当前位置:网站首页>Experiment 4 CTF practice
Experiment 4 CTF practice
2022-07-25 02:56:00 【Headwind/】
The experiment purpose : Through the penetration process of the target , understand CTF Competition mode , understand CTF Scope of knowledge covered , Such as MISC、PPC、WEB etc. , by way of practice , Strengthen the ability of teamwork , Master the preliminary CTF Actual combat ability and information collection ability . Familiar with network scanning 、 Probe HTTP web service 、 Directory enumeration 、 Raise the right 、 Image information extraction 、 Use of password cracking and other related tools .
System environment :Kali Linux 2、WebDeveloper Target source :https://www.vulnhub.com/
Experimental tools : There is no limit
Experimental steps and contents :
Purpose : Get the target Web Developer file /root/flag.txt in flag.
The basic idea : This segment IP Address survival scan (netdiscover); Network scanning (Nmap); Browse HTTP service ; Site directory enumeration (Dirb); Package file found “cap”; analysis “cap” file , Find the website management background account password ; Plug in utilization ( There are loopholes ); Exploit the vulnerability to obtain the server account password ;SSH Remote login server ;tcpdump Alternative applications .
The implementation details are as follows :
1、 Finding goals (netdiscover), find WebDeveloper Of IP Address . Screenshot .
2、: utilize NMAP Scan target host , The target host port is found to be open 、 Service situation , Screenshot and explain the services provided by the target ?( Use the knowledge points of the first experiment )
The port service opened by the target
22 port : Open the remote login service
80 port : Turn on http service
3、 If the target host provides HTTP service , Try using your browser to access the target website . Screenshot . Is there any information available ?
4、 utilize whatweb Detect the... Used by the target website CMS Templates . Screenshot . Analyze the use of CMS What is it? ?
5、 Web search wpscan, Briefly describe its function
function :WPScan yes Kali Linux The default comes with a vulnerability scanning tool , It uses Ruby To write , Able to scan WordPress A variety of security vulnerabilities in the website , These include WordPress Its own loopholes 、 Plug in vulnerabilities and theme vulnerabilities . The latest version WPScan Your database contains more than 18000 There are plug-in vulnerabilities and 2600 A theme vulnerability , And support the latest version of WordPress. It is worth noting that , It can not only scan things like robots.txt Such sensitive files , It can also detect currently enabled plug-ins and other functions
6、 Use Dirb Website directory .(Dirb It's a special tool for blasting catalog , stay Kali Has been installed by default , There are also foreign similar tools patator,dirsearch,DirBuster, Domestic imperial sword ) Screenshot . Find a directory that seems to be related to network traffic ( route ).

6、 utilize Wireshark Analyze the packet , analysis TCP Data flow . Find any useful information ? Screenshot .

Use the information obtained in the previous step to enter the background of the website . Screenshot 
8、 Use this CMS There is ( plug-in unit Plugin) Loophole .
9、 Take advantage of the vulnerability of the plug-in to raise rights .
programme 3: Using file management plug-ins (File manager) Loophole .
Install the plug-in , You can browse directly wp-config.php.


**10、SSH logon server
Try to connect to the remote server by using the user name and password to access the database obtained in the previous step . Screenshot .
1、 Try to view /root/flag.txt **
Cannot be viewed .
10、 Use tcpdump Execute arbitrary orders ( When tcpdump After capturing the packet, the specified command will be executed .)
Check the executable commands of the current identity and find that you can root Permissions to perform tcpdump command
Create Attack File 
Discovery can root Permissions to perform tcpdump command
Create Attack File
touch /tmp/exploit1
write in shellcode
echo ‘cat /root/flag.txt’ > /tmp/exploit
Give executable permission
chmod +x /tmp/exploit
utilize tcpdump Execute arbitrary orders
sudo tcpdump -i eth0 -w /dev/null -W 1 -G 1 -z /tmp/exploit -Z root
get flag
tcpdump Detailed command :
-i eth0 Capture packets from the specified network card
-w /dev/null Output the captured packet to the empty device ( Do not output packet results )
-z [command] Run the specified command
-Z [user] Specify the user to execute the command
-G [rotate_seconds] Every time rotate_seconds Once every second -w Specified dump
-W [num] Specify the number of packets captured
边栏推荐
- After working for two months in the summer vacation, I understood three routing schemes of keepalived high availability
- Inheritance (prototype)
- [TinyML]EfficientFormer:Vision Transformers at MobileNet Speed
- Mark down learning
- Three ways to solve your performance management problems
- JS written test question -- realize the flat function of array
- Request and response
- Learning record 12
- Wechat sports field reservation of applet completion works applet graduation design (8) graduation design thesis template
- Sum of "n" numbers of force deduction summary
猜你喜欢
Mid year summary and personal feelings
JS foundation -- data

Tp5.1 login configuration method of whether to login public functions (complete login case)

Simulation Implementation of string function (Part 1)

Learning notes - talking about the data structure and algorithm of MySQL index and the introduction of index
DOM operation -- get elements and nodes

Learning record XIII
![[stm32f103rct6] motor PWM drive module idea and code](/img/a5/3010acff73c8913e967ff3a024877e.png)
[stm32f103rct6] motor PWM drive module idea and code
Is redis'module'not an internal or external command?
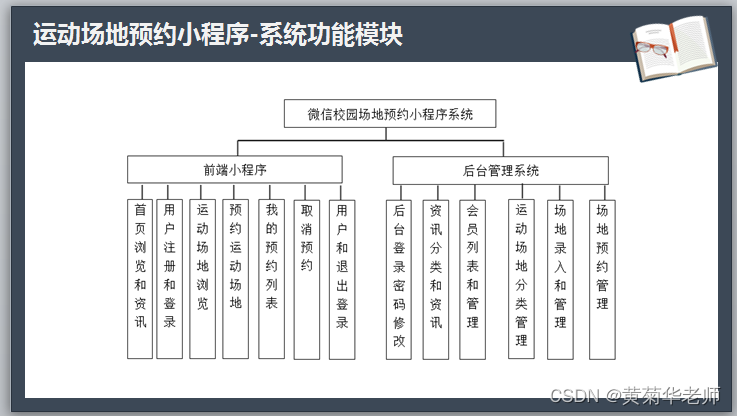
Wechat sports field reservation of the finished works of the applet graduation project (6) opening defense ppt
随机推荐
What are you working for? Don't give up is our only choice, come on, everyone
Daily three questions 7.19
[stm32f103rct6] motor PWM drive module idea and code
Text reading end judgment
# CF #808 Div.2(A - C)
Edit mathematical formulas in markdown
Details of happens before rules
Wechat sports field reservation of the finished works of the applet graduation project (5) assignment
Resolved (the latest version of selenium reported an error) attributeerror: module 'selenium webdriver‘ has no attribute ‘PhantomJS‘
Mp4 package analysis
Tp5.1 initialize initialization method (not \u initialize)
hello csdn
Dynamic planning of force buckle punch in summary
Web -- JDBC tool class writing
Object.defineproperty use
Map set learning
List title of force buckle summary
Learning Record V
JS written test question -- browser kernel
Flume's study notes