当前位置:网站首页>Haitai Advanced Technology | application of privacy computing technology in medical data protection
Haitai Advanced Technology | application of privacy computing technology in medical data protection
2022-06-29 11:36:00 【Financial science and Technology Society】
- Medical data security risks
In recent years , The security of medical data is increasingly concerned . Because of the particularity of medical service , Medical data protection faces a large number of threats at any time , The information security and privacy protection of medical data have become increasingly prominent , Medical personal sensitive information disclosure incidents occur from time to time , These sensitive information data leakage events , Violation of personal privacy , It has a bad social impact . Medical data security risks exist in the whole life cycle of medical data , Including medical data generation 、 collection 、 Storage 、 Privacy disclosure during exchange and use .
The current global epidemic is rampant , Seriously threatening people's lives , Medical data plays an important role in epidemic prevention and control , Strengthen the application of password technology for the protection of sensitive medical data , Of great significance .
- Application of privacy computing technology
Privacy computing is a new technology to provide privacy protection , Covering the cross integration of many disciplines , Including secure multi-party computation based on cryptography (MPC)、 Hardware based trusted execution environment (TEE) And artificial intelligence based federated learning (FL). Among them, secure multi-party computing based on cryptography is not a single technology , It includes homomorphic encryption 、 Secret sharing ( Key splitting )、 Inadvertently transmit 、 Confusion circuit and other technologies .
The demand for medical data sharing and utilization is a focus of privacy computing . Medical research 、 Clinical diagnosis 、 Medical services have a strong demand for statistical analysis and application mining based on medical data , However, the privacy of medical data makes sharing and utilization difficult . On the one hand, it is difficult to collect and integrate data across institutions , On the other hand, it is difficult for cross agency data joint application . Privacy computing provides a solution to this problem . Take advantage of privacy computing , On the basis of establishing a standardized database with decentralized storage , It can realize distributed joint statistical analysis , So as to obtain the research results of clinical scientific research . In the process of novel coronavirus pneumonia outbreak , Using secure multiparty Computing , Implement joint analysis and share results , To realize real-time tracking of virus epidemiology and prediction of future virus evolution , Help prevent and control the epidemic .
Here are two examples , Introduce homomorphic encryption and secret sharing ( Key splitting ) Application in medical data protection .
Homomorphic encryption and its application
Homomorphic encryption technology plays an important role in the field of encryption technology . Essentially , Homomorphic encryption refers to such an encryption function , Add and multiply the plaintext and then encrypt it , Add and multiply the ciphertext after encryption , The result is equivalent . Because of this good nature , People can entrust a third party to process the data without divulging information . Regarding this , Homomorphic encryption technology can well solve the problems faced by big data storage in the process of cloud computing platform .
Compared with professional big data companies , Medical institutions usually have relatively weak data processing capacity , Third parties such as cloud computing centers are needed to implement data processing and analysis to achieve more efficient analysis results . But hospitals have the obligation to protect sensitive information and privacy of patients , Data cannot be directly handed over to a third party in clear text . With the support of homomorphic encryption technology , Medical institutions can send encrypted data to third parties ( Cloud platform side ). Patient sensitive information is stored in the cloud through homomorphic encryption , Data encrypted by homomorphism can perform ciphertext based operations in the cloud , Including inquiries 、 retrieval 、 Statistics, etc , The result of the operation is still in ciphertext form , The cloud sends back the operation result data based on ciphertext , The doctor performs the corresponding homomorphic decryption on the operation result to obtain the result corresponding to the plaintext operation . The whole data processing result 、 The data content is completely unknown to the cloud , Thus effectively protecting patients' privacy .
Privacy computing service system developed by Haitai Fangyuan , As the password infrastructure of the cloud platform , It not only has the general commercial password service function , It can also provide homomorphic services for the cloud platform , Provide privacy protection for medical data . Using the privacy computing service system , Realize the statistical analysis of medical data security under the protection of data privacy , It can be applied to epidemiological studies 、 Clinical research 、 Precise epidemic prevention, etc . in fact , Privacy computing service system is an important part of Haitai Fangyuan password service platform , It can also be used in finance 、 Public Security 、 Transportation and TOC( Such as shopping 、 Take-out food 、 Travel, etc ) scene , Provide personal information protection and data security services , Realize the secure use of private data without disclosing the original information .
Secret sharing and its applications
Under the background of network and distributed environment, medical data sharing can be summarized as secure multi-party computing in many cases . The main idea of secure multiparty computing is : In a distributed network , Two or more parties execute an algorithm based on their secret inputs , So that all parties get the correct output at the same time , And protect the confidentiality of their input information . Secret sharing (Secret Sharing) Is an important technology of secure multiparty computing , The principle of secret sharing is to divide the input data of each participant into several pieces , Distribute to all participants to save , And through these partitions, secure multi-party computation . Through the calculation based on the data slice , The input of each participant can be protected . A classic scheme of secret sharing is Shamir Proposed threshold secret sharing scheme , Its characteristic is that the recovery of secret data does not require all data fragments , Only part of the data is required to be partitioned . Secret sharing is often used for key protection , When the secret data is the key in cryptographic operation , Secret sharing is key splitting .
Haitai Fangyuan has a number of technical invention patents in key division , Include SM2 Joint encryption and decryption scheme 、SM9 Cooperative signature schemes and SM9 Cooperative decryption scheme, etc , The mobile intelligent terminal password module product developed by the company based on key division technology can be used to encrypt and protect sensitive data including medical data , And realize collaborative decryption .
- summary
As an important technology to solve the problem of data value circulation and sharing , Privacy computing technology has become a hot spot , But there are also constraints . One is the lack of technical application standards that support the application of privacy computing technology , There are many questions to be clarified , Thus affecting the promotion of technology , Second, privacy computing technology should be applied on a large scale , It also needs to be further improved in terms of performance . It is suggested to gradually establish the application standards of privacy computing technology and product certification system , Strengthen the research on algorithm standard compilation and algorithm optimization , Promote the development of privacy computing technology application specifications
边栏推荐
- [3 questions per day (2)] minimum operand for generating alternate binary strings
- Getting started with the lvgl Library - Animation
- 微博评论架构设计
- Mastering the clever use of some shell wildcards will make us write with half the effort
- LeetCode 535 TinyURL的加密与解密[map] HERODING的LeetCode之路
- Hit the industry directly! The first model selection tool in the industry was launched by the flying propeller
- Micro blog comment architecture design
- 面试高并发,凉了!!(全程高能,建议收藏)
- MySQL 索引失效的几种类型以及解决方式
- Unity学习笔记--Vector3怎么设置默认参数
猜你喜欢

misc3~7
Modbustcp protocol network learning single channel infrared module (medium shell version)

Live broadcast by technical experts from China Kuwait Fangde: how to build a private cloud platform based on openstack and CEPH| Issue 27

在日本的 IT 公司工作是怎样一番体验?
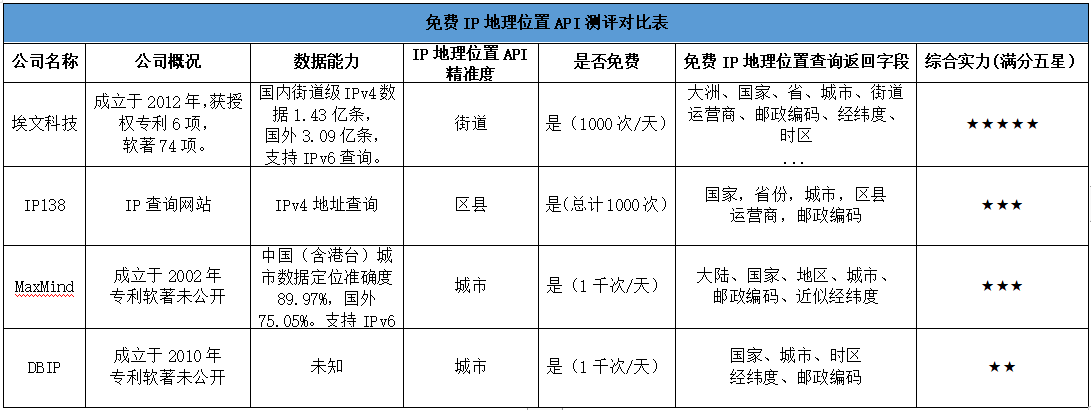
关于IP定位查询接口的测评Ⅱ

Online text filter less than specified length tool

行业分析| 快对讲,楼宇对讲

多线程实现客户端与服务端通信(初级版本)

中国计算语言学大会、全国知识图谱与语义计算大会赛题火热进行中

Modbustcp protocol network learning single channel infrared module (double-layer board)
随机推荐
The necessary operation for those big guys to fly 666 inadvertently at the bash command line terminal
Is it safe to open a stock account online
(JS) status mode
math_ Mathematical expression & deformation of equation equation & accumulation of combined operation skills / means
Modbustcp protocol network learning single channel infrared module (double-layer board)
Graduation season · advanced technology Er - workers in the workplace
在日本的 IT 公司工作是怎样一番体验?
又拍雲 Redis 的改進之路
由ASP.NET Core根据路径下载文件异常引发的探究
(JS) handwritten bind function
Spark - one to one correspondence between task and partition and detailed explanation of parameters
安全 创新 实践|海泰方圆受邀参加“数字时代的网信创新与价值共创”技术交流研讨会
The first "cyborg" in the world died, and he only transformed himself to "change his life against the sky"
(JS) catch errors (exceptions)
Add notification announcements to send notifications to online users
Babbitt | yuancosmos daily must read: HTC announced the launch of the first yuancosmos mobile phone, which costs about 2700 yuan. What are the new ways to play
Uboot for embedded driver development -- common command parameters in uboot
Lizuofan, co-founder of nonconvex: Taking quantification as his lifelong career
在编写shell脚本时如何正确姿势地管理临时文件
misc3~7