当前位置:网站首页>[error record] Android application security detection vulnerability repair (strandhogg vulnerability | set activity component android:taskaffinity= "")
[error record] Android application security detection vulnerability repair (strandhogg vulnerability | set activity component android:taskaffinity= "")
2022-06-11 01:53:00 【Hanshuliang】
List of articles
One 、 Error message
Check whether the application exists StrandHogg Loophole :
StrandHogg It's an existence in Android Application vulnerabilities in multitasking systems . this
Exploit APP Inventory file AndroidManifest.xml in
android:taskAffinity Property settings for , Make installed in Android Evil on the equipment
An application can be disguised as any other application on the device , Including those requiring privileges
Any system application . When the user clicks the normal application icon , Malicious programs can block
Intercept and hijack this task , And pretend to be the interface of a normal application , So as to steal the user's
sensitive data . At the same time, malicious applications can also impersonate normal applications and request permission from users ,
Include SMS、 Photo 、 A microphone and GPS etc. , This allows attackers to access SMS and
Mail list 、 View Album 、 Eavesdropping and tracking the victim, etc .
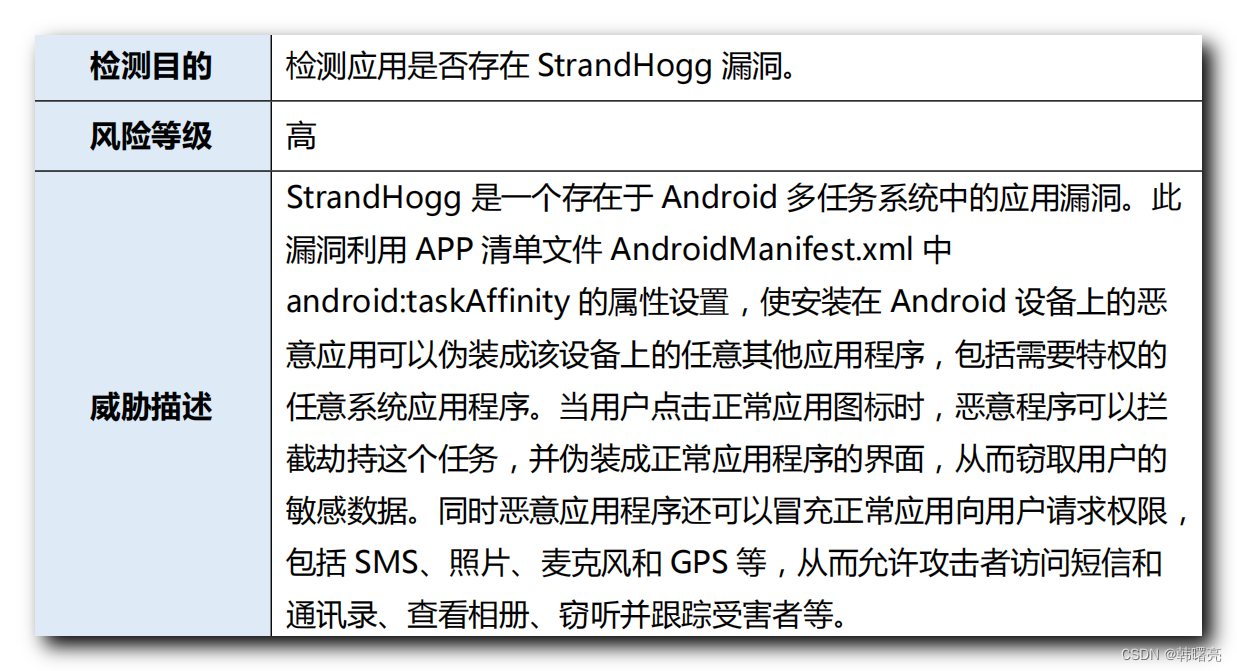
The report information generated during the above-mentioned inspection
Two 、 Revise the plan
stay AndroidManifest.xml In manifest file , Set all Activity Affinity properties of components :
android:taskAffinity=""
If there is direct setting of affinity attribute , If none is set to an empty string ;
边栏推荐
猜你喜欢
![[leetcode] a group of K flipped linked lists](/img/38/0b3cf215f49489bb5c3293471a818a.jpg)
[leetcode] a group of K flipped linked lists

【BSP视频教程】BSP视频教程第17期:单片机bootloader专题,启动,跳转配置和调试下载的各种用法(2022-06-10)

1.5、PX4载具选择
![[ongoing update...] 2021 National Electronic Design Competition for college students (III) interpretation of the anonymous four axis space developer flight control system design](/img/63/3193186820215b9babc3d00e1ef20b.jpg)
[ongoing update...] 2021 National Electronic Design Competition for college students (III) interpretation of the anonymous four axis space developer flight control system design

2021-2-26编程语言知识点整理
Linux安装mysql数据库详解

Xpath注入

The problem of slow response of cs-3120 actuator during use

Detectron2 trains its own dataset and converts it to coco format

视频压缩数据集TVD
随机推荐
[leetcode] flat multi-level bidirectional linked list
1.2. Ros+px4 preliminary basic knowledge
Leetcode 2054 two best non overlapping events
Win11触摸键盘主题如何更换?Win11更换触摸键盘主题的方法
【错误记录】Android 应用安全检测漏洞修复 ( StrandHogg 漏洞 | 设置 Activity 组件 android:taskAffinity=““ )
MeterSphere教程:接口返回结果为空时如何进行断言
AI 狂想|来这场大会,一起盘盘 AI 的新工具!
flutter_ Swiper carousel map plug-in
1.4PX4程序下载
Xpath注入
CLIP论文详解
2.2. Ros+px4 simulation multi-point cruise flight - Square
1.4px4 program download
Threejs: streamer effect encapsulation
薪的测试开发程序员们,你为何要走?和产品相互残杀到天昏地暗......
Threejs: how to get the boundingbox of geometry?
Be careful, these hidden "bugs" of "array" to "collection"“
从解读 BDC 自动生成的代码谈起,讲解 SAPGUI 的程序组成部分试读版
Threejs: pit encountered in drawing Bessel curve with two-point coordinates
Tencent Cloud Database tdsql - Dajia comments | The Past, Present and Future of basic software