当前位置:网站首页>CTF Crypto---RSA KCS1_ Oaep mode
CTF Crypto---RSA KCS1_ Oaep mode
2022-07-25 06:58:00 【3tefanie, Zhou】
List of articles
subject
The title is given to two documents .RSA A public key file public.key, cipher text flag.encpublic.key
-----BEGIN PUBLIC KEY-----
MIIBJDANBgkqhkiG9w0BAQEFAAOCAREAMIIBDAKCAQMlsYv184kJfRcjeGa7Uc/4
3pIkU3SevEA7CZXJfA44bUbBYcrf93xphg2uR5HCFM+Eh6qqnybpIKl3g0kGA4rv
tcMIJ9/PP8npdpVE+U4Hzf4IcgOaOmJiEWZ4smH7LWudMlOekqFTs2dWKbqzlC59
NeMPfu9avxxQ15fQzIjhvcz9GhLqb373XDcn298ueA80KK6Pek+3qJ8YSjZQMrFT
+EJehFdQ6yt6vALcFc4CB1B6qVCGO7hICngCjdYpeZRNbGM/r6ED5Nsozof1oMbt
Si8mZEJ/Vlx3gathkUVtlxx/+jlScjdM7AFV5fkRidt0LkwosDoPoRz/sDFz0qTM
5q5TAgMBAAE=
-----END PUBLIC KEY-----
flag.enc
CQGd9sC/h9lnLpua50/071knSsP4N8WdmRsjoNIdfclrBhMjp7NoM5xy2SlNLLC2
yh7wbRw08nwjo6UF4tmGKKfcjPcb4l4bFa5uvyMY1nJBvmqQylDbiCnsODjhpB1B
JfdpU1LUKtwsCxbc7fPL/zzUdWgO+of/R9WmM+QOBPagTANbJo0mpDYxvNKRjvac
9Bw4CQTTh87moqsNRSE/Ik5tV2pkFRZfQxAZWuVePsHp0RXVitHwvKzwmN9vMqGm
57Wb2Sto64db4gLJDh9GROQN+EQh3yLoSS8NNtBrZCDddzfKHa8wv6zN/5znvBst
sDBkGyi88NzQxw9kOGjCWtwpRw==
The problem solving process
Can pass openssl You can get n and e Or make use of python Medium RSA Module acquisition n and e1.openssl obtain n and e
openssl rsa -pubin -text -modulus -in warmup -in public.key
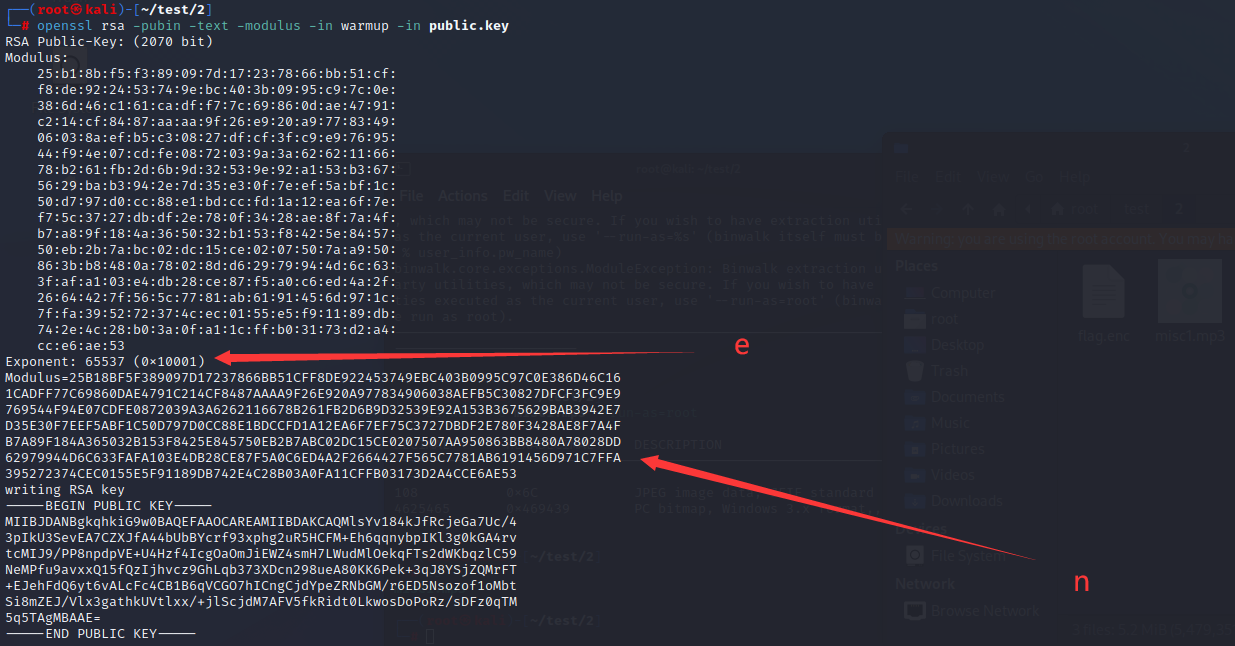
2. utilize python Medium RSA Module acquisition n and e
from Crypto.PublicKey import RSA
with open('C:\\Users\\ASUS\\ desktop \\crypto\\public.key', 'r') as f:
data = f.read()
key = RSA.importKey(data)
n = key.n
e = key.e
print(n)
print(e)
f.close()

Then read flag.enc, Proceed again base64 Decrypt the ciphertext C
with open('C:\\Users\\ASUS\\ desktop \\crypto\\flag.enc', 'r') as f:
data = f.read()
enc = base64.b64decode(data)
print(bytes_to_long(enc))
f.close()
Use yafu decompose n, obtain p and q
p= 3133337
q= 25478326064937419292200172136399497719081842914528228316455906211693118321971399936004729134841162974144246271486439695786036588117424611881955950996219646807378822278285638261582099108339438949573034101215141156156408742843820048066830863814362379885720395082318462850002901605689761876319151147352730090957556940842144299887394678743607766937828094478336401159449035878306853716216548374273462386508307367713112073004011383418967894930554067582453248981022011922883374442736848045920676341361871231787163441467533076890081721882179369168787287724769642665399992556052144845878600126283968890273067575342061776244939
And then I figured out phi_n as well as d
p= 3133337
q= 25478326064937419292200172136399497719081842914528228316455906211693118321971399936004729134841162974144246271486439695786036588117424611881955950996219646807378822278285638261582099108339438949573034101215141156156408742843820048066830863814362379885720395082318462850002901605689761876319151147352730090957556940842144299887394678743607766937828094478336401159449035878306853716216548374273462386508307367713112073004011383418967894930554067582453248981022011922883374442736848045920676341361871231787163441467533076890081721882179369168787287724769642665399992556052144845878600126283968890273067575342061776244939
phi = (p-1)*(q-1)
d = gmpy2.invert(e,phi)
Because the encryption script uses PKCS1_OAEP Mode of RSA encryption , So we need to manually construct the private key to decrypt the ciphertext . Use the original pow(c,d,n) It is impossible to decrypt the ciphertext correctly .
therefore , We need to start with PKCS1_OAEP Pattern construction private key , Then use this private key to decrypt the ciphertext file .
from Crypto.PublicKey import RSA
from Crypto.Cipher import PKCS1_OAEP
privkey = RSA.construct((int(n),int(e),int(d),int(p),int(q)))
key = PKCS1_OAEP.new(privkey)
flag = key.decrypt(enc)
print(flag)
Problem solving script
from Crypto.PublicKey import RSA
from Crypto.Cipher import PKCS1_OAEP
import base64
from Crypto.Util.number import *
import gmpy2
with open('C:\\Users\\ASUS\\ desktop \\crypto\\public.key', 'r') as f:
data = f.read()
key = RSA.importKey(data)
n = key.n
e = key.e
print(n)
print(e)
f.close()
with open('C:\\Users\\ASUS\\ desktop \\crypto\\flag.enc', 'r') as f:
data = f.read()
enc = base64.b64decode(data)
f.close()
p= 3133337
q= 25478326064937419292200172136399497719081842914528228316455906211693118321971399936004729134841162974144246271486439695786036588117424611881955950996219646807378822278285638261582099108339438949573034101215141156156408742843820048066830863814362379885720395082318462850002901605689761876319151147352730090957556940842144299887394678743607766937828094478336401159449035878306853716216548374273462386508307367713112073004011383418967894930554067582453248981022011922883374442736848045920676341361871231787163441467533076890081721882179369168787287724769642665399992556052144845878600126283968890273067575342061776244939
e= 65537
c = bytes_to_long(enc)
n = 79832181757332818552764610761349592984614744432279135328398999801627880283610900361281249973175805069916210179560506497075132524902086881120372213626641879468491936860976686933630869673826972619938321951599146744807653301076026577949579618331502776303983485566046485431039541708467141408260220098592761245010678592347501894176269580510459729633673468068467144199744563731826362102608811033400887813754780282628099443490170016087838606998017490456601315802448567772411623826281747245660954245413781519794295336197555688543537992197142258053220453757666537840276416475602759374950715283890232230741542737319569819793988431443
phi = (p-1)*(q-1)
d = gmpy2.invert(e,phi)
privkey = RSA.construct((int(n),int(e),int(d),int(p),int(q)))
key = PKCS1_OAEP.new(privkey)
flag = key.decrypt(enc)
print(flag)
flag:
EKO{
classic_rsa_challenge_is_boring_but_necessary}
【 Green locust shade , Bright moonlight . The spring breeze blows , All flowers compete for beauty 】
边栏推荐
- CTF Crypto---RSA KCS1_OAEP模式
- What are the hazards of insufficient sleep?
- Two week learning results of machine learning
- [C language] program environment and preprocessing
- MySQL remote login
- Observer mode
- Recycleview realizes horizontal sliding of overlapping items
- 【C】程序环境和预处理
- [jailhouse article] base architectures for virtual physical computing (2018)
- Simple factory factory method Abstract Factory
猜你喜欢
![[C language] document processing and operation](/img/d7/3d34401f78399dcd6d571bc0bc84bf.png)
[C language] document processing and operation

【愚公系列】2022年7月 Go教学课程 015-运算符之赋值运算符和关系运算符

使用 Web API 上传和下载多个文件

Rambus announces ddr5 memory interface chip portfolio for data centers and PCs

微生物健康,不要排斥人体内微生物

Observer mode

Common mode inductance has been heard many times, but what principle do you really understand?

常吃发酵馒头是否会伤害身体

Qt实战案例(53)——利用QDrag实现拖拽拼图功能

健康打卡每日提醒累了?那就让自动化帮你---HiFlow,应用连接自动化助手
随机推荐
Builder pattern
"Wei Lai Cup" 2022 Niuke summer multi school training camp 1 supplementary problem solution (incomplete)
Easy to use code statistics tool
Microorganisms are healthy. Don't exclude microorganisms in the human body
Tp5.1 foreach adds a new field in the controller record, and there is no need to write all the other fields again without changing them (not operating in the template) (paging)
[daily question] sword finger offer II 115. reconstruction sequence
【transformer】DeiT
Clear wechat applet and wechat H5 cache
Over adapter mode
Mysql database
流量对于元宇宙来讲并不是最重要的,能否真正给传统的生活方式和生产方式带来改变,才是最重要的
微生物健康,不要排斥人体内微生物
Tab bar toggle style
The ultimate difference between MVC and three-tier architecture
The code of Keil and Si compiler is not aligned??
Cointegraph wrote: relying on the largest Dao usdd to become the most reliable stable currency
Two week learning results of machine learning
Simple factory factory method Abstract Factory
JS data type judgment - Case 6 delicate and elegant judgment of data type
[add, delete, modify, and check the array base]