当前位置:网站首页>X86 CPU, critical! The latest vulnerability has caused heated discussion. Hackers can remotely steal keys. Intel "all processors" are affected
X86 CPU, critical! The latest vulnerability has caused heated discussion. Hackers can remotely steal keys. Intel "all processors" are affected
2022-06-25 03:41:00 【QbitAl】
Fish and sheep From the Aofei temple
qubits | official account QbitAI
x86 CPU, dangerous !
A new safety study shows that : In a country called Hertzbleed Under the attack mode of , Hackers can steal encryption keys directly from remote servers .
Whether it's Intel or AMD CPU, It's not immune .
The scope of influence is probably aunt sauce's .
Intel : All .

AMD:

The research came from research institutions such as the University of Texas at Austin and the University of Illinois at Urbana Champaign , Once the relevant papers were issued, they triggered a heated discussion .

What exactly happened , Let's study it carefully together .
in the light of DVFS The attack of
In cryptography , Power analysis It is a side channel attack method that has long existed .
for instance , By measuring the power consumed by the chip while processing data , Hackers can extract this encrypted data .
Fortunately, power analysis can not be realized remotely , The attack means are relatively limited .
But in Hertzbleed in , The researchers found that , Use dynamic voltage frequency scaling (DVFS), The power side channel attack can be transformed into a remote attack !
and DVFS, It is what major manufacturers are currently using to reduce CPU An important function of power consumption .
To be specific , The researchers found in the experiment , In some cases ,x86 The dynamic frequency scaling of the processor depends on the data being processed , Its particle size is milliseconds .
That is to say ,DVFS Caused by the CPU Frequency variation , It can be directly linked to the power consumption of data processing .
because CPU The difference in frequency can be converted into the difference in actual occurrence time , By monitoring the response time of the server , Attackers can observe this change remotely .

In the paper , The researchers are running SIKE( An encryption algorithm ) Tested on the server of Hertzbleed.
Results show , In an unoptimized attack version , They were in 36 Hours and 89 Within hours , Completely extracted Cloudflare Encryption library CIRCL And Microsoft PQCrypto-SIDH All keys in .
Intel &AMD: No patch
The researchers say , They are already in 2021 To Intel in the third quarter of 、Cloudflare And Microsoft disclosed the research . First quarter of this year , They also share AMD There was communication .
however , Intel and AMD There are no plans to patch this .
Intel senior director of secure communications and event response Jerry Bryant Think :
Although it is interesting from a research point of view , But we don't think this kind of attack is feasible outside the laboratory environment .
Intel rated the vulnerability as medium .
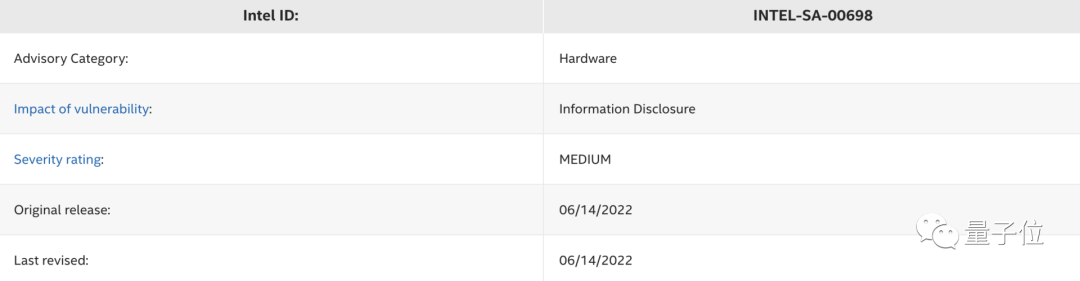
But Intel also mentioned in the announcement : Guidelines are being released to address this potential vulnerability .
While Microsoft and Cloudflare aspect , The encryption code base has been updated .
The researchers estimate that , These updates make CIRCL and PQCrypto-SIDH The cost of unpacking performance increases 5% and 11%.
They mentioned , Disable the frequency boost function , Intel's “Turbo Boost”、AMD Of “Turbo Core” etc. , Can ease Hertzbleed The problems brought about by , But this will have a bad impact on the system performance .
in addition , What's interesting is , The researchers revealed that , Intel did not issue a patch , But they were asked to postpone the release of the findings .
Reference link :
[1]https://www.hertzbleed.com/
[2]https://arstechnica.com/information-technology/2022/06/researchers-exploit-new-intel-and-amd-cpu-flaw-to-steal-encryption-keys/
— End —
Live registration | Arrayed optical waveguide :
Push AR The display technology of glasses going to the consumer market within three years
The development of metacosmic industry , Bringing together cutting-edge technologies , Build a new form of the next generation Internet . and AR equipment , Or will become the next generation of Internet “ Access level ” equipment .
Consumption level AR What is the core competitiveness of the equipment ?AR What is the technical principle of optical module ? How is its development ? Your first pair AR What will the device look like ?6 month 16 Japan , The live broadcast will be announced ~

Focus on me here , Remember to mark the star ~
边栏推荐
- MySQL根据表前缀批量修改、删除表
- Is it safe to open a stock account with the customer's haircut account link? Tell me what you know
- Wechat applet obtains the parameters carried after scanning the QR code
- Overview of AOSP ~ WiFi architecture
- 单例的饥饿、懒汉模式案例
- 发布功能完成02《ivx低代码签到系统制作》
- AI自己写代码让智能体进化!OpenAI的大模型有“人类思想”那味了
- Huawei failed to appeal and was prohibited from selling 5g equipment in Sweden; Apple regained the first place in the world in terms of market value; DeNO completes round a financing of USD 21million
- Tutorial on installing SSL certificates in Microsoft Exchange Server 2007
- Expressing the transformation of two coordinate systems with vectors
猜你喜欢

About sizeof() and strlen in array

后台页制作01《ivx低代码签到系统制作》

支付宝被风控7天怎么办?付解决方案

MySql安裝教程

Array - fast and slow pointer in one breath

TCC mode explanation and code implementation of Seata's four modes

ICML 2022 | 字节跳动 AI Lab 提出多模态模型:X-VLM,学习视觉和语言的多粒度对齐...
20年ICPC澳门站L - Random Permutation

automated testing

nacos实践记录
随机推荐
New solution of 202112-2 sequence query
mysql学习笔记--单张表上的增删改查
马斯克被诉传销索赔2580亿美元,台积电公布2nm制程,中科院发现月壤中含有羟基形式的水,今日更多大新闻在此...
Insurance app aging service evaluation analysis 2022 issue 06
大咖说*计算讲谈社|如何提出关键问题?
Is it safe for Guoxin golden sun to open an account in the steps of opening new bonds
Introduction to database system
Difference between left join on and join on
What is an SSL certificate and what are the benefits of having an SSL certificate?
Expressing the transformation of two coordinate systems with vectors
How does the administrator prohibit another person from kicking himself?
Datetimeformat is invalid under @requestbody
Install ffmpeg in LNMP environment and use it in yii2
Wechat applet obtains the parameters carried after scanning the QR code
Tutorial on installing SSL certificates in Microsoft Exchange Server 2007
发布功能完成02《ivx低代码签到系统制作》
AI自己写代码让智能体进化!OpenAI的大模型有“人类思想”那味了
Rebeco: using machine learning to predict stock crash risk
Is it safe to open an online stock account?
VSCode中如何实现点击DOM自动定位到相应代码行