当前位置:网站首页>[Tang Laoshi] C -- encapsulation: member method
[Tang Laoshi] C -- encapsulation: member method
2022-06-27 18:19:00 【An old lion of Tang Dynasty】
Last article review
Access modifier
Determine access to member variables
public—— public
private—— private
Member variables
Variables declared in class
Describe the characteristics
The assignment is arbitrary
Any type
Any number
Today we will study in the future
Behavior of objects
Member method
【 Member method 】
Through the previous articles , We can already use member variables to describe the characteristics of objects in classes , But for objects , Characteristics alone are not enough . Such as human characteristics : full name , Age , Gender , Nationality and so on can be expressed by member variables , But for human behavior : Walk , having dinner , Sleep and so on , You can't use member variables . What we are going to learn today Member method , In the idea of object-oriented programming , Namely Used to express behavior Of !
Member method ( function )
↓↓↓↓
Declare methods in classes ( function )
↓↓↓↓
Write in a class statement block

Member method ( function ) The basic rules of
1. Declared in a class statement block
2. The rules are basically the same as the function declaration rules
3. Affected by access modifier rules
4. Is used to describe the behavior of objects
5. The return value parameter is not restricted
6. There is no limit to the number of methods
Member method ( function ), It is used to represent the behavior of objects , We can command an object to do a certain behavior through member methods , Concrete behavior is implemented externally without concern . We just need to know that we can get a certain result by issuing an order .
For example, when we play games , Player objects can move , Can release skills , These are the actions of the player object , We just need to call the corresponding behavior method ( function ), It can act accordingly . We only need to implement the specific logic in the function .
How to use these member methods ( function )?
↓↓↓↓

Be careful
The member method should not add static keyword
The member method must instantiate the object before using
Member methods are affected by access modifiers
public Decorated methods can be called externally
private Decorated methods can only be called internally
Don't write access modifiers to think private
【 summary 】
The member method is simple to understand : Write methods in classes ( function ), These methods represent the behavior of the object , These behaviors are realized through the logic in the method .
Member method
Describe behavior
Class
Any number
Return values and parameters
According to the demand
Focus on Tang Laoshi Get more dry content

边栏推荐
- Software testing - the concept of testing, the detailed introduction of unit testing, and how to design test cases
- Wanzhou gold industry: a common technical term in gold t+d transaction?
- Generate zip package command
- [leetcode] 2. Add two numbers (user-defined listnode), medium
- leetcode 70. climb stairs
- Extract field year / quarter effect based on date
- ROS "topic" programming implementation
- How to write a resume?
- Handling of difficult and miscellaneous problems during the installation and configuration of qt5.5.1 desktop version (configuring arm compilation Kit)
- d3dx9_ How to repair 40.dll? Win10 system d3dx9_ What if 40.dll is lost?
猜你喜欢

Explain the distributed computing of Apache skywalking OAP in detail
![[JS reverse hundreds of examples] I love to solve 2022 Spring Festival problems and receive red envelopes](/img/cb/0be2b2cf3b2cfa903190b7795d3cd7.jpg)
[JS reverse hundreds of examples] I love to solve 2022 Spring Festival problems and receive red envelopes

Simulated process scheduling
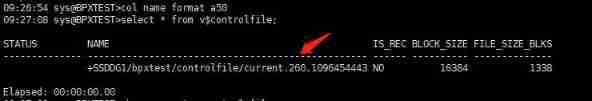
Control file related views

【多线程】线程通信调度、等待集 wait() 、notify()

Teach you how to realize pynq-z2 bar code recognition

07. Express routing

Wanzhou gold industry: what knowledge points do you need to master to invest in precious metals?
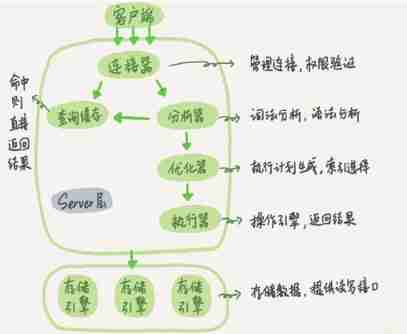
Overview of Inspur Yunxi database executor

How to improve it electronic equipment performance management
随机推荐
seata性能可以通过什么方式提高?比如增加数据库的计算节点?
Study on heritability and field experiment design
Some details of Huawei OSPF
CDH cluster installation
Jeesite 4.0 replaces the default view style and customizes the theme
d3dx9_ How to repair 32.dll? d3dx9_ Solution to 32.dll missing
[multithreading] thread communication scheduling, waiting set wait(), notify()
Drawing for example study of flashcc
Wanzhou gold industry: a common technical term in gold t+d transaction?
07. Express routing
[JS reverse hundreds of examples] I love to solve 2022 Spring Festival problems and receive red envelopes
428 binary tree (501. mode in binary search tree, 701. insert operation in binary search tree, 450. delete node in binary search tree, 669. prune binary search tree)
(5) SPI application design and simulation verification 1 - logic sorting
d3dx9_ How to repair 25.dll? d3dx9_ 25.dll where to download
Huawei cloud devcloud launched four new capabilities, setting two domestic firsts
Handwritten promise series - all
How much room does Migu video have for development without relying on sports events?
Sword finger offer 22 The penultimate node in the linked list
leetcode 19. Delete the penultimate node of the linked list
Application practice of day13 for loop distinguish the application of traversing break continue