当前位置:网站首页>Attack and defense world web questions
Attack and defense world web questions
2022-06-30 14:10:00 【bk268】
web Rookie zone
view_source

Open the source code and find the answer here 
robots

see robots.txt file 
Find out flag File and open 
backup

There are backup files in the website , Common backup file suffixes are :“.git” 、“.svn”、“ .swp”“.~”、“.bak”、“.bash_history”、“.bkf” Try to URL Back , Try to find that the file suffix of this problem is .bak
Get a file to open and get the answer
cookie

Check first according to the title cookie
Find out look-here The value of is cookie.php Open this. php file

Follow the prompts to view this http Response package for 
Get the answer
disabled_button
When you open the topic and see the button you can't press, you will think of a familiar topic you learned before 
Open the source code and you will see this disable
Delete disable We can press this button
This will not make it disappear 
Get the answer
weak auth
Open the title to get a login interface
 Just type in and you will be prompted to say The user is called admin
Just type in and you will be prompted to say The user is called admin
View the source code to see  Then we'll use it burp Blow up the password
Then we'll use it burp Blow up the password
Set the Firefox proxy to open the request
Send to tester
Input the downloaded password dictionary to explode 
 notice 123456 The higher the frequency, the correct password should be
notice 123456 The higher the frequency, the correct password should be
( I don't know what went wrong. There was no answer after the explosion Then I input the user name and password on the web page to get the answer )
simple_php
Analysis of the php It means 
You can understand a And b Both of these values are in get The way
Then we must comply with a And b And must be bypassed in some way
We make a=0.0;b=1234*2 Go around 
get_post

First we should understand get And post Usage of 
We go through get Add... After the URL ?a=1
Get the following request 
adopt hackbug quantum Plugins enable b=2 With post Form submission 
Get the final answer
xff_referer
Read other people's blogs to understand what this title means
- xff yes http The extended head , Role is to make Web The server gets the IP Real address ( Forgeable ). Because many users access through a proxy server , The server can only get the proxy server's IP Address , and xff Its purpose is to record the reality of users IP. Usually you can modify it directly http In the header X-Forwarded-For Field to simulate the final of the request ip.
- referer yes http The extended head , The function is to record the address of the source page of the current request page . Server usage referer Confirm the source of the visit , If referer The content does not meet the requirements , The server can intercept or redirect requests .
So use brup Grab the bag , See in the response that it must come from Google , So add another Referer: https://www.google.com, You can get flag.

It is sent to the repeater
 The first step is to write... In the left box X-Forwarded-For:123.123.123.123i
The first step is to write... In the left box X-Forwarded-For:123.123.123.123i
It is found that... Appears in the response HTML Must be https://www.google.com
Step 2 continue to write Referer:https://www.google.com
Click send to get the answer
webshell
 In a word, Trojans
In a word, Trojans
I went backstage with a kitchen knife to get the answer  First add a shell
First add a shell Get the answer
Get the answer
command_execution
- Command Execution Vulnerability : Symbol &、|、|| Can be used as a command connector , The user submits the execution command through the browser , Because the server does not filter the execution function , Causes the command to be executed without specifying an absolute path .
Open and find a PING The page of , Try it first ,ping Local ,ping 127.0.0.1 Discovery can ping through .
Then we mixed it with orders ls To operate :127.0.0.1 && ls, Found to be executable .
After use find Command to find all txt Text
Reuse cat Open about flag The text of  simple_js
simple_js
According to the title, we can know that this question is about js Knowledge of language  View the source code of the web page and observe the main body js The code finds that whatever is entered, the last value returned is
View the source code of the web page and observe the main body js The code finds that whatever is entered, the last value returned is
dechiffre(h)
So we're going to go straight to
\x35\x35\x2c\x35\x36\x2c\x35\x34\x2c\x37\x39\x2c\x31\x31\x35\x2c\x36\x39\x2c\x31\x31\x34\x2c\x31\x31\x36\x2c\x31\x30\x37\x2c\x34\x39\x2c\x35\x30
Conduct url Decrypt ( take \x Convert to %)
Get a bunch of ASCII code
Decimal conversion gives the answer
边栏推荐
- Apache Doris Compaction優化百科全書
- 数据库表为什么写不进数据了
- [Title brushing] avoid flooding
- 数字化转型道阻且长,如何迈好关键的第一步
- 【Redis 系列】redis 学习十六,redis 字典(map) 及其核心编码结构
- Introduction to reverse commissioning - VA and RVA conversion in PE 04/07
- Exlipse operates on multiple rows at the same time. For example, input the same text in multiple lines and columns at the same time
- Begin End use the pit encountered
- Jetpack Compose 实现完美屏幕适配
- Lifting scanning tool
猜你喜欢

【 scientific literature measurement 】 mining and visualization of keywords in foreign and Chinese Literature
navicat数据库建表是没有utf8选项。

损失函数:DIOU loss手写实现

MFQE 2.0: A New Approach for Multi-FrameQuality Enhancement on Compressed Video

There is no utf8 option for creating tables in Navicat database.

Loss function: Diou loss handwriting implementation
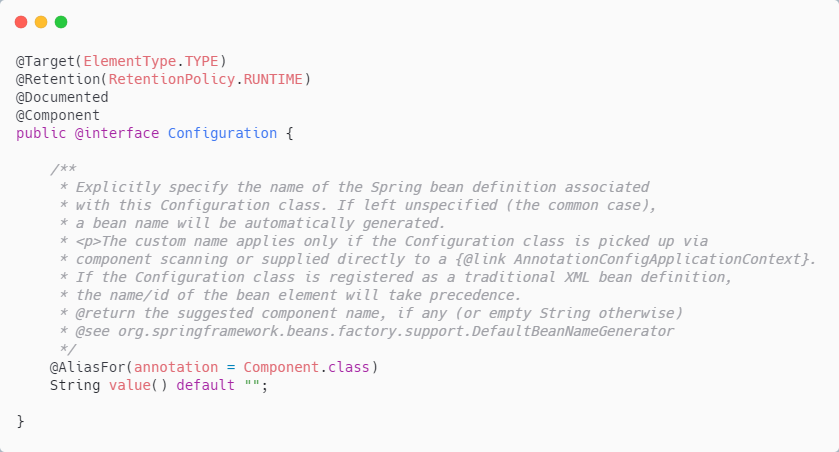
Tencent two sides: @bean and @component are used on the same class. What happens?

IM即时通讯应用开发中无法解决的“顽疾”

Google Earth Engine(GEE)——将字符串的转化为数字并且应用于时间搜索( ee.Date.fromYMD)

Rpm2rpm packaging steps
随机推荐
Click the TD cell of table to open the dialog pop-up window. After obtaining the value, put the value back into the TD cell
There is no utf8 option for creating tables in Navicat database.
Go language for loop multivariable use
JMeter transaction controller
科普达人丨漫画图解什么是eRDMA?
Go sync. WaitGroup
【系统分析师之路】第五章 复盘软件工程(敏捷开发)
PHP reverses scenarios based on code and skillfully uses debug_ backtrace()
Three uses of golang underscores
DNS resolution home network access public DNS practice
从控制层返回到js的json数据带“\”转译符,怎么去掉
DB2 SQL Error: SQLCODE=-206, SQLSTATE=42703
Directory related commands
【科学文献计量】外文文献及中文文献关键词的挖掘与可视化
【科研数据处理】[基础]类别变量频数分析图表、数值变量分布图表与正态性检验(包含对数正态)
Project management - common English vocabulary I
[kubernetes series] k8s set mysql8 case insensitive
IM即时通讯应用开发中无法解决的“顽疾”
Mutex lock, read / write lock, spin lock, pessimistic lock, and optimistic lock
ot initialized – call ‘refresh’ before invoking lifecycle methods via the context: Root WebApplicati