当前位置:网站首页>RSA encryption and decryption details
RSA encryption and decryption details
2022-06-26 17:51:00 【lmn_】

0x01 RSA Summary
RSA The algorithm is an asymmetric cryptographic algorithm . Asymmetric cryptography is also called public key cryptography , It means that each pair of encryption contains a public key ( May be known to others ) And a private key ( May not be known to everyone ). Effective security requires maintaining the privacy of the private key ; Public keys can be publicly distributed without compromising security .
RSA The security of depends on the practical difficulty of decomposing the product of two large primes , But relatively slow , Can be called “ Break down the problem ”.
RSA application
- The client sends its public key to the server and requests some data
- The server encrypts the data with the public key of the client and sends the encrypted data
- The client receives this data and decrypts it
0x02 RSA Detailed algorithm flow
RSA Four steps of algorithm
- Key generation
- Key distribution
- encryption
- Decrypt
About RSA The relevant formula
n = p * q
ø(n) = (p - 1) * (q - 1)
ed ≡ 1 mod ø(n)
c = m**e mod n
m = c**d mod n
simple example
It is known that :P = 11,q = 29,e = 3
seek d
Through the formula :
ø(n) = (p - 1) * (q - 1)
φ(n) = (p-1)(q-1) = (11-1)*(29-1) = 280
Through the formula :
ed ≡ 1 mod ø(n)“≡” It's the sign of congruence in number theory
If two integers ed and 1 Satisfy ed-1 Can be ø(n) to be divisible by , It's called an integer ed And 1 To mold ø(n) congruence1 < d < ø(n)
3d ≡ 1 mod 280
3d mod 280 = 1
d = 187
Through the formula :
n = p * q
n = 11 * 29 = 319
Public key (n,e)
Private key (n,d)
obtain :
Public key (319,3)
Private key (319,187)

Or use a script to solve d:
gmpy2.invert(e,(p-1)*(q-1))
What is the maximum number that can be encrypted with this key pair
The encryption function is :
c(m) = m^e mod nThe decryption function is :
m(c) = c^d mod n
RSA The length of the name text that the algorithm can encrypt at one time is proportional to the length of the key .
len_in_byte(raw_data) = len_in_bit(key)/8-11
If less than this length , You need to supplement the data , be called padding, Without data complement, users cannot determine the true length of the decrypted content .
n The length of the key is the length of the key ,n = 319,n The binary of is 100111111, The key is 9 position ,RSA The maximum length of the actual encrypted plaintext is also 1024bits
When encrypting plaintext m = 23 when , Seeking ciphertext c
The encryption function is :
c(m) = m^e mod n

c(m) = 23^3 mod 319 = 12167 mod 319
c(m) = 45
import gmpy2
n = 319
e = 3
m = 23
print(pow(m, e, n))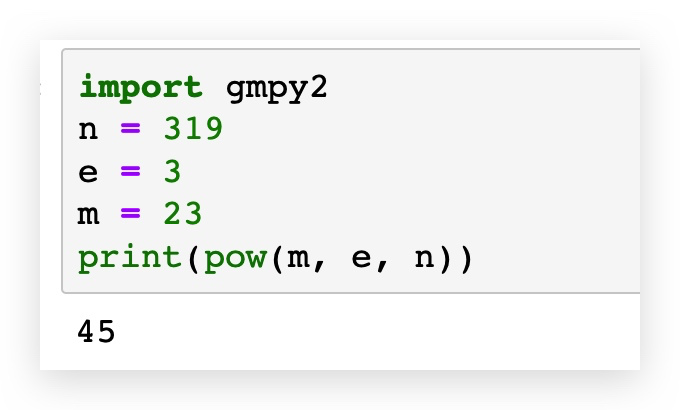
When ciphertext c = 23 when , Ask for clear text m
The decryption function is :
m(c) = c^d mod n
m(c) = 23^187 mod 319
m(c) = 199
import gmpy2
n = 319
d = 187
c = 23
print(pow(c,d,n))

边栏推荐
- 解决pycharm里面每个字母占一格空格的问题
- 背包问题求方案数
- Distributed Architecture Overview
- 【Unity】在Unity中使用C#执行外部文件,如.exe或者.bat
- Leetcode - 226. Retourner l'arbre binaire (bfs)
- How does Guosen Securities open an account? Is it safe to open a stock account through the link
- 一起备战蓝桥杯与CCF-CSP之大模拟炉石传说
- 无需人工先验!港大&同济&LunarAI&旷视提出基于语义分组的自监督视觉表征学习,显著提升目标检测、实例分割和语义分割任务!
- 二分查找法-1
- [code Capriccio - dynamic planning] t583. Deleting two strings
猜你喜欢

#26class中get和set设置

数字签名标准(DSS)
ACL 2022 | zero sample multilingual extracted text summarization based on neural label search

Knapsack problem with dependency

Rich professional product lines, and Jiangling Ford Lingrui · Jijing version is listed

DoS及攻擊方法詳解
Niuke network: Design LRU cache structure design LFU cache structure

14《MySQL 教程》INSERT 插入数据

next(iter(dataloader))的一点点体会

Ndroid development from introduction to mastery Chapter 2: view and ViewGroup
随机推荐
map和filter方法对于稀缺数组的处理
ZCMU--1367: Data Structure
#25class的类继承
DoS及攻击方法详解
玩转Linux,轻松安装配置MySQL
Live broadcast preview | how can programmers improve R & D efficiency? On the evening of June 21, the video number and station B will broadcast live at the same time. See you or leave!
Microservice architecture practice: user login and account switching design, order query design of the mall
接水面试题
Microservice architecture practice: business management background and SSO design, SSO client design
KDD 2022 | 如何在跨域推荐中使用对比学习?
国信证券怎么开户?通过链接办理股票开户安全吗
js强制转换
分布式缓存/缓存集群简介
halcon之区域:多种区域(Region)特征(5)
贝叶斯网络详解
Platform management background and merchant menu resource management: Design of platform management background data service
LeetCode——226. Flip binary tree (BFS)
直播预告|程序员进击,如何提升研发效能?6月21日晚视频号、B站同步直播,不见不散!
next(iter(dataloader))的一点点体会
【uniapp】uniapp手机端使用uni.navigateBack失效问题解决