当前位置:网站首页>Analysis of source code data anti leakage solution
Analysis of source code data anti leakage solution
2022-06-09 20:46:00 【Cnsidna. No.1】
Why source code management
Various embedded R & D and platform software R & D industries , Each has its own core data and core documents , User data and other sensitive information , These information data have the following commonalities :
It belongs to the core confidential information , In case of leakage, it will have a bad impact on
There are many types of core data , Source code data , Employees have high computer skills
A lot of data is in the business system , It's not a document
If you don't control , Designers and users can easily copy the data through various ways , Cause leakage .
Common secret related ways for R & D personnel
Because R & D personnel are more proficient in computers than ordinary office personnel , In addition to the common network , mail ,U disc ,QQ And other data diffusion methods , There are many other methods that are very easy for developers ( Not listed completely ):
Physical method :
Network cable direct connection , Unplug the network cable from the wall , Then connect directly to an uncontrolled computer ;
winPE start-up , Via CD or U Discoid winPE start-up , Even directly ISO The image starts .
virtual machine , Through installation VMWare virtual machine , Use peripherals in the virtual machine U disc , The Internet .
Other uncontrolled computers , That is, copy the data to other uncontrolled computers in the network , transit
Upload online , By building an upload server on the public network , Bypass Internet Behavior Management
Data distortion :
Write a console program , Print the code to DOS On the console, and then save the screen information as ;
Write the code to Log Log file , Or write code to shared memory , Then another program reads away .
Write interprocess communication program , Pass the code through socket, news ,LPC,COM,mutex, Shear plate , Pipeline and other interprocess communication methods , Transfer to send the data ;
adopt IIS/Tomcat etc. web The parser transfers , Publish the code data as a web page , Then browse the browser and save as , Or just write txt box , Copy all the code during initialization ;
Peripheral transfer
For embedded development scenarios , You can use the serial port ,U mouth , The network port burns the code to the equipment and leaks the secret
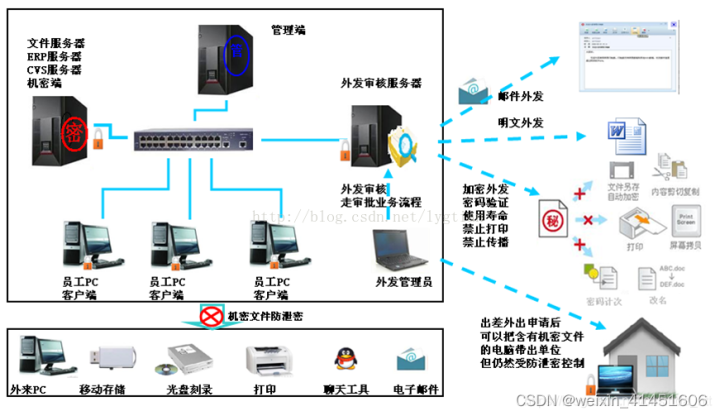
SDC Sandbox anti disclosure software
Developed by shenxinda SDC Sandbox leak proof products , Adopt kernel defense in depth , It is a driver level anti disclosure Software . Do not encrypt files , A sandbox is like a container , The container contains our confidential information . The documents we work on are all in sandboxes . The sandbox is completely isolated from ordinary computers . You might ask , What if I want to access the Internet , All programs to access the Internet are launched from the tray , Such as browser , Chat software, etc .SDC The sandbox is divided into the following parts : The management end , Confidential end , Documents are sent out , client .
The management end : Sandbox Control Center , Control all clients . The control of the client covers all aspects . Let me give you a few control functions : Reverse screenshot When someone wants to view some confidential information of the company remotely to the employee's computer ,SDC The client will control the remote software , Remote people see a black screen . But the computers on the staff side are in normal use . If you can control, you can let go . clipboard In sandbox mode, employees want to copy and paste company data such as files to the Internet through the clipboard ,SDC Sandbox is controlled , You can control the maximum number of clipping words .
Confidential end : Escort the server , Ordinary computers do not have access to confidential servers . Only sandbox computers can access , Do not encrypt the company's data , Protect data to the greatest extent .
client : Normal mode and sandbox mode . All software installation should be in sandbox mode . Work must be in sandbox mode , Because all the working data are on the encrypted disk , Sandbox can only be accessed in encrypted mode . In sandbox mode, it is isolated from the outside world . To access the Internet, only programs launched from the tray can , And follow the principle of only getting in and not getting out , Can get files from the Internet to the sandbox computer , However, to send documents from this machine to the Internet, you have to go through document approval .
Documents are sent out : A file distribution system is installed on a computer . The of this computer ip That is, the address where the document is sent out . Each sandbox employee matches an account number for sending out files . The specific approval method is not cumbersome here .
边栏推荐
- Lambda Exception
- Mr. wuyaohui, the world pioneer of ordinary ternary logic mathematics, announced the scientific research achievements of all truth tables of ordinary ternary logic mathematics to the world (Wu's law)
- LeetCode 497. 非重叠矩形中的随机点**
- Who says redis can't save big keys
- Basic flow of data processing
- Application of anonymous function in C #
- UTM to latitude and longitude
- Detailed explanation of uboot
- Open source a nodejs firewall gadget
- Redis知识点
猜你喜欢

Integer ordered array lookup -- traversal and half / bisection
![[tgowt] cmake to Ninja construction](/img/e9/8ce56c421ee98c0b36464fc65dd39d.png)
[tgowt] cmake to Ninja construction

The HMI Software memory is abnormal, resulting in a crash exit bug

SSM driving school management system

A potential bug in creating project generated word library in HMI

Bug in upgrading SD card / TF card of HMI serial interface screen

排序-快速排序

Ceisum三维场景demo

Just learning embedded, I want to ask what is interrupt and what is the concept of interrupt

dump. Pcapng packet parsing
随机推荐
UTM to latitude and longitude
C#中关于Partial的作用
Extended application of C # static class
C reverse sort
c#逆序排序
idea:new没有class
Parsing fluent from source code_ Precise local refresh of Redux
Share 10 tips on using reduce function
Integer ordered array lookup -- traversal and half / bisection
Daily question - leecode59 (spiral matrix II)
Kubevirt network source code analysis
Gamefi's new departure, aquanee will log in to gate and bitmart on June 9
Some applications between delegates and events in C #
关于C#Unity读写文件
ModelArts存储方案建议
Share 4 methods of JS deep copy
Mysql:1062 Duplicate entry '1' for key 'PRIMARY'
Redis知识点
[database data recovery] SQL Server database data recovery case
HMI 软件内存异常,导致奔溃退出的bug