当前位置:网站首页>john爆破出現Using default input encoding: UTF-8 Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
john爆破出現Using default input encoding: UTF-8 Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
2022-07-02 16:47:00 【鐵錘2號】
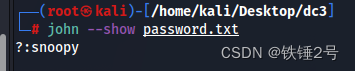
出現這個提示不是說明破解失敗了,而是這個hash以前被你破解過,可以使用以下命令查看破解出的密碼是什麼。
john --show password.txt
例子
有一個password.txt中存儲了哈希,之前被我破解過,我再破解出現上述提示
john password.txt
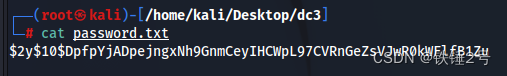

我們重新加載之前破解出來的密碼
john --show password.txt
边栏推荐
- LeetCode 6. Z 字形变换 (N字形变换)
- 大廠面試總結大全
- ROW_NUMBER()、RANK()、DENSE_RANK区别
- The median salary of TSMC's global employees is about 460000, and the CEO is about 8.99 million; Apple raised the price of iPhone in Japan; VIM 9.0 releases | geek headlines
- Vscade set multi line display of tab
- pwm呼吸灯
- Kubernetes family container housekeeper pod online Q & A?
- Some problems about MySQL installation
- Privacy computing technology innovation and industry practice seminar: Learning
- 历史上的今天:支付宝推出条码支付;分时系统之父诞生;世界上第一支电视广告...
猜你喜欢
![[North Asia data recovery] data recovery case of raid crash caused by hard disk disconnection during data synchronization of hot spare disk of RAID5 disk array](/img/51/f9c1eed37794db8c8d0eefd60b9e3d.jpg)
[North Asia data recovery] data recovery case of raid crash caused by hard disk disconnection during data synchronization of hot spare disk of RAID5 disk array
大廠面試總結大全
pwm呼吸灯

总结|机器视觉中三大坐标系及其相互关系

Today in history: Alipay launched barcode payment; The father of time-sharing system was born; The first TV advertisement in the world

Mathematical analysis_ Notes_ Chapter 5: univariate differential calculus

基于Impala的高性能数仓实践之执行引擎模块

The median salary of TSMC's global employees is about 460000, and the CEO is about 8.99 million; Apple raised the price of iPhone in Japan; VIM 9.0 releases | geek headlines
![OSPF - route aggregation [(summary) including configuration commands] | address summary calculation method - detailed explanation](/img/8b/36be3191a7d71f4a8c8181eaed8417.jpg)
OSPF - route aggregation [(summary) including configuration commands] | address summary calculation method - detailed explanation
Yyds dry inventory company stipulates that all interfaces use post requests. Why?
随机推荐
绝对真理和相对真理思考
LeetCode 3. 无重复字符的最长子串
Résumé de l'entrevue de Dachang Daquan
Unity uses ugui to set a simple multi-level horizontal drop-down menu (no code required)
Unity Json 编写
基于Impala的高性能数仓实践之执行引擎模块
Bone conduction non ear Bluetooth headset brand, bone conduction Bluetooth headset brand recommendation
Global and Chinese market of desktop hot melt equipment 2022-2028: Research Report on technology, participants, trends, market size and share
外企高管、连续创业者、瑜伽和滑雪高手,持续迭代重构的程序人生
LeetCode 2. Add two numbers
【云原生】简单谈谈海量数据采集组件Flume的理解
Mathematical analysis_ Notes_ Chapter 5: univariate differential calculus
618 deep resumption: Haier Zhijia's winning methodology
请问怎么在oracle视图中使用stustr函数
What is normal distribution? What is the 28 law?
虚假的暑假
七一献礼:易鲸捷 “百日会战”完美收官 贵阳银行数据库提前封板
Global and Chinese market of oil analyzers 2022-2028: Research Report on technology, participants, trends, market size and share
月报总结|Moonbeam6月份大事一览
Interview summary of large factories