当前位置:网站首页>447 Bili Bili noodles warp 1
447 Bili Bili noodles warp 1
2022-07-01 22:45:00 【liufeng2023】
1、 Yes const and volatile The understanding of the
const:
- const Indicates that the decorated variable cannot be modified , If modified , The compiler will report an error .
- If you have a const Modify the modified variable after taking the address or reference , Then there will be undefined behavior , The compiler is not guaranteed to get the desired results .
volatile:
- volatile Be sure to pay attention to , It has nothing to do with multithreading ;
- Its function is to Memory visibility , Prevent the compiler from volatile Modify the variables to do some related optimization ;
Do not add variables volatile, The compiler will optimize variables :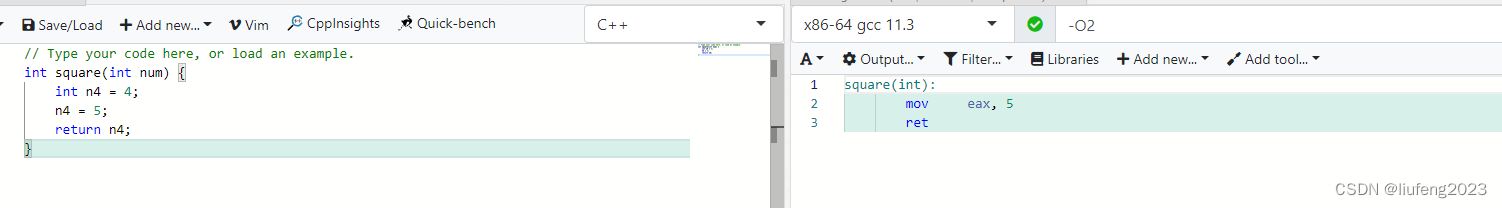
And added volatile modification , The generated assembly is like this :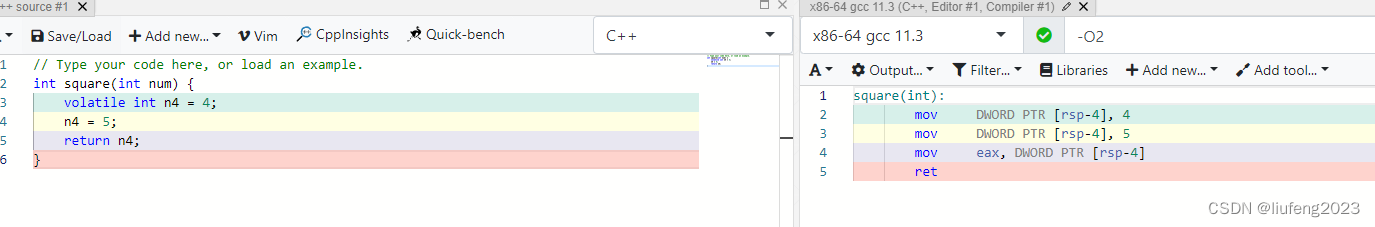
C++ Of volatile Generally, it is only used to communicate with hardware , We can hardly program with .
For details, see :https://en.cppreference.com/w/cpp/language/cv
2、Linux The process of generating executable programs
Four processes !
1、 Preprocessing ; Mainly did the following work :
- Expand all #define Macro definition , Replace text ;
- Delete all comments in the program ;
- Handle all conditional compilation ,#if、#ifdef、#elif etc. ;
- Deal with all #include Instructions , Copy the contents of these header files to the referenced source file ;
- Add line number and filename ID , It is convenient for the compiler to generate warnings and debugging information ;
- Keep all #pragma Compiler Directives , Because the compiler will use them ;
2、 compile ; Perform a series of operations on the preprocessed file to generate the corresponding assembly file
- Lexical analysis : Also known as lexical scanning , Through the scanner , Using the algorithm of finite state machine, the string in the source code is divided into a series of marks , Such as addition, subtraction, multiplication, division, number brackets, etc .
- Syntax analysis : Use the parser to analyze the marks generated by lexical analysis by means of context free grammar , Generate parsing tree . During this period, if the expression is illegal ( Brackets don't match, etc ), You're going to report a mistake .
- Semantic analysis : Syntax analysis checks whether the expression is legal , Check whether the expression makes sense , For example, a floating-point integer is assigned to a pointer , The compiler will report an error .
- Interlanguage generation : Do some syntax tree optimization , Such as 6+2=8.
- Object code generation and optimization : Generate object assembly code from intermediate code .
3、 assembly ;
- Use The assembler converts the assembly code into instructions that the machine can execute , In fact, it is to translate the assembly instructions and machine instructions one by one according to the comparison table .
4、 link ;
- The basic units processed above are source files , After the above processing, multiple source files become multiple target files ;
- link Namely The process of packaging and assembling multiple object files into a whole , This The whole is an executable program .
Friends who want to know more deeply , Advice to see 《 Self cultivation of programmers 》, You can also see my summary :https://mp.weixin.qq.com/s/PaXLQnaCjGkQGIjnPnqRww
3、Linux How does the program work
This involves many knowledge points :
- What is a process , How the process is established ?
- What is virtual memory ? Why have virtual memory ?
- How the program works ?
1、 adopt fork System call creates a new process ;
2、 adopt execve The system call executes the specified ELF file , With environment variables and parameters ;
3、 Check ELF Validity of executable , Like magic number ( The file format can be determined by magic number )、Segment The quantity of ;
4、 Looking for dynamically linked segments , Set dynamic linker path ;
5、 according to ELF Program header table description of executable file , Yes ELF File mapping , For example code 、 data 、 Read only data ;
6、 initialization ELF Process environment ;
7、 Change the return address of the system call to ELF The entry address of the executable
4、 The process of missing pages in memory
It involves many pre knowledge points :
- Virtual memory management
- Mapping of virtual memory to physical memory
- The concept of page table and page
Memory page missing The page to be accessed is not in main memory , The operating system needs to load the page into main memory and then access it , The execution of the command will be temporarily stopped , Generate an exception that the page does not exist .
The process of page break processing is as follows :
1、 If there are free physical pages in memory , Assign a physical page frame r, And then turn to 4 Step , Or turn to 2 Step ;
2、 Choose a page replacement algorithm , Select a physical page frame to be replaced r, Its corresponding logical page is q, If the page has been modified during memory , Write it back to external storage ;
3、 take q The corresponding page table entry is modified , Put the dwell position 0;
4、 Will need to visit the page p Load to physical page r in ;
5、 modify p The content of the corresponding page table entry , Put the dwell position 1, Set the physical page frame number to x;
6、 Rerun the interrupted instruction .
5、 The concepts of left and right values
What can take the address is the lvalue , What can't get the address is the right value .
6、 Mobile semantics
The official definition of :
- Mobile semantics mainly provides the ability to move expensive objects from one address to another in memory , At the same time, steal the source resources in order to build the target with the least cost .
Main uses :
- Be able to use mobile constructor and mobile assignment operator , When we use temporary objects , Reduce unnecessary copy operations .
7、 Advantages and disadvantages of template use ?
advantage :
- More flexible , reusable ;
- Automatically generate code at compile time , Greatly reduce development time ;
shortcoming :
- It's difficult to debug ;
- Generally, the implementation of functions in the template will be placed in the header file , The implementation details will be exposed ;
- Extensive use of templates , It will take a long time to compile .
8、 Program output
for (char i = 0; i < 256; ++i)
{
printf("%d\n", i);
}
Output is :
0 1 2 … 127 -128 -127 … -1 0 1… Infinite loop !
127 The binary of is 0111 1111( Complement code )
-128 The binary of is 1000 0000( Complement code )
reason :
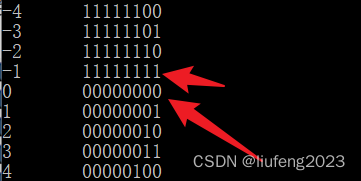

As can be seen from the results above ,ch stay 127 after , The values are determined by 127 Turned into -128, Continue to perform when ch by -1 Back to the original 0 value . Just like the closed loop drawn above , 0->127,-128->0->127…
Let's analyze it from the perspective of binary :
In the computer , Signed numbers are represented by complements .
about char Type of 1 byte 8 Digit number , The first bit is the sign bit , The rest of the bits are numeric .
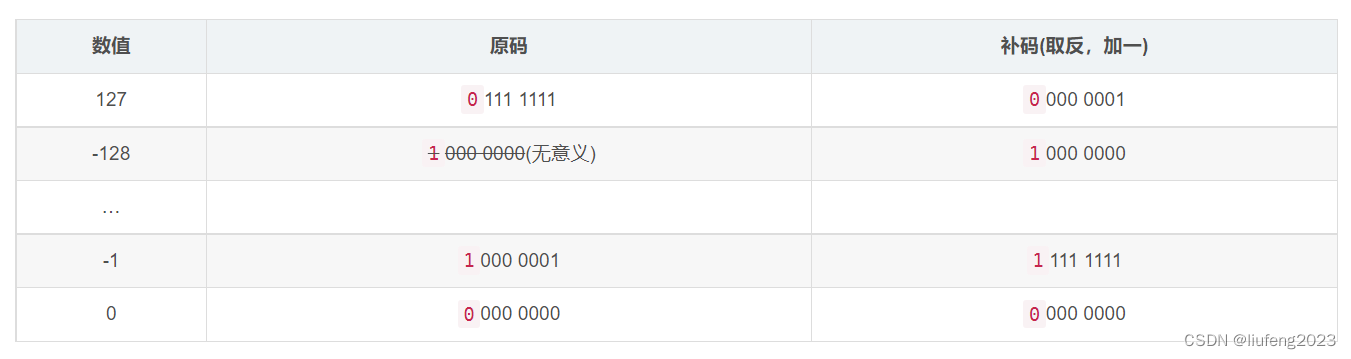
2^7-1 = 127
- 127 The binary of is 0111 1111( Complement code )
- -128 The binary of is 1000 0000( Complement code )
because 127 + 1 Backward position , Make the high bit overflow to the sign bit .
The sign bit marks the positive and negative of the array , Then the value changes from a positive number to a negative number .
and 1000 0000( Complement code ) yes -128 Complement , Then he means signed number -128 .
The relationship between the source code and complement of negative numbers is : Original code -> Take the opposite +1 => Complement code .
For positive numbers , Do not distinguish the original code / Inverse code / Complement code , Are expressed in their own original code , Only negative numbers are distinguished .
For signed numbers , We take one as the sign bit in the first place , Indicates the positive and negative of the value .
And for 0, We have two representations : namely +0 ⇒ 0000 0000 、 -0 ⇒ 1000 0000 , This is clearly unreasonable .
+0 And -0 Should represent the same number , And we can find :
1000 0000( primary ) As the original code , Its complement is still1000 0000( repair )( High overflow , discarded )- -127
1111 1111( primary ) Minus one ( Plus minus one ) The binary value of is also1000 0000. and-127 - 1The value of is-128.( Negative numbers are complemented ,1111 1111 +1000 0001 =》1000 0000)
Then we can use Complement code 1000 0000 Express -128 . And because we cancel “ negative 0” The concept , A binary bit combination is left to represent other values ( Used to represent -128).
It can be seen from the previous analysis that , Complement code 1000 0000 The original code value of can represent negative 0, However, we don't need “ negative 0”, So for Complement code 1000 0000 We do not study its original code , It only has complement meaning , Express -128 . therefore , stay 127 After adding one, it becomes -128 .
边栏推荐
- 倒置残差的理解
- Chapter 9 Yunji datacanvas company has been ranked top 3 in China's machine learning platform market
- 13th Blue Bridge Cup group B national tournament
- 台积电全球员工薪酬中位数约46万,CEO约899万;苹果上调日本的 iPhone 售价 ;Vim 9.0 发布|极客头条
- CSDN购买的课程从哪里可以进入
- LC501. Mode in binary search tree
- # CutefishOS系统~
- Redis配置与优化
- 聊一聊Zabbix都监控哪些参数
- 旅游管理系统
猜你喜欢

Pytorch sharpening chapter | argmax and argmin functions

详解ThreadLocal

多图预警~ 华为 ECS 与 阿里云 ECS 对比实战

The fixed assets management subsystem reports are divided into what categories and which accounts are included

The second anniversary of the three winged bird: the wings are getting richer and the take-off is just around the corner

Appium自动化测试基础 — 补充:Desired Capabilities参数介绍
性能测试计划怎么编写

What is the difference between PMP and NPDP?

搜狗微信APP逆向(二)so层
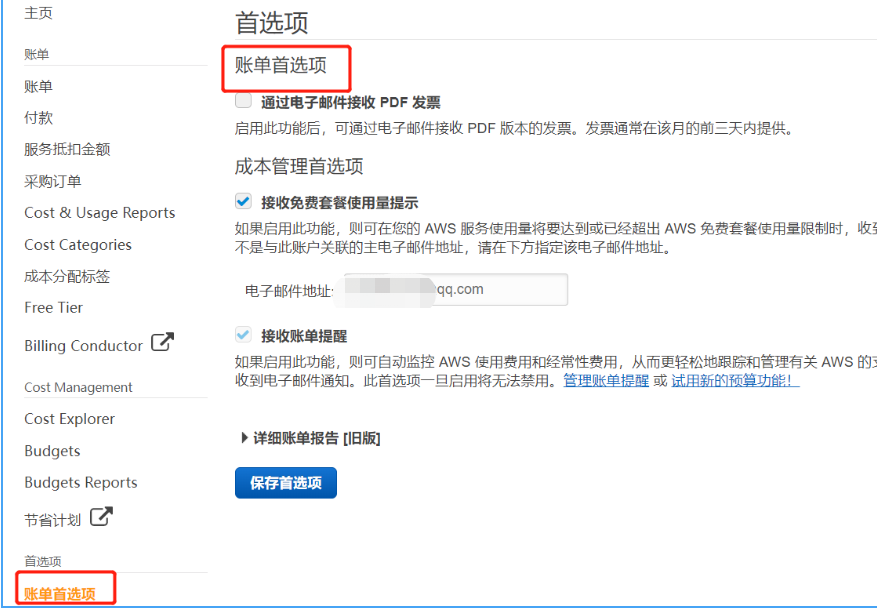
删除AWS绑定的信用卡账户
随机推荐
【扫盲】机器学习图像处理中的深层/浅层、局部/全局特征
Pytorch's code for visualizing feature maps after training its own network
Mask wearing detection method based on yolov5
Mysql——》Innodb存储引擎的索引
QStringList 的常规使用
Is PMP certificate really useful?
内部字段分隔符
GenICam GenTL 标准 ver1.5(4)第五章 采集引擎
Relationship and difference between enterprise architecture and project management
Resttemplate remote call tool class
Recent public ancestor offline practice (tarjan)
三翼鸟两周年:羽翼渐丰,腾飞指日可待
Delete AWS bound credit card account
【图像分割】2021-SegFormer NeurIPS
Flume interview questions
Recent public ancestor (LCA) online practices
好友新书发布,祝贺(送福利)
Learning notes on futuretask source code of concurrent programming series
倒置残差的理解
13th Blue Bridge Cup group B national tournament