当前位置:网站首页>Remote login sshd service
Remote login sshd service
2022-06-28 11:42:00 【redhat-YAN】
Remote login sshd service
One 、sshd The service is introduced
Openssh function
1.sshd Functions of services :
Security can be enabled on the remote host through the network shell operation
Secure SHell ssh client
Secure SHell daemon( Daemon , management ssh The process of , similar systemctld System daemons ) sshd Server side
2. Installation package
openssh-server
3. Master profile
/etc/ssh/sshd_conf
4. Default port 22( You can understand ,ip It's the gate of home , The port is the room door )
( The service is ip The open interface on the , To connect this interface is to use the functions of this program )
5. Client commands ssh
6. Experimental environment : Two virtual machines ,a Is the server ,b The client side.
Able to communicate , Close the drawing ,init 3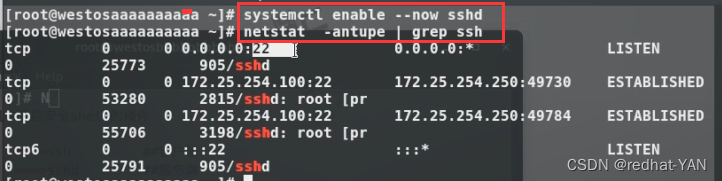
Two 、 Usage method
2.1 Basic usage
ssh It's used by the client , The server is connected
Can be in ssh Directly followed by the command
ssh -l Remote host users ( The server ) ip|hostname
ssh -l root 172.25.254.100
yes, The first connection will have 
fingerprint In your current directory .ssh/ Under
such as :cd /root/.ssh/
This file and the server 100 The above file is a match
Two key equally 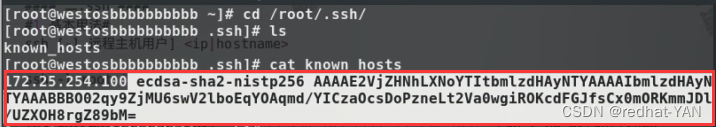

The second connection has no authentication fingerprint 
2.2 Analog matching ( authentication ) You don't succeed , Remote login failed
Delete the original key Restart the service , Then regenerate key
current key It's different from before 
Certification has changed , Authentication mismatch , Not through 
resolvent ( Prompt the red box to mark , There is a problem with this line of file ):
Delete the first line  summary :
summary :
When the connection is rejected due to authentication problems, the solution
Delete the corresponding line in the reminded file
3、 ... and 、 Common parameters
3.1 Common parameters
-l Specify the login user
-i Specify private key
-X Open graphics
-f Background operation
-o Specify connection parameters
-t Specify the connecting strip
3.2 Common parameter usage
-X Parameters
-X Open graphics
Real connection a host
ssh -l root 172.25.254.100
gedit Open graphics , It won't work
because ,ssh The default connection is text connection , Unable to open the graph  ``
``
ssh -X -l root 172.25.254.100
gedit
With the right to open graphics software 
-f Parameters
Can be in ssh Directly followed by the command 
Waiting for the opening time will occupy your terminal
After entering the backstage , You can run new instructions at the terminal 
-o Parameters
Specify connection parameters , This parameter can be in man View in
The most common parameters StrictHostKeyChecking=no
ssh -o "StrictHostKeyChecking=no" -l root 172.25.254.100
It will be automatically input as yes

-t Parameters
Connect A Server time , I have no right , Another server 250 I can connect and another server can connect A The server , You can connect first 250 In by 250 Jump to the A
First connect to 250 The server is then controlled by 250 The server jumps to 100
This is the time A What the server sees is 250 The server connects to it 
Four 、key authentication
4.1 Concept
B The client side. ,A Is the server
ssh -l root 172.25.254.100 So the connection must know root The password of the user on the remote server

This authentication method is called user authentication
The authentication method is symmetric encryption , Encryption and decryption use the same string of characters , Such as : The fingerprint
Asymmetric encryption , Encryption and decryption are different , Keys and locks
Symmetric encryption , Easy to crack , Can be brutally cracked ( Try one by one with a fast computer ), So the password should have strength verification , also Easy to forget
Asymmetric encryption , Encryption uses the public key , Decryption with private key , Will not be stolen , An attacker cannot log on to the server without a secret key
4.2 Generate public key and secret key
Public and private keys do not have to be generated on the server side , Both client and server can generate public and private keys ( For example, you can buy locks )
For example, generate public and private keys on the client side
ssh-keygen Commands for generating public and private keys
Ask you key( The secret key encrypts the string file ) Where to keep it , If you change the save path, you need to change ssh Master profile , Change trouble , So just use the default 
Set a password , You need a secret key and a password ,( The password of the secret key ) trouble , Directly enter  The public and private keys generate
The public and private keys generate 
cat /root/.ssh/id_rsa
This is the private key ( Unlock ) Public key ( locked )
Public key ( locked )cat /root/.ssh/id_rsa.pub
From the server frigerprint Fingerprint authentication password , Prove that this host B Connect to server A It was the original host B
 Both the generated public key and secret key are interactive , Not conducive to automatic operation
Both the generated public key and secret key are interactive , Not conducive to automatic operation
If you use scripts to generate public and secret keys , Scripts cannot run automatically
Automation is not interactive
ssh-keygen --help
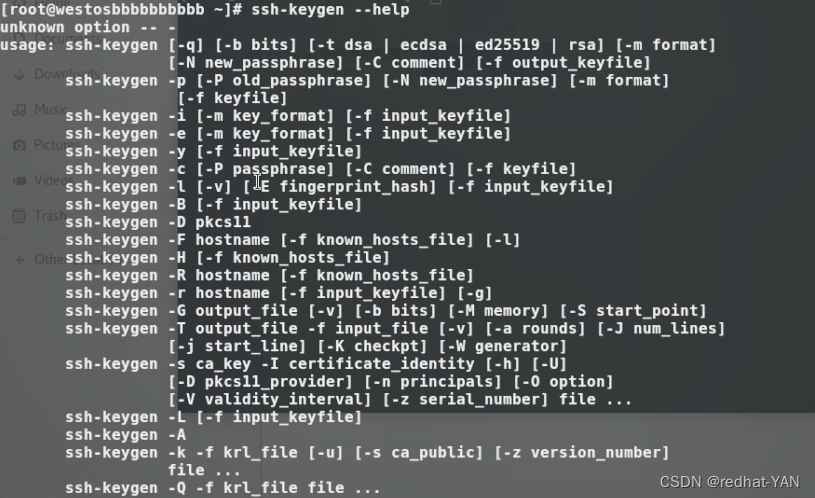
Non interactive generation of public and secret keys -f Specify to save the encrypted file -P Indicates the specified password
ssh-keygen -f /root/.ssh/id_rsa -P ""

4.3 Use of public and private keys ( locked )
ssh-copy-id -i /root/.ssh/id_rsa.pub [email protected]
Password of the server to be locked , Ask the locked server for permission , Otherwise it is illegal
You can't lock someone's house with a lock 
This time the server A There will be multiple files , This file is actually a public key 
and B The public key of is the same
 client B There's a private key , There is only one secret key
client B There's a private key , There is only one secret key 
Direct connection , No password required ( The only private key is used to open the public key by default )

If there are many private keys ,-i Specify the specific private key to open the public key 
4.4 summary
ssh-keygen -f /root/.ssh/id_rsa -P "" Generate Key
ssh-copy-id -i /root/.ssh/id_rsa.pub [email protected] use key Encrypt the server
After encrypting the server, there are two authentication methods , If you have a private key, you do not need to enter a password to connect , No private key input password connection
5、 ... and 、sshd Security optimization of services
5.1 Safety problem description
5.1.1 Original password and key authentication
7 Host can connect to our server A, Have the right to enter the password , But the function itself is not safe , It should not be opened , So turn off this function
So you need to run the server A Turn off unsafe functions on 
5.1.2 Modify the port
Do not modify port , As we all know, the port is 22 Default port
5.1.3 Limit who can connect and who can't
Set who can only be connected or who cannot be connected
5.2 Turn off the original password authentication
Edit server A Primary profile for 
Change to no The server A The password authentication function of is turned off , Only public and private keys (key) Authentication can be connected to
Before turning off password authentication , First, put key The authentication service is started , because Key Authentication requires password authentication to admit permission at the beginning Key authentication ( Allow locking )
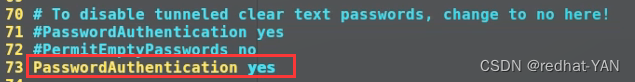
Restart the service systemctl restart sshd
Now I have no right to enter the password , Now we can't even crack it by force , Because there is no way to enter the password 
5.3 Modify the port
Because the server is turned on selinux Will limit your port changes , You need to change selinux Warning mode
Close the fire wall 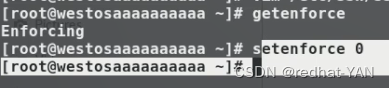
systemctl disable --now firewalld
Because the fire wall only allows 22 port , If you open the fire wall 2021 The test failed
Modify master profile

Restart the service systemctl restart sshd
The port becomes 2021 了


5.4 Set connectable objects ( Black and white list of users )
White list Only on the list can they be ssh Connect
In the main configuration file , Find a space to write AllowUsers westos You can only connect to westos user
Restart the service systemctl restart sshd
Multiple users
AllowUsers westos root
Restart the service systemctl restart sshd
Successful connection 
The blacklist The list cannot be ssh Connect
DenyUsers westos
westos Cannot pass ssh Connect
Restart the service systemctl restart sshd
5.5 summary

边栏推荐
- Web page tips this site is unsafe solution
- [sciter]: use of sciter FS module scanning file API and its details
- Day31 JS notes DOM 2021.09.26
- 工作组环境下的内网渗透:一些基础打法
- Unity screenshot function
- js中的class类模式及语法 2021.11.10
- Day34 JS notes regular expression 2021.09.29
- SQL必需掌握的100个重要知识点:检索数据
- 第2章 还记得点、线、面吗(二)
- Simple understanding of ThreadLocal
猜你喜欢

Making and using of static library

无法重新声明块范围变量

2022中国信通院首届业务与应用安全发展论坛成功召开!
Jetpack Compose Desktop 桌面版本的打包和发布应用

Cannot redeclare block range variables

Day39 prototype chain and page Fireworks Effect 2021.10.13

day34 js笔记 正则表达式 2021.09.29

Fancy features and cheap prices! What is the true strength of Changan's new SUV?

day31 js笔记 DOM下 2021.09.26

Training notice | special training notice on epidemic prevention and security prevention for overseas Chinese funded enterprises, institutions and personnel in 2022
随机推荐
使用API快捷创建ECS
Compareto() and equals() methods of BigDecimal class
如临现场的视觉感染力,NBA决赛直播还能这样看?
网页提示此站点不安全解决方案
携手Cigent:群联为SSD主控固件引入高级网络安全防护特性
基于验证码识别的机器学习项目captcha_trainer操作实践
Is it safe to buy stocks and open an account on the account QR code of the CICC securities manager? Ask the great God for help
day28 严格模式、字符串 js 2021.09.22
Intranet penetration in the working group environment: some basic methods
mysql-. SQL file phishing Online
day34 js笔记 正则表达式 2021.09.29
Join hands with cigent: group alliance introduces advanced network security protection features for SSD master firmware
智联招聘基于 Nebula Graph 的推荐实践分享
ThreadLocal的简单理解
工作组环境下的内网渗透:一些基础打法
李宏毅《机器学习》丨7. Conclusion(总结)
【sciter】: sciter-fs模块扫描文件API的使用及其注意细节
Everyone can participate in open source! Here comes the most important developer activity in dragon lizard community
This Exception was thrown from a job compiled with Burst, which has limited exception support. 报错
Thesis reading (59):keyword based diverse image retrieval with variable multiple instance graph