当前位置:网站首页>How to encrypt the device
How to encrypt the device
2022-06-29 01:31:00 【CNSINDA_ HK】
Many enterprise servers , In particular, the business system server is relatively fragile , Even with anti-virus software 、 Deployed firewalls 、 And patch regularly , Still
However, there will be various risks of intrusion and tampering , Even blackmail virus .
introduction
With Germany's “ Industry 4.0”、 In the United States “ Reindustrialization ” Trend 、“ Made in China 2025” And so on , And cloud computing 、 big data 、 Artificial intelligence 、 The accelerated integration of new generation information technology and manufacturing technology such as the Internet of things , Industrial control system has changed from original closed and independent to open 、 From single machine to interconnection 、 From automation to intelligence . While the industrial enterprises have gained great momentum of development , There are also a lot of potential safety hazards , The industrial control system as a key national infrastructure “ The central nervous system ”, Its security concerns the strategic security of the country 、 Social stability, .
One 、 Overview of industrial control safety
Want to know about industrial control safety , First, understand the asset object itself , That is, industrial control system .
1、 What is industrial control
About the definition of industrial control system , There are many on the Internet , I won't go back to , The following picture is from csdn Found , I think it's pretty good . Refer to the definition of industrial control , Can help you have a better understanding .
2、 The impact of industrial control safety
There are many cases about industrial control safety , Recent examples are 2019 year 3 month , Most parts of Venezuela are without power , The national transportation system is paralyzed , The subway system is shut down , Mass disruption of communication .2019 year 7 month , The Iranian information Corps broke into the United States 30 Control centers for multiple substations , It led to a massive blackout in New York 4 Hours , Cause large-scale chaos, etc . One of the most famous 、 The most influential is 2010 year 6 month , The Iranian nuclear power plant suffered “ Seismic net ” Virus attack . There was once a film in China “ Seismic net ” A movie based on events , named 《 Hackers fight 》, Those who are interested can go and have a look , You can have a more intuitive understanding of industrial control safety .
The pain point of the industrial computer is that it is not connected to the Internet , The operating system cannot be patched , Virus library cannot be updated , Ordinary anti-virus software is useless ; Because it is a special equipment , The user's NMS dare not install anti-virus software on it ; Is there a virus in the system , The production line is interrupted , Great loss .
Personal suggestion is to use the way of host reinforcement to strengthen the industrial computer , To resist the virus
The core points of host reinforcement :
1、 System reinforcement
Lock the debugged system , Become a trusted system .
In a trusted system , Illegal procedure 、 Scripts can't run . And it will not affect data access .
Even if the system has vulnerabilities , Even administrator privileges are lost , This trusted system is secure .
2、 Program reinforcement
The executable program is signed by trusted signature 、 Start the script in real time hash Value verification , If the verification fails, the startup is rejected , And trusted programs cannot be disguised .
3、 Document reinforcement
Protect files of the specified type from tampering .
4、 Disk encryption
Create a safe sandbox , The sandbox is isolated from the outside , Encrypt the data in the sandbox , Ensure that the data can only be used under the premise of effective authorization management , To be decrypted . If there is no authorization , Even administrators cannot copy and use this data , Even system cloning does not work .
5、 Database hardening ( Structured data )
first floor : Database files are forbidden to be accessed and tampered with by unfamiliar programs . Ensure database file level security .
The second floor : Database port access trusted filtering , Only business programs are allowed to connect to the database port , At the end of the connection string IP+ port + In the account password , Append process identification .
The third level : Database connection SQL Intelligent filtering of text , Prevent critical data from being retrieved and accessed , Prevent the data in the database from being accessed illegally , Prevent dangerous operations of database forms .
The core points of host reinforcement :
1、 System reinforcement
Lock the debugged system , Become a trusted system .
In a trusted system , Illegal procedure 、 Scripts can't run . And it will not affect data access .
Even if the system has vulnerabilities , Even administrator privileges are lost , This trusted system is secure .
2、 Program reinforcement
The executable program is signed by trusted signature 、 Start the script in real time hash Value verification , If the verification fails, the startup is rejected , And trusted programs cannot be disguised .
3、 Document reinforcement
Protect files of the specified type from tampering .
4、 Disk encryption
Create a safe sandbox , The sandbox is isolated from the outside , Encrypt the data in the sandbox , Ensure that the data can only be used under the premise of effective authorization management , To be decrypted . If there is no authorization , Even administrators cannot copy and use this data , Even system cloning does not work .
5、 Database hardening ( Structured data )
first floor : Database files are forbidden to be accessed and tampered with by unfamiliar programs . Ensure database file level security .
The second floor : Database port access trusted filtering , Only business programs are allowed to connect to the database port , At the end of the connection string IP+ port + In the account password , Append process identification .
The third level : Database connection SQL Intelligent filtering of text , Prevent critical data from being retrieved and accessed , Prevent the data in the database from being accessed illegally , Prevent dangerous operations of database forms .
Which host reinforcement brands are worth recommending :
At present, several brands that have done well in the field of host reinforcement are known in the market :
1、 Xinda's MCK Host reinforcement and CBS Sebo lock .
2、 Wisteria cloud security .
3、 Luoan Technology .
4、 wave .
5、 Anheng .
6、 Convinced .
7、 Tian Rong Xin .
In no particular order . Personal recommendations MCK Mainframe reinforcement +CBS Plan , Because what our company buys is MCK Mainframe reinforcement +CBS. It is said that their sandbox encryption is also an old brand in the industry , You can rely on .
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , The purpose of anti-virus encryption is to blackmail smart devices , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , The purpose of anti-virus encryption is to blackmail smart devices , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , The purpose of anti-virus encryption is to blackmail smart devices , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , The purpose of anti-virus encryption is to blackmail smart devices , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , The purpose of anti-virus encryption is to blackmail smart devices , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , The purpose of anti-virus encryption is to blackmail smart devices , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
边栏推荐
- Misunderstanding of innovation by enterprise and it leaders
- In MySQL database, the two data written when creating tables with foreign keys are the same. Do I copy them or fail to display them
- 第七天 脚本与特效
- What is the reason why easycvr can't watch the device video when it is connected to the home protocol?
- Typescript (6) function
- How to select database
- Statistical learning method (3/22) k-nearest neighbor method
- Learning notes of Lichuang EDA: Copper laying dead zone? isolated island? Dead copper?
- AHA C language, C language programming introductory books and PPT (PDF version) download website
- [eight part essay] MySQL
猜你喜欢

Day 8 script and audio

测试只能干到35岁?35岁+的测试就会失业?

What is the difference between immunohistochemistry and immunohistochemistry?

月薪过万的测试员,是一种什么样的生活状态?
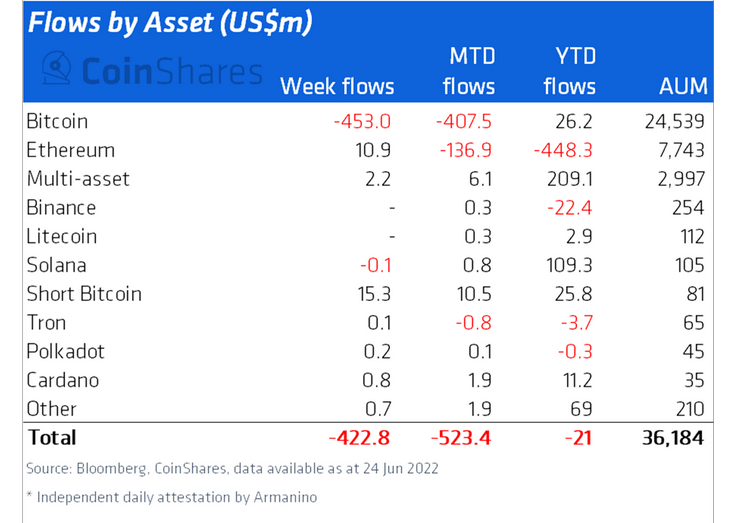
Last week, institutional encryption asset products outflow US $423million, a record high
![[image processing] image curve adjustment system based on MATLAB](/img/9c/176473a0083f075e54a45fbb4ed6ea.png)
[image processing] image curve adjustment system based on MATLAB

Magic Quadrant of motianlun's 2021 China Database

The metadata request parsing principle of OData XML format applied by SAP ui5 is based on domparser

Bmfont make bitmap font and use it in cocoscreator
Kuboardv3与监控套件安装
随机推荐
To the interface problems we have encountered
How to use PN junction to measure temperature?
What is the difference between the history and Western blotting
Brief description of 802.1x Protocol
Misunderstanding of innovation by enterprise and it leaders
【温度检测】基于matlab GUI热红外图像温度检测系统【含Matlab源码 1920期】
Pytorch -- use and modification of existing network model
[solution] longest common subsequence
Battle drag method 1: moderately optimistic and build self-confidence (2)
手把手教你搞懂测试环境项目部署
栈的增删查改---动态内存
3D, point cloud splicing
Kuboardv3 and monitoring kit installation
How to solve the problem of Caton screen when easycvr plays video?
PAT甲级真题1165
linux7(centos7)设置oracle11开机自启动
2022年启牛商学院证券账户开户安全的嘛?
EdrawMax思维导图,EdrawMax组织结构图
Statistical learning method (2/22) perceptron
Typescript (5) class, inheritance, polymorphism