当前位置:网站首页>Huawei computer test ~ offset realizes string encryption
Huawei computer test ~ offset realizes string encryption
2022-07-26 13:24:00 【weixin_ forty-three million seven hundred and sixty-six thousan】
1. Title Description : Give the original string str, Encryption is achieved by changing each letter of the string , The encryption method is in every letter str[i] Offset a specific array element a[i] The amount of . Array a The first three digits of have been assigned :a[0]=1,a[1]=2,a[2]=4, When i>=3 when , Array elements a[i]=a[i-1]+a[i-2]+a[i-3].
- for example : original text abcde After encryption bdgkr, The offsets are 1,2,4,7,13.
- Input description : The first line is an integer n, Express n Group test data . Each set of data contains a row , original text str( Contains only lowercase letters , Longer than 0 Less than 50).
- Output description : Each group of test data output one line , It means ciphertext .
// String offset xy -> ya , abcde -> bdgkr
public static void tm001(){
Scanner scanner = new Scanner(System.in);
while (scanner.hasNext()){
String line1 = scanner.nextLine();
int count = Integer.parseInt(line1);
List<String> stringList = new ArrayList<>();
int maxLen = 0;
for (int i = 0; i < count; i++) {
String input = scanner.nextLine();
if (input.length() > maxLen){
maxLen = input.length();
}
stringList.add(input);
}
// Calculate directly from the maximum length Move step set Calculate only once
int[] moveArr = new int[Math.max(maxLen, 3)];
moveArr[0] = 1;
moveArr[1] = 2;
moveArr[2] = 4;
for (int i = 3; i < maxLen; i++) {
// When adding Take the remainder Prevent the stack from exceeding int Range
// in consideration of Integer.MAX_VALUE = 2147483647, Directly remainder the result Ensure that each number is not greater than 26
moveArr[i] = (moveArr[i-1] + moveArr[i-2] + moveArr[i-3]) % 26;// 26 Letters
}
for (String line : stringList) {
char[] chars = line.toCharArray();
StringBuilder stringBuilder = new StringBuilder();
for (int i = 0; i < chars.length; i++) {
int move = moveArr[i];
// 'a' = 97 , 'z' = 122
// prevent appear 25 + 25 Etc. greater than 26 The situation of Take the mold again
int result = ((chars[i] - 97) + move)%26 + 97; // 26 Letters Subscript from 0 Start ~25
stringBuilder.append((char)result);
}
System.out.println(stringBuilder);
}
}
}
边栏推荐
- B+树(5)myISAM简介 --mysql从入门到精通(十七)
- A college archives management system based on asp.net
- 基于WebRTC和WebSocket实现的聊天系统
- Some practical operations of vector
- [5gc] what is 5g slice? How does 5g slice work?
- 异步线程池在开发中的使用
- [flower carving hands-on] fun music visualization series small project (12) -- meter tube fast rhythm light
- AI theory knowledge map 1 Foundation
- pomerium
- LeetCode 69. x 的平方根
猜你喜欢

【花雕动手做】有趣好玩的音乐可视化系列小项目(12)---米管快速节奏灯

我们被一个 kong 的性能 bug 折腾了一个通宵
![[applet] why can't the onreachbottom event be triggered? (one second)](/img/da/3641040c63f6db4d227dcf2ff89919.png)
[applet] why can't the onreachbottom event be triggered? (one second)

Precautions for triggering pytest.main() from other files

Kubelet CRI container runtime

Algorithm -- continuous sequence (kotlin)

Elementary notes of binary tree

3D modeling and rendering based on B é zier curve
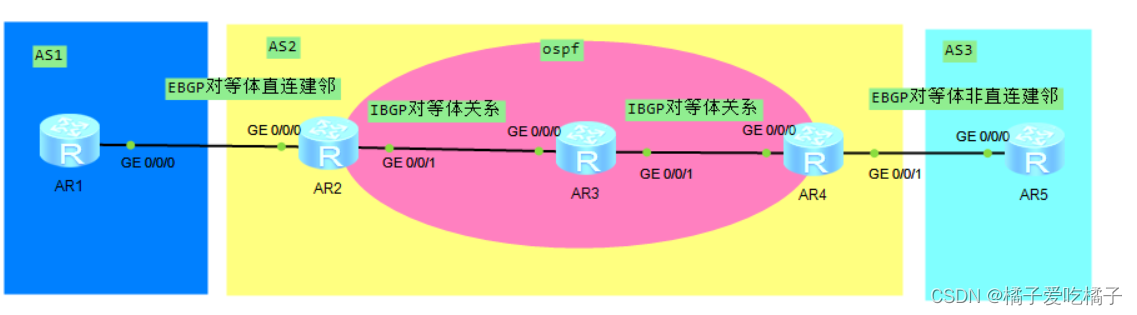
Hcip day 11 comparison (BGP configuration and release)

Dimension disaster dimension disaster suspense
随机推荐
解决远程主机无法连接mysql数据库的问题
B+ tree index use (6) leftmost principle -- MySQL from entry to proficiency (18)
B+树索引使用(8)排序使用及其注意事项(二十)
Leetcode 1523. count odd numbers within the interval
panic: Error 1045: Access denied for user ‘root‘@‘117.61.242.215‘ (using password: YES)
key&key_ Len & ref & filtered (4) - MySQL execution plan (50)
Slam 02. overall framework
基于ASP.NET的某高校学院档案管理系统
Hcip day 11 comparison (BGP configuration and release)
Detailed explanation of factory mode
Codeforces round 810 (Div. 2) [competition record]
学习pinia 介绍-State-Getters-Actions-Plugins
Leetcode 217. there are duplicate elements
[5g] what are Cu and Du in 5g?
B+ tree (5) introduction to MyISAM -- MySQL from getting started to mastering (17)
Research status and pain points of deep learning 3D human posture estimation at home and abroad
pomerium
The child component triggers the defineemits of the parent component: the child component passes values to the parent component
Target detection network r-cnn series
Flutter multi-channel packaging operation