当前位置:网站首页>File upload vulnerability (III)
File upload vulnerability (III)
2022-06-25 04:54:00 【Key_ Words】
The first part : Basic overview of file upload
File upload vulnerability means that the user uploads an executable script file , And through this script file to obtain the ability to execute server-side commands . A common scenario is web The server allows users to upload pictures or save ordinary text files , Users bypass the upload mechanism to upload malicious code and execute it to control the server . Obviously, this loophole is getshell One of the fastest and most direct methods , It should be noted that there is no problem with uploading files , The problem is that after the file is uploaded to the server , How the server processes and interprets files .
The second part : Basic operation of file upload
1. Modify the file name suffix
The suffix of normal picture file is generally jpg png gif etc.
First upload a picture code , Then, modify the suffix to... Through packet capturing .php Implement a simple bypass .
2. Modify file Content-Type type (MIME)
The normal picture type is :image/gif image/png image/jpeg etc.
Upload a php file , adopt bp Catching the bag php Of Content-Type Change to the normal picture type to bypass .
3. Upload php3 php4 php5 phtml And so on
If the other party's blacklist is only right php Suffixes are filtered , Not considered php5 This kind of , Then you can upload directly php3 The back door of such suffixes
4. Upload (.htaccess) The file of , Then upload the image Trojan horse

5. Case write 、 Add a space and a dot at the end 、::$DATA Bypass
When the other party does not filter one or more of the four , Use bp After capturing packets, modify the implementation to bypass
6. The spaces and dots at the end of the overlay bypass 、 superposition php Bypass
The spaces and dots at the end of the overlay bypass : When the other party's blacklist detects spaces and dots only once , Can stack bypass .
superposition php Bypass : When the other side's blacklist will be right php When such suffixes are removed and removed only once , Can stack bypass .
The third part : White list bypass
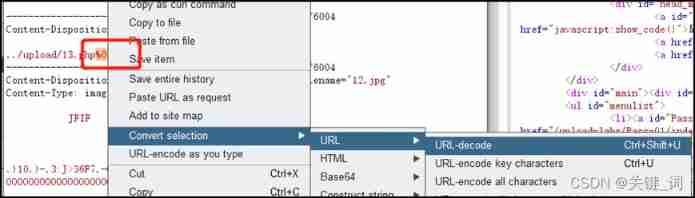
1.%00 truncation ( Judge GET still POST Accept parameters )
(1) If it is GET Acceptance value 、 Upload a jpg picture , Then change the path , Here's the picture :

(2) If it is POST Acceptance value 、 Upload a jpg picture , Then change the path , then %00 Conduct URL code :
2. picture +php Code , Form a picture code to upload
Premise : Want to parse out the php Code , The website must contain vulnerabilities .
First make a picture code , It can be used directly Notepad Open the picture directly and add a php Code , But need 16 Base number , Otherwise the picture may go wrong . It's fine too cmd Generate , Command statement :copy 14.jpg /b + 14.php /a webshell.jpg As shown in the figure , We are uploading this generated image .

Access after uploading
3. getimagesize() function
principle : This function means : The target file will be 16 To do a read , To read the first few strings is not in line with the requirements of the picture
Bypass : Whether the test can cooperate with the file containing vulnerability to bypass .
4. exif_imagetype() function
principle : Read the first byte of an image and check its signature .
Bypass : Whether the test can cooperate with the file containing vulnerability to bypass .
The second kind :
5. move_uploaded_file() function
The first one is :
Principle and its bypass : Function img_path By post Parameters save_name The control of the , Can be in save_name utilize %00 truncation ( Be careful php Version below 5.3).
The second kind :
move_uploaded_file() There is such a feature , The end of the file is ignored /.
6. Second rendering
Bypass imagecreatefromjpeg() function
Upload according to the original method , We can find that it can still be uploaded , However, the cooperation contains vulnerabilities that cannot be resolved , At this time, we copy the uploaded picture and use Notepad open , Found what we originally wrote php The code is gone , This is the second rendering, which puts the inside of us php The code is deleted .
We compare the original picture with his modified picture , See which part hasn't been modified . take php Put the code in the unchanged part , Cooperation contains vulnerabilities , That's all right. . Use HxD Hex Editor Compare :
:
The specific implementation needs to be written by myself Python Program , It is basically impossible to construct an image that can bypass the rendering function by manual attempt webshell Of , Just know how to solve it
Be careful : If the second rendering is verified before uploading, there is no way .
7. Conditional competition
principle : Let's look at the code. He uploads the pictures first , Just start to judge the suffix 、 Second rendering . If we access this file at the moment we upload it , Then he can't delete this file 、 Second rendering . This is equivalent to opening a file , Then delete the file , You will be prompted that this file is opened in another program and cannot be deleted
8. Array bypassing

Upload_labs Answer link :https://www.cnblogs.com/-an-/p/12666933.html
9. Cooperate with parsing vulnerability to bypass
(1)IIS 6.0 Parsing vulnerabilities
(2)Apache Parsing vulnerabilities
(3)Nginx Parsing vulnerabilities
(4)Windows File naming
Part of the article refers to , Link to the original text :https://blog.csdn.net/weixin_39190897/article/details/85334893
边栏推荐
- Working principle of asemi three-phase rectifier bridge
- XML (VIII)
- Apache+php uploading large files
- Kotlin Compose 监听软键盘 点击enter提交事件
- Immutable learning road -- farewell to traditional copy
- 515. find the maximum value / Sword finger offer II 095 in each tree row Longest common subsequence
- Sleep more, you can lose weight. According to the latest research from the University of Chicago, sleeping more than 1 hour a day is equivalent to eating less than one fried chicken leg
- buuctf(re)
- buuctf web
- Upgrade PHP to php7 The impact of X (2), the obsolescence of mcrypt decryption
猜你喜欢
随机推荐
parallel recovery slave next change & parallel recovery push change
In Net 6 using dotnet format formatting code
Write shell script error summary
dotnet-exec 0.4.0 released
Heavy broadcast | phase shift method + mathematical principle derivation of multi frequency heterodyne + implementation
What if win11 Bluetooth fails to connect? Solution of win11 Bluetooth unable to connect
基于SSH实现的学生成绩管理系统
Calculate student grade (virtual function and polymorphism)
固态硬盘开盘数据恢复的方法
Immutable learning road -- farewell to traditional copy
ASEMI三相整流桥的工作原理
Specific operations for uploading pictures in PHP
[image fusion] image fusion based on MATLAB directional discrete cosine transform and principal component analysis [including Matlab source code 1907]
How PHP gets the user's City
Record the problem of C # print size once
ROS2/DDS/QoS/主题的记录
ThinkPHP 5 log management
OOP stack class template (template +ds)
Google Earth Engine(GEE)——全球JRC/GSW1_1/YearlyHistory数据集的批量下载(中国区域)
本轮压力测试下,DeFi协议们表现如何?






![[untitled]](/img/68/5e711f7c473dcea54a56f7b7e48604.png)

