当前位置:网站首页>Information collection for network security (2)
Information collection for network security (2)
2022-06-13 05:18:00 【Python's path to becoming a God】
Preface : ha-ha , Come on. , Statement : Mind mapping from Xiaodi penetration test
information gathering
one .CDN Bypass
1. Determine whether the website exists cdn technology
Super ping: If you return IP Is not the only , It means that there is cdn The server
2. common cdn Bypass technology
2.1 Subdomain query
DNS Inquire about :https://dnsdb.io/zh-cn/
Micro step online :https://x.threatbook.cn/
Online domain name information query :http://toolbar.netcraft.com/site_report?url=
DNS、IP Etc :http://viewdns.info/
CDN Inquire about IP:https://tools.ipip.net/cdn.php
SecurityTrails platform : https://securitytrails.com/domain/www.baidu.com/history/a
Online sub domain name and secondary domain name query :http://tools.bugscaner.com/subdomain/
ps:
In general ,www.XXX.com and XXX.com Point to the same DNS The server , Get into XXX.com Will automatically jump to www.XXX.com, therefore XXX.com No need for large flow , Don't do it CDN. If added www I can't detect it , You can try to get rid of , Maybe you can get the truth IP 了
2.2 Mail service query
Mail service query many companies will have a mailbox server , Most of these email servers don't do CDN Of . Because email servers are usually accessed by insiders of the company , So most don't do CDN. therefore , Then we can according to the email sent to us by the other party's email server , To judge each other's IP Address
2.3. Abroad IP Check the website
Some websites to save costs , Will not put CDN Deployed abroad . Suppose your own Internet company has a website , But your customer base is mainly in China , Because there are not many foreign users , So it's not worth building abroad CDN, Therefore, visiting domestic websites from abroad is likely to directly visit the truth of the main station ip Address .
https://tools.ipip.net/cdn.php
2.4. Legacy documents , Scan the whole network
Some sites were built at the beginning , Will use some files to test the site , for example “phpinfo()” file , Such documents may contain real IP Address . You can use Google Search engine search keywords “site:xxx.com inurl:phpinfo.php”, Search the site for legacy files
2.5. The dark engine searches for files
google,shodan,zoomeye,fofa etc.
Specific files here , It refers to the of the site icon file , That is, the icon of the website , General view of the web page source code can find , Approximate format “http://www.xx.com/favicon.ico”. stay shodan Search website icon The syntax of the icon is :http.favicon.hash:hash value ,hash Is an unknown random number , We can go through shodan Syntax to see what has been shodan Of the included websites hash value , To further obtain all with a certain icon Website .
obtain icon Of hash value
2.6.dns Historical record
The site is using CDN Before service , It's true IP The address may be DNS The server recorded , Now we can go through DNS History records find the real goal IP. and “ Look at ” It's often said ddos Attack or traffic exhaustion attack , Open online CDN When , Will flow by Region , For example, this node has 100M Traffic , When this flow runs out , When users visit the website again, they will visit the real ip Address .
The intelligence community :
https://x.threatbook.cnDNSdb
https://dnsdb.io/zh-cn/
Ii. . Site construction and waf
Preface
Information collection is very important for the early stage of penetration testing , Because only after we have enough information about the target website or target host , We can better detect vulnerabilities . In security testing , Information collection is a very important link , The information of this link will affect the subsequent success probability , How much information you have will determine the size of the opportunity to find vulnerabilities , In other words, the test task that determines whether the goal can be completed
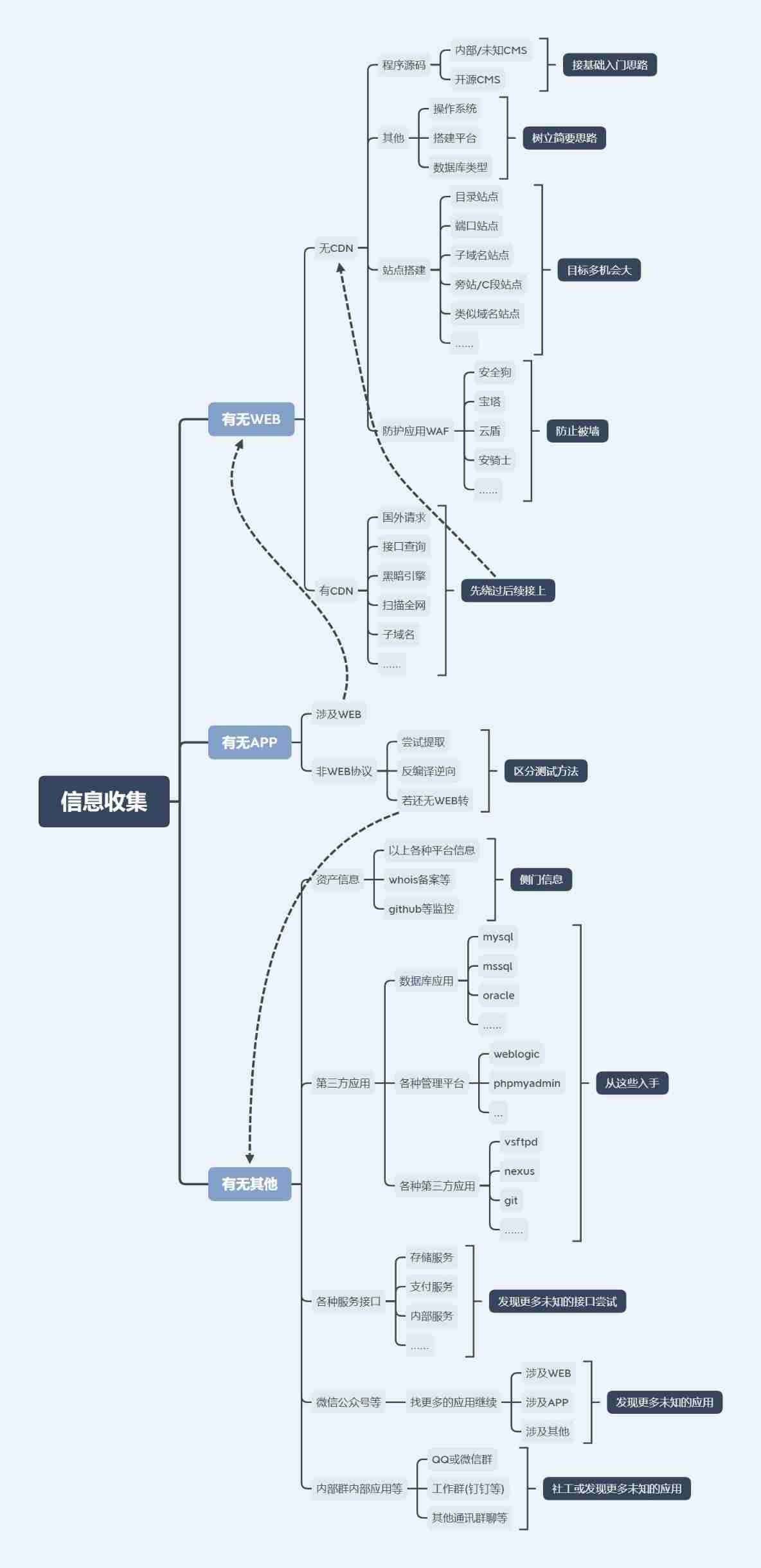
Site construction analysis
1. Directory site
The principle is a website , But the difference is the difference in the directory
for example :D:\tools\PHPstudy\PHPTutorial\WWW\DVWA-master and D:\tools\PHPstudy\PHPTutorial\WWW\mantisbt-2.25.0 The only difference between the two is the directory path
But two websites are two sets of programs , There is a loophole in the source code of a website , Another website will suffer , It is equivalent to giving two sets of vulnerability schemes
You can find... Through the directory scanning tool
2. Port class site
On the same server , Separate websites with ports , A website has a security problem , It will also lead to security problems on another website
3. Subdomain site
If IP Different , Then the two sites may not be on the same server
4. Similar to name site
From the same company's website , Change based on suffix


5. sidenote ,c Segment site
- sidenote
Marginal note is an intrusion method , Literally, it means -“ Inject... From the side ”, Exploit the vulnerabilities of different websites on the same host to get webshell, Thus, the physical path of the user exposed by the program or service on the host can be used for intrusion . Different sites on the same server . Two or more websites are placed on the same server , One of the websites is the target .
- c paragraph
Different servers and different sites in the same network segment . The website has one or more sites , Through the server IP Address of the network segment to test
6. Build a software feature site
Integrated construction software : pagoda 、PHPstudy、WMAP、INMAP(Nginx)
The conventional building software has the default account and password of the conventional database , If the builder doesn't change it , Can become a breakthrough idea .
WAF protective
1. What is? waf
Web Application protection system ( Also known as : Website application level intrusion prevention system . english :Web Application Firewall, abbreviation : WAF). Use an internationally accepted saying :Web The application firewall is designed by performing a series of actions against HTTP/HTTPS The security policy for Web An application that provides protection .
It is divided into : Hardware form and software form .
Firewalls purchased in security companies are hardware , Personal websites and small businesses are software .
2. How to quickly identify waf
Sqlmap Is a detection and utilization SQLi Vulnerability tools , Is based on python To write , The recognition rate in the industry is high ,sqlmap Used to detect WAF Types want to compare Wafw00f More for .
Sqlmap Used to detect every kind of WAF The equipment is a python file , Also from cookie Information or return header information to judge .
command :python sqlmap.py -u “[http://www.XXXXX.org/1.php?id=1]"-identify-waf( It seems that similar dynamic parameters can only be used if they are or modified by themselves )
3. distinguish waf Significance for safety testing
If the target is found to have WAF Words , Do not scan with a scanning tool
3 . Asset monitoring
POC、EXP、Payload And Shellcode( Original link portal )
- Concept
POC: Full name ’ Proof of Concept ', chinese ’ Proof of concept ’ , It often refers to a piece of code that proves a vulnerability .
EXP: Full name ’ Exploit ', chinese ’ utilize ', It refers to the action of using system vulnerability to attack .
Payload: chinese ’ Payload ', Success exploit after , Code or instruction actually executed in the target system .
Shellcode: Simple translation ’ shell Code ', yes Payload A kind of , Because of its positive establishment / reverse shell And get the name .
- Some attention
POC Is used to prove the existence of vulnerabilities ,EXP Is used to exploit vulnerabilities , The two are usually not in the same category , Or say ,PoC It's usually harmless ,Exp Usually harmful , With POC, Only then EXP.
Payload There are many kinds of , It can be Shellcode, It can also be a system command directly . The same Payload Can be used for multiple vulnerabilities , But each vulnerability has its own EXP, In other words, there is no universal EXP.
Shellcode There are many kinds , Including positive , In reverse , even to the extent that meterpreter.
Shellcode And Shellshcok Is not a ,Shellshock especially 14 Discovered in 2003 Shellshock Loophole .
- Payload modular
stay Metasploit Framework 6 There is one in the big module Payload modular , There are... Under this module Single、Stager、Stages There are three types ,Single It's a all-in-one Of Payload, Do not rely on other files , So its volume will be relatively large ,Stager It is mainly used when the memory of the target computer is limited , You can transmit a smaller Stager Used to establish a connection ,Stages To use Stager Establish a connection to download the following Payload.Stager and Stages There are many types , Suitable for different scenes .
- summary
Imagine yourself as an agent , Your goal is to monitor an important person , One day you suspect that the window of the target's home may not be closed , So you came forward and pushed , As a result, it pushed away , This is a POC. Then you went back , Start preparing the infiltration plan for the next day , The next day you infiltrated his house through the same loophole , I checked all the important documents carefully , A hidden bug was installed when leaving , What you do on this day is a EXP, What you do at his house is different Payload, Just think of the bug as Shellcode Well !
Github monitor
Easy to collect and sort out the latest exp or poc Facilitate the discovery of assets related to test objectives
Various subdomain name queries
DNS, Keep on record , certificate
Global node request cdn
Enumerate or resolve subdomain names
Easy to find administrator related registration information
Dark engine related search
fofa,shodan,zoomeye
The official account of WeChat is acquired
Internal group internal application internal interface

The demo case
Monitor the latest EXP Release and others
#Title: wechat push CVE-2020
#Date: 2020-5-9
#Exploit Author: weixiao9188
#Version: 4.0
#Tested on: Linux,windows
#cd /root/sh/git/ && nohup python3 /root/sh/git/git.py &
#coding:UTF-8
import requests
import json
import time
import os
import pandas as pd
time_sleep = 60 # every other 20 Climb once a second
while(True):
headers1 = {
“User-Agent”: "Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko)
Chrome/70.0.3538.25 Safari/537.36 Core/1.70.3741.400 QQBrowser/10.5.3863.400"}
# Judge whether the file exists
datas = []
response1=None
response2=None
if os.path.exists(“olddata.csv”):
# If the file exists, each crawl 10 individual
df = pd.read_csv(“olddata.csv”, header=None)
datas = df.where(df.notnull(),None).values.tolist()# In the extracted data nan Turn into None
requests.packages.urllib3.disable_warnings()
response1 = requests.get(url=“https://api.github.com/search/repositories?q=CVE2020&sort=updated&per_page=10”,headers=headers1,verify=False)
response2 =
requests.get(url=“https://api.github.com/search/repositories?q=RCE&ssort=updated&per_page=10”,hea
ders=headers1,verify=False)
else:
# There is no crawling all
datas = []
requests.packages.urllib3.disable_warnings()
response1 = requests.get(url=“https://api.github.com/search/repositories?q=CVE2020&sort=updated&order=desc”,headers=headers1,verify=False)
response2 =
requests.get(url=“https://api.github.com/search/repositories?q=RCE&ssort=updated&order=desc”,heade
rs=headers1,verify=False)
data1 = json.loads(response1.text)
data2 = json.loads(response2.text)
for j in [data1[“items”],data2[“items”]]:
for i in j:
s = {“name”:i[‘name’],“html”:i[‘html_url’],“description”:i[‘description’]}
s1 =[i[‘name’],i[‘html_url’],i[‘description’]]
if s1 not in datas:
data1 = json.loads(response1.text)
data2 = json.loads(response2.text)
for j in [data1[“items”],data2[“items”]]:
for i in j:
s = {“name”:i[‘name’],“html”:i[‘html_url’],“description”:i[‘description’]}
s1 =[i[‘name’],i[‘html_url’],i[‘description’]]
if s1 not in datas:
#print(s1)
边栏推荐
- C language learning log 12.5
- Mysql database crud operation
- RT thread console device initialization
- C language learning log 12.25
- Dynamic programming - longest common substring
- Chapter 15 mechanism: Address Translation
- Qmessagebox in pyqt5
- Customer information management system - C language
- Solutions to conflicts between xampp and VMware port 443
- OpenCV中的saturate操作(饱和操作)究竟是怎么回事
猜你喜欢
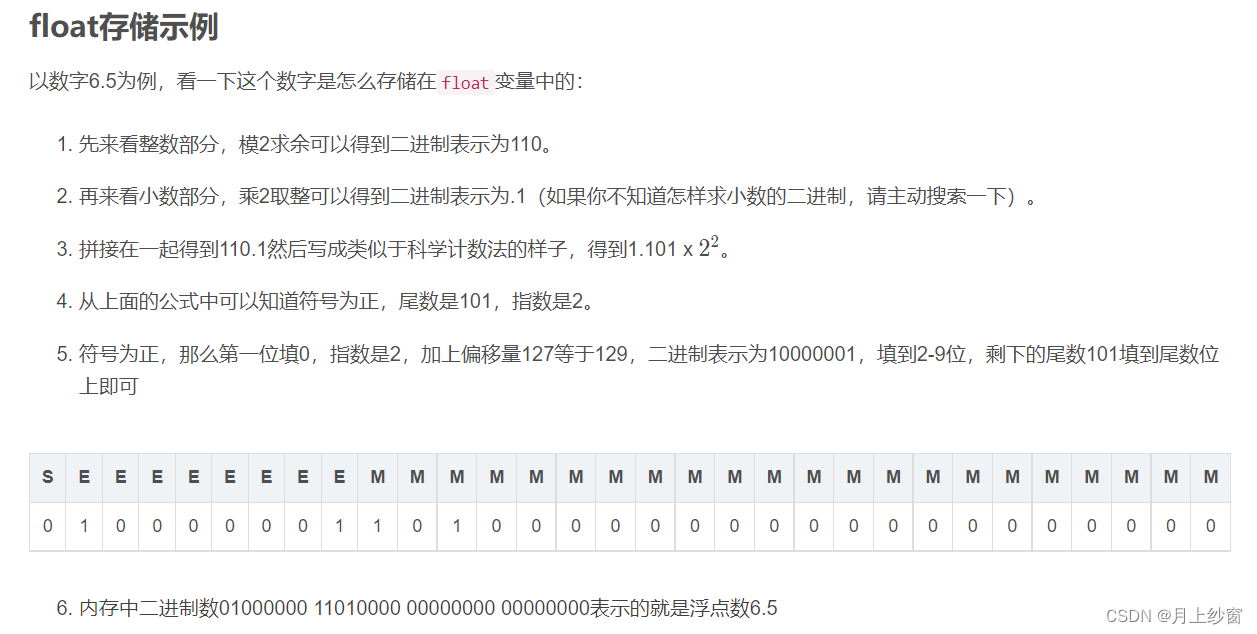
float类型取值范围

RTSP streaming using easydarwin+ffmpeg

Case - the list set stores student objects and traverses them in three ways

Database design

Recursion and recursion

Simple SR: best buddy Gans for highly detailed image super resolution

QT interface rendering style

Luogu p1036 number selection

Wampserver (MySQL) installation

What is the saturate operation in opencv
随机推荐
Chapter 2 process management
MySQL table data modification
Chapter 15 mechanism: Address Translation
RTSP streaming using easydarwin+ffmpeg
Modification and analysis of libcoap source code by Hongmeng device discovery module
Small project - household income and expenditure software (2)
Listiterator list iterator
Clause 26: avoid overloading universal reference types
Simple greedy strategy
What is the saturate operation in opencv
C language learning log 10.4
The problem of flex layout adaptive failure
Bm1z002fj-evk-001 startup evaluation
C language learning log 10.10
Pyqt5 controls qpixmap, qlineedit qsplitter, qcombobox
Shell instance
Windbos run command set
metaRTC4.0稳定版发布
redis
Std:: map insert details