当前位置:网站首页>What is a subnet mask? (Powercert animated videos)
What is a subnet mask? (Powercert animated videos)
2022-06-25 20:58:00 【Leap soil and tea】
What is Subnet Mask?
This article is a translation of the following link video :
【IT Hard core animation handling / Chinese and English double characters 】 What is a subnet mask ?
Example of subnet mask
Suppose you have a small business ,IP Address :192.168.1.0, Subnet mask :255.255.255.0, Now suppose your small business has a total of 12 Computers , all 12 All computers are on the same network , These computers belong to different departments , Represented by color , But suppose you want to divide these computers into three different networks , In this way, each department can not see the network traffic of other departments .
therefore , You want to split a network in your enterprise into three small networks .
The method of splitting this network into smaller networks is realized through subnets , The method is to change the default subnet mask by borrowing some bits specified by the host and using them to create a subnet .
- In this subnet mask , We will change some zeros in the host part to one , So we can create more networks .
- If we keep the subnet mask unchanged , It will get a containing 256 Network of hosts , Technically speaking , We must now subtract the host , Because the values are 1,0 Reserved for broadcast and network addresses respectively , So we actually have 254 Available hosts .
We need to change this subnet mask , So we can generate the three networks we need
for example , Let's borrow one from the mainframe section , This is our new subnet mask , So now the fourth binary octet is 128, Because when you calculate the first bit of the binary octet , It's equal to 128.
1) Borrow a bit , This will divide the network in two , So now it is no longer a containing 254 Network of hosts , Instead, provide two networks or each subnet that contains 126 Of hosts .
2) Now let's continue borrowing another bit from the host section , Now we have borrowed two people from the host , So this is the new subnet mask in our fourth binary octet 192, So by borrowing two , This will further divide the network , Now we will have four subnets , Each subnet has 62 Console host .
3) Let's borrow another bit from the host part again , This is a new subnet mask , By borrowing 3 position , This will divide the network into 8 Subnet , Each subnet has 30 Console host .
4) If we borrow four bits , We will get 16 Subnet , Each subnet has 14 Console host
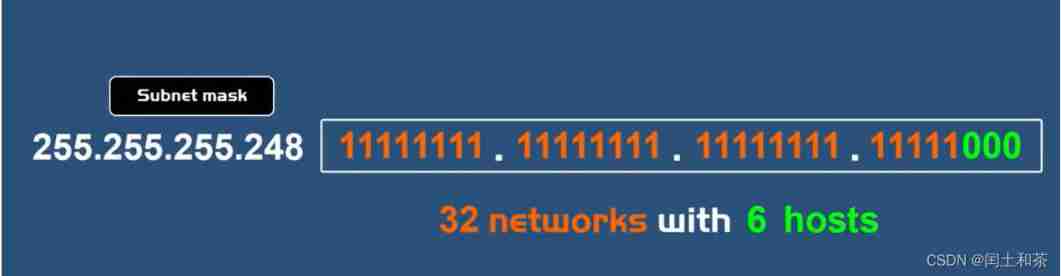
5) If we borrow 5 A bit , We will get 32 Subnet , Each subnet has 6 Host computer .
6) If we borrow 6 position , We will get 64 Subnet , Each subnet has two hosts
7) If we borrow 7 position , It will provide us with 128 Subnet , But no hosts are available .
The more bits the network portion borrows from the host portion , The number of networks that can be created doubles , However, the number of hosts per network will also be reduced by half at each bidding .
If we want to divide this network into three smaller networks or subnets , We have to borrow two bits from the host part , So even if we only need three networks , This subnet mask at least allows the network to work with it . Therefore, the new custom subnet mask of our three subnets is 255.255.255.192
So now our network is divided into three smaller subnets .
IP Address classification
- Addresses and subnet masks fall into five different categories , namely A To E class .
- A,B,C Classes are used for commercial purposes
- You can IP The number in the first octet of the address and the default subnet mask to distinguish which category they belong to .
A、B and C Class IP Diagram of address and default subnet mask
Now? , When organizations need to be connected , They will need one according to the needs of the organization IP Address category , This category is based on the number of hosts they have . therefore , If an organization has many hosts , They will need one A class IP Address , One A class IP Addresses can be generated up to 1600 Ten thousand hosts .
A class IP The host part of the address is very large , The host uses three octets , This is why it can generate so many hosts . An example of an organization needing so many hosts is similar to Internet Service provider , Because they need to put millions IP Address distribution to all customers .
One B class IP The address can generate up to 65000 hosts . This category is applicable to large and medium-sized organizations .
One C class IP Addresses can generate 254 Console host . One C class IP Addresses are used for small organizations and families with few hosts .
CIDR
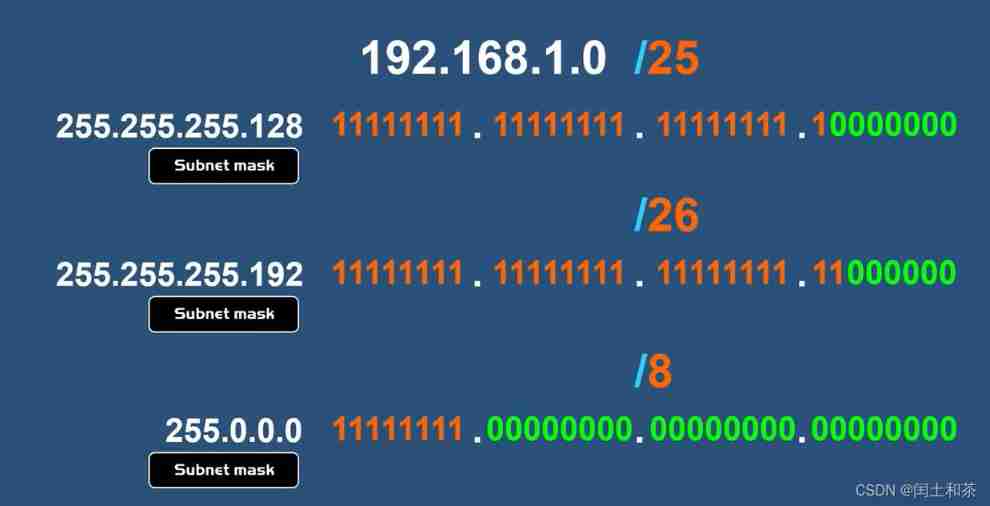
The subnet mask can also be called CIDR To represent .CIDR Represents classless inter domain routing , Also known as slash notation . Slash notation is a shorter way to write a subnet mask , It does this by writing a forward slash , Then write a number in the count subnet mask to achieve this
for example , If you see IP The address is denoted by a slash 24. This means that the length of the subnet mask is 24 position , That is to say, its length is 24 position .
If the sign is a slash 25, This means that the length of the subnet mask is 25 position , Or if it's a slash 26, This means that the length of the subnet mask is 26 position , Or if CIDR The notation is a slash 8, This means that the length of the subnet mask is 8 position .
边栏推荐
- Insert and update each database
- 同花顺app是正规的吗?到底安不安全
- Causes and solutions of unreliable JS timer execution
- Decryption of APP parameters of a cross-border export e-commerce - dunhuang.com
- Desktop network error display red ×, Component failed to start
- The latest promo! 1 minute to understand the charm of the next generation data platform
- Is it safe for qiniu school to open an account in 2022?
- Data query of server SQL. The most important chapter in database learning
- Basic process of configuring utf8 in idea
- Common optimization of e-commerce server system architecture
猜你喜欢
Docker failed to remotely access 3306 after installing MySQL

Cvpr2020 | the latest cvpr2020 papers are the first to see, with all download links attached!

Flexible scale out: from file system to distributed file system
Interviewer: why does TCP shake hands three times and break up four times? Most people can't answer!

Heavy update! Yolov4 latest paper! Interpreting yolov4 framework

Installing mysql8 under centos8

1.1-mq visual client preliminary practice

Molecular dynamics - basic characteristics of molecular force field
HMS core actively explores the function based on hardware ear return, helping to reduce the overall singing delay rate of the singing bar by 60%
Tencent music knowledge map search practice
随机推荐
银河证券靠谱吗?开证券账户安全吗?
[distributed system design profile (1)] raft
The beginning of manjaro's journey
Sonar series: continuous scanning through Jenkins integrated sonarqube (IV)
After 20 days' interview, I finally joined Ali (share the interview process)
Cvpr2020 | the latest cvpr2020 papers are the first to see, with all download links attached!
[opencv] opencv from introduction to mastery -- detailed explanation of input and output XML and yaml files
Is it legal to open an account for flush stock trading software? Is it safe?
[data recovery in North Asia] a data recovery case in which the upper virtual machine data is lost due to the hard disk failure and disconnection of raid6 disk array
Interview records
Win10 common software
Illustrated with pictures and texts, 700 pages of machine learning notes are popular! Worth learning
How does jest expose specific problems in complex judgment conditions?
Slenium tips: how to handle some dialog boxes that may appear on Web pages
A new paradigm for large model application: unified feature representation optimization (UFO)
1.0-mq getting started and using
Is it safe for Xiaobai to open a stock account online?
Basic knowledge of software engineering required for soft test
Getting started and using postman
Exploration of advanced document editor design in online Era