当前位置:网站首页>Bloom filter
Bloom filter
2022-07-03 00:17:00 【JunesFour】
The bloon filter
List of articles
1. Use scenarios
- Making ⽤word⽂ Stall time ,word How to tell if a word is spelled correctly .
- ⽹ Collateral climbing ⾍ Program , How to keep it from climbing the same url⻚⾯? Error allowed .
- spam ( SMS ) How to design the filtering algorithm ? Error allowed .
- When the police handle a case , How to judge a suspect ⼈ Whether in ⽹ On the escape list ? Control error False positive rate .
- How to solve the cache penetration problem ? Error allowed .
2. The basic idea
You can go through more than one Hash Function maps an element to several points in a bitmap , Mark these points as true, At query time , By querying whether these points are true, You can judge whether this element exists in the bloom filter . So bloom filter phase ⽐ Traditional query structure ( for example :hash,set,map And so on ) more ⾼ effect , Occupy ⽤ More space
⼩.
Be careful :
- The bloon filter cannot delete elements , Because it does not store specific elements , Only a few points mapped to the element are stored , And each point may be covered by the results of multiple element mapping .
- Bloom filter can only judge that an element does not exist or may exist , When using hash All points mapped by the function are true when , This element may exist , As long as one doesn't true, It must not exist .
3. Implementation of the bloom filter
form
Bitmap (bit Array )+ n individual hash function .
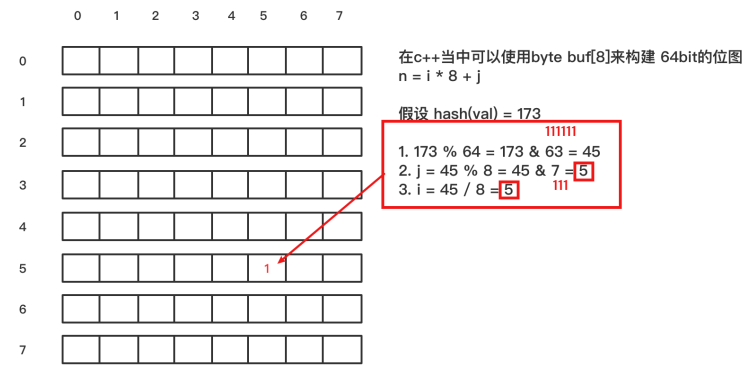
principle
When ⼀ Elements plus ⼊ Bitmap time , adopt k individual hash Function maps this element to the of the bitmap k A little bit , And set them as 1; When retrieving , Re pass k individual hash Function operation to detect the of bitmap k Whether all points are 1; If there is any reason not to 1 The point of , So I don't think it exists ; If it's all 1, There may be ( There is an error ).
There are only two states for each slot in the bitmap (0 perhaps 1),⼀ Slots are set to 1 state , But it is not clear how many times it has been set ; I don't know how many str1 Hash mapping and which hash Function mapping ; So don't ⽀ Hold the delete operation .
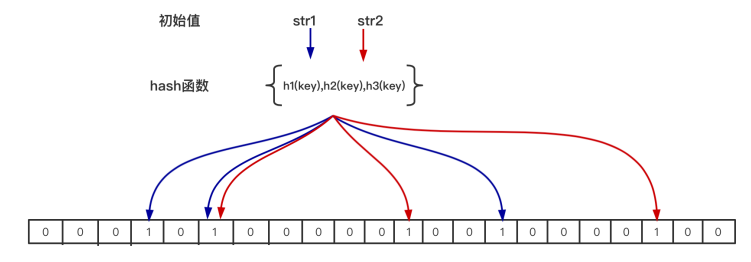
4. The design of Bloom filter
In practice, we should ⽤ In the process , How the bloom filter makes ⽤? How many hash function , Bitmap of how much space to allocate , save
How many elements are stored ? In addition, how to control the false positive rate ( The bloan filter can define ⼀ Must not exist , Not clear ⼀ There must be , Then there is
Your judgment is wrong , False positive rate is the probability of wrong judgment )?
We usually use the following four parameters to solve the above problem :
- n – The number of elements in the bloom filter , Pictured above Only str1 and str2 Two elements that n=2.
- p – False positive rate , stay 0-1 Between 0.000000.
- m – Space occupied by bitmap .
- k – hash Number of functions .
The formula is as follows :
n = ceil(m / (-k / log(1 - exp(log(p) / k))))
p = pow(1 - exp(-k / (m / n)), k)
m = ceil((n * log(p)) / log(1 / pow(2, log(2))))
k = round((m / n) * log(2))
The following two parameters m and k From the above two parameters n and p To calculate the , You can calculate by yourself , You can also enter the first two values on the relevant website and calculate the last two values :

k individual hash function
Among the above calculation results ,k=23 , In practice, , We won't really choose 23 individual hash function , It's a double hash To simulate 23 individual hash function :
// Mining ⽤⼀ individual hash function , to hash Pass on different species ⼦ Offset value
// #define MIX_UINT64(v) ((uint32_t)((v>>32)^(v)))
uint64_t hash1 = MurmurHash2_x64(key, len, Seed);
uint64_t hash2 = MurmurHash2_x64(key, len, MIX_UINT64(hash1));
for (i = 0; i < k; i++) // k yes hash Number of functions
{
Pos[i] = (hash1 + i*hash2) % m; // m It's a bitmap ⼤⼩
}
边栏推荐
- Mapper agent development
- Interpretation of new plug-ins | how to enhance authentication capability with forward auth
- TypeError: Cannot read properties of undefined (reading ***)
- yolov5test. Py comment
- Optimization of streaming media technology
- 经济学外文文献在哪查?
- Create an interactive experience of popular games, and learn about the real-time voice of paileyun unity
- Where can I check the foreign literature of economics?
- Is the multitasking loss in pytoch added up or backward separately?
- MATLAB signal processing [Q & a notes-1]
猜你喜欢

Which software can translate an English paper in its entirety?
CADD course learning (4) -- obtaining proteins without crystal structure (Swiss model)
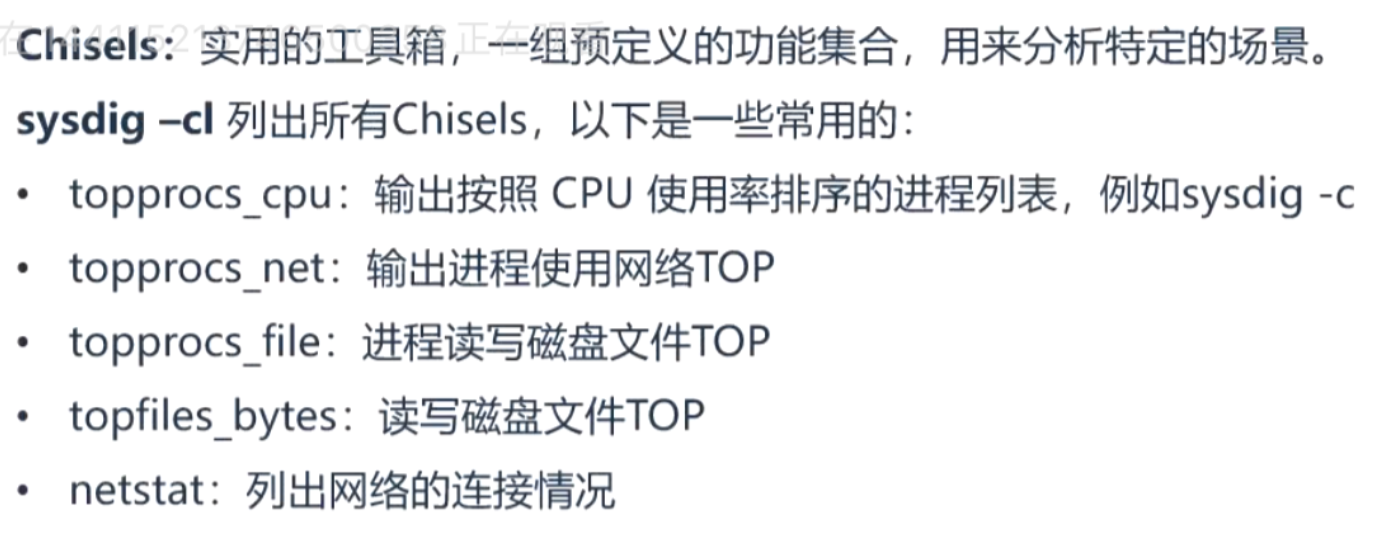
Sysdig analysis container system call

PR FAQ, what about PR preview video card?
What is the official website address of e-mail? Explanation of the login entry of the official website address of enterprise e-mail

JS interviewer wants to know how much you understand call, apply, bind no regrets series

基于OpenCV实现口罩识别
Matlab 信号处理【问答笔记-1】
Improvement of RTP receiving and sending PS stream tool (II)

CADD课程学习(4)-- 获取没有晶体结构的蛋白(SWISS-Model)
随机推荐
Talk with the interviewer about the pit of MySQL sorting (including: duplicate data problem in order by limit page)
Open source | Wenxin big model Ernie tiny lightweight technology, which is accurate and fast, and the effect is fully open
Matlab 信号处理【问答笔记-1】
[reading notes] phased summary of writing reading notes
67 page overall planning and construction plan for a new smart city (download attached)
List of major chip Enterprises
35 pages dangerous chemicals safety management platform solution 2022 Edition
流媒体技术优化
What website can you find English literature on?
RTP 接发ps流工具改进(二)
Additional: token; (don't read until you finish writing...)
Define MySQL function to realize multi module call
Interface automation coverage statistics - used by Jacobo
MySQL advanced learning notes (4)
1380. Lucky numbers in the matrix
QT 如何将数据导出成PDF文件(QPdfWriter 使用指南)
Digital collection trading website domestic digital collection trading platform
Interface difference test - diffy tool
MFC gets the current time
MySQL advanced learning notes (III)