当前位置:网站首页>【Prometheus】5. Alertmanager alarm (incomplete)
【Prometheus】5. Alertmanager alarm (incomplete)
2022-06-24 15:36:00 【Try something new for a long time】
1. Deploy Alertmanager And Prometheus signal communication , And create alarm rules
Download address 1:https://github.com/prometheus/alertmanager/releases
Download address 2:https://prometheus.io/download/
- download alertmanager wget https://github.com/prometheus/alertmanager/releases/download/v0.22.0-rc.0/alertmanager-0.22.0-rc.0.darwin-amd64.tar.gz
- decompression tar zxvf alertmanager-0.22.0-rc.0.darwin-amd64.tar.gz
- Modify the configuration file cd alertmanager-0.22.0-rc.0.darwin-amd64 && vim alertmanager.yml
- Check the configuration file ./amtool check-config alertmanager.yml
- start-up alertmanager ./alertmanager --config.file=alertmanager.yml
- stay prometheus Middle configuration alertmanager communicate
- Create alarm rules (prometheus Under the table of contents )
- restart prometheus systemctl restart prometheus
-----
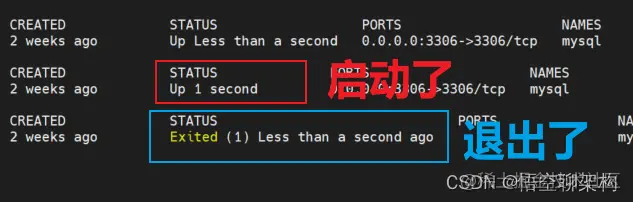
2. Alarm status
- Inactive: Nothing happened
- Pending: Threshold triggered , But the alarm duration... Is not met
- Firiing: Threshold triggered and alarm duration met , The alarm is sent to the recipient
3. Alarm allocation
A little .....
4. Alarm convergence ( grouping , Inhibition , silent )
5. Prometheus How can an alarm be triggered ?
6 . Write alarm rule cases
边栏推荐
- Domestic payment system and payment background construction
- "Industry foresight" future development trend of intelligent security monitoring industry
- FPGA based analog I ² C protocol system design (Part 2)
- [log service CLS] initial experience of Tencent cloud CLS log service
- Istio Troubleshooting: using istio to reserve ports causes pod startup failure
- The future of robots -- deep space exploration
- The security market has entered a trillion era, and the security B2B online mall system has been accurately connected to deepen the enterprise development path
- MySQL replication series 6- tables related to replication information
- Service visibility and observability
- Do you really know the difference between H5 and applet?
猜你喜欢
An accident caused by a MySQL misoperation, and the "high availability" cannot withstand it!

高速公路服务区智能一体机解决方案

Bert whitening vector dimension reduction and its application

【C语言刷题——Leetcode12道题】带你起飞,飞进垃圾堆

Stm32f1 and stm32cubeide programming examples -ws2812b full color LED driver (based on spi+dma)
Laravel8 uses faker to call factory to fill data

Method after charging the idea plug-in material theme UI

【我的OpenGL学习进阶之旅】OpenGL的坐标系的学习笔记

CVPR 2022 - Interpretation of selected papers of meituan technical team

Laravel 8 realizes auth login
随机推荐
Which securities company is better and safer for great wisdom to choose when opening an account
Is it safe for futures companies to open accounts
Two way combination of business and technology to build a bank data security management system
FPGA based analog I ² C protocol system design (Part 2)
Tencent cloud native intelligent data Lake Conference will be held, revealing the panoramic matrix of Tencent cloud data Lake products for the first time
Wi-Fi 7 来啦,它到底有多强?
[parameter configuration tutorial] how should the parameters in the RTMP streaming camera be configured?
How to build a high-performance go cache Library
Is it safe to open an account for flush stock on mobile phone!
Attacked! Cloud development monitoring alarm practice
Monitoring and warning | is the website attacked?
为什么企业实施WMS仓储管理系统很容易失败
Unimelb COMP20008 Note 2019 SM1 - Data formats
个人如何开户炒股 炒股开户安全吗
How to optimize performance
Task priority motion planning of floating base
Working with collections
Istio practical skill: enable accesslog locally
How to modify the login user name of easynvr video monitoring system?
How to achieve long-term development of voice social source code?