当前位置:网站首页>Vulnhub funbox: rookie (funbox2) target penetration
Vulnhub funbox: rookie (funbox2) target penetration
2022-07-24 05:38:00 【Outstanding, outstanding】
Vulnhub-Funbox: Rookie(funbox2) Target penetration
Vulnhub-Funbox: Rookie(funbox2) Penetration test
One . About the target
Running on the Vmware The target cannot be obtained in IP, Try bridging 、NAT、 Only the three modes of the host are fruitless , No choice but to use it VirtualBox, but NAT And bridge mode IP, Only in host-only The target machine can only be obtained in mode IP.
Two . IP And port detection

Found only open 21,22,80 port 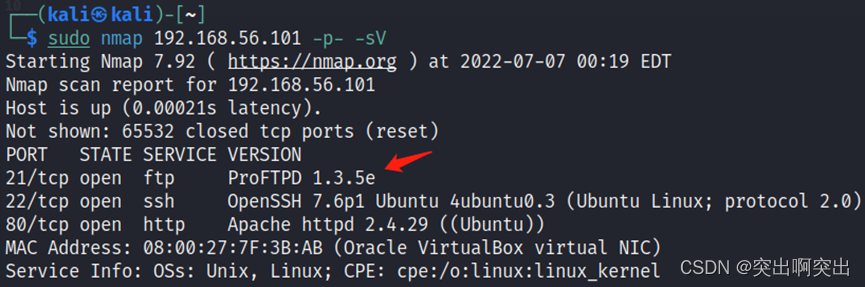
3、 ... and . 21 Port information collection

View above 2 Script , Found to be CVE-2015-3306 Any file copy 

It cannot be directly used after trying , Try another port **
Four . 80 Port information collection

Scan the directory , Find out robots.txt, However, it cannot be used 


There seems to be a deadlock , Can we go back to 21 Port to try ?
5、 ... and . FTP Anonymous logins
It suddenly occurred to me whether I forgot to try anonymous login just now …
user name :anonymous, The password is empty 
Check the directory , I found a bunch of compressed packages with file names very similar to user names , Download to the local decompression try 
It is found that the content of the file is id_rsa, But you need a password to decompress , Start using john Crack , Crack to tom.zip The password for iubire
notes : If you ask me why I don't use fcrackzip Crack , Because currently in host-only Pattern , and fcrackzip Not kali Bring their own , It needs to be installed by hand 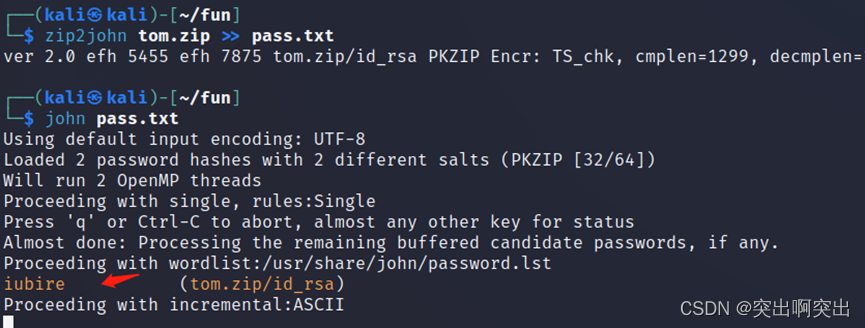
decompression tom.zip obtain id_rsa, Is a private key 
6、 ... and . ssh Key login
Log in with the key obtained above 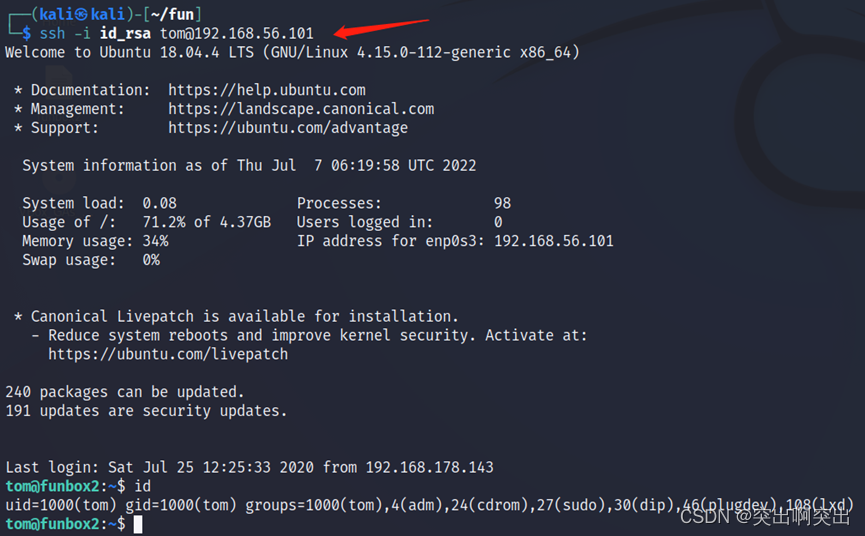
Discovery is a limited rbash,ls -la Check the directory 
View history command , It is found that data is written to the database , Much like user name and password (tom/xx11yy22!)
sudo Have a try , Password input xx11yy22!
found sudo Improper configuration , You can execute commands with all user permissions , Try switching root, You don't need a password ~
meaning , Unexpectedly, it's so right …
** summary :**ftp Anonymous logins —— File download —— Password cracking ——ssh Sign in ——sudo Improper allocation of rights
边栏推荐
- B站视频评论爬取——以鬼灭之刃为例(并将其存储到csv中)
- CESS 测试网上线!首个提供多元应用场景的去中心化存储网络
- Geoserver自动化上传Shapefile
- Canvas - fill
- Useref create dynamic reference
- Mobile software development ISO simple wechat
- 通用分页2.0
- 4. Draw a red triangle and a yellow square on the screen. Triangle in the back, small; Square in front, big. Using the fusion technology, the triangle can be seen through the square, and the source an
- Inventory Poka ecological potential project | cross chain characteristics to promote the prosperity of multi track
- Variables and constants in C language
猜你喜欢
随机推荐
波卡生态发展不设限的奥义——多维解读平行链
Draw a moving teapot on the screen. The teapot first moves slowly towards the screen, becoming smaller and smaller, becoming more and more blurred; Then it grows bigger and clearer, and keeps repeatin
jsp标签
波卡创始人 Gavin Wood:波卡治理 v2 会有哪些变化?
在 Polkadot 中进行创建的三种方式 —— 平行链、平行线程、智能合约
Web3 Foundation grant program empowers developers to review four successful projects
XML解析
Hex to RGB
利用流媒体将RSTP流转成WEB端播放(二)[可回看]
special effects - 鼠标移动,出现星星拖尾
树状结构+节点
随意写写 cookie,sessionStorage,localStorage和session
Vulnhub-Funbox: Rookie(Funbox2)靶机渗透
盘点波卡生态潜力项目 | 跨链特性促进多赛道繁荣
再次聊聊浏览器缓存
OpenGL simulates the process of a ball falling to the ground and bouncing up in real life. Draw a ball on the screen, and the ball will fall from top to bottom, hit the ground and bounce up again.
visibility:hidden 和 display:none
浏览器的本地存储
Draw a square on the screen and use ice BMP texture maps the square; Draw a yellow teapot after the square. Assuming that the square is transparent, draw the mixed effect of teapot and square; Adjust
OpenGL draws two points on the screen, a blue point on the right, using anti aliasing technology, and a red point on the left, without anti aliasing technology. Compare the difference between the two






![利用流媒体将RSTP流转成WEB端播放(二)[可回看]](/img/b9/2c0e6eb19acaa2356ff49f6e272826.png)