当前位置:网站首页>[actual combat record] record the whole process of the server being attacked (redis vulnerability)
[actual combat record] record the whole process of the server being attacked (redis vulnerability)
2022-07-03 22:01:00 【Anty_ Ria】
Catalog
summary
In the original project process , Pay more attention to the realization of project functions . And ignore a very important thing —— Disaster recovery capacity of the project . Although I have heard of hacker attacks , But I always feel that I am far away from these things , This kind of thing should not happen to me . Because of negligence , Then I had the experience of being attacked . Fortunately, the offensive means are relatively common , And the server alarms in time , I react quickly , Only then did we strengthen the solution to this crisis .
The whole process of the event
Plan to take a look at the server status before going to bed at night , It doesn't matter , It scares me directly .( Post a part , There are many subsequent attacks )
good heavens , This is really the first time I have encountered such a thing , Enter the alarm log and take a closer look , It is found that the server is offsite SSH Connected to , Blind guess should be brutally cracked password . Then click into the console … I'm a fool , This is really hard to break .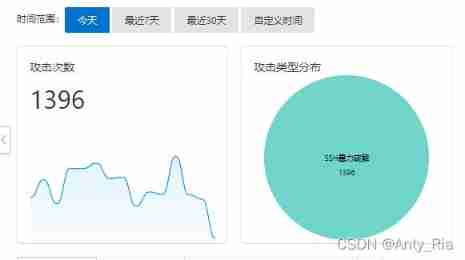
To tell the truth, I'm really flustered at this time , After all, the first experience . But there was a little excitement in the panic , Instantly ignite fighting spirit , Soon after calming down , First submitted Alibaba emergency work order , Then start to settle down and solve .
The earliest alarm was about the mining program , I can't think of the answer . My server is always fine , Where did the mining program come from , Is it because I accidentally downloaded the Trojan horse program ??
I follow the console log , Baidu all the way , Finally, I found a similar case . The server was invaded as a miner , But how can good without loopholes be invaded . I carefully recall my recent operation , Deployed two days ago Redis… wait ! It seems that I just saw one Redis Attack events caused by vulnerabilities .
Go back and watch it again , I found that the situation encountered by that brother was highly consistent with mine . Decisive and direct Baidu Redis dig . Directly open the door to the new world .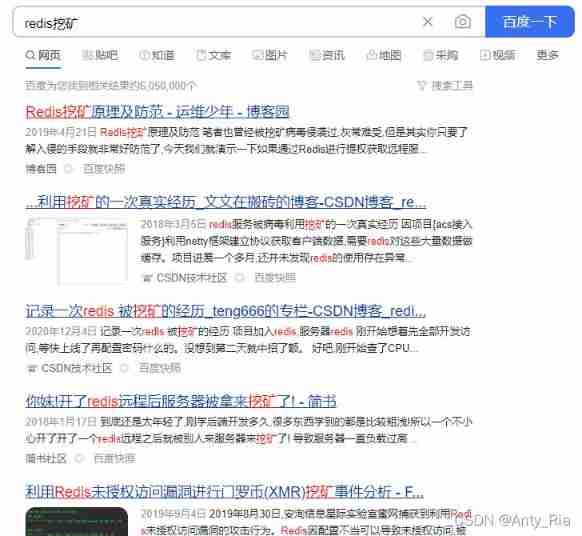
Because I have no experience , The whole processing process is fighting against resourcefulness . It can only be said that the attacker will always think one step more than you . When I try to stop Redis The service , One of me Root The account failed because of insufficient permissions .
Then , I try to use chattr Tools to empower , Then a dramatic scene happened , Console prompt command not found .
Is this uninstalled directly for me . Just when I was confused , The mobile phone receives the alarm message again : There are worm codes and Backdoors in the system , I realized that I should first try to block the source of the attacker . But at this time, the key is modified by the other party , Because there are no permissions , modify SSH The password has also failed .
I quickly switched to the console , Obtain again through other verification methods Administrator rights , thus , Everything began to get under control , I quickly revised SSH password , Then start cloud killing .
Have to say ,“ Problem procedure ” Are very hidden . Remove the most prominent documents , What impressed me more were the programs hidden in the system's scheduled tasks and the programs hidden in /tmp Some files under the folder .
But in artificial + Under the fierce offensive of both tools , Filter according to the time when the file was created , Quickly screened and cleaned up a batch of scripts . Then replace Redis Default port , Restart project , Modify the firewall .
But there has always been a ip Hang it here , Blocking cannot block , Just reverse it and see which bastard it is .

I found his website , Find out how to contact , Send an email warning directly !
Then just put this ip adopt iptables Full port black .
So far, the whole event is basically over , There may still be unclean places in the system . Other follow-up work will be done slowly .
This solution summary
The root cause :Redis Loophole
First, let's have a general understanding of the attack process :
Generally speaking , because Redis By default 6379 port . The attacker first uses the scanning tool to scan to open 6379 Port server , Then attack
The user puts his own key , adopt Redis Vulnerabilities in the replacement file mechanism , Sneak it into your server , This is the time , Attacker on
We've got it SSH The ability to connect . You can start further damage to the server .
Stop loss plan
- Shut down the server , The firewall shuts down immediately 6379 port . Cut off the attack input source .
- Rollback using server snapshots .
- Cloud kill , Handle suspicious files .
- Submit work orders quickly , Get advice and help from professionals
Prevention programs
- Often take snapshot backups of the server
- Replacement port , Do not use the default port , Set more complex passwords
- Pay more attention to Redis Update log of , Reacting quickly after the vulnerability is exposed will reduce losses .
- The realization of functions is no longer the first element in development , We should take into account security .
Main cause : Self factors
Insufficient attention has been paid to the risks of cloud deployment , Not enough attention has been paid to vulnerabilities .
summary
Through this event , Gained a lot of additional knowledge , Also alert yourself to unknown things, there are many , You must always be alert , Reduce unnecessary losses .
边栏推荐
- 2022 safety officer-a certificate registration examination and summary of safety officer-a certificate examination
- Electronic tube: Literature Research on basic characteristics of 6j1
- No more! Technical team members resign collectively
- JS Demo calcule combien de jours il reste de l'année
- MySQL - idea connects to MySQL
- Investment planning analysis and prospect prediction report of China's satellite application industry during the 14th five year plan Ⓑ 2022 ~ 2028
- How to install sentinel console
- 油猴插件
- English topic assignment (28)
- What is the content of the securities practice examination?
猜你喜欢

On my first day at work, this API timeout optimization put me down!

Notes on MySQL related knowledge points (startup, index)

Teach you how to install aidlux (1 installation)
![[SRS] build a specified version of SRS](/img/01/0d2d762e01b304220b8924d20277e3.jpg)
[SRS] build a specified version of SRS
Collection | pytoch common loss function disassembly

MySQL——idea连接MySQL

MySQL - idea connects to MySQL
Bluebridge cup Guoxin Changtian single chip microcomputer -- hardware environment (I)

90 后,辞职创业,说要卷死云数据库

The latest analysis of crane driver (limited to bridge crane) in 2022 and the test questions and analysis of crane driver (limited to bridge crane)
随机推荐
Capturing and sorting out external articles -- autoresponder, composer, statistics [III]
The 14th five year plan and investment feasibility study report of China's industry university research cooperation Ⓧ 2022 ~ 2028
2022 G3 boiler water treatment registration examination and G3 boiler water treatment examination papers
DR-AP40X9-A-Qualcomm-IPQ-4019-IPQ-4029-5G-4G-LTE-aluminum-body-dual-band-wifi-router-2.4GHZ-5GHz-QSD
What should the future of the Internet be like when Silicon Valley employees flee the big factory and rush to Web3| Footprint Analytics
treevalue——Master Nested Data Like Tensor
JS notes (III)
Miscellaneous things that don't miss the right business
Report on the development strategy of China's engineering bidding agency and suggestions for the 14th five year plan Ⓙ 2022 ~ 2028
Collections SQL communes
Electronic tube: Literature Research on basic characteristics of 6j1
常用sql集合
Memory analyzer (MAT)
抓包整理外篇——————autoResponder、composer 、statistics [ 三]
Are the top ten securities companies safe to open accounts and register? Is there any risk?
An expression that regularly matches one of two strings
Décompiler et modifier un exe ou une DLL non source en utilisant dnspy
Blue Bridge Cup Guoxin Changtian MCU -- program download (III)
China's TPMS industry demand forecast and future development trend analysis report Ⓐ 2022 ~ 2028
The latest analysis of R1 quick opening pressure vessel operation in 2022 and the examination question bank of R1 quick opening pressure vessel operation