当前位置:网站首页>Overview of cross chain protocol IBC
Overview of cross chain protocol IBC
2022-06-13 07:58:00 【Boiled soybeans in brine】
Cross Chain Protocol IBC summary
One . What is? IBC?
IBC Is the abbreviation of inter chain communication protocol (Inter-Blockchain Communication Protocol). Transfer data and status information between multiple different blockchain networks through packet exchange . The original use is more through IBC The protocol realizes cross chain token transfer .
IBC The goal of is to transfer application information between two independent seven layer networks , So we need something outside the chain relay Put packets in the chain A And chain B Relay between networks . chain B Receive the chain A The data must be able to independently verify the supporting information it contains , This proof represents the chain A A certain state on ( And its corresponding operation ) Authenticity . In order to make IBC The agreement works , Must rely on the underlying trust mechanism , Trust the chain A And chain B In their respective consensus algorithms , Also believe in light client authentication , Through the verification of block header information , Prove what happened on the blockchain .
Two . How to achieve IBC?
1. The life cycle of the connection
1.1 Establishing a connection
Between the two chains, we must first establish “ Connect ”, That is, the initial trust relationship ; At the moment when the connection is established, the two chains need to exchange basic trust data ( Trust root )-- Yes PoS A network is a set of verifiers' public keys in two chains , The trust root must be verifiable by a third party .
1.2 Keep connected
During the whole connection period, it is necessary to continuously obtain the new block of the other party , Based on trust root and continuous block header , The block height of the other party when the connection is established , Continuously verify the correctness of subsequent block heads at any height ; These block headers are validation IBC The basis of trust for packets .
1.3 disconnect
When a bifurcation or security event occurs , Close the connection in time ; This can be triggered by chain governance or automatic cheating detection .
2. Data packets 、 Receipt and timeout processing
2.1 Data packets
Is made up of metadata ( Data header ) And opaque data payload ( Data body ) Composed of messages . The data header contains the type 、 Sequence number 、 Source chain ID、 Target chain ID、 Timeout parameters ; The data body contains data that needs to be understood and processed by the blockchain application layer , That is, the proof of the source chain state change .
2.2 receipt
yes “ reverse ” Data packets ,B The chain receives and processes data from A After the packet of the chain , Will give A Send a corresponding receipt .
2.3 timeout handler
The source chain sends packets , You can specify a timeout parameter represented by the block height or timestamp on the target chain in the data header ; The target chain will not process the received timeout packets , If the source chain does not receive a receipt after the packet sent times out , It will roll back the state on the chain corresponding to the packet .
3. Strictly ordered messaging
To make the whole system work , The delivery of packets must maintain strict global ordering :
· The consensus algorithm ensures that the processing of transactions on the chain follows a single precise sorting .
· IBC The protocol ensures that messages about the processing status of on chain transactions follow a single precise ordering in the process of cross chain transmission .
· IBC Using the channel mechanism to achieve sorting control : Each chain maintains both send and receive channels for each connection , Each channel maintains a counter , The counter of the sending channel generates the sequence number for the outgoing message , The counter of the receiving channel is used to verify the sequence number of the incoming message .
· Strict sequencing guarantee is a prerequisite for deriving global state consistency .
4. Consensus requires
IBC Protocol security requires the finality of consensus algorithm to prevent double blossom , The final performance of different consensus algorithms is different :
· Tendermint and PBFT Class consensus algorithm satisfies the real-time finality ( optimal )
· Ethereal Casper FFG Consensus algorithms provide fast finality
· Bitcoin consensus algorithm (PoW, Tezos) Provide probability finality , The application layer needs to select a security threshold
3、 ... and .Cosmos IBC relayer
relayer The software package contains a basic repeater implementation , You want to enable IBC Relay packets between chain groups / User use of data
The repeater supports the following functions :
- establish / to update IBC Tendermint light Customer
- establish IBC Connect
- establish IBC Transfer channels .
- Start cross chain transfer
- Relay cross chain transfer transactions , Its acknowledgement and timeout
- Relay from status
- Relay from stream events
- send out IBC Interrupt the upgrade UpgradePlan Suggest
- In the trade on the bracelet on IBC Upgrade customer after major change upgrade
The repeater is currently unable to :
- Use user selected parameters ( for example UpgradePath) Create client
- Submit IBC Customer unfreezing suggestions
- Monitor and submit misconduct to customers
- Use to divide Tendermint In addition to the IBC light client , for example Solo Machine
- Connect to not implemented / not enabled IBC Chain
- Use different IBC Implement connection to chain ( Chain not used SDK Of
x/ibcmodular )
Four .IBC Cross chain transfer process
IBC It belongs to Cosmos-SDK A special module in . It's special , Mainly reflected in IBC It provides cross chain capabilities between blockchains
If A On the chain Alice Need to send 10 individual ATOM Token to B On the chain Bob On , It will go through the following four steps
- Tracking
A On the chain IBC The modules will be synchronized continuously B Block header information on the chain ,B On the chain IBC Empathy . In this way , Both parties can track the changes of the verifier set on each other's blockchain , In essence , Namely A chain 、B Chains maintain each other's light nodes
- Bonding
When using IBC After initializing a cross chain transfer ,A On the chain 10 individual ATOM In fact, it is locked 
- Proof relay
A certificate A The chain is locked 10ATOM Of “ evidence ” Will be routed to B On the chain IBC modular 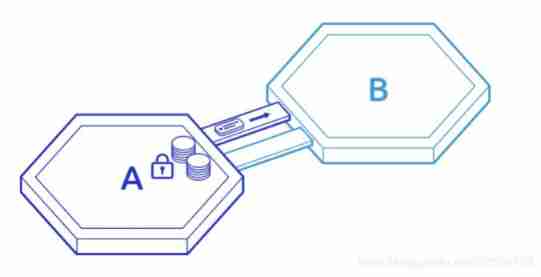
- Verify
B Chain combination A Light node information of the chain , Yes, this one “ evidence ” After passing the verification ,B Chain meeting “ Casting ”10 Share ATOM Voucher( Coupons ), these Voucher It can be used for subsequent circulation . Of course these Voucher You can also return to by the same cross chain method A chain ,A On the chain ATOM The token performs the unlocking operation accordingly
5、 ... and .IBC handshake protocol
IBC Agreement is Cosmos The core interface protocol in , It can realize the trust of cross chain messages between blockchains 、 Reliable forwarding , And effectively control the flow 、 Multiplexing and other functions .
stay Cosmos in , Each function is highly modular , Each function is realized by loading different modules ,IBC So it is with . stay IBC When the design , Reference to the transport layer TCP agreement , It also hopes to become a blockchain “TCP agreement ”. More Than This , stay IBC Can also be seen in all aspects of TCP The figure of , First let's look at IBC Some basic concepts in .Cosmos IBC A connected 、 Reliable cross chain message transmission
IBC The protocol and TCP Comparison of related concepts 
cosmos A complete explanation in the community IBC Handshake and communication flow of the protocol , As shown in the figure below :
The connection process of a cross chain transaction is shown in the figure above , and TCP The agreement is similar to ,IBC The establishment of requires the establishment of multiple handshake processes , A step of initializing the client is added , This is a key link for cross chain
Establish handshake connection on the basis of light client , Handshake connection is basically divided into three parts .
- Start cross chain user to chain A launch OpenInit request , wait for Relayer Received the request .
- Relayer Work on routing cross chain message packets , If you receive OpenInit Request ,Relayer Will construct a OpenTry The request is sent to the chain B On .
- chain B received OpenTry After the request , If you agree , The message will be acknowledged ( Generate OpenACK Data packets , And as before by Relayer Forward to chain A.
- chain A adopt OpenACK The packet determines whether the handshake is successful , If it works , Send the last... For this handshake OpenConfirm Packet return chain B. If the handshake fails , The connection failed
Although in Cosmos It is mentioned in the design that disordered Channel, But the default implementation uses an ordered pattern . If according to TCP By analogy with the protocol cluster , Orderly Channel and TCP similar , disorder Channel Be similar to UDP, disorder Channel according to UDP In a word , It is also applicable in some scenarios that do not pay much attention to the sequence of message packets across the chain . meanwhile Cosmos The design also takes into account Channel Ability to send messages , Allow one Connection Build more than one Channel, In different cross chain application scenarios , You can use different Channel Send a message , So as to isolate different businesses .
After the above series of handshakes , The application layer can be used in Channel Send your own data on .Cosmos It specifies some necessary fields for sending cross chain transactions , Here's the picture :
among Sequence and SourcePort Fields are functions that assume their literal meaning , It is also a field that must be specified , and TimeoutHeight and TimeoutTimestamp yes Cosmos Provides a timeout mechanism . If the cross chain transaction has not been completed at a certain block height or at a certain time , The user can specify that the transaction be rolled back ( For example, cross chain transfer , It can prevent funds from freezing for a long time ). and Data Fields are reserved for users to customize , To cope with possible complex cross chain scenarios
IBC The method of establishing connection is adopted for cross chain , differ Polkadot Of XCMP agreement ,XCMP The parallel chain in the protocol can directly forward cross chain messages
边栏推荐
- Install cuda+cusp environment and create the first helloword starter project
- [deep learning]: introduction to pytorch to project practice (XII) convolutional neural network: padding and stride
- A small soft raster engine with clear thinking and a case of quaternion combination
- 免费文件服务器储存技术
- Detailed explanation of digital certificate and Ca
- 25 | adventure and prediction (IV): it's raining today. Will it rain tomorrow?
- 20 | 面向流水线的指令设计(上):一心多用的现代CPU
- 直播回顾 | 积极防御体系下BAS技术创新探索
- Redis Cluster - the underlying principle of cluster execution commands
- [MySQL] rapid data deletion recovery tool - binlog2sql
猜你喜欢

本地靶场2-文件上传漏洞(三)-网络安全
![[pytorch] pytorch0.4.0 installation tutorial and GPU configuration collection (including test code)](/img/b4/138b7ae8c73e38663ea84ece79273b.jpg)
[pytorch] pytorch0.4.0 installation tutorial and GPU configuration collection (including test code)
![[redis problem] record a big key problem handling](/img/ad/787d5911fac2cc2105e439d906b67f.jpg)
[redis problem] record a big key problem handling
![[problem record] json decoder. JSONDecodeError:Extra data: line xxx column xxx(char xxxx)](/img/29/ec3e5a1566b4c3ecb0eef1ceede98d.jpg)
[problem record] json decoder. JSONDecodeError:Extra data: line xxx column xxx(char xxxx)

STM32CubeMX的下载和安装方式
2022年电工(初级)考题及模拟考试

汽配行业面临的难题用什么软件帮忙解决呢

分布式系统之道:Lamport 逻辑时钟

【clickhouse专栏】基础数据类型说明

17 | 建立数据通路(上):指令+运算=CPU
随机推荐
Simple use of logs
Remote office solution under epidemic situation
Redis' underlying data structure -- SDS
C盘爆满?简单几招教你释放、清理C盘几十G空间,最有效的C盘清理方法
v-for生成的子组件列表删除第n行出现数据错乱问题
[problem record] json decoder. JSONDecodeError:Extra data: line xxx column xxx(char xxxx)
Unity exit Editor Mode
Redis learning journey master-slave replication
Redis learning journey -- subscription and publishing
Index push down (ICP) for mysql5.6
25 | adventure and prediction (IV): it's raining today. Will it rain tomorrow?
Redis Cluster - the underlying principle of slot assignment
[pytorch] pytorch0.4.0 installation tutorial and GPU configuration collection (including test code)
Free file server storage technology
uniapp 小程序根据权限动态生成 tabbar
MySQL table cache most detailed notes
【clickhouse专栏】基础数据类型说明
JMeter UDP pressure measurement
21 | pipeline oriented instruction design (Part 2): How did Pentium 4 fail?
A small soft raster engine with clear thinking and a case of quaternion combination