当前位置:网站首页>JS reverse case -rus5 logic learning
JS reverse case -rus5 logic learning
2022-06-30 01:59:00 【Eleven elder sister】
Catalog
One 、rs5 characteristic
About 4 The introduction of Dai can be seen in this article , Some processes and 4 Generation is almost the same. This article omits the introduction
Server response status code 202 perhaps 412 Return to the first cookie_S( perhaps cookie_O);
then js Confusion produces a second cookie_T( perhaps cookie_P),Only carry valid cookie_T( perhaps cookie_P) To correctly request the page status code 200How to distinguish between several generations of versions , see cookie_T( perhaps cookie_P) The first number of , The vast majority of generations can be identified by this number ;cookie_T( perhaps cookie_P),
The difference is P representative (https)、T representative (http) It's actually a different agreement, Common are :gOEoYMGvg36yT、neCYtZEjo8GmP、9CKCOkIaqzqET、DLjfPow8PDr4T;
load vm Of 1 More than ten thousand lines of code
Inlet characteristicsYes 3 Kind of , Pictured 4 generation 、 Old edition 5 generation 、 new edition 5 generation , See this article for more detailed version differentiation


Two 、cookie Formal logical analysis
The following process can be understood as a one-step debugging process,cookie You can read this article first , meanwhile vm Before thinking analysis, you can Look at this article1、 First type script Break point and refresh the web page , First, the external chain will be loaded js file ( Let's call it version.js), It may be a little stuck here. Just wait a while , And will js The contents of the file are assigned to global variables
$_tsThis object
2、 Keep following script Breakpoints go , It will jump to a self executing function of the source code js here , Let's call it main.js

3、main.js Execute to
callThe location of , Only two things have been done :$_tsObjects have many properties ,version.jsThe file was decrypted into VM The executable js Code , Get into call Function for decrypted to vm Of js Code , We call it... For shortvm.js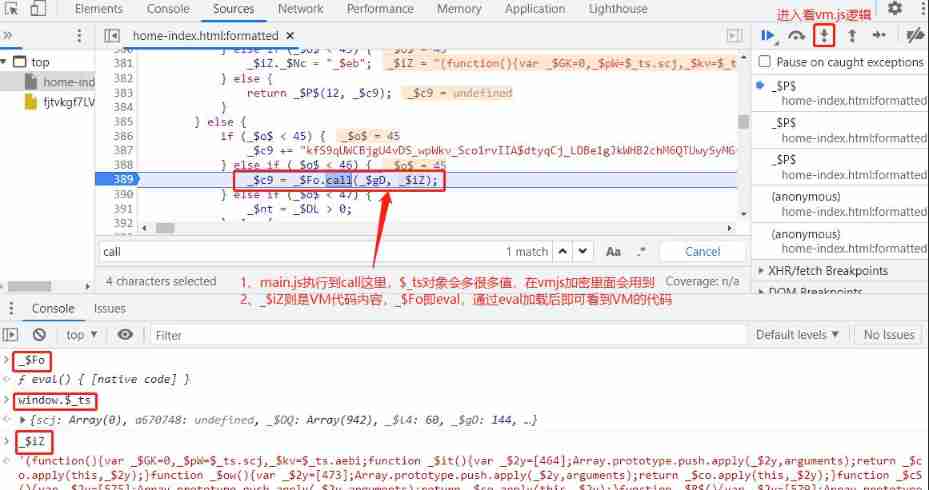

4、 Then passed hook_cookie + Stack backtracking location we know generate cookie The entrance to is vm In code
_$6p(); ===》 _$co(772, 1) ===》 _$co(742, _$TI, false);This position , To 742 The control flow of starts to generate cookie Logic.


5、 So we'll search directly next time
(772, 1)Look for cookie Entry generation logic for (Pay attention to the point: From now on, you need to save a static file for fiddler Replace or overrides Replace to start static analysis , Prevent each refresh of function variable names from being dynamic and difficult to analyze , It's not easy to buckle )
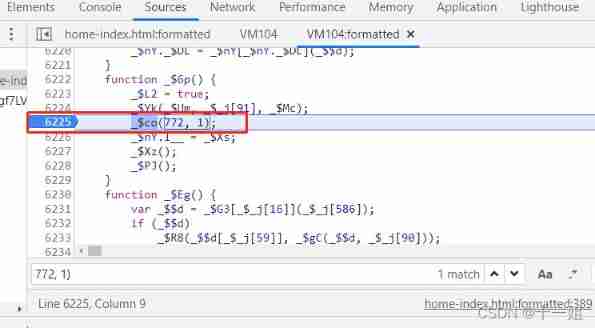

6、742 The first step in the control flow code is to jump here , First, a timestamp difference is generated , In the rear 128 The number of digits in the group will be changed to 8 Digit group push go in
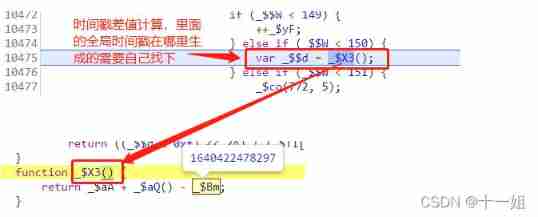
7、742 The second step of the control flow code is to jump here , take
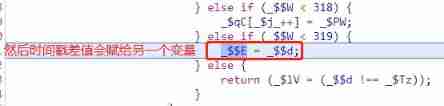
_$$dA variable is assigned to another variable_$$E,( In the middle of the _$Wp Variables are only used to determine which way to change the control flow if ~else Of , Next, many processes will use similar judgments to change the direction of control flow , Ignore here )
8、742 The third step of the control flow code is to jump here , Get into 279 New control flow for ,
The core main logic is 279 In the control stream
9、279 The first step of control flow , First, define a local variable as follows

10、279 The second step of the control flow code is to jump here
_$co(157);, Are some automated tools for feature detection (msCrypto、ActiveXObject、_Selenium_IDE_Recorder,_selenium,callSelenium) etc. , If any , There will be 3 Global variables will be changed , The default does not change , So there is no need to enter the control flow for debugging
11、279 The third step of the control flow code is to jump here
_$Sc(4, _$t2);There will be a global variable that will change , Later on 128 There will be... In the digit group push go in , among _$t2 If this is true It will change 25165824, Default undefined


12、279 The fourth step of the control flow code is to jump here , Generated
_$qC, One 128 Bit empty array
13、279 The fifth step of the control flow code is to jump here ,
It's very important ,695 The control flow of will $_ts Of 5 Values generate 20 Digit group , Among them is 4 The order of values is very important and needs to be mapped

14、695 The first step of the control flow code will
$_tsThe first value of generates 16 Digit group , The second step code will 16 Digit group and 4 Values are connected

15、279 The sixth step of the control flow code is to jump here , The difference of the previous timestamp is converted to 8 Digit group

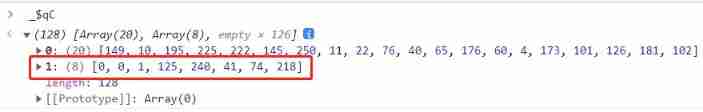
16、279 Control flow seventh 、 8、 ... and 、 Nine 、 The ten step code jumps here ,
_$qC128 Bit empty array has push 了 6 One went in

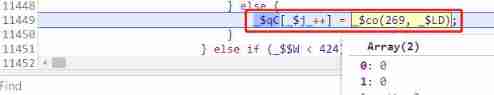


17、279 Control flow step 11 ,push One.
_$34Four bit array of , This 4 The bit group is obtained in the initialization process _$ts An array generated by one of the values


18、279 Control flow 12th 、 Thirteen steps ,push One.
_$CLAn eight bit array of , This 8 The digit group can be written to death for the time being ; then push There's a 0 Also write death first

19、279 Control flow fourteenth 、 15、 ... and 、 Sixteen steps , then push 了 3 Representative is Chrome; then push One. 8 Digit group ( Here's one
_$bJ=25165824, If the previous selenium When detected , This value will change ); then push 了 14 Fixed value

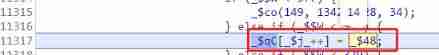

20、279 Control flow step 18 , Indexes
_$1g Preemption,push One. undefined, Then there will be values to override this undefined, at present_$qC128 The digit group has push 了 13 A the


21、279 Control flow step 19 ,
_$co(58)This control flow will return withlocalStorageRelated values , If it's worth it , will push One 20 Digit group , Not this time push


22、279 Control flow step 20 ,
_$co(247, _$_j[580]);This control flow will returnlocalStorage["$_f0"]Value , If it's worth it , will push One 20 Digit group , Not this time push
23、279 Control flow step 21 ,
_$co(247, _$_j[154]);This control flow will returnlocalStorage["$_fh0"]Value , If it's worth it , will push One 20 Digit group , Not this time push
24、279 Control flow step 22 ,
_$co(247, _$_j[636]);This control flow will returnlocalStorage["$_f1"]Value , If it's worth it , will push One 20 Digit group , Not this time push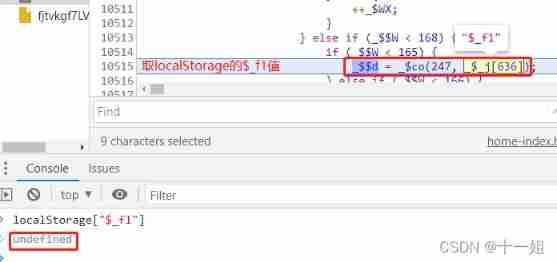
25、279 Control flow step 23 ,
_$JkIs the value corresponding to the network statusNetworkInformation.type, This return is 0, then_$tyOr operation



26、279 There is another wave of judgment in the control flow , return
localStorageCorrelation value , As usual undefined, If it's worth it , will push One 20 Digit group , Not this time push
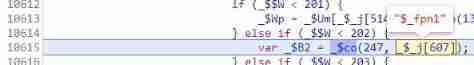

27、279 Control flow step 24 ,push A fixed value 4, It's initializing 777 Control flow generated by , then
_$tyOr operation
 ==》
==》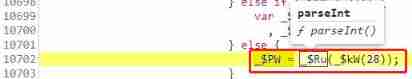


28、279 Control flow step 25 ,
_$tyOr operation , then push One.'https:443'.length, Then return the protocol port at the same time 9 The digit group again push



29、279 Control flow step 25 ,
_$1g PreemptionThe index of , Here will be multiple or operations_$tyTurn it into 4 The digit group is supplemented by , thus 128 Digit group push Finished ,17 Bit length (localStorage It will be longer if it is worth it )


30、279 Control flow step 25 , Keep intercepting 128 Before the digit group 17 Bit has been assigned


31、279 Step 26 of the control flow returns 128 Digit group final 17 Bit all merged and spliced array , thus
279 Control flow pairs 128 The operation of digit group is over , Continue to go 742 Control flow logic
32、742 The control flow then enters 279 Control the entry of the flow , The generated results give
_$ty
33、742 Control flow step 4 code , It generates a 32 Digit group

34、742 Control flow step 5 code ,

35、742 Control flow step 6 code , That by 17 The bit merged array is now connected to another _$ts Value , Calculate a large value , Then the large value is converted to 4 The digit group is connected to 17 Bit merged array
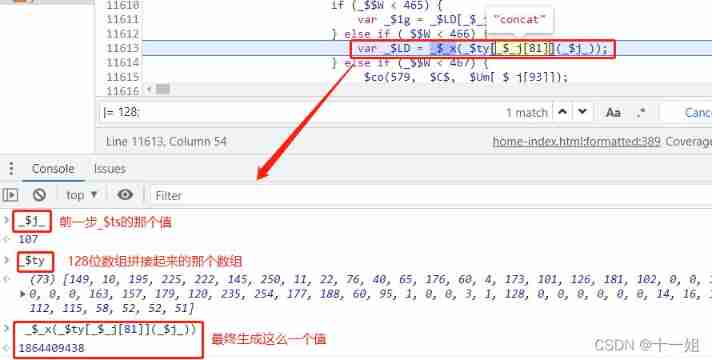


36、742 Control flow step 7 code , For timestamp , The timestamp difference is converted to an array , And it turns into cookie Prefix string
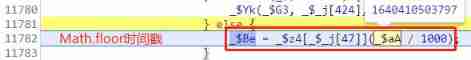






37、742 Control flow step 8 code ,
Generated cookie, Will be5 + Timestamp array string + (128 A combination of digits + 32 A combination of digits ) Array string converted to, thus 742 Control flow has ended ,go back to 772 Control flow of
38、772 Control flow into 742 Control the entry of the flow , Generated
_$$d namely cookie
39、772 The control flow then puts _$$d namely cookie Given to document.cookie, thus (772,1) Control flow ends

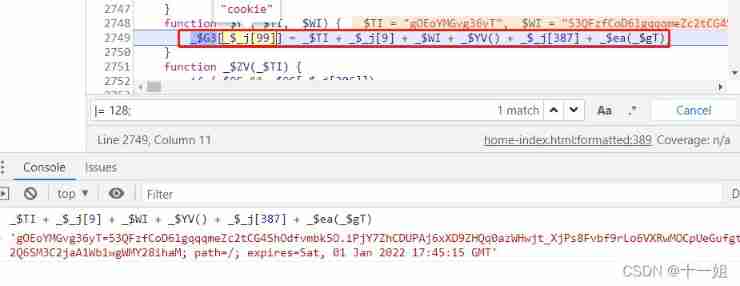

40、 Finally, the logic flow of the deduction code is as follows

3、 ... and 、cookie Operations after generation
- 1、
_$6p()The function performs the generation cookie after , The remaining 2 And then bind functions to some global objects , And thenBack to cookie To the front main.js 了

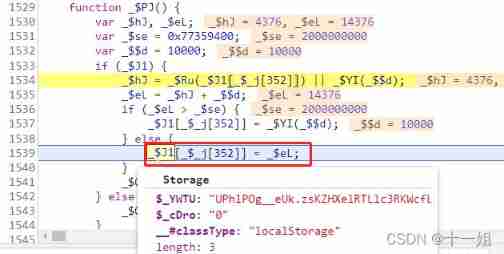
- 2、 among
_$6p()Function generation completed cookie after , give back_$tsThe property of is bound to a function ; And then there's the modification xhr Object , Picturedxhr.openTo be changed to another function ; modify xhr After the object is changedStorage.$_ndvalue , This parameter may be used in suffix generation

Four 、 Suffix generation analysis
1、 Suffix generation is recommended to see This article , as well as This article details why suffixes are not found , First determine which request and what suffix , If here search request , Two suffix parameters , Actually sum 4 Generation suffixes are the same xhr.open The function has been modified

2、 After the page has been loaded , Open the console and infinite will pop up debugger, then never pause here Beyond infinity debugger, then xhr Lower breakpoint , Then click the search button to trigger xhr request , It will automatically break to the following page , Then start to analyze

3、
_$9vFunction is the specific logical part of generating suffix , First pair url Parameter to array , Then generate the suffix hKHnQfLv, And then generate the suffix 8X7Yi61c
4、 The final suffix logic flow is as follows

边栏推荐
- Conversion between opencv and image (valid for pro test)
- Application features and functions of painting Aquarium
- What should I do when I feel confused after graduation from university?
- 【MySQL 04】使用MySQL Workbench 8.0 CE 備份及恢複Linux中的MySQL數據庫
- [binary tree] maximum binary tree II
- 搞透AQS原理(流程图及同步队列图解)
- (1) Basic learning - figure out the difference between pin, pad, port, IO and net
- MySQL monitoring 3
- MySQL monitoring 2
- [graph neural network] overview of graph classification learning [2]: graph classification based on graph neural network
猜你喜欢

Understand AQS principle (flow chart and synchronous queue diagram)
![[MRCTF2020]Ezpop-1|php序列化](/img/65/9b7a3ae3552d8784b0c77a1130d762.png)
[MRCTF2020]Ezpop-1|php序列化

Unity2D--给动画添加关键帧并绑定事件

Write this number in C

DTW学习(dynamic time warping)——思想、代码实现

C语言 成绩排名

What should be paid attention to in the design and production of the Urban Planning Museum

Using face_ Recognition library reports an error reason: cudnn_ STATUS_ NOT_ SUPPORTED

C language I want to pass

Scala基础【入门及安装】
随机推荐
012_ switch
工具与生活服务
(1)基础学习——图解pin、pad、port、IO、net 的区别
手势数字启蒙学习机
Varnish foundation overview 4
018_ rate
【MySQL 04】使用MySQL Workbench 8.0 CE 備份及恢複Linux中的MySQL數據庫
cookie加密8
Pytorch模型训练到哪里找预训练模型?
魔百盒CM201-2-CH-Hi3798MV300-300H-EMMC和NAND_红外蓝牙语音_通刷固件包
Scala basics [introduction and installation]
Fake divorce turns into real divorce. What about property
Local page floating animation is realized with the help of scroll wheel
Leetcode 46 Full arrangement (February 15, 2022)
Varnish foundation overview 3
What should I do when I feel confused after graduation from university?
[MySQL 04] sauvegarde et restauration de la base de données MySQL sous Linux en utilisant MySQL Workbench 8.0 ce
Que se passe - t - il si un faux divorce devient un vrai divorce?
Conversion between opencv and image (valid for pro test)
C语言 说反话