当前位置:网站首页>Detailed explanation of redis's single login
Detailed explanation of redis's single login
2022-07-26 12:46:00 【User 9919783】
Environmental requirements :redis3.8.2+maven+springBoot+jdk1.8+freemarker Templates
1、 Demand background
At home on weekends , Last colleague suddenly contacted , Let me do a single sign on function for his website , So I sort out the logic first , Realize the function and record .
Single sign in (Single sign on) seeing the name of a thing one thinks of its function , After a website logs in , Other websites do not need users to continue to enter account passwords , And can login without secret , This technology is used very frequently in large websites , For example, Alibaba , When users log in to their system , Each subsystem can log in automatically , If you log in to a treasure , Log in to a monument , You also need a password , You also need to re-enter your password to log in to Taobao , This will definitely result in a very poor user experience , And the authentication logic of the system will also be troublesome , At this time, single sign on appears .
2、 Code instance
This article demonstrates two systems
1、 Ensure that when accessing the login page of the system , Enter the first homepage of the system , When visiting the login page of system 2 , Enter the homepage of system 2 .
2、 When accessing system one or system two , We need to judge redis Whether there is a current user in , If it exists, login without secret .
3、 Logical processing , Before logging in, first judge whether the account and password in the database are correct , If the user logs in correctly on the page , Then it returns login success , And put in redis, Set an expiration time for him .
4、 Guaranteed at redis Other subsystems can log in without secret within the expiration time .
边栏推荐
- What is a callback function? Understanding of the word "back"
- 编程式导航路由跳转到当前路由(参数不变), 多次执行会抛出NavigationDuplicated的警告错误?
- yolov7训练危险品识别 pytorch
- .eslintrc.js configuration description
- 什么是回调函数,对于“回”字的理解
- Understand test.py in gaitset
- Optical distance sensing chip 4530a combining ambient light, proximity sensing and infrared ranging
- Knowledge points of C language documents
- 14.2字节流学习
- “2022华为开发者大赛中国区东部赛区开幕式”在福州成功举办
猜你喜欢

【2243】module_ param.m

Code error reporting and problem solving experience II: test error reporting in yolov5
![[wechat applet] read the article, data request](/img/9a/3b9aef6c5f5735b886252ec830798c.png)
[wechat applet] read the article, data request
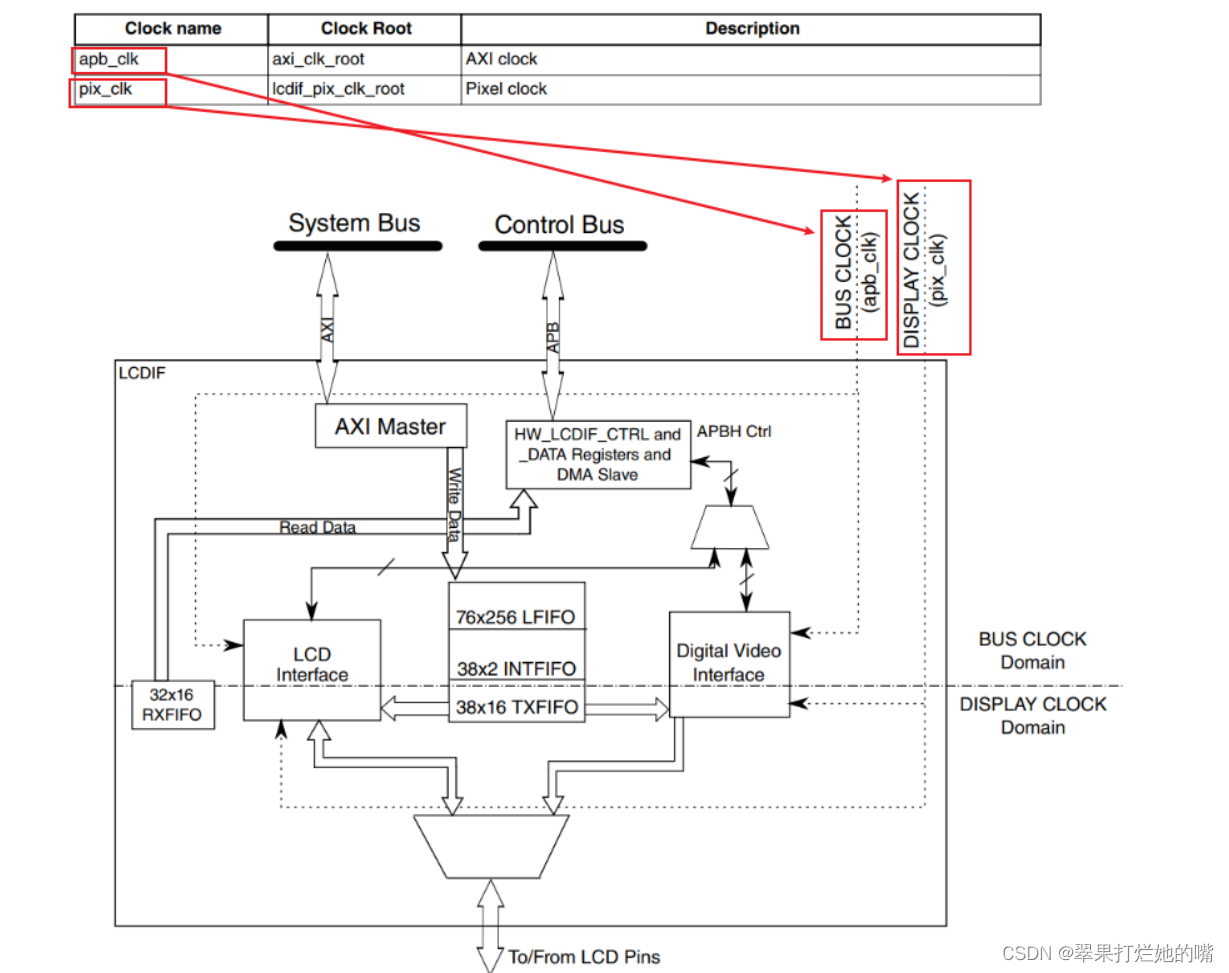
LCD笔记(7)LCD驱动程序框架_配置时钟

微软关闭了两种攻击途径:Office 宏、RDP 暴力破解

Redis master-slave replication principle

论文阅读-MLPD:Multi-Label Pedestrian Detector in Multispectral Domain(海康威视研究院实习项目)

Removable tablespace

Knowledge points of C language documents

Kubernetes----高级存储之PV和PVC简介
随机推荐
Data query where
数据库组成存储过程和函数
Removable tablespace
Flutter's learning path
论文阅读-MLPD:Multi-Label Pedestrian Detector in Multispectral Domain(海康威视研究院实习项目)
Analysis of Wireshark data package of network security B module of national vocational college skills competition Wireshark 0051.pcap
Kubernetes----高级存储之PV和PVC简介
14.2 byte stream learning
Optical distance sensing chip 4530a combining ambient light, proximity sensing and infrared ranging
可移动表空间
Oracle的Windows版本能在linux中使用吗?
In the digital era, what "golden treasure" is driving the development of pharmaceutical enterprises for a century?
如何组装一个注册中心?
行业案例|指标中台如何助力银行业普惠金融可持续发展
Minesweeping games - easy to play addictive (C language version)
Overseas app push (Part 2): Channel Integration Guide for overseas manufacturers
How much do you know about the two infrastructures of the badminton stadium?
Knowledge points of C language documents
Problems and solutions in the learning process of file class
.eslintrc.js configuration description