As the attack and defense drill mechanism matures , In the actual combat of attack and defense , The attack methods adopted by the red team are constantly upgraded with the development of network technology . The red team keeps updating its arsenal , And start using file free attacks 、 Supply chain attack and other higher-level attack technologies to bypass the defensive side's defense system , Conduct covert attacks .
From the perspective of enterprises , Traditional safety equipment has been lost , Such as a variety of Webshell The confusion 、 The penetration of social engineering into the terminal , These technologies used by attackers can basically penetrate the security architecture and systems stacked under the traditional security products . for example , With BYOD、 Cloud computing, etc , The attack area of enterprises has greatly increased , The dynamic entrance of enterprise and personal devices provides many attack points for the red team .
MITRE ATT&CK The framework establishes a knowledge base of attack defense confrontation , The attacker's tactics are recorded based on real data 、 Techniques and procedures (TTP), It provides a unified communication platform for the blue team and the red team .
Security personnel can use this framework as a starting point , Verify the detection range within its own environment , And according to the attacker's TTP Hunt for unknown threats , So as to strengthen the defense capability .
Detailed solutions , Please scan the code to download 《 Ivy threat hunting solution 》.

One 、 In the actual attack and defense, we are faced with 3 Big “ Soul torture ”
In the actual network attack and defense , Most enterprises are usually 3 A problem .
1、 How to detect unknown threats ?
How to detect unknown threats ? This problem is a paradox . Usually , Enterprises have purchased various safety products , But what can be detected are known threats . For known threats , The enterprise will make it a rule , Match according to the rules when the attacker attacks again . and
An unknown threat is one that has no idea how an attacker is invading . under these circumstances , How to detect an attacker's intrusion ?
2. How to confirm and analyze alarms ?
Now? , Many enterprises have purchased a variety of security equipment to improve their security defense capabilities , But then there are a lot of alarms . Regarding this , The enterprise needs to determine the following 3 A question :
secondly , The attacker's permission to reside on the machine is usually multipoint , Even if one of the detection rules is hit , He can come back at any time through other stops , This is very common in attack and defense practice .
Last , When the safety equipment gives an alarm , The attacker may have done a lot , For example, stealing vouchers 、 Leave more back doors , How to know all these situations from an alarm ?
3、 How to find other control points left by attackers in the intranet ?
When a machine of the enterprise sends out an alarm , The attacker may have invaded dozens of machines in the intranet of the enterprise . But how will the enterprise deal with this warning ?
They will confirm that this alarm is a real Trojan horse or a real attack , But because attackers often clear the traces of their own operations , So the security personnel don't know where they got in .
As an expedient , The security personnel had to delete the back door first , Or take the machine offline . Responsible security personnel may find many relevant personnel in different departments , Investigate logs on various devices for analysis .
But the vast majority of security personnel can't find out why , And then it's over , In fact, they don't know that the attacker left a back door in many machines .
How to get a clue from 、 An alarm restores the network attack “ crime scene ”, Trace back to other control points of the attacker in the intranet ?
Few enterprises can really solve these problems , If these problems are not solved , So what does it mean ?
The ability of enterprises to find real attacks is very poor . Although the security personnel saw a lot of warnings , But after the investigation, it was found that they all came from worms or automated scanning tests , In fact, no real attack was found .
Even if the security personnel discover the real attack , They can't solve the problem completely , The attacker cannot be completely removed from the system . Attackers tend to be multipoint resident , Even if the enterprise solves one of these problems , The attacker still resides in the intranet for a long time , And more confident .
Due to the lack of overall analysis of the enterprise , You can only see a single point of problem , Unable to confirm the loss after being attacked , therefore , It is difficult for enterprises to make an accurate assessment of the overall loss .
With the continuous improvement of the actual combat level of network attack and defense , this 3 One problem is that many enterprises have not solved it now 、 Also difficult to solve . Regarding this , How should enterprises make up for the missing parts of their security system ? Its core lies in changing passive detection into active analysis , Use threat hunting to make up for the shortcomings of enterprises in these areas .
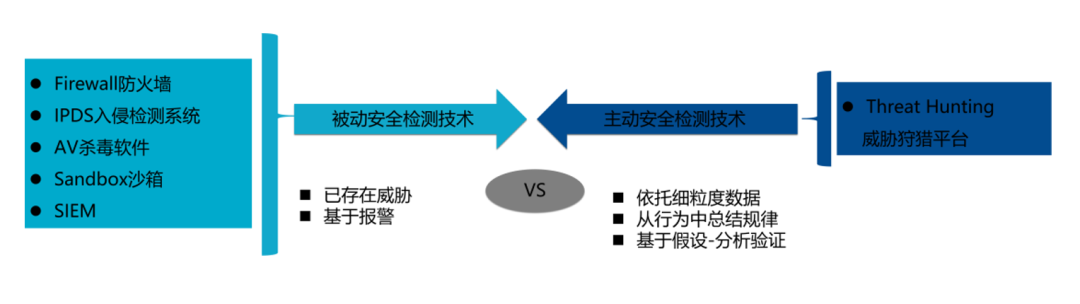
Two 、 Threatening to hunt : Turn passive defense into active analysis
Turning passivity into initiative , First, we need to explain the difference between passive detection and active analysis . Passive detection means passing through a firewall 、IPS、 Antivirus software 、 The sandbox 、SIEM Wait for the alarm generated by the safety product to find the problem . Because these alarms are rule-based , These rules are built into security products , Once data meets these rules , The security product will give an alarm . therefore , This approach is passive , Only those known threats can be found , For emerging threats , There's nothing it can do .
What is active analysis ? Active analysis is a more fine-grained correlation analysis based on the data provided by various security devices . For active analysis , Some security analysts specialize in analyzing threat clues from massive amounts of data , Build relationship image , To predict when an attack will occur, and so on . In the field of cyber security , Active analysis is often used in threat hunting systems .
Threat hunting is an active method to find and remedy undiscovered network attacks .
The threat hunting process includes searching for lost targets (IoC)、 survey 、 Classification and remediation . Threat hunting can be based on IoC drive , It can also be hypothesis driven , That is, start hunting from the initial assumption or problem , for example , Have we been affected by the rumored attacks ?
For threatening hunting , First of all, we should change our point of view , Its core lies in the shift from cognitive attacker to cognitive self .
Usually the business of an enterprise is regular , Even if the business of the enterprise will generate a lot of data , If security personnel continue to observe their business , Then you can also find your own subtle changes .
No matter which way the attacker uses to invade the enterprise , After the intrusion, it will destroy the system or steal data , This will cause the business operation rules to be broken or abnormal . If the security personnel focus on themselves , You can understand yourself deeply , Find your own rules , The slightest disturbance to the attacker can be reflected .
This is the core idea of threat hunting , It is based on the collection of its own fine-grained data , Find abnormal conditions through in-depth analysis of the summarized rules and their own running status .
3、 ... and 、 be based on ATT&CK Examples of threat hunting
As mentioned above ,
ATT&CK The framework is an attack and defense knowledge base based on real data , Security personnel can base on the attacks summarized in the framework TTP Threat hunting , To solve the problems faced in the actual attack and defense .
Here is what we call ATT&CK An example of threat hunting based on the framework .
2020 year 8 month , We found an intrusion into an organization . We observed a series of attackers in the whole invasion TTPs, This indicates that there may be multiple with advanced access APT The attacker .
During the invasion , Attackers often exploit compromised user accounts with administrative access . We also observed that , In addition to being widely used by attackers Webshell And custom tools and try to dump credentials outside , Also used. DLL Hijacking and for command and control (C2) communication WebMail Services and so on , This reflects that the attacker uses the persistent execution scheme to achieve the goal .
In the malicious activities just discovered , The attacker accessed a pre-existing Webshell, And use it for host reconnaissance , Including system information discovery and file and directory discovery . In reconnaissance activities , We have observed the use of Webshell Parsing C:\Windows\debug\PASSWD.LOG Log files . According to observation , The command used by the attacker is cmd/ccd/d"c:\Windows\debug\"¬epadpasswd.log.
It is known that PASSWD.LOG The file contains information about password changes 、 Authentication information , And the terminal services account “TsInternetUser” More about it . It should be noted that , In the use of “TsInternetUser” When the account authenticates the terminal services session , No login dialog box will pop up .
after , The attacker launched a pre-existing backdoor , To execute basic reconnaissance commands “quser”. This backdoor takes advantage of what remote desktops usually access “ Sticky key authentication bypasses ” function , The calling command used is rundll32.exe C:\Windows\System32\Speech\Common\MSACM32.dll, Run. Through the above DLL Analyze , Find that it belongs to “ Login bypass ” technology , It can allow an attacker to bypass any executable selected by the user .
DLL The absolute path of is very important , Because of malice DLL By using Microsoft Utility Manager(Utilman) Auxiliary program DLL Search order to achieve persistence , This technology is called “DLL Search sequence hijacking ”. When the user selects narrator Accessibility options ,Utilman Will load and execute malicious DLL.narrator Accessibility options initially perform some anti tamper checks , Then the hidden floating toolbar window is displayed on the display . And then , This window will listen for key events , If you observe that the user has entered a character sequence , A file open dialog box will be displayed . Once the operator selects a file , The file will be shell As a local SYSTEM Service account execution .
According to our subsequent continuous monitoring findings , One of the core tasks of an attacker is to dump credentials , They are likely to use this to maintain or deepen their foothold , And continue to move horizontally in the network of the victim organization . We found that attackers would write and try to execute custom versions of on multiple hosts Mimikatz Voucher dump tool . for example , An attacker may write and attempt to execute on the host Mimikatz Variant binaries mmstart_x64.exe.
Although attackers started using mmstart_x64.exe Voucher dump did not succeed , But the attacker switched to an alternate customization Mimikatz Variation file m.exe, Then on other hosts ( Including two domain controllers ) Attack again on . An example command line associated with this executable is shown below :
m.exe powerful-d sekurlsa logonpasswords >c:\windows\temp\12.txt
We find that attackers are very skilled at using Mimikatz Software . This is because after the last failure , The attacker appeared on another domain controller the next day , And use process injection to successfully inject malicious DLL powerkatz.dll Inject svchost.exe In memory space of , especially netsvcs In the group , And try to execute Mimikatz. Execute malicious tools by executing process injection , This is usually a method used by attackers to circumvent security detection .
About a month later , We observe that legal WMI(Windows Management specification ) Provided wmiprvse.exe Malicious... Was loaded from the exception location DLL file loadperf.dll.
The above malware uses... Registered in the target organization Webmail, Communicate via email , And it seems to contain Webmail Account voucher to receive C2 command . Through analysis , We found that malware passed through Webmail Services communicate to receive tasks , Message drafts and .rar Attachment for communication . Besides , The malware can also execute commands on the host . This example can reflect how deeply the attacker has a foothold in the victim organization network .
The following is based on MITRE ATT&CK The framework summarizes all the tactics and technologies used in this intrusion , It includes some technologies that may not be included in the previous intrusion profile .


For more details on threat hunting ,
Please scan the code to download 《 Ivy threat hunting solution 》.

原网站版权声明
本文为[InfoQ]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/173/202206221051080477.html














