Install and configure Jenkins
- 我想咨询一下,mysql一个事务对于多张表的更新,怎么保证数据一致性的?
猜你喜欢
Photoshop plug-in action related concepts actionlist actiondescriptor actionlist action execution load call delete PS plug-in development
面试突击62:group by 有哪些注意事项?

Visual task scheduling & drag and drop | scalph data integration based on Apache seatunnel

Your childhood happiness was contracted by it
CODING DevSecOps 助力金融企业跑出数字加速度
P1451 求细胞数量/1329:【例8.2】细胞
PyTorch二分类时BCELoss,CrossEntropyLoss,Sigmoid等的选择和使用

数据库学习——数据库安全性

Coding devsecops helps financial enterprises run out of digital acceleration

Photoshop插件-动作相关概念-ActionList-ActionDescriptor-ActionList-动作执行加载调用删除-PS插件开发
随机推荐
Handwriting promise and async await
Thymeleaf uses background custom tool classes to process text
安装配置Jenkins
Selection and use of bceloss, crossentropyloss, sigmoid, etc. in pytorch classification
The elimination strategy of redis
NBA赛事直播超清画质背后:阿里云视频云「窄带高清2.0」技术深度解读
一键更改多个文件名字
【C 题集】of Ⅷ
I collect multiple Oracle tables at the same time. After collecting for a while, I will report that Oracle's OGA memory is exceeded. Have you encountered it?
爱可可AI前沿推介(7.5)
Differences between IPv6 and IPv4 three departments including the office of network information technology promote IPv6 scale deployment
js亮瞎你眼的日期选择器
Common redis data types and application scenarios
Drive brushless DC motor based on Ti drv10970
Your childhood happiness was contracted by it
DVWA range clearance tutorial
Machine learning notes - gray wolf optimization
Cartoon: programmers don't repair computers!
CODING DevSecOps 助力金融企业跑出数字加速度
Redis' transaction mechanism
 https://blog.csdn.net/weixin_53919192/category_11813282.html?spm=1001.2014.3001.5482
https://blog.csdn.net/weixin_53919192/category_11813282.html?spm=1001.2014.3001.5482