当前位置:网站首页>In the digital era, enterprises must do well in user information security
In the digital era, enterprises must do well in user information security
2022-06-28 03:13:00 【Software test network】
《 Network security law 》 Five years of implementation , China's Internet industry is changing from web2.0 The trend of the times web3.0 Time . On the mobile Internet 、 Cloud computing and other related fields , We are in a new era of big data , The importance of user information security has far exceeded that of any previous era .

In the face of mobility 、 Digital security situation , Multipoint DMALL Raise information security to the strategic development level of the enterprise , Strengthen attention and input at the technical level , It has established a strong network security force in line with multi-point characteristic services , The business is strictly required to meet the network security industry standards , for example ISO27001 Information security management system certification 、GDPR Other norms , Continuously improve the enterprise itself and the majority of users 、 Consumer data security .
In the process of enterprise production , Network security challenges exist in all aspects . If the user information and data are not properly protected , It is very likely to be punished by criminals 、 Bad businesses use illegal means to obtain , When the user is not allowed 、 Sell illegally without knowing it 、 Use , Yes ⽤ The privacy of the user 、 The right to know and so on all cause harm , what ⾄ Will threaten ⼈⾝ Security . Multipoint DMALL Attach great importance to user information security , basis 《 Data security law 》《 Personal information protection law 》, Obtain necessary information under the premise of user authorization , And store sensitive user information through dynamic encryption 、 Strictly control data permissions 、 Regularly audit data access logs, etc , Highly protect user information .
In promoting the construction of network security , Multipoint DMALL Work at multiple levels . For network infrastructure security , Complete the security baseline construction for each production server 、 Deploy host security products , Conduct security capability coverage vulnerability scanning 、 System patch check 、 Trojan virus monitoring 、 Monitor and intercept common intrusion behaviors, etc ; In every network environment 、 Network import and export deployment of various security analysis 、 The alarm 、 Interception equipment , for example IPS、 A firewall 、WEB Application firewall 、 Honeypot system ; In terms of network isolation , Different network environments cannot be interconnected , Ports only open service related ports , For example, the production environment and network environment are only open 80、443、8080 port .
For business code security , Multipoint DMALL Establish R & D process management according to its own code and business characteristics , And on this basis, design multi-point DMALL Of DevSecOps Ability , Inject safety requirements into product design , Provide code scanning tools during the code writing phase , Add... During product testing IAST Security scanning capability covers common security vulnerabilities , Conduct manual penetration test before the product goes online 、 Third party security company external security testing , Finally, it will be put into operation .
For safe operation , Daily operation of all safety equipment , Analyze device logs , Identify safety risks at the first time ; Launch multipoint safety emergency response center (DMSRC), Responsible for receiving safe communities 、 Third party security vulnerability notification , Make up for the problems of safety construction ; Conduct security penetration tests on all assets at multiple sites on a quarterly basis , Covering all business systems at multiple sites 、 Production environment 、 Mobile Internet applications , If any safety problem is found, the corresponding responsible person will be informed in time for repair 、 Retest , Eliminate security issues internally .
meanwhile , Multipoint DMALL implement 《 Network security emergency response process 》, The risk of network security will be avoided at the first time . for example , Yes log4j Of 0day Security vulnerability notification , After the announcement 2 All online services can be intercepted within hours log4j Security vulnerability attacks , stay 48 Complete all involved within hours log4j Application and rectification of vulnerabilities .
Protect user information security , What else do we need to do ? Multipoint DMALL As SaaS Service providers , Cannot do without “ cloud ” technology , A large number of microservices or Serverless technology . Multipoint DMALL The security team will continue to cultivate security technologies that are in line with business development , Build different security defenses 、 Monitoring equipment and platform tools , Build cloud native security capabilities , Vessel safety technology , Aspire to online safety and zero accidents . Protect the integrity of information 、 A secret 、 You can use 、 controllable , It is inseparable from the joint efforts of the whole industry and even the whole society . Information security confrontation is the confrontation between information and technology , We need to understand the attack techniques used by network attackers , So as to promote defense with attack ; We have better information about vulnerabilities than attackers , Master various security vulnerabilities and risks in front of the attacker , Fix the vulnerability before implementing the attack .
Here it is , We call on security vendors 、 Software manufacturer 、 Enterprises 、 White hat and other forces are working more closely , Create a healthier environment for users 、 Secure network environment .
边栏推荐
- 剑指 Offer 53 - I. 在排序数组中查找数字 I(改进二分)
- [today in history] June 15: the first mobile phone virus; AI master simahe was born; Chromebook launch
- Simple elk configuration to realize production level log collection and query practice
- RichView TRVStyle TextStyles
- Severe Tire Damage:世界上第一个在互联网上直播的摇滚乐队
- CMU puts forward a new NLP paradigm - reconstructing pre training, and achieving 134 high scores in college entrance examination English
- 如何判断线程池已经执行完所有任务了?
- 分布式事务TCC浅析
- 为什么大厂压力大,竞争大,还有这么多人热衷于大厂呢?
- 【活动早知道】LiveVideoStack近期活动一览
猜你喜欢
What if win11 cannot use dynamic wallpaper? Solution of win11 without dynamic wallpaper

Simple file transfer protocol TFTP

Severe Tire Damage:世界上第一个在互联网上直播的摇滚乐队

How to run unity webgl after packaging (Firefox configuration)

Gateway微服務路由使微服務靜態資源加載失敗
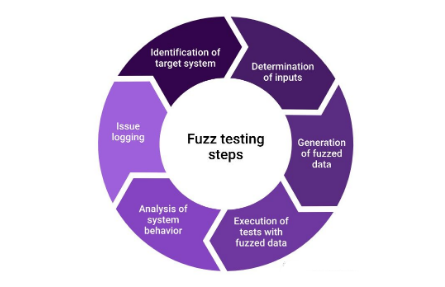
2021年软件测试工具总结——模糊测试工具

腾讯游戏发布40多款产品与项目 其中12款为新游戏

Basic flask: template rendering + template filtering + control statement
![[today in history] June 18: JD was born; The online store platform Etsy was established; Facebook releases Libra white paper](/img/88/6cdd2b604522261e2a88020c5d6ae7.jpg)
[today in history] June 18: JD was born; The online store platform Etsy was established; Facebook releases Libra white paper

Opencv -- geometric space transformation (affine transformation and projection transformation)
随机推荐
Notepad++--常用的插件
js清空对象和对象的值:
Arduino Esp8266 Web LED控制
isEmpty 和 isBlank 的用法區別
读书,使人内心宁静
项目实战!手把手教你 Jmeter 性能测试
抓包整理外篇fiddler————了解工具栏[一]
CI & CD 不可不知!
The first place on the list - the carrying rate of front-end equipment is up to 10%, and the top 10 suppliers of digital key solutions
RichView TRVStyle ParaStyles
Flask Foundation: template inheritance + static file configuration
Apache——阿帕奇简介
音视频技术开发周刊 | 251
Heartless sword Chinese English bilingual poem 004 Sword
多快好省,低门槛AI部署工具FastDeploy测试版来了!
没错,是水的一篇
Livedata interview question bank and answers -- 7 consecutive questions for livedata interview~
将PCAP转换为Json文件的神器:joy(安装篇)
apache、iis6、ii7独立ip主机屏蔽限制ip访问
[plug in -statistical] statistics the number of code lines and related data